Deploying TA200 as an Inline Aggregator to Enable Enforcing Uniform Security Policies (5.14)
Introduction
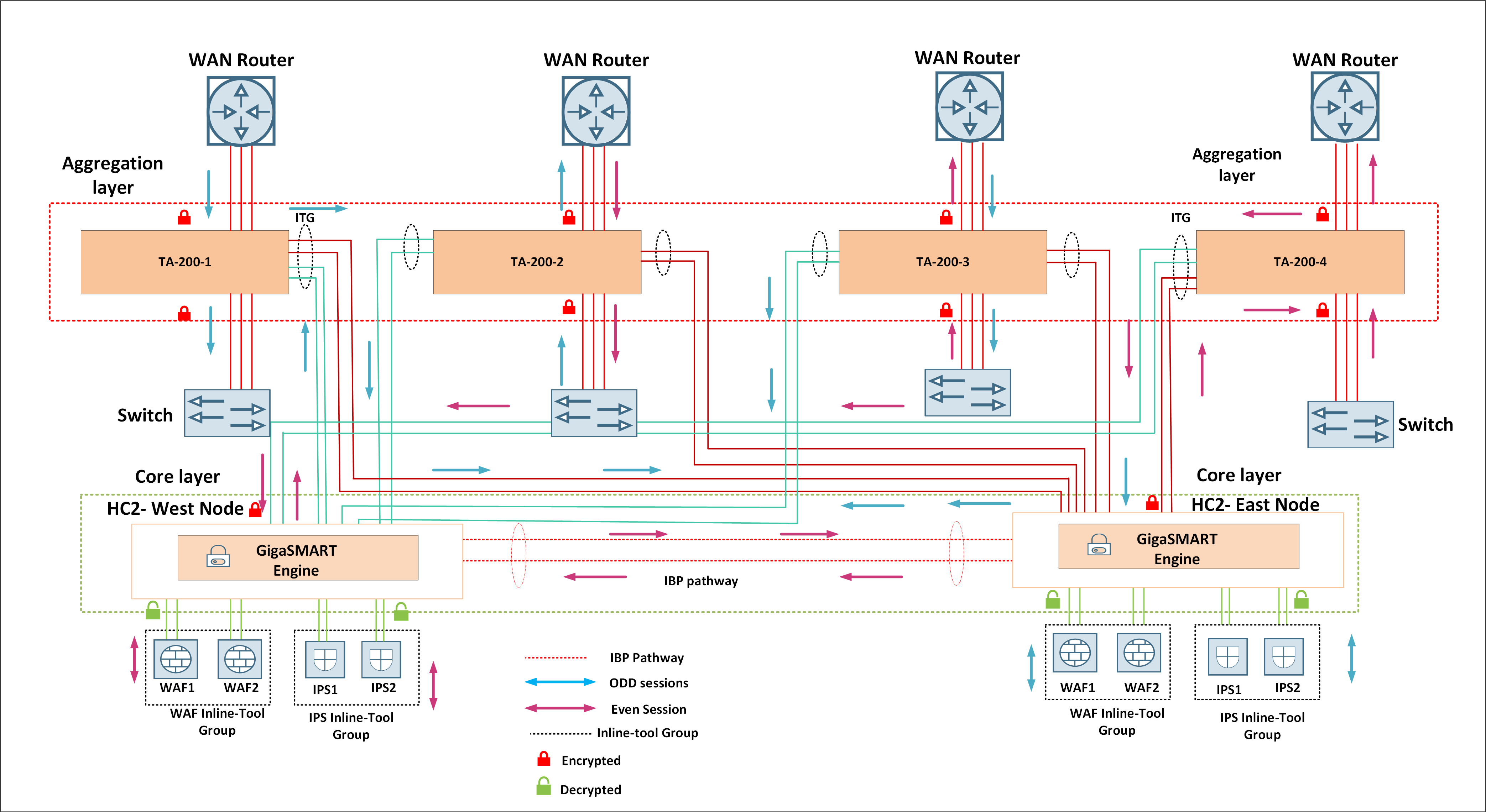
Multi-path redundant networks can pose different challenges to the security monitoring tools. Firstly, the upstream and downstream traffic that are part of the same session could traverse along different paths (asymmetric traffic). When you have an inline tool inspecting the asymmetric traffic, the tool may not receive the complete session thus creating a black hole. Secondly, as the network grows, the inline traffic may have to be aggregated in order to apply uniform security policies. Gigamon's inline bypass solution resolves the challenge with asymmetric traffic flow by forwarding the same flows to a single tool irrespective of the network paths they traverse. In addition, Gigamon inline bypass solutions can be deployed in a tiered fashion to resolve the second issue. The following Gigamon Validated Design (GVD) illustrates one such scenario.
Watch this quick video to learn more about the challenges with asymmetric flow of traffic in a network.
Design Overview
This design illustrates deploying the Gigamon devices in tiers as follows:
-
Aggregation Layer: Consists of GigaVUE-TA-200 to aggregate and forward the inline traffic to the core layer for applying the common security policies.
-
Core Layer: Consists of a pair of GigaVUE-HC2 devices that are deployed, one on each path, to normalize the asymmetric traffic, decrypt it using Gigamon's Inline SSL solution, and forward it to pairs of IPS and WAF for inspection. The inspected traffic is encrypted by the Gigamon devices and forwarded to the aggregation layer to be mapped further.
To learn more about this solution, read complete details on the Gigamon Community: Deploying TA200 as an Inline Aggregator to Enable Enforcing Uniform Security Policies 5.14.