Configure UCT-C Features
This section walks you through enabling key UCT-C features to enhance traffic visibility and security.
For details, refer to the following sections:
Configure Precryption in UCT-C
GigaVUE-FM allows you to enable or disable the Precryption feature.
Rules and Notes
Memory limits for UCT-C:
| The memory limit changes depending on the number of vCPUs in the worker node. For example, if the worker node has 16 vCPUs, the Precryption feature consumes around 1GB of memory (16 * 64 MB). |
| Secure tunnels require additional (16 *64 MB) memory. Hence, the total memory that you must allocate for the TAP is 1 GB. |
| Use the PRECRYPTION_RING_BUFFER_MEMORY_MB field in the YAML file to configure the memory allocation. |
| UCT-C supports both the protocol version IPv4 and IPv6. |
| To use IPv6 tunnels, your GigaVUE‑FM and the fabric components version be 6.6.00 or above. |
The YAML configuration option allows you to choose the amount of buffer size.
To configure the Precryption feature in UCT-C, follow the steps listed in Configure Traffic Policy.
Note: You can deploy only one Precryption policy per Monitoring Domain.
After enabling the Precryption, configure the Create Source Selectors, and the Rules.
Selective Precryption
GigaVUE-FM allows you to filter packets during the Precryption in the Data Acquisition at the UCT-C level. This filtering is performed according to the L3/L4 5 tuple information (5-tuple filtering) running on the containers.
For details on how to configure Selective Precryption when configuring the Rules, refer to Enable Selective Precryption.
Enable Selective Precryption
If you wish to use selective Precryption, follow these steps:
| 1. | Disable the Enable toggle button to turn off the default passall rule. |
| 2. | Select  to add another rule. to add another rule. |
| 3. | Enter the name of the rule and choose Pass (passes the traffic) or Drop (drops the traffic) in Action menu. |
Note: In the absence of a Precryption rule, traffic is implicitly allowed. However, once rules are defined, they include an implicit pass all rule. If the traffic is not conformed to any of the specified rules, it will be passed.
| 4. | Select one of the following directions: |
| • | Bi-directional: Allows the traffic in both directions of the flow. A single Bi-direction rule should consist of 1 Ingress and 1 Egress rule. |
| • | Ingress: Filters the traffic that flows in. |
| • | Egress; Filters the traffic that flows out. |
| 5. | Select the value of the priority. The value helps to prioritize the rules must for filtering. Select the value as 1 to pass or drop a rule in top priority. Similarly, you can select the value as 2, 3, 4 to 8, where 8 is for setting a rule with the least priority. You can add Drop rules based on the priority and, then add pass rules. |
| 6. | Select the required Filter Type (L3 or L4). |
| a. | For L3: |
Select the required Filter Name. The available options are IPv4 Source, IPv4 Destination, IPv6 Source, IPv6 Destination, and Protocol (common for both IPv4 and IPv6).
Enter or select the Filter Value based on the selected Filter Name.
Note: When using Protocol as the Filter Name, select TCP from the drop-down menu.
| b. | For L4: |
Select the required Filter Name. The available options are Source Port and Destination Port.
Select the Filter Relation. The available options are Not Equal to and Equal to.
Enter the source or destination port value.
Configure Secure Tunnels in UCT-C
You can configure Secure tunnel on:
Precryption Traffic
Mirrored Traffic
You can enable the Secure Tunnel for mirrored traffic. By default, Secure Tunnel is disabled.
