Configure Role-Based Access for Third Party Orchestration
Before deploying the fabric components using a third party orchestrator, we must create users, roles and the respective user groups in GigaVUE-FM. The Username and the Password provided in the User Management page will be used in the registration data that can be used to deploy the fabric components in your orchestrator.
Users
The Users page lets you manage the GigaVUE-FM and GigaVUE-OS FM users. You can also configure user's role and user groups to control the access privileges of the user in GigaVUE-FM.
Add Users
This section provides the steps for adding users. You can add users only if you are a user with fm_super_admin role or a user with either read/write access to the FM security Management category.
Important: It is recommended to create users through GigaVUE‑FM:
| You cannot view or manage users created in GigaVUE‑FM CLI using GigaVUE‑FM. |
| You cannot view changes made to the users in GigaVUE‑FM CLI in GigaVUE‑FM. |
Note: Monitor and operator users are not available in GigaVUE‑FM. However, if you upgrade from a previous version in which monitor/operator users have been mapped in map default user, then after upgrade:
| In AAA: Users authenticated through the external servers will be assigned the fm_user role. |
| In LDAP: Remote group based DN entry will not be migrated. |
To add users perform the following steps:
| 1. |
On the left navigation pane, click |
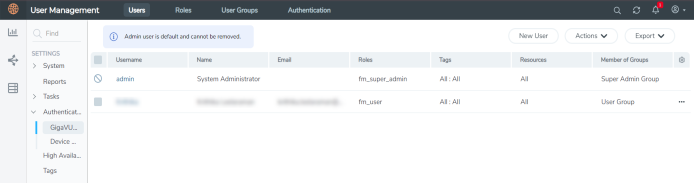
| 1 | FM Users Page |
| 2. | Click New User. In the Add User wizard that appears perform the following steps. |
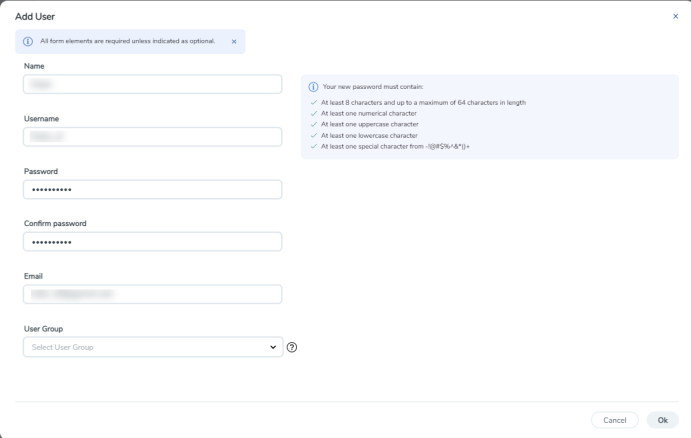
| 2 | Create User |
| a. | In the Add User pop-up box, enter the following details: |
| Name: Actual name of the user |
| Username: User name configured in GigaVUE-FM |
| Email: Email ID of the user |
| Password/Confirm Password: Password for the user. Refer to the Change Your Password section. |
| User Group: User group |
Note: GigaVUE‑FM will prompt for your password.
| b. | Click Ok to save the configuration. |
The new user is added to the summary list view.
You can also assign users to roles and user groups that set the access permissions. Refer to the following sections for details:
Note: If you have logged in as a user with fm_super_admin role or a user with either read/write access on FM security Management category, then click on the ellipsis to:
| Assign User Group: Assign user group to users. |
| Edit: Edit the user details. |
| Delete: Delete a user. |
| Unlock: Unlock a locked user. |
How to Unlock User Account
To unlock a locked user, you must be a user with fm_super_admin role or a user with either read/write access on FM security Management category.
To unlock:
- Select the required user whose account you want to lock.
- Click on the ellipses and select Unlock. You can also click the Actions drop-down button and select Unlock.
- A notification message prompts up. Click Unlock to unlock the user.
The user account is unlocked. An event is triggered in the Events page, and an email will be sent if Email Notification settings are configured.
The User name and password provided in this section will be used as the User and Password in the registration data.
After adding User, you must configure roles for third party orchestration.
Create Roles
You can associate a role with user. Under the Select Permissions tab select Third Party Orchestration and provide read/write permissions.
Create Roles
This section describes the steps for creating roles and assigning user(s) to those roles.
GigaVUE‑FM has the following default roles:
| fm_super_admin — Allows a user to do everything in Fabric Manager, including adding or modifying users and configuring all AAA settings in the RADIUS, TACACS+, and LDAP tabs. Can change password for all users. |
| fm_admin — Allows a user to do everything in Fabric Manager except add or modify users and change AAA settings. Can only change own password. |
| fm_user — Allows a user to view everything in Fabric Manager, including AAA settings, but cannot make any changes. |
Note: If you are a user with read-only access you will be restricted from performing any configurations on the screen. The menus and action buttons in the UI pages will be disabled appropriately.
