Configure Inline TLS/SSL Decryption Using GigaVUE‑FM
This section describes how to configure inline TLS/SSL decryption using GigaVUE‑FM.
Note: Before configuring, review Get Started with Inline TLS/SSL Decryption for pre-requisites and review Introduction to Inline TLS/SSL Map Workflows.
|
Configure Inline TLS/SSL Decryption Using GigaVUE‑FM:
|
Inline TLS/SSL Map Workflow Steps (for Flow B) :
|
| 1 | Select Inline TLS/SSL Configuration Workflow |
To configure inline TLS/SSL decryption:
- Access the workflow
- Go to Physical Nodes and select a GigaVUE‑HC1, GigaVUE‑HC2, or GigaVUE‑HC3.
- Complete the Configure Inline TLS/SSL Decryption Using GigaVUE‑FM.
- Complete the Inline TLS/SSL Map Workflow Steps (for Flow B) .
- After completing the set-up workflows, verify Your Maps.
- Click To Maps to verify the maps created by the workflow.
- For inline network ports, go to Inline Bypass > Inline Networks. Select the inline network port and click Edit from the Actions drop-down menu. Under Configuration, select a traffic path of To Inline Tool. If using protected inline networks, disable Physical Bypass.
- Click Apply.
-
On the left navigation pane, click
 , and then select Physical > Nodes.
, and then select Physical > Nodes. -
In the Physical Nodes page, select the node for which you want to create the Key Store password. Go to GigaSMART>Inline SSL >Key Store.
- Set Up Keychain Password
- Click Keychain Password from the Actions drop-down menu.
-
Enter a password in the Password field.
You can only configure a strong password. A strong password should include at least eight (8) or more characters (up to 64) and include the following:
one uppercase letter one lowercase letter one numerical character one special character - Enable the Auto login check box to let GigaVUE-FM unlock the key store when the node reboots
- Click Save. The keychain password is setup.
- Set Up the Key Pairs
- Add a New key pair:
- Click New to configure the primary signing certificate and private key. The primary CA re-signs certificates for servers that present a valid certificate.
- Enter an Key Alias for the Key Pair. Click RSA or ECDSA for Key Type. Click PEM or PKCS12 for Type.
(optional) For Passphrase, enter a passphrase for the key.
Select a Private Key by pasting the copied key in PEM format or installing from URL or installing from local directory.
Select a Certificate by pasting the copied key in PEM format or installing from URL or installing from local directory.
- Click OK. The Primary Key Pair is added and can be selected from the Key Store page.
- Still under Key Store, repeat the "Add a key pair" steps to configure the secondary signing certificate and private key.
- Add a New key pair:
- Set up the Signing Certificate Authority (CA)
- The next step is to configure Signing CA. Click Signing CA from the Inline SSL page.
- Click Add and map each of the key pairs installed to the Primary Root CA and Secondary Root CA.
- Click OK to confirm the changes. The signing CA is configured.
- Set Up the Trust Store (optional)
- The next step is to configure the Trust Store.
- Click Trust Store from the Inline SSL page.
- No configuration is required if you use the default Trust Store by selecting Reset to Default from the Actions menu.
- Set Up the inline SSL Policy Profile
- The next step is to set up Inline SSL Profile.
- Click SSL Profiles from the Inline SSL page.
- Click New to configure an inline TLS/SSL profile. The profile specifies policy configuration, such as certificate handling and actions to take for the profile.
- Enter an alias for the profile. Under Policy Configuration, select a Default Action of Decrypt. Under Security Exceptions, select Decrypt or Drop.
- Under No-decrypt list/Decrypt list, enable the No-decrypt list and Decrypt list checkbox. Enter the paths to the files.
- Under Policy Rules, click Add a Rule.
- Select Category from the Rule drop-down (under condition) menu. Select financial_services from the Category drop-down menu. Add another rule.
- Select Category from the Rule drop-down menu. Select health_and_medicine from the Category drop-down menu. Add another rule.
- Select Domain from the Rule drop-down menu. Enter youtube.com in Value text box for the Domain. Click Apply.
- The inline TLS/SSL profile is added. For details about the Inline TLS/SSL Policy Profile fields and their descriptions, refer to Inline TLS/SSL Policy Profile—Field References.
- Set Up Network Access
- The next step is to set up Network Access.
- Click Network Access from the Inline SSL page.
- Select DHCP and DHCP Enabled for a specified GigaSMART module.
- Click OK. The network access is configured.
Note: To verify the Network Access configuration, you can do the Ping Test as follows:
- Navigate to GigaSMART > Inline SSL > Network Access.
- In the Inline SSL Network Access window, on the Ping Test section, enter or select the GigaSMART Port and IP Address/Host Name.