Prerequisites
While creating Secure Tunnel, you must provide the following details:
| SSH key pair |
| CA certificate |
Configure Secure Tunnels from UCT-C Container to GigaVUE V Series Node
To configure a secure tunnel in a UCT-C Container, you must configure one end of the tunnel to the UCT-C and the other end to a GigaVUE V Series node. You must configure CA certificates in UCT Container, and the private keys and SSL certificates in the GigaVUE V Series Node. Refer to the following steps for configuration:
| 1. | Upload a Custom Certificate: |
| a. | You must upload a CA to UCT-C Container for establishing a connection with the GigaVUE V Series node. |
| b. | Go to Inventory > Resources > Security > CA List. |
| c. | Select Add. The Add Certificate Authority page appears. |
| d. | Enter the Alias and choose the certificate from the desired location. |
| e. | Select Save. For more information, refer to Adding Certificate Authority. |
| 2. | Upload an SSL Key: To add an SSL Key to GigaVUE V Series node, follow the steps in the section |
| 3. | Select the SSL Key when you create a Monitoring Domain and configure the fabric components in GigaVUE-FM. |
| 4. | Select the CA certificate when you create a monitoring domain and configuring the fabric components in GigaVUE-FM. To select the CA certificate, follow the steps in Create Monitoring Domain. |
| 5. | Create and add the secure tunnel when you configure the traffic policy. For details, refer to Configure Traffic Policy. |
Adding Certificate Authority
The Certificate Authority (CA) List page allows you to add the root CA for the devices.
To upload the CA using GigaVUE-FM, follow these steps:
- Go to Inventory > Resources > Security > CA List.
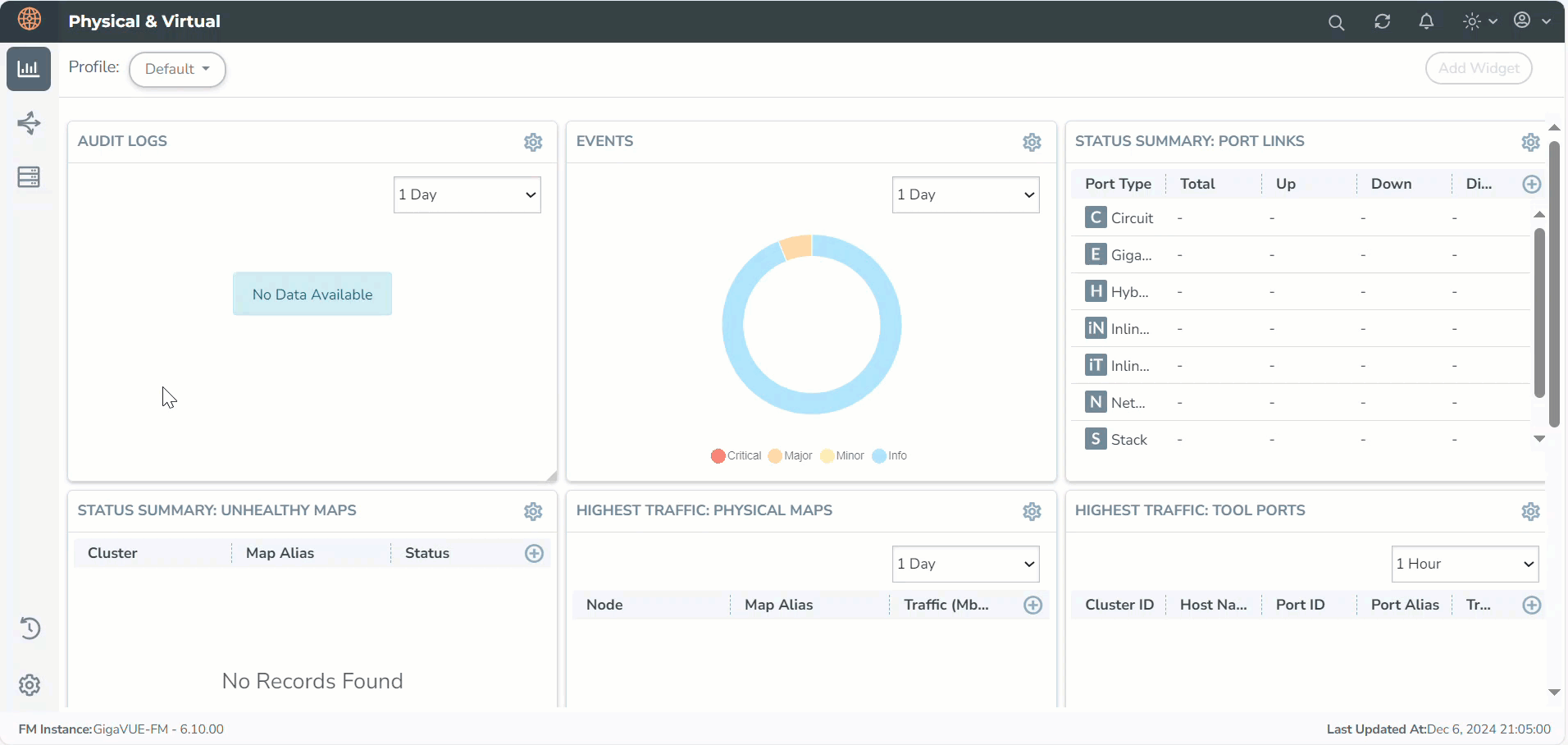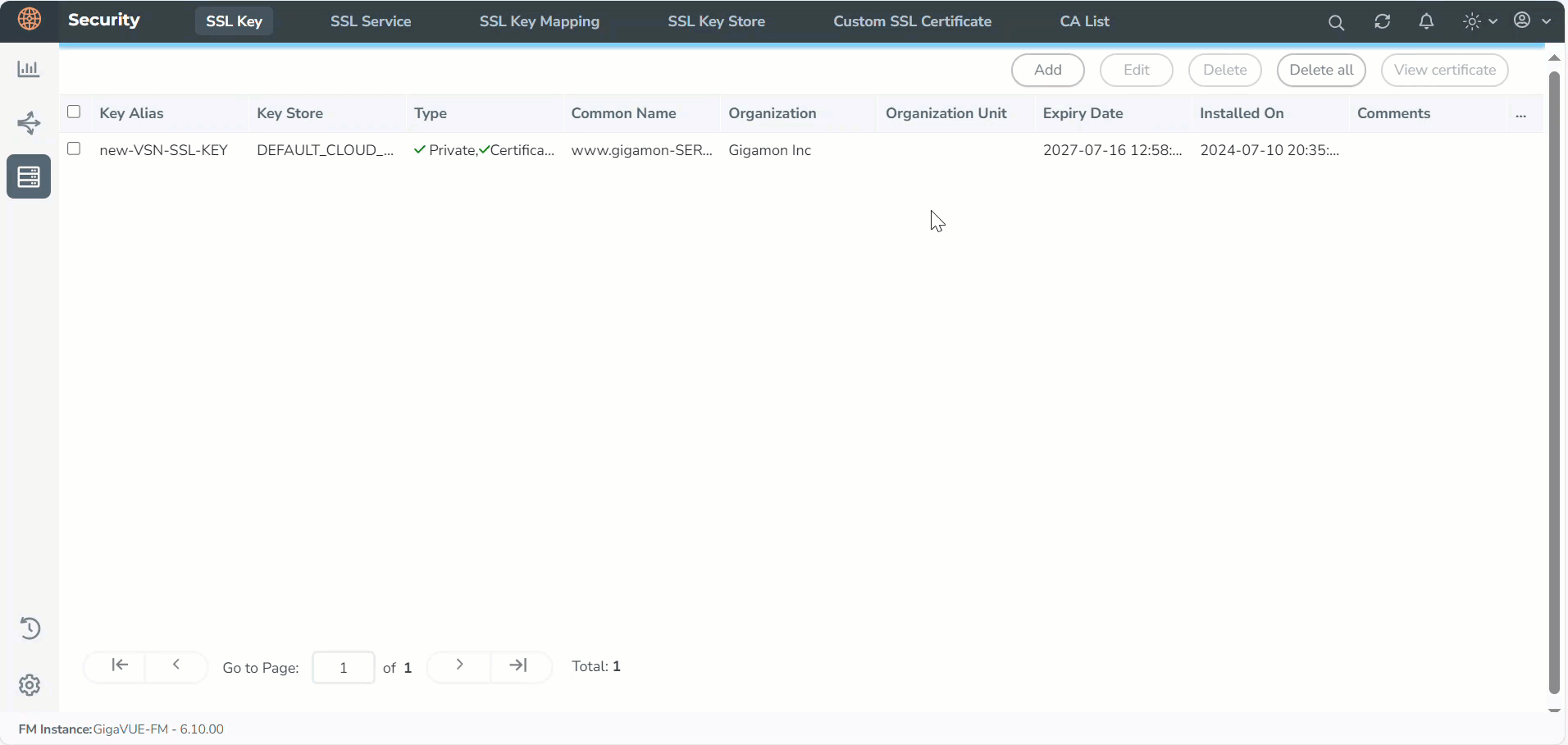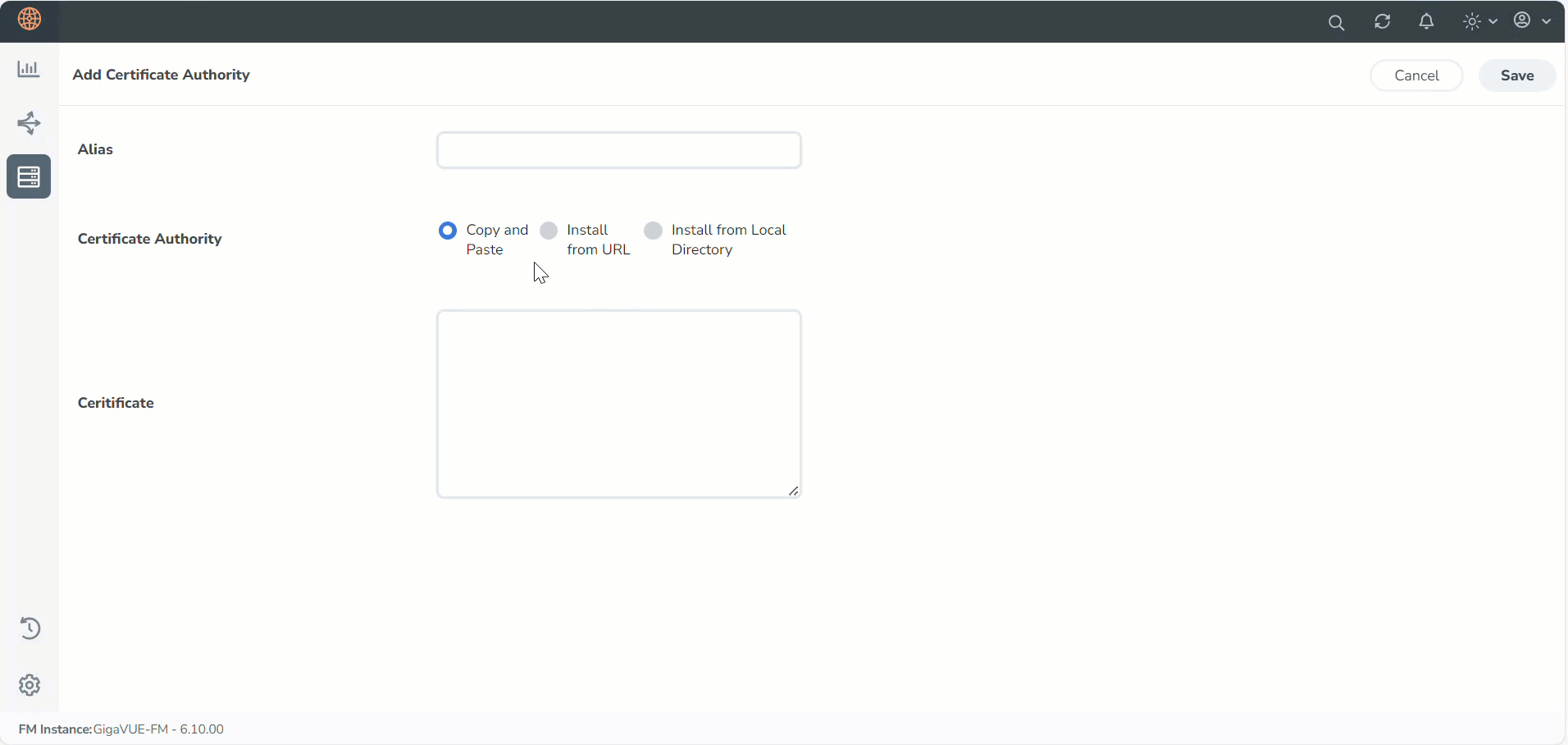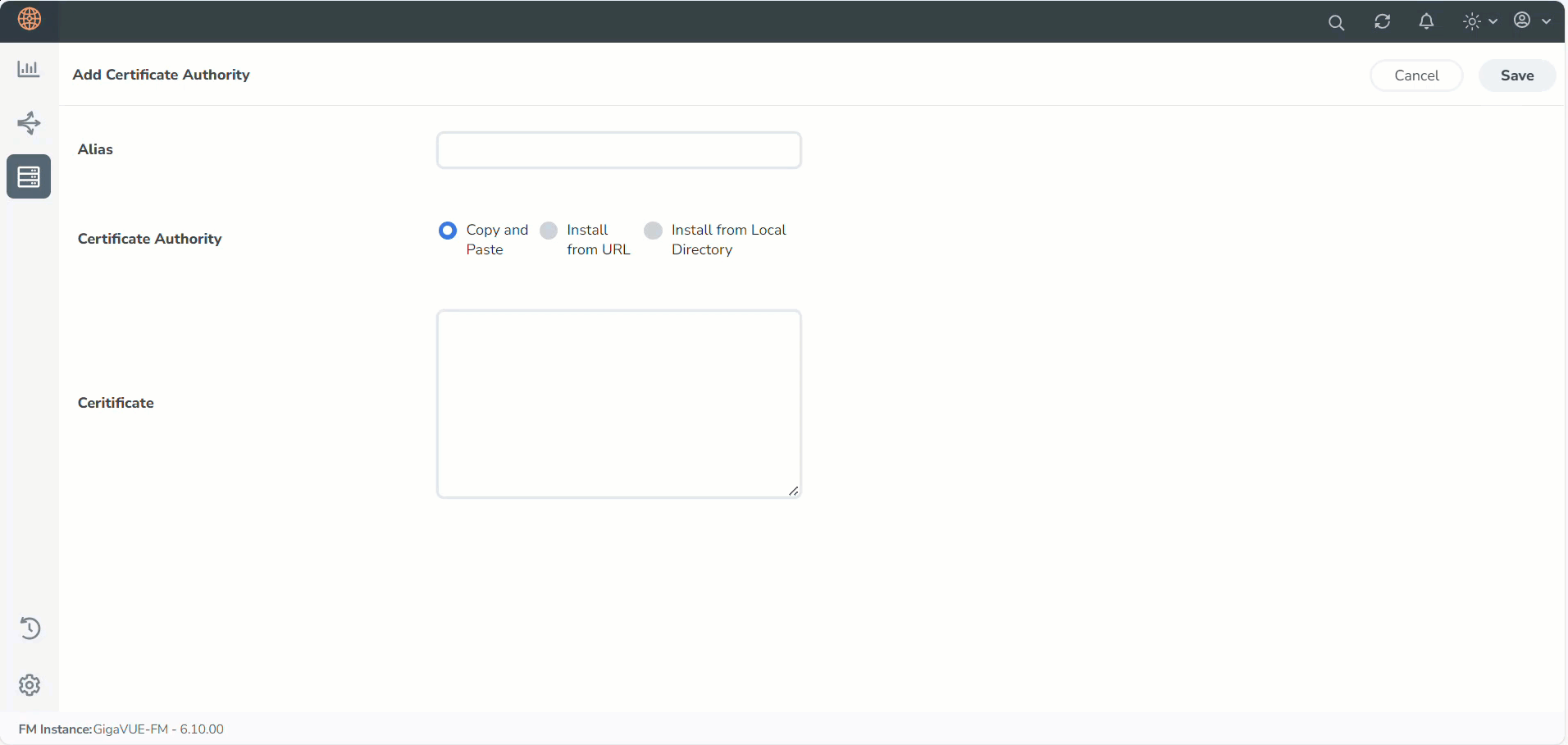
- Select Add, to add a new Custom Authority.
The Add Certificate Authority page appears. - In the Alias field, enter the alias name of the Certificate Authority
- Use one of the following options to enter the Certificate Authority:
- Copy and Paste: In the Certificate field, enter the certificate.
- Install from URL: In the Path field, enter the URL in the format: <protocol>://<username>@<hostname/IP address>/<file path>/<file name>. In the Password field, enter the password.
- Install from Local Directory: Select Choose File to browse and select a certificate from the local directory.
- Select Save.