Starting in software version 5.7, you can create custom user roles in addition to the default user roles in GigaVUE‑FM. Access control for the default roles and the custom roles is based on the categories defined in GigaVUE‑FM. These categories provide the ability to limit user access to a set of managed inventories such as ports, maps, cluster, forward list and so on.
Refer to the following table for the various categories and the associated resources. Hover your mouse over the resource categories in the Roles page to view the description of the resources in detail.
|
Category |
Associated Resources |
|||||||||||||||||||||||||||
|
All |
Manages all resources
|
|||||||||||||||||||||||||||
|
Infrastructure Management |
Manages resources such as devices, cards, ports and cloud resources. You can add or delete a device in GigaVUE‑FM, enable or disable cards, modify port parameters, set leaf-spine topology. The following resources belong to this category:
Note: Cloud APIs are also RBAC enabled.
|
|||||||||||||||||||||||||||
|
Traffic Control Management |
Manages inline resources, flow maps, GigaSMART applications, second level maps, map chains, map groups. The following resources belong to this category:
Note: Cloud APIs are also RBAC enabled. |
|||||||||||||||||||||||||||
|
FM Security Management |
Ensures secure GigaVUE‑FM environment. Users in this category can manage user and roles, AAA services and other security operations. |
|||||||||||||||||||||||||||
|
System Management |
Controls system administration activities of GigaVUE‑FM. User in this category are allowed to perform operations such as backup/restore of GigaVUE‑FM and devices, and upgrade of GigaVUE‑FM. The following GigaVUE‑FM resources belong to this category:
|
|||||||||||||||||||||||||||
|
Forward list/CUPS Management |
Manages the forward list configuration. The following resources belong to this category:
|
|||||||||||||||||||||||||||
|
Third Party Orchestration |
Used to deploy fabric components using external orchestrator. | |||||||||||||||||||||||||||
|
Device Certificate Management |
Manages device certificates. |
|||||||||||||||||||||||||||
|
Other Resource Management |
Manages virtual and cloud resources |
You can associate the custom user roles either to a single category or to a combination of categories based on which the users will have access to the resources. For example, you can create a ‘Physical Devices Technician’ role such that the user associated with this role can only access the resources that are part of the Physical Device Infrastructure Management.
Note: A user with fm_admin role has both read and write access to all of the categories, but has read only access to the FM Security Management category.
To create a role
| 1. |
On the left navigation pane, click |
| 2. | Click New Role. |
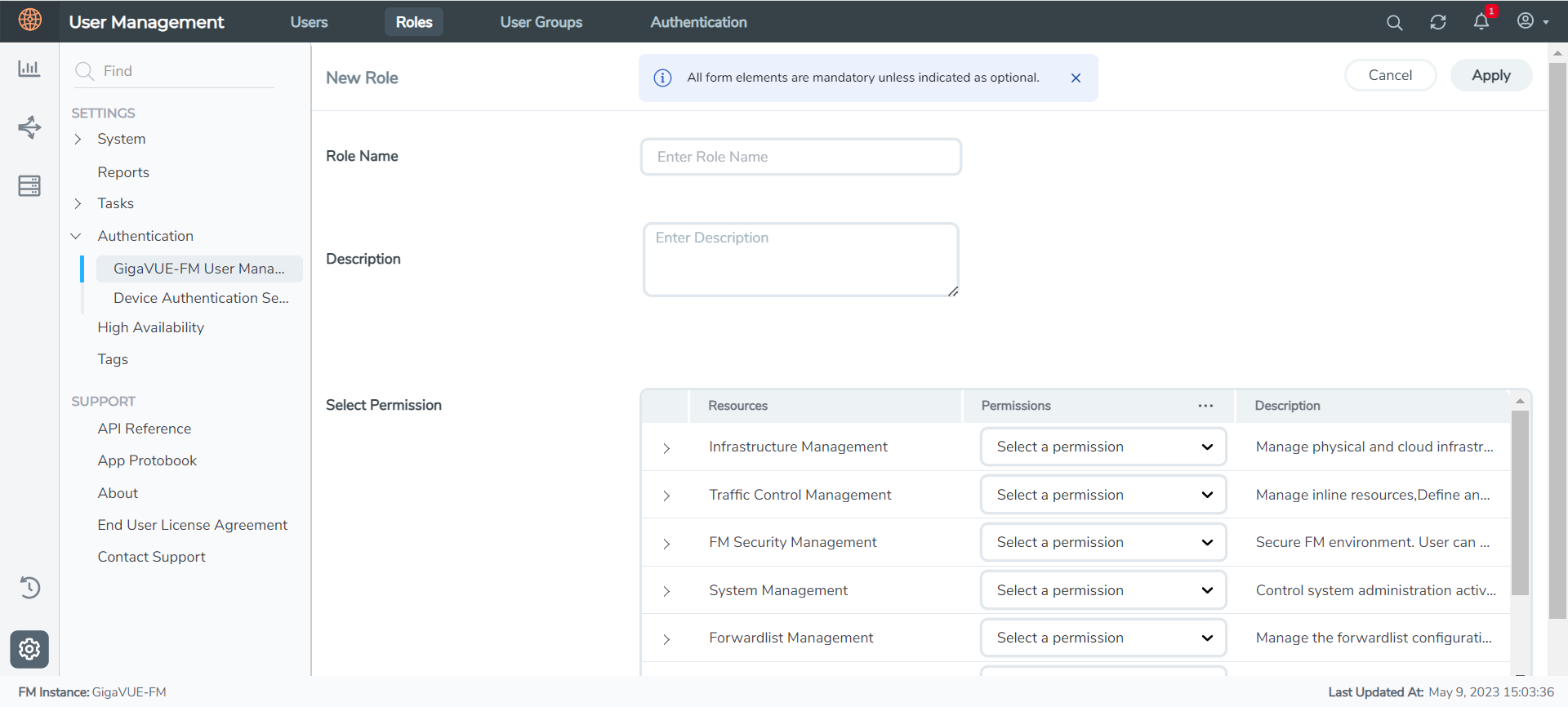
| 3. | In the New Role page, select or enter the following details: |
- Role Name: Name of the role.
