Gigamon Precryption™ with Secure Tunnel to Gain Visibility into the Cloud (AWS) Environment (6.4)
Introduction
Nearly 80% of all internet traffic is encrypted and enterprises uses encryption as the primary method for communication. The TLS cryptographic protocol is used to secure an ever-increasing portion of the internet’s web, messaging and application data traffic. Various communication protocols leverage TLS to encrypt and encapsulate their contents—protecting them from being observed or modified in transit. Although this is great for privacy and confidentiality, it creates a serious blind spot for security even though Enterprises spend a lot of money and resources on IT security solutions.
For example, when you download a document from an external website, your firewall or intrusion detection system can inspect the packets of data that come through the local network. But if that communication is happening over an SSL connection, then the system cannot see through the encryption to detect what is really inside the document. It should come as no surprise, by taking advantage of encryption, attackers also been adopting TLS and bypass most inspection devices. It also prevents defenders from detecting / stopping deployment of malware.
To achieve the goal of fully inspecting the traffic for the customers, Gigamon Precryption™ technology delivers plain text visibility of encrypted communications to the full security stack, without the traditional cost and complexity of decryption and thus redefines security for virtual, cloud, and containerized applications. To further secure the precrypted data flow from user workload to the Gigamon fabric, Gigamon has introduced secure tunnels feature that enables secure delivery of the precrypted data.
This GVD focuses on deploying the Gigamon cloud suite with Precryption™ and Secure Tunnel in AWS. It aims to deliver plain text visibility into encrypted traffic, secure the plain text traffic during transit from user workloads to Gigamon fabric, and subsequently forward it to the tools in an out-of-band fashion.
Please check with your Gigamon Sales contact or Gigamon Support for more information regarding the support for the cloud/virtualization platform that you are considering.
Design Topology
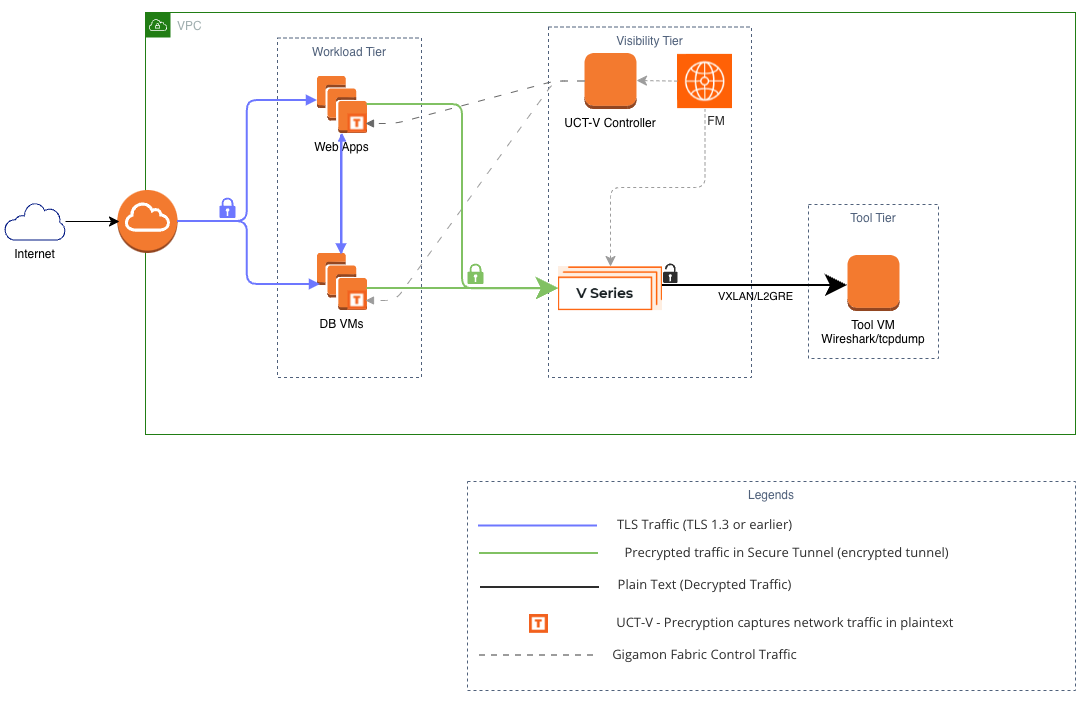
Design Overview
The design outlines the use of the Gigamon Cloud Suite with Precryption™ and Secure Tunnel in AWS to capture traffic in plain text on the user workloads and then securely forward this unencrypted data from user workload to the Gigamon fabric that is the GigaVUE V Series node. Subsequently forward the data from GigaVUE V Series node to the monitoring tools.
Precryption™: Precryption technology leverages native Linux functionality to tap, or copy, communications between the application and the encryption library, such as OpenSSL. It captures network traffic in plaintext, either before it has been encrypted, or after it has been decrypted. The functionality doesn’t interfere with the actual encryption of the message nor its transmission across the network. There’s no proxy, no retransmissions, no break-and-inspect. Instead, this plaintext copy is forwarded to the Gigamon Deep Observability Pipeline for further optimization, transformation, replication, and delivery to tools.
Secure Tunnel: The Secure Tunnel securely transfers the cloud captured packets on UCT-V and UCT-C to a GigaVUE V Series node. The data from UCT-V and UCT-C are encapsulated in PCAPng format, and the encrypted data is sent over a TLS connection to a GigaVUE V Series node.
This design has Workload Tier, Visibility Tier, and the Tool Tier.
-
Workload Tier: Consists of workload VMs which communicate with each other and the internet over TLS 1.3 or earlier, that is the encrypted traffic.
-
Visibility Tier: A typical AWS deployment on a platform utilizes the following Gigamon components to achieve visibility.
-
GigaVUE-FM is the management console to deploy, configure, and troubleshoot the deployment.
-
Fabric Images
-
GigaVUE-V Series Node is a traffic aggregator for monitored EC2 targets that can decapsulate the traffic over Secure Tunnel. It supports various filtering and traffic optimization techniques to sanitize the traffic before forwarding to the tool/s.
-
UCT-V is an agent that is installed in EC2 targets. It enables Precryption on the instances, forward Precrypted and selected mirrored traffic from the instances to the GigaVUE-V Series Node. It also encapsulates the traffic over Secure Tunnel. It is offered as .db and .rpm packages.
-
UCT-V Controller manages and orchestrates UCT-V on multiple instances.
-
-
-
Tool Tier: Consists of the tools. This design uses Wireshark as the monitoring tool.
Within the VPC, GigaVUE FM oversees the deployment of the fabric components, including the GigaVUE V Series node and the UCT-V Controller. The TLS encrypted traffic hitting the EC2 targets is captured in plain text using Precryption enabled by UCT-V. A Secure Tunnel between UCT-V and the V Series node is established over TLS securing the plain text data transfer between the two. The TLS session between UCT-V and V Series node is established by providing CA cert to UCT-V and by providing server cert (signed by this CA) and the private key to V Series node. The CA cert, server cert, and the private key are provided to these components through the FM.
To learn more about this solution, read complete details on the Gigamon Community: Precryption_with_Secure_Tunnel_to_Gain_Visibility_into_the_Cloud_AWS_Environment