- Click Ping to run the ping test. The test results appears in the Ping Result box.
Next, complete the Inline TLS/SSL Map Workflow Steps (for Flow B)
The following table lists and describes the attributes that define the Inline TLS/SSL Policy Profile.
|
Field |
Description |
||||||||||||||||||
|
Alias |
Enter a unique name for the flexible inline SSL APP. |
||||||||||||||||||
|
Policy Configuration |
|||||||||||||||||||
|
SSL Monitor Mode |
Select an SSL Monitor Mode from one of the following options:
Refer to Inline TLS/SSL Monitor Mode for details. |
||||||||||||||||||
|
Default Action |
Select one of the following option:
|
||||||||||||||||||
|
URL Cache Miss Action |
Select one of the following options:
|
||||||||||||||||||
|
Tool Fail Action |
The failover action taken in response to a failure of an inline tool. Select one of the following options:
|
||||||||||||||||||
|
Decrypt Tool bypass |
Bypasses the decrypted TLS/SSL traffic. |
||||||||||||||||||
|
No Decrypt Tool bypass |
Bypasses the non-decrypted TLS/SSL traffic. |
||||||||||||||||||
|
Non-SSL TCP Traffic Tool bypass |
Bypasses the non-TLS/SSL, that is the TCP intercepted traffic. |
||||||||||||||||||
|
High Availability |
Select the check box to detect the link switchover by upstream device that is in active or standby mode. Note: Do not select this check box if the inline network links are in active state. Refer to High Availability Active Standby for details. |
||||||||||||||||||
|
Network Group Multiple Entry |
Select this check box to allow the traffic from different inline network to reenter GigaSMART. Refer to Inline Network Group Multiple Entry for details. |
||||||||||||||||||
|
Tool Early Engage |
Select this check box to allow the inline tools to change the MAC address or VLAN IDs. When a connection request is received from the client, GigaSMART establishes the connection with the inline tool first, before connecting with the server. This helps the inline tools to modify the MAC address or VLAN IDs when sending the traffic back to the server. Refer to Tool Early Engage for additional information and limitations. |
||||||||||||||||||
|
One-Arm Mode |
Select this check box to have both the client and server traffic travel through the same physical link or logical aggregate port channel. Refer to Tool Early Engage for additional information and limitations. Note: You can enable the One-Arm mode only if you have enabled the Tool Early Engage option. |
||||||||||||||||||
|
StartTLS Port |
Enter the required SSL/TLS ports. Refer to StartTLS and HTTP CONNECT for details. |
||||||||||||||||||
|
Security Exceptions |
You can choose to either decrypt or drop the traffic for the following certificates:
You can also choose to configure the security exceptions for certificate revocation validation based on OCSP or CRL on inline decryption profile. Select one of the following options:
Refer to Certificate Revocation List (CRL), Online Certificate Status Protocol (OCSP), CRL and OCSP, and Checking Certificate Revocation Status for details. |
||||||||||||||||||
|
No-decrypt list/Decrypt list |
Select the following check boxes:
To update/append, download the existing whitelist/blacklist text file from GigaVUE-FMFM, add new entries, and upload. This will not remove the existing entries in the list. To replace the entire list, download the existing whitelist/blacklist text file from GigaVUE-FM, retain a copy, clear the list and upload a new whitelist/blacklist. Refer to No-decrypt Listing Policy and Decrypt Listing Policy for details. |
||||||||||||||||||
|
Policy Rules |
Add the required policy rules for the inline decryption profile. |
||||||||||||||||||
|
TCP Port Map Decryption |
The TCP destination port for decrypted traffic sent to inline tools can be configured as part of the inline decryption profile. Configure the required Priority 1 map, which is user configurable and Priority 2 map, which is the default out port. Refer to Inline TLS/SSL Decryption Port Map for details. |
||||||||||||||||||
|
TCP Settings |
Configure the required TCP settings as follows:
|
||||||||||||||||||
|
Server Key Map |
A server key map binds a server with a key pair alias. |
||||||||||||||||||
|
Split-Proxy Settings |
|||||||||||||||||||
|
Split-Proxy |
Select the check box to enable the split proxy settings for the inline decryption solution. The TLS connection between the server and client is divided into two independent connections and the security parameters are kept separate. |
||||||||||||||||||
|
Non-PFS Ciphers (Server) |
Select the check box to enable the non-PFS ciphers settings for the inline decryption solution that has the split proxy settings enabled. This setting is to indirectly force the server to use protocols that are lower than TLS1.3 with non-PFS ciphers. This means that the ciphers with DHE/ECDHE key-exchange will not be used on the server side. |
||||||||||||||||||
- After completing the Configure Inline TLS/SSL Decryption Using GigaVUE‑FM, go to Workflows and select Inline SSL Map from the Inline GigaSMART Operations section.