- Description: Description of the role.
- Select Permission: In the Select Permission table, select the required permission for the various resource categories.
| 4. | Click Apply to save the configuration. |
Create User Groups
You can use the user group option to associate the users with Roles and Tags. A user group consists of a set of roles and set of tags associated with that group. When a user is created they can be associated with one or more user groups.
Create User Groups
Starting in software version 5.8.00, you can use the user group option to associate the users with Roles and Tags. A user group consists of a set of roles and set of tags associated with that group. When a user is created they can be associated with one or more user groups.
The following user groups are available by default in GigaVUE‑FM. You will not be able to edit or change these groups in the system.
|
User Group |
Tag Key and Tag Value |
Permission |
|---|---|---|
|
Super Admin Group |
Tag Key = All Tag Value = All |
Group with privileges of fm_super_adminrole. |
|
Admin Group |
Tag Key= All Tag Value = All |
Group with privileges of fm_admin role. |
|
View only user |
Tag Key = All Tag Value = All |
Group with privileges of fm_user role. |
By creating groups and associating to tags and roles, you can control the users of the following:
- The category of resources which the user can access, such as the clusters, ports, maps and so on. This is defined using the Roles option. Refer to the Roles section for more details.
- The physical and logical resources that the user can access, such as the ports in a cluster that belong to a specific department in a location. This is defined using the Tags option.
Refer to the following flow chart to see how access control operation occurs when the user accesses a resource:
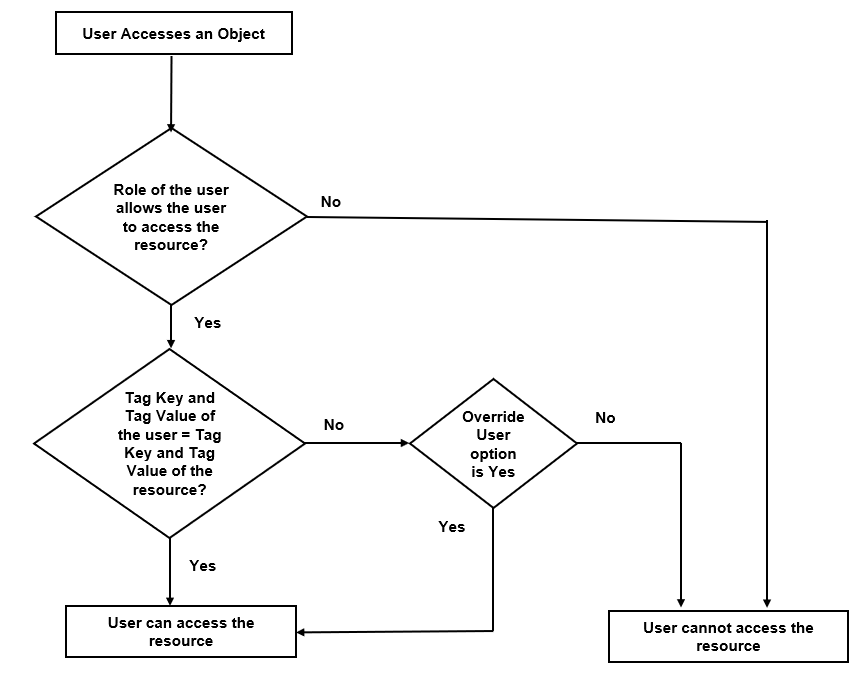
To create a user group:
| 1. |
On the left navigation pane, click |
| 2. | Click New Group. In the Wizard that appears, perform the following steps. Click Next to progress forward and click Back to navigate backward and change the details. |
| 3. | In the Group Info tab, enter the following details: |
- Group Name
- Description
| 4. | In the Assign Roles tab, select the required role. |
| 5. | In the Assign Tags tab, select the required tag key and tag value. |
| 6. | In the Assign Users tab, select the required users. Click Apply to save the configuration. Click Skip and Apply to skip this step and proceed without adding users. |
The new user group is added to the summary list view.
Click on the ellipses to perform the following operations:
| Modify Users: Edit the details of the users. |
| Edit: Edit an existing group. |



