Configure GigaVUE Fabric Components in GigaVUE‑FM
After configuring the Monitoring Domain, you reach the Azure Fabric Launch Configuration page. In the same page, you can configure all the GigaVUE fabric components.
Enter or select the required information as described in the following table:
|
Fields |
Description |
|
Connections |
A connection that you created in the monitoring domain page. For details, refer to Create Monitoring Domain. |
|
Centralized Virtual Network |
Alias of the centralized VNet in which the UCT-V Controllers, V Series Proxies, and the GigaVUE V Series nodes are launched. |
|
Authentication Type |
Select SSH Public Key as the Authentication Type to connect with the Centralized VNet. |
|
SSH Public Key |
The SSH public key for the GigaVUE fabric components. |
|
Resource Group |
The Resource Groups created in Azure for communication between the controllers, nodes, and GigaVUE-FM. |
|
Security Groups |
The security group created for the GigaVUE fabric components. |
|
Enable Custom Certificates |
Enable this option to validate the custom certificate during SSL Communication. GigaVUE‑FM validates the Custom certificate with the trust store. If the certificate is not available in Trust Store, communication does not happen, and a handshake error occurs. Note: If the certificate expires after the successful deployment of the fabric components, then the fabric components moves to failed state. |
|
Certificate |
Select the custom certificate from the drop-down menu. You can also upload the custom certificate for GigaVUE V Series Nodes, GigaVUE V Series Proxy, and UCT-V Controllers. For details, refer to Secure Communication between GigaVUE Fabric Components. |
