Introduction
In multi-path redundant networks, asymmetric routing is inherent because upstream and downstream traffic that belongs to the same session can traverse in different paths. When you have an inline tool to inspect both the paths, the tool may not receive the full session creating a black hole and this can affect the inspection. Gigamon's Resilient Inline solution lets an inline tool to receive all traffic thereby improving detection. A Resilient Inline Arrangement can be achieved by deploying two Gigamon H Series devices inline along the network path and connecting each other devices through an Inter-Broker Pathway. However, there could be some dependencies with existing tools that need to be managed. By default, Gigamon's Resilient Inline solution appends VLAN IDs to network traffic before guiding relevant traffic to the tools. If your network traffic is already tagged, the tools will receive Q-in-Q traffic. You have a tool that does not support inspecting such traffic.
Gigamon's Resilient inline with the Single Tag feature lets you map between network and tool tag so that the tool always receives single-tagged traffic; the Inline Bypass solution replaces the network tag with tool tag before forwarding traffic to the tool and replaces the tool tag with network tag while forwarding traffic to the network.
Design Overview
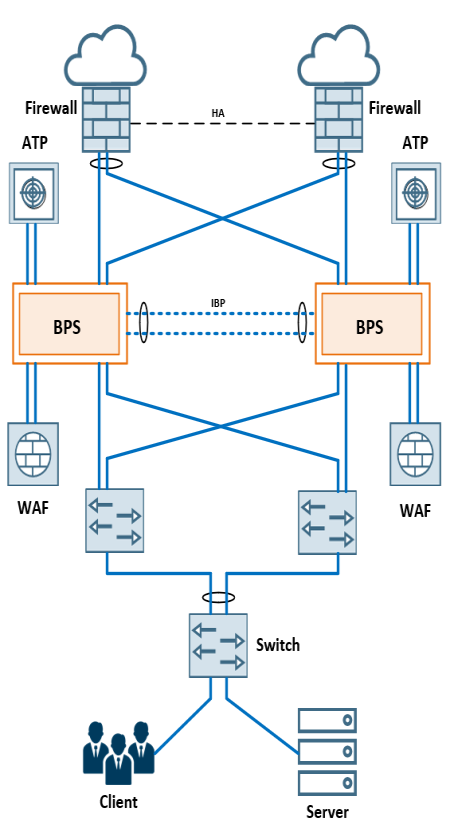
The design illustrates two firewalls deployed in a High Availability Active-Active mode for inspecting traffic to/from the internet, a Web Application Firewall (WAF) and an Advanced Threat Prevention (ATP) tool connected to a Gigamon H Series device along each network path for traffic inspection. Each Gigamon device is connected to the other through an Inter-Broker Pathway.
Figure 1: Topology to Inspect Networks with Asymmetric Routing
To learn more about this solution, read complete details on the Gigamon Community: Inspecting-Networks-with-Asymmetric-Routing-5-10.