Enabling GigaSECURE TLS Decryption to Offload SSL Inspection from Next-Generation Firewall (6.2)
Introduction
Network segmentation is a widely adapted practice to ensure scalability and security in a network. Often, clients and servers within an enterprise network reside on different network segments. The traffic between the clients and servers may traverse tools, such as a Next-Generation Firewall (NGFW) performing Network address Translation (NAT), Port address translation (PAT) and inter-VLAN routing. Depending on the type of NGFW, the performance could degrade if TLS decryption is enabled in that tool. In such scenarios, it is advisable to offload the TLS decryption from tools to improve the tool's performance. You can also selectively decrypt the traffic for inspection, there by improving the shelf life of the tool.
The following Gigamon Validated Design (GVD) illustrates deploying an Inline SSL decryption solution to offload the TLS decryption from a NGFW for:
-
East-West (E-W) Decryption - To decrypt the traffic destined to internal servers (inbound) from the internal clients. Since this east-west traffic traverses via the Internal network, there is no NAT/PAT enabled on the Firewall.
-
North-South (N-S) Decryption - To decrypt the traffic destined to the Internet (outbound) from the internal clients. A PAT policy is enabled on the Firewall to translate the source IPs of the internal clients with the Firewall Internet zone IP before the traffic is sent to the Internet.
-
South-North (S-N) Decryption - To decrypt the traffic destined to the hosted web application servers (inbound) from the clients on the internet. A Static NAT aka Destination NAT policy is configured on the Firewall to translate the destination address.
Topology Diagram
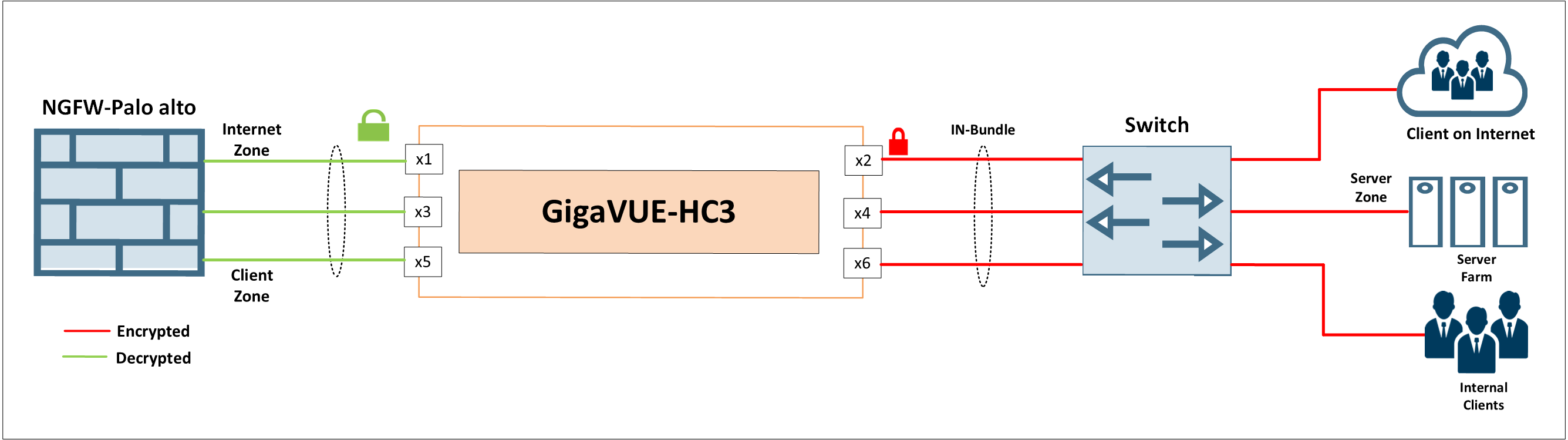
Design Overview
The given example illustrates deployment of GigaVUE-HC3 in an enterprise to offload the TLS decryption from a Next-generation firewall (NGFW), which is deployed in layer-3 mode. An NGFW typically supports many security zones in the network. (In this case, it has three layer-3 zones)
-
The Client Zone—The default gateway for the client traffic traversing to server zone and Internet zone
-
The Server Zone— The default gateway to the web-application servers in the server farm.
-
The Internet Zone — Gateway for the clients from the internet to connect with the web-applications in the server farm.
Note: This design can be applied for Firewalls with multiple interfaces as well as for Firewall with a single physical interface and multiple sub interfaces (aka VLANs).
To learn more about this solution, read complete details on the Gigamon Community: Enabling-GigaSECURE-TLS-Decryption-to-offload-SSL-inspection-from-Next-Generation-Firewall-6-2