|
Prefer IPv6 |
Enables IPv6 to deploy all the Fabric Controllers, and the tunnel between hypervisor to GigaVUE V Series Nodes using IPv6 address. If the IPv6 address is unavailable, it uses an IPv4 address. Note: This option can be enabled only when deploying a new GigaVUE V Series Node. If you wish to enable this option after deploying the GigaVUE V Series Node, then you must delete the existing GigaVUE V Series Node and deploy it again with this option enabled. |
|
Select Yes to configure V Series Proxy for the monitoring domain. For details, refer to Configure GigaVUE V Series Proxy |
|
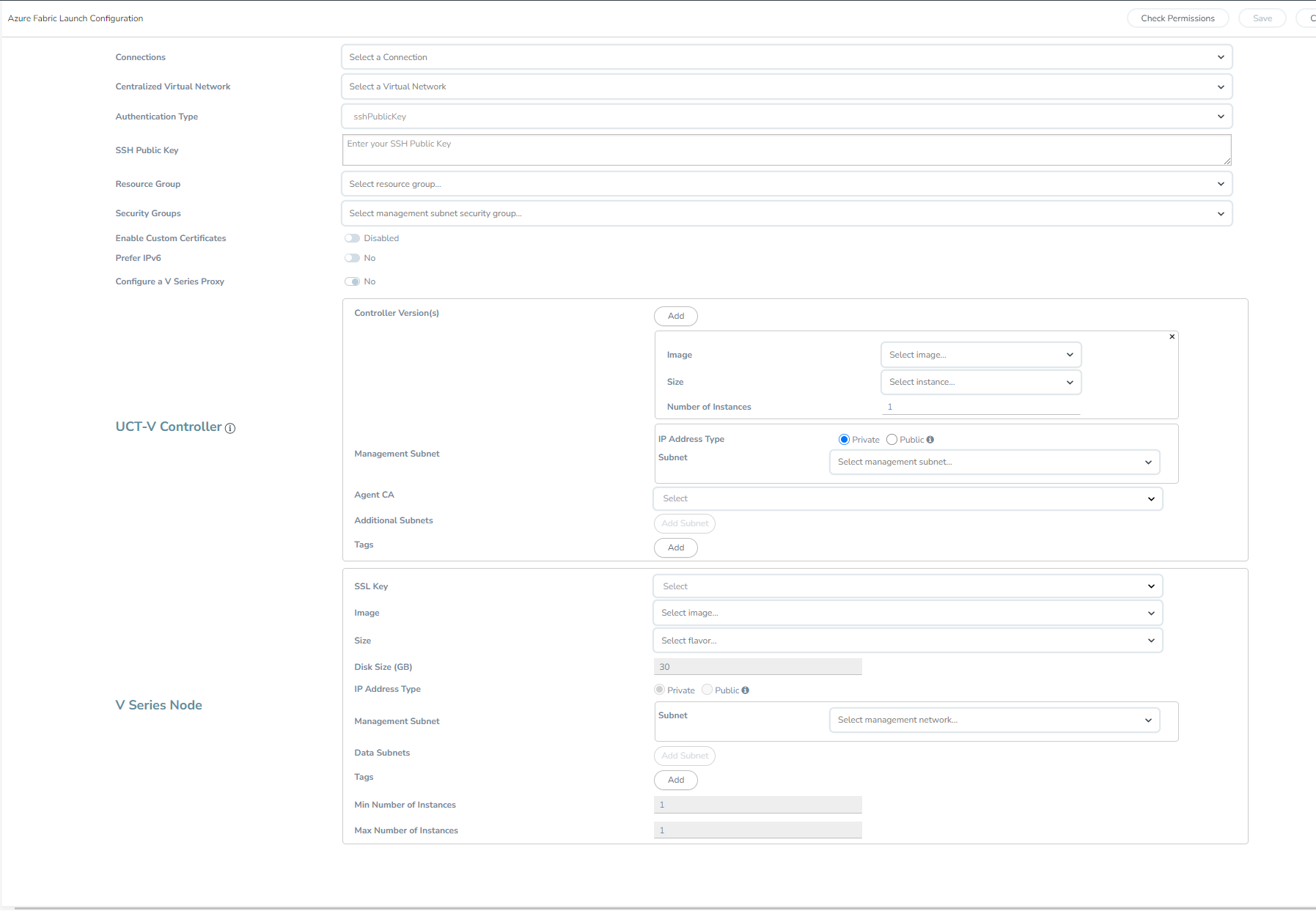
For details, refer to the following topics:
Configure UCT-V Controller
A UCT-V Controller manages multiple UCT-Vs and orchestrates the flow of mirrored traffic to GigaVUE V Series nodes.
Note: A single UCT-V Controller can manage up to 500 UCT-Vs. The recommended minimum instance type is Standard_B4ms for UCT-V Controller.
A UCT-V Controller can only manage UCT-Vs that has the same version.
To configure the UCT-V Controllers,
Note: You can configure UCT-V Controller only if your Traffic Acquisition Method is UCT-V.
In the Azure Fabric Launch Configuration page, enter or select the appropriate values for the UCT-V Controller as described in the following table.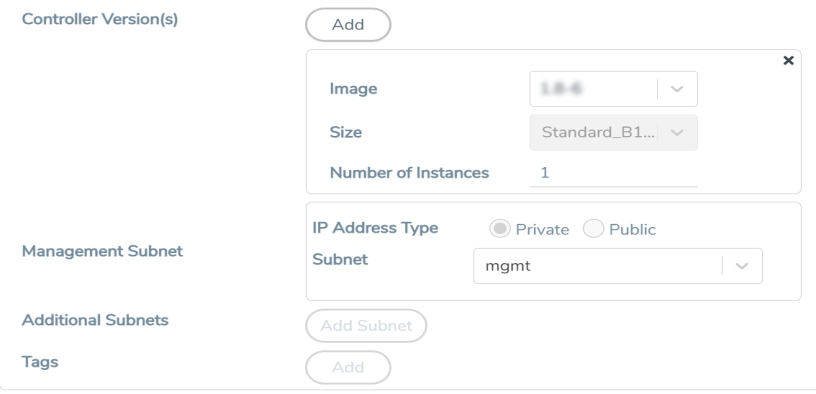
Configure GigaVUE V Series Proxy
GigaVUE V Series Proxy can manage multiple GigaVUE V Series Nodes and orchestrates the flow of traffic from GigaVUE V Series nodes to the monitoring tools. GigaVUE-FM uses one or more GigaVUE V Series Proxies to communicate with the GigaVUE V Series nodes.
