Create a Monitoring Domain
GigaVUE-FM connects to the AWS Platform through the public API endpoint. HTTPS is the default protocol which GigaVUE-FM uses to communicate with the API. For more information about the endpoint and the protocol used, refer to AWS service endpoints.
GigaVUE-FM provides you the flexibility to monitor multiple VPCs. You can choose the VPC ID and launch the GigaVUE fabric components in the desired VPCs.
Note: To configure the Monitoring Domain and launch the fabric components in AWS, you must be a user with fm_super_admin role or a user with write access to the Infrastructure Management category. Refer to Role Based Access Control for more detailed information.
Prerequisites:
Complete one of the following actions, depending on your deployment option.
|
Deployment Options |
Reference Topics |
|
GigaVUE-FM Orchestration |
|
|
Deploying GigaVUE Fabric Components using GigaVUE-FM with Traffic Acquisition method as Traffic Mirroring or Customer Orchestrated Source |
|
|
Deploying GigaVUE Fabric Components using AWS with Traffic Acquisition method as UCT-V |
|
|
Third Party Orchestration |
|
|
Deploying GigaVUE Fabric Components using AWS with Traffic Acquisition method as Traffic Mirroring or Customer Orchestrated Source |
|
|
Deploying GigaVUE Fabric Components using AWS with Traffic Acquisition method as UCT-V |
|
To create a Monitoring Domain:
- Go to Inventory > VIRTUAL > AWS , and then select Monitoring Domain.
- On the Monitoring Domain page, select New. The Monitoring Domain Configuration page appears.
- Select Check Permissions and validate whether you have the required permissions.
- In the Monitoring Domain field, enter an alias used to identify the Monitoring Domain.
- From the Traffic Acquisition Method drop-down list, select one of the following tapping method:
- UCT-V: UCT-Vs are deployed on your VMs to acquire the traffic and forward the acquired traffic to the GigaVUE V Series Nodes. If you select UCT-V as the tapping method, you must configure the UCT-V Controller to communicate to the UCT-Vs from GigaVUE-FM.
You can also configure the UCT-V Controller and UCT-Vs from your own orchestrator. For details, refer to Configure GigaVUE Fabric Components in AWS using Third Party Orchestration - Integrated Mode. - VPC Traffic Mirroring: If you select the VPC Traffic Mirroring option, the mirrored traffic from your workloads is directed directly to the GigaVUE V Series nodes, and you need not configure the UCT-Vs and UCT-V Controllers.
For more information on VPC Peering, refer to VPC peering connections in the AWS Documentation. Peering is required to send mirrored traffic from other VPCs into a centralized GigaVUE V Series deployment. You can choose to use an external load balancer for Traffic Mirroring. Select Yes to use load balancer. For details, refer to Configure AWS Elastic Load Balancing. - UCT-V Controller configuration is not applicable for Traffic Mirroring.
- Traffic Mirroring does not support cross-account solutions without a load balancer.
- For VPC Traffic Mirroring option, additional permissions are required. For details, refer to Permissions and Privileges (AWS).
- After deploying the Monitoring Session, a traffic mirror session is created in your AWS VPC consisting of a session, a filter, sources, and targets. For more details, refer to Traffic Mirroring in AWS Documentation.
- Customer Orchestrated Source: If you use select Customer Orchestrated Source as the tapping method, you can use the Customer Orchestrated Source as a source option in the monitoring session, where the traffic is directly tunneled to the GigaVUE V Series nodes without deploying UCT-Vs and UCT-V Controllers. The user is responsible for creating this tunnel feed and pointing it to the GigaVUE V Series Node(s).
Note: When using Application Metadata Exporter (AMX) application, select the Traffic Acquisition Method as Customer Orchestrated Source.
NOTE:
- UCT-V: UCT-Vs are deployed on your VMs to acquire the traffic and forward the acquired traffic to the GigaVUE V Series Nodes. If you select UCT-V as the tapping method, you must configure the UCT-V Controller to communicate to the UCT-Vs from GigaVUE-FM.
- In the Traffic Acquisition Tunnel MTU, enter the MTU value.
-
The Maximum Transmission Unit (MTU) is the maximum size of each packet that the tunnel endpoint can carry from the UCT-V to the GigaVUE V Series Node. The default value is 8951.
-
When using IPv4 tunnels, the maximum MTU value is 8951. Ensure that the UCT-V tunnel MTU is 50 bytes less than the destination interface MTU size of the UCT-V.
-
When using IPv6 tunnels, the maximum MTU value is 8931. Ensure that the UCT-V tunnel MTU is 70 bytes less than the destination interface MTU size of the UCT-V.
- Turn on the Use FM to Launch Fabric toggle, to deploy GigaVUE Fabric Components using GigaVUE‑FM.
- Select Yesto Configure GigaVUE Fabric Components in GigaVUE‑FM
- Select No to Configure GigaVUE Fabric Components in AWS using Third Party Orchestration - Integrated Mode.