- Set Up Inline Networks
- Select FLOW B.
- The first step in the Workflow is Inline Network(s). Select a default inline network from the Inline Network(s) drop-down menu. This is a protected inline network.
- Set Up Inline Tools
- Click Next. The next step in the Workflow is Inline Tool(s).
- Click Create Inline Tool. Then click Port Editor. In the Quick Port Editor, locate ports and select Type of Inline Tool from the drop-down menu. Click Enable for those ports.
- Click OK. The inline tool port is added. Click Close to exit the Quick Port Editor.
- Still under Inline Tool(s), enter an alias for the inline tool. Select Port A and Port B from the drop-down menus for the inline tool port pair. Under Configuration, ensure that Inline tool sharing mode is selected. Under Heartbeats, select Enable Regular Heartbeat.
- Click OK. The inline tool is configured.
- Create GigaSMART Group
- Click Next. The next step in the Workflow is GS Group. Click Create to configure a GigaSMART group and associate it with a GigaSMART engine port. Enter an alias for the GigaSMART group and select a GigaSMART engine port from the Port List.
- Click OK. The GigaSMART group is added.
-
Note: You should always allow a maximum of 3 minutes time gap when you delete and recreate a gsgroup through GigaVUE-FM.
- Set Up the Virtual Port
- Click Next. The next step in the Workflow is Virtual Port. Click Create to configure a virtual port.
- You cannot add multiple vports on the same gsgroup.
- Enter an alias for the virtual port, select the previously configured GigaSMART group, then select an Inline Failover Action.
- Click OK. The virtual port is added.
- Set Up the GigaSMART Operation
- Click Next. The next step in the Workflow is GS Operation. Click Create to configure a GigaSMART operation.
- Enter an alias for the GigaSMART operation, select the previously configured GigaSMART group, select Inline SSL as the GigaSMART Operation (GSOP), then select the previously configured Inline SSL profile.
- Click OK. The GigaSMART operation is added.
- Set Up the Inline Rule-Based Map
- Click Next. The next step in the Workflow is Inline Rule Based Map.
- Configure the inline rule-based map. This map directs traffic from the inline network to the inline tool, using a specified rule. It has the same source port as the inline first level map and the same destination port as the inline second level map. Enter an alias for the map, and select the map Type (Inline) and Subtype (By Rule), select the source inline network and the destination inline tool.
- Click Add a Rule to specify a map rule. Click Bi-directional, select IPv4 Protocol from the Rule drop-down menu, and select TCP from the Protocol drop-down menu. Select Port Destination from the Rule drop-down menu and enter 80 in the text box for Min.
- Click OK. The map is added.
- Set Up the Inline First-Level Map
- Click Next. The next step in the Workflow is Inline First Level Map.
- Configure the inline first level map. This map directs TCP traffic from the inline network to a virtual port (and to GigaSMART). Enter an alias for the map, and select the map Type (Inline First Level) and Subtype (Ingress to Virtual Port). Under Map Source and Destination, select the inline network as the source and the virtual port as the destination. Under Map Rules, click Add a Rule. Select IPv4 Protocol from the Rule drop-down menu, and select TCP from the Protocol drop-down menu.
- Click OK. The map is added.
- Set Up the Inline Second-Level Map
- Click Next. The next step in the Workflow is Inline Second Level Map.
- Configure the next map, which is the inline second level map. This map directs traffic from the virtual port, uses the inline TLS/SSL GigaSMART operation, and sends traffic to the inline tool. Enter an alias for the map and select the map Type (Inline Second Level) and Subtype (Egress from Virtual Port). Under Map Source and Destination, select the virtual port as the source and the inline tool as the destination, then select the inline SSL GigaSMART operation.
- Click OK. The map is added.
- Set Up the Collector Map
- Click Next. The next step in the Workflow is Collector Map (bypass).
- Configure a collector map for any unmatched traffic including non-TCP traffic, which is directed to bypass. Enter an alias for the map, and select the map Type (Inline) and Subtype (Collector), then select a Traffic Path of ByPass. Under Map Source and Destination, select the inline network as the source.
- Click OK. The map is added.
Refer Offloading TLS Decryption for an One-armed Inline Tool in L3 or IP Forwarding Mode for more detailed information.
Inline TLS/SSL L3 Tool NAT/PAT Support
This feature focuses on a new approach in GigaSMART to offload TLS decryption from Layer 3 inline-tools performing NAT/PAT (Network Address Translation / Port Address Translation) on the traffic passing through them. The GigaSMART engine maintains two separate sessions towards the client and server-side to achieve this.