Note: A single GigaVUE V Series Proxy can manage up to 100 GigaVUE V Series nodes. The recommended minimum instance type is Standard_B1s for V Series Proxy.
To configure the GigaVUE V Series Proxy,
- In the Azure Fabric Launch Configuration page, select Yes to Configure a V Series Proxy. The GigaVUE V Series Proxy fields appears.
- Enter or select the appropriate values for the V Series Proxy. For details, refer to the UCT-V Controller field descriptions.
Configure GigaVUE V Series Node
GigaVUE V Series node is a visibility node that aggregates mirrored traffic from multiple UCT-Vs. It applies filters, manipulates the packets using GigaSMART applications, and distributes the optimized traffic to cloud-based tools or backhaul to GigaVUE Cloud Suite for Azure using the standard VXLAN tunnels.
To launch a GigaVUE V Series node:
In the Azure Fabric Launch Configuration page, enter or select the appropriate values for the GigaVUE V Series Node. 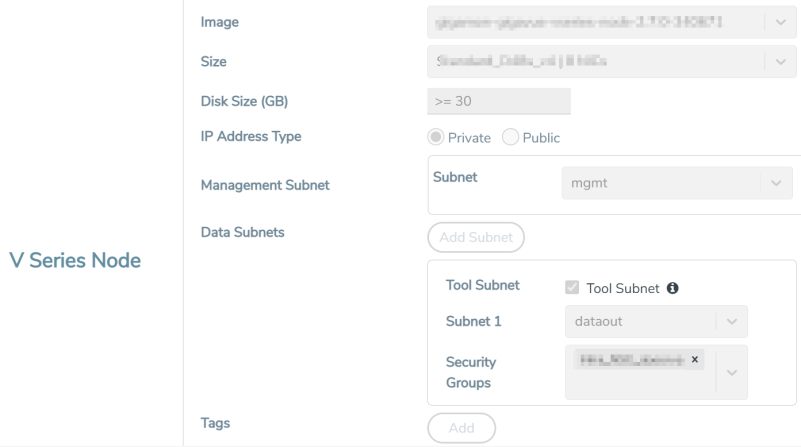
|
Fields |
Description |
|||||||||
|
Image |
From the Image drop-down list, select a GigaVUE V Series Node image. |
|||||||||
|
Size |
From the Size down-down list, select a size for the GigaVUE V Series Node. The default size for GigaVUE V Series Node configuration is Standard_D4s_v4. |
|||||||||
|
Disk Size (GB) |
The size of the storage disk. The default disk size is 30GB. Note: When using Application Metadata Exporter, the minimum recommended Disk Size is 80GB. |
|||||||||
|
IP Address Type |
Select one of the following IP address types:
|
|||||||||
|
Management Subnet |
Subnet: Select a management subnet for GigaVUE V Series. The subnet that is used for communication between the UCT-Vs and the GigaVUE V Series Nodes, as well as to communicate with GigaVUE-FM. Every fabric component (both controllers and the nodes) need a way to talk to each other and GigaVUE-FM. So, they should share at least one management plane/subnet. |
|||||||||
|
Data Subnet(s) |
The subnet that receives the mirrored VXLAN tunnel traffic from the UCT-Vs. Select a Subnet and the respective Security Groups. Click Add to add additional data subnets. Note: Using the Tool Subnet checkbox you can indicate the subnets to be used by theGigaVUE V Series Node to egress the aggregated/manipulated traffic to the tools. |
|||||||||
|
Tag(s) |
(Optional) The key name and value that helps to identify the GigaVUE V Series Node instances in your Azure environment. For example, you might have GigaVUE V Series Nodes deployed in many regions. To distinguish these GigaVUE V Series Nodes based on the regions, you can provide a name that is easy to identify. To add a tag:
|
|||||||||
|
Min Instances |
The minimum number of GigaVUE V Series Nodes to be launched in the Azure connection. The minimum number of instances that can be entered is 1. Note: Nodes are launched when a monitoring session is deployed if GigaVUE-FM discovers some targets to monitor. The minimum amount is launched at that time. The GigaVUE-FM will delete the nodes if they are idle for over 15 minutes. |
|||||||||
|
Max Instances |
The maximum number of GigaVUE V Series Nodes that can be launched in the Azure connection. When the number of instances per V Series node exceeds the max instances specified in this field, increase the number in the Max Instances to Launch. When additional V Series nodes are launched, GigaVUE-FM re-balances the instances assigned to the nodes. This can result in a brief interruption of traffic. |
Click Save to complete the Azure Fabric Launch Configuration.
