Gaining Traffic Visibility into AWS Environments with AWS Gateway Load Balancer and 3rd party Firewall/Inline Devices using VPC mirroring (5.14)
Introduction
Organizations migrate to Public cloud from conventional datacenters for various reasons, such as scalability, agility, low Capex, or to take services closer to their clients etc. In the process, they sometimes encounter operational challenges, such as lack of support for their existing services (for example, security ecosystem including Firewalls, IPS, web proxies and other deep packet inspection services). Adding to this challenge is the abstracted network layer that prevents the technologies used in the physical data center (that were implemented, perfected and imbibed as organization's standards) from being replicated in the cloud infrastructure. With the introduction of AWS Gateway LoadBalancer (GWLB), it is now easy to deploy, scale, and achieve high availability of such partner services in the AWS platform.
Appliances, such as Firewall IPS, etc (referred here as inline security services) inspect the live traffic on the network to verify the organization's network access before redistributing the traffic to the intended destination. Due to the nature of public cloud networking and the partner services performing their actions in transparent mode, the traffic exchange in the Gateway Load Balancer has to rely on a layer of GENEVE encapsulation. In instances where customers need to tap the traffic for out-of-band security inspection, they would find the tapped traffic as GENEVE packets. In order to support all traffic exchange scenarios, Gigamon has introduced the GENEVE decapsulation GigaSMART app. This app enables seamless integration of out-of-band monitoring solutions for AWS deployments with GWLB-enabled partner services.
In this GVD, we will be covering how GigaVUE cloud suite for AWS can be used to acquire traffic from GWLB-enabled services, decapsulate the GENEVE headers in teh traffic, and provide the optimized traffic for further analytics based on customer's business needs.
NOTE: Please check with your Gigamon Sales contact or Gigamon Support for more information regarding support for the cloud/virtualization platform that you are considering.
Design Topology
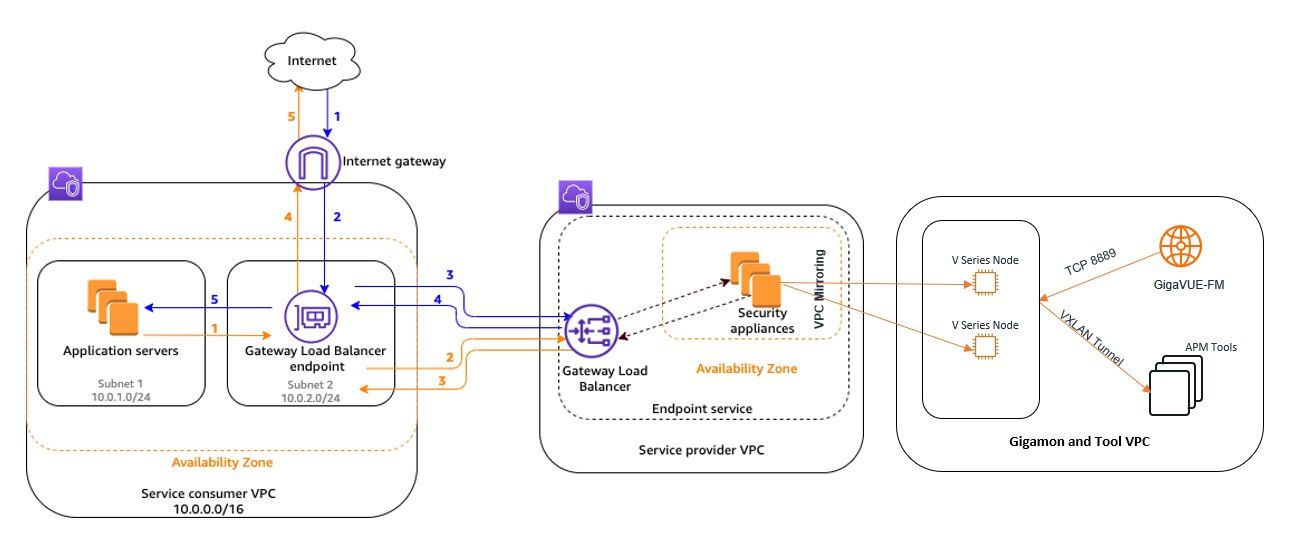
Design Overview
This design depicts the deployment of GigaVUE Cloud Suite for AWS environments that have GWLB implementation for the security appliances, such as firewalls. In such deployments, the applications and the partner appliances are typically in different VPCs, and therefore, in our reference presentation, each entity is present in a separate VPC. The application tiers/customer workload VPC is configured with the Gateway load balancer endpoint while the partner service VPC is configured with the Gateway load balancer. Gigamon deployed VPC has the solution components, such as GigaVUE FM, V Series Nodes, and the OOB tools which consume the mirrored and decapsulated data. Note that the customer application data flow has been denoted by numbered (request) and (response) lines while Gigamon-acquired traffic flow is denoted by Orangelines for easier distinction.
This design includes monitoring of all the traffic from the security appliances as well as the service provider VPC. For traffic that is being mirrored from a partner service appliance, it may not always be feasible to use the GvTAP agents and hence, we would recommend to leverage the VPC mirroring functionality on AWS.
A typical Gigamon AWS deployment consists of the following cloud suite components:
- GigaVUE-FM (Fabric Manager): It provides an unified interface to deploy, configure, and troubleshoot the Gigamon solution.
- GigaVUE-V Series Node version 2.4.0: This is the traffic aggregator for the EC2 targets that support VPC mirroring. It supports various filtering and traffic optimization techniques to sanitize the traffic before forwarding to the tools.
WTo learn more about this solution, read complete details on the Gigamon Community: Gaining Traffic Visibility into AWS Environments with AWS Gateway Load Balancer and 3rd-party Firewall Inline Devices using VPC Mirroring 5.14.