Deploying Application Metadata Intelligence
Introduction
The Security Operations Centers heavily depend on the ability to collect, correlate, and analyze network events to quickly identify and respond to security threats. But getting access to the right traffic data from across the network, without overloading the system can be a challenge. Most Security Operations organizations have a broad understanding of the applications that are running on their network. However, many do not have visibility into specific applications that are consuming the resources. While security budgets are stretched thin, organizations struggle to support increased demand. Inefficiencies often result in all traffic being analyzed by all network security tools, whether it is relevant or not.
Application Metadata Intelligence provides detailed metadata information about the applications streaming through a network. In a security context, this is especially useful because security appliances are looking for the “needle in the haystack”; that is, to identify a single sequence of threat packets or flows from the entire mass of network flows without spending all the CPU cycles to process raw traffic. Gigamon Application Metadata, powered by deep packet inspection, provides summarized and context-aware information about raw network packets. It supplies network and security tools with more than 5,000 L4–L7 metadata attributes that shed light on the application’s performance, customer experience, and security.
Application metadata is the simplest and most comprehensive way to obtain application behavior. You can learn critical details of flows, reduce false positives by separating signals from noise, identify nefarious data extraction and accelerate threat detection through proactive, real-time traffic monitoring versus reactive forensics. SIEM solutions, for example, use this information to correlate and analyze log data from servers and security appliances, such as IPS, anti-malware and firewalls.
Easily incorporate metadata elements into your current monitoring and security tools. Gigamon Metadata Intelligence comes with pre-built tool specific templates such as for Splunk and IBM QRadar. You will also benefit from a growing ecosystem of third-party vendors who are integrating Gigamon Application Metadata into their tools for out-of-the-box support for more powerful advanced threat protection and data loss prevention.
Design Topology
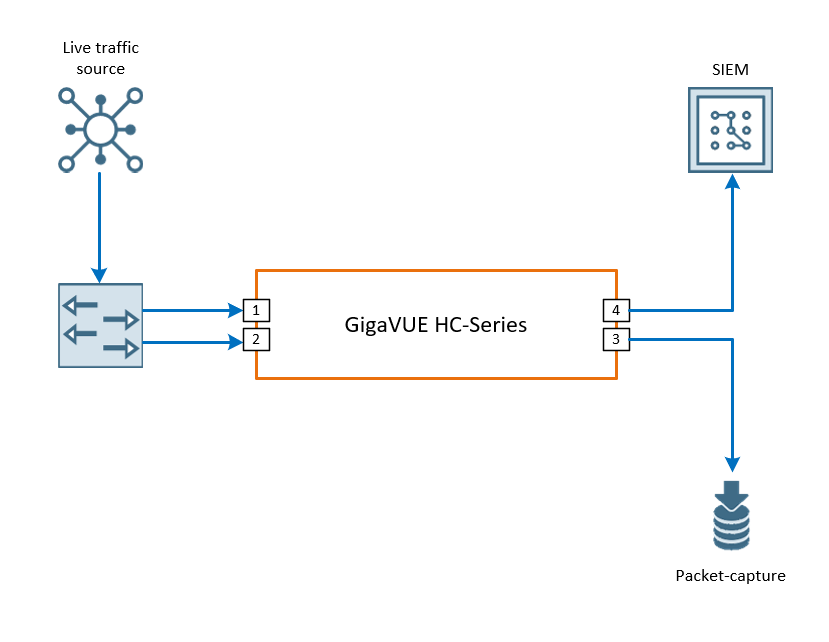
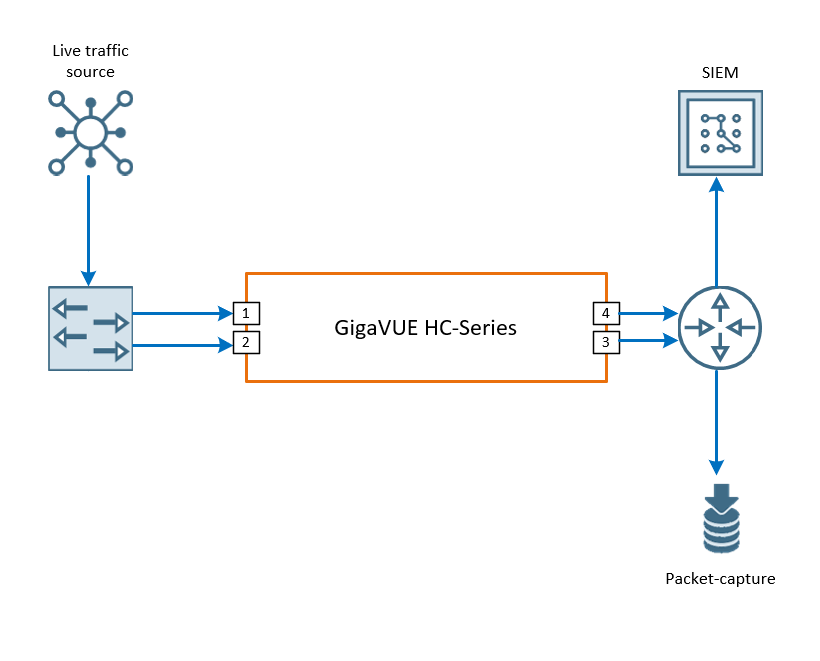
Design Overview
Depending on the security requirements, there can be one or more out-of-band SIEM tools deployed in the network.
To learn more about this solution, read complete details on the Gigamon Community: Deploying_Application_Metadata_Intelligence