Check Permissions while Configuring GigaVUE Fabric Components using GigaVUE‑FM
To check for permissions from the Azure Fabric Launch page, follow these steps:
- In the Azure Fabric Launch page, enter the details as mentioned in Configure GigaVUE Fabric Components in GigaVUE‑FM.
- Select Check Permissions. The Check Permissions widget opens.
The permission status for Inventory, Security Group, and Fabric Launch are displayed in this widget. - Select INVENTORY > Check Inventory Permissions.
You can view the required inventory permissions. Inventory permissions with the access status Denied are either missing in the IAM Policy or have restricted boundary - Select SECURITY GROUPS > Check Security Group Permissions.
You can view the ports required for the security groups. The ports in the Denied State are not open in the security group. The user blocks or restricts ports with the status Explicit denied. The ports with status Partially configured have incorrect IP address. - Select FABRIC LAUNCH > Check Fabric Launch Permissions.
You can view the permissions required for deploying the GigaVUE fabric components. The Virtual Machine permissions with the access status Denied could be missing in the IAM Policy.Note: The permissions "Microsoft.Compute/virtualMachines/write" and "Microsoft.Network/networkInterfaces/join/action" are dependent and cannot be validated separately. So, if either of the permissions is denied or not configured, then both permissions will be displayed as "Denied".
The IAM POLICY tab lists the sample policy containing the required permissions for deploying the GigaVUE Cloud Suite for Azure. You must update the Azure IAM policy with the missing permissions that are highlighted in the JSON.
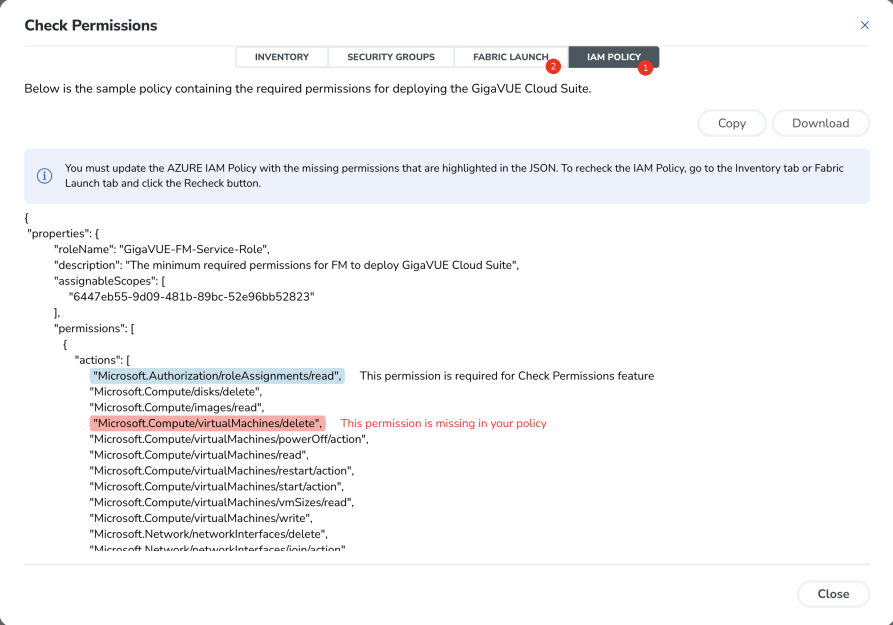
Note: Populating the permissions status for Fabric launch takes a longer duration.