- Turn on the Enable IPv6 Preference toggle, to create IPv6 tunnels between UCT-V and the GigaVUE V Series Nodes.
Note: This appears only when Use FM to Launch Fabric is disabled and Traffic Acquisition Method is UCT-V.
- Under Connections, in the Name field, enter an alias used to identify the connection.
- From the Credential drop-down list, select an AWS credential. For detailed information, refer to Create AWS Credentials.
- From the Region drop-down list, select AWS region for the Monitoring Domain. For example, US West.
- From the Accounts drop-down list, select the AWS accounts.
- From the VPCs drop-down list, select the VPCs to monitor.
- Select Save.
You can view the new Monitoring Domain in the Monitoring Domain page list view.
To edit a Monitoring Domain, select the deployed Monitoring Domain and select Actions. From the drop-down list, select Edit, the Monitoring Domain Configuration page appears.
Check Permissions while Creating a Monitoring Domain
To check the permissions while creating a Monitoring domain, follow these steps:
- Go to Inventory > VIRTUAL > AWS, and then select Monitoring Domain. The Monitoring Domain page appears.
- Select New. The Monitoring Domain Configuration page appears.
- Enter the details as mentioned in the Create a Monitoring Domain section.
- Select the Check Permission button. The Check Permissions widget opens.
- Select the connection for which you wish to check the required permissions and then click Next.
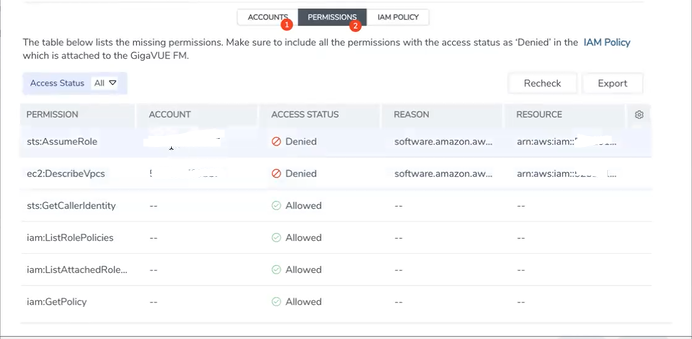
- Select on the Permission Status to view the missing permissions. The ACCOUNTS tab lists the accounts and the permissions status.
- Review the accounts that has an error in the permission status. The PERMISSIONS tab lists the permissions required to run GigaVUE Cloud Suite for AWS.
- Make sure to include all the permissions with Access Status as Denied in the IAM policy. The IAM POLICY tab lists the sample policy containing the required permissions for deploying the GigaVUE Cloud Suite for AWS.
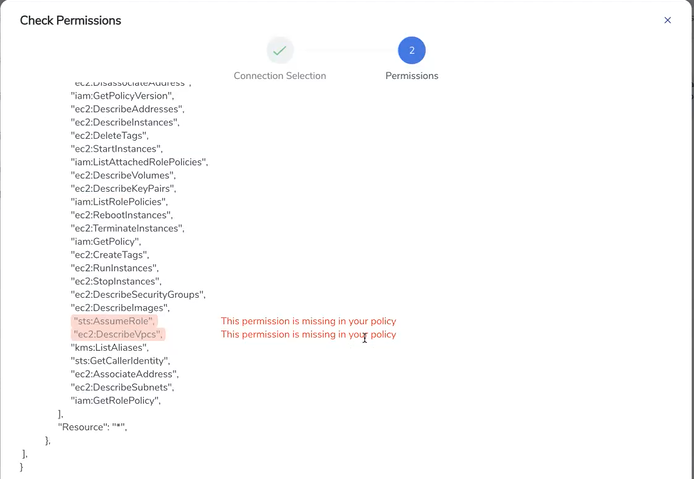
- Update the AWS IAM policy with the missing permissions that are highlighted in the JSON.
- Go to the PERMISSIONS tab and select Recheck to recheck the IAM policy.
When you select Copy or Download, the entire JSON file is copied or downloaded.
Note: After updating the IAM Policy, it takes around 5 minutes for the changes to reflect on the Check Permissions screen.
You can view the permission status reports in the Monitoring Domain page. Permission status reports consist of previously run Check permissions reports. They are auto purged once every 30 days. You can change the purge interval from the Advanced Settings page. For details, refer to Configure AWS Settings.
-
View permission status report: In the Monitoring Domain page, select Actions > View Permission Status Report.
-
View or delete individual reports: Select the report and select Actions.
What to do Next:
Based on your chosen deployment option, perform any of the following actions:
- Use FM to Launch Fabric is enabled: You are navigated to the AWS Fabric Launch Configuration page. For details, refer to Configure GigaVUE Fabric Components in GigaVUE‑FM.
- Use FM to Launch Fabric is disabled: You must deploy GigaVUE Fabric Components using AWS. For details, refer to Configure GigaVUE Fabric Components in AWS using Third Party Orchestration - Integrated Mode.



