Offloading TLS Decryption for an One-armed Inline Tool in L3 or IP Forwarding Mode (5.12)
Introduction
Network segmentation is widely adapted for scalability and security reasons. Often, clients and servers within an enterprise network reside on different network segments. The traffic between the clients and servers may traverse such tools as a Next-Generation Firewall (NGFW), deployed in one-arm mode, performing IP forwarding and inter-VLAN routing. Depending on the type of NGFW, the performance could degrade if TLS decryption is enabled. You can offload TLS decryption to improve the tool's performance. You can also selectively decrypt the traffic for inspection, thereby improving the shelf life of the tool.
With GigaVUE-OS 5.11, A pair of dummy inline tool ports are required to support this feature. Whereas with GigaVUE-OS 5.12 the dummy inline tool ports are not required.
The following Gigamon Validated Design (GVD) illustrates deploying an Inline SSL Decryption solution to offload the TLS decryption without a dummy inline tool ports.
Design Overview
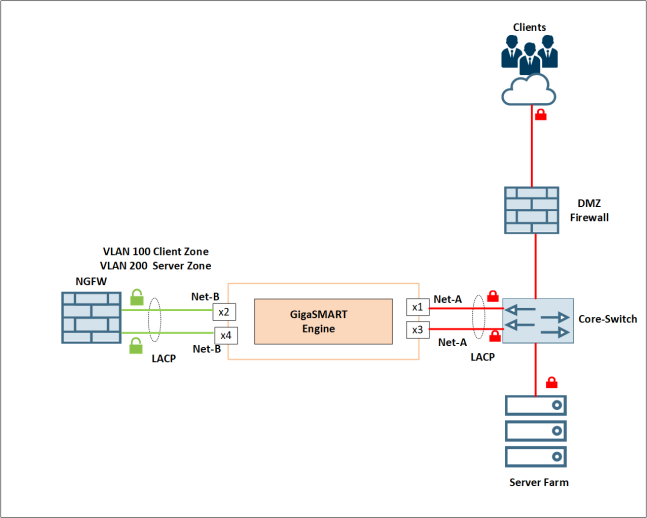
The below example illustrates an enterprise, which has deployed GigaVUE-HC2 to offload the TLS decryption from a Next-generation firewall (NGFW), which is deployed in layer-3 one-armed mode.
The NGFW is deployed with a virtual layer 3 interfaces with multiple links in a port-channel and LACP configured between NGFW and DMZ firewall. It is important to note that these two links are for one-armed mode redundancy and are not configured in the traditional 2 link/2 port model traditionally associated with bump-in-the-wire/virtual wire deployment modes.
The NGFW typically supports many security zones. (In this case, it has two-layer-3 zones)
-
The Client Zone—the default gateway for the client traffic traversing via the DMZ firewall.
-
The Server Zone—the default gateway for the web-application servers in the server farm.
The clients’ traffic is sent to the NGFW for security inspection, which is the default gateway, via the GigaVUE-HC2 device. The NGFW uses its internal routing to forward the traffic destined to Web-application servers in the server zone. The opposite logic applies in the reverse direction.
This use case assumes that the NGFW does not do any NAT or PAT while enforcing the security policy.
Figure 1: GigaSECURE Inline SSL Solution
To learn more about this solution, read complete details on the Gigamon Community: Offloading-TLS-Decryption-for-an-One-armed-Inline-Tool-in-L3-IP-Forwarding-Mode-5-12.