Supported Platforms
| Gen3 cards in HC1 and HC3 |
| HC1-Plus |
Topology
The following are the preferred topologies for connecting to L3 NAT/PAT tools. The tool must be connected to the Nb side of the inline-network pair and the network links must be connected to the Na side of the inline-network pair.
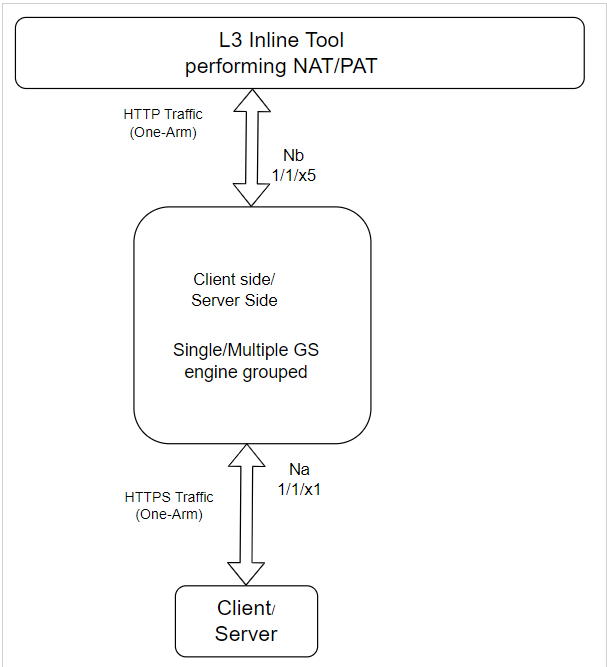

The traffic from the network is forwarded to the tool and the reverse traffic from the tool is forwarded to the server side.
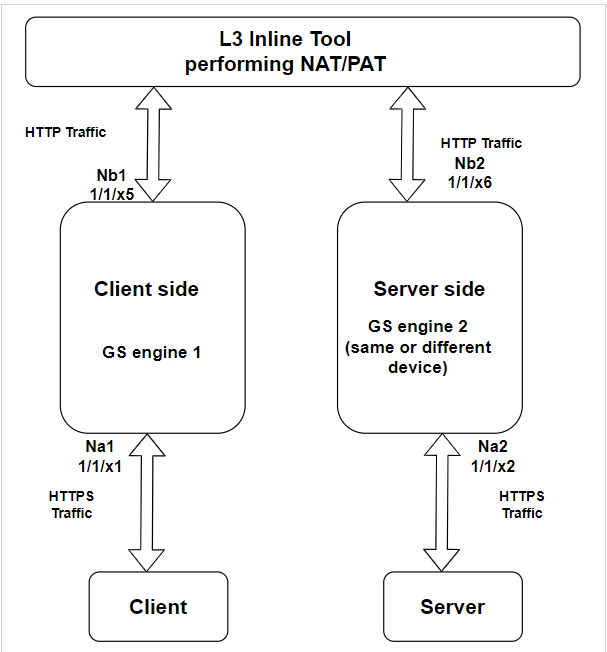
Also due to separation of client and server side connections, it is possible to have the client and server connected across GS engines or devices as shown below.
However currently there is no communication mechanism between separate engines or devices. The fail-over action for these solutions must be vport-drop to avoid leaking of decrypted traffic to the network.
HTTP 2.0 Downgrade
In the Inline SSL APP, the HTTP2 Downgrade option is enabled by default, when the Nat-Pat Mode is enabled. The HTTP 2.0 traffic is downgraded to HTTP 1.1 and decrypted. When HTTP2 Downgrade option is disabled, the HTTP2 traffic is forwarded without decryption.
Cache Timeout
The server information is cached for performance optimization. The default time out is 30 minutes. The cache is flushed when the cache timeout value is set to zero. The cache is disabled when the timeout value is set to zero.
Refer to the following Gigamon Validated Design for more information:
- Offloading TLS Decryption for an One-Armed Inline Tool in L3 with NAT/PAT Mode
- Enabling GigaSECURE TLS Decryption to Offload SSL Inspection from Next-Generation Firewall
Limitations
| The decrypted data to inline tool is limited to HTTP/1.1 protocol over TLS, inline tool will only see encrypted data on other application protocols. |
| The StartTLS traffic will not be decrypted as it is non HTTP traffic. |
| It does not support bypass tool since all the packets from client or server need to pass to inline tool for NAT/PAT. |
| This feature cannot co-exist with features such as Network group multiple entries, Inline network high availability, RIA, Tool early engage, Tool early inspect, one-arm, and Destination port translation. |
| The IPv6 version is not supported in software release version 6.1.00. The IPv6 version is supported from software release version 6.2.00. |



