Setting up Certificate (PKI) based Encryption in FMHA
Each GigaVUE‑FM has its own private certificate, public certificate, and a chain of Certificate Authority (CA) and Root certificates. It is important to create certificates with different Common Name (CN) or Subject Alternative Name (SAN) for each node. This prevents issues with certificate replacement in the Network Security Services Database (NSS DB).
Configure Certificates in FMHA Nodes
To configure a three-node FMHA using certificate based IPSec tunnel for authentication, follow these steps:
| 1. | Import Self Certificates for Each FMHA Node to NSS DB |
| 2. | Share Certificates to Peer FMHA Nodes |
| 3. | Import Peer Certificates |
| 4. | Verify Imported Self Node Certificates and Peer Node Certificates on NSS DB |
| 5. | Create fmha.yaml |
| 6. | Switch to Certificate Based From GigaVUE-FM GUI |
Import Self Certificates for Each FMHA Node to NSS DB
The certificate chain, which includes the public and private certificates, is packaged in P12 format and can be found at the following location:
/etc/gigamon/cms.p12
To import the GigaVUE-FM certificate into the NSS (Network Security Services) database, use the following command on each node in the HA cluster:
ipsec import /etc/gigamon/cms.p12
This command imports the certificate from the cms.p12 file for the respective node.
A message successfully imported certificate from cms.p12 will show up with alias : CMS on the NSS DB.
To generate cms.p12 with custom certificates, refer to Post Installation Configurations.
Share Certificates to Peer FMHA Nodes
Use scp to copy the localhost.crt file from each node to every other node in a three-node FMHA cluster consisting of node-a, node-b, and node-c.
localhost.crt location on each node: /etc/pki/tls/certs/localhost.crt
peer node certificate availability in each node
on Host-A : host-b.crt, host-c.crt are peer certificates
on Host-B : host-a.crt, host-c.crt are peer certificates
on Host-C: host-a.crt, host-b.crt are peer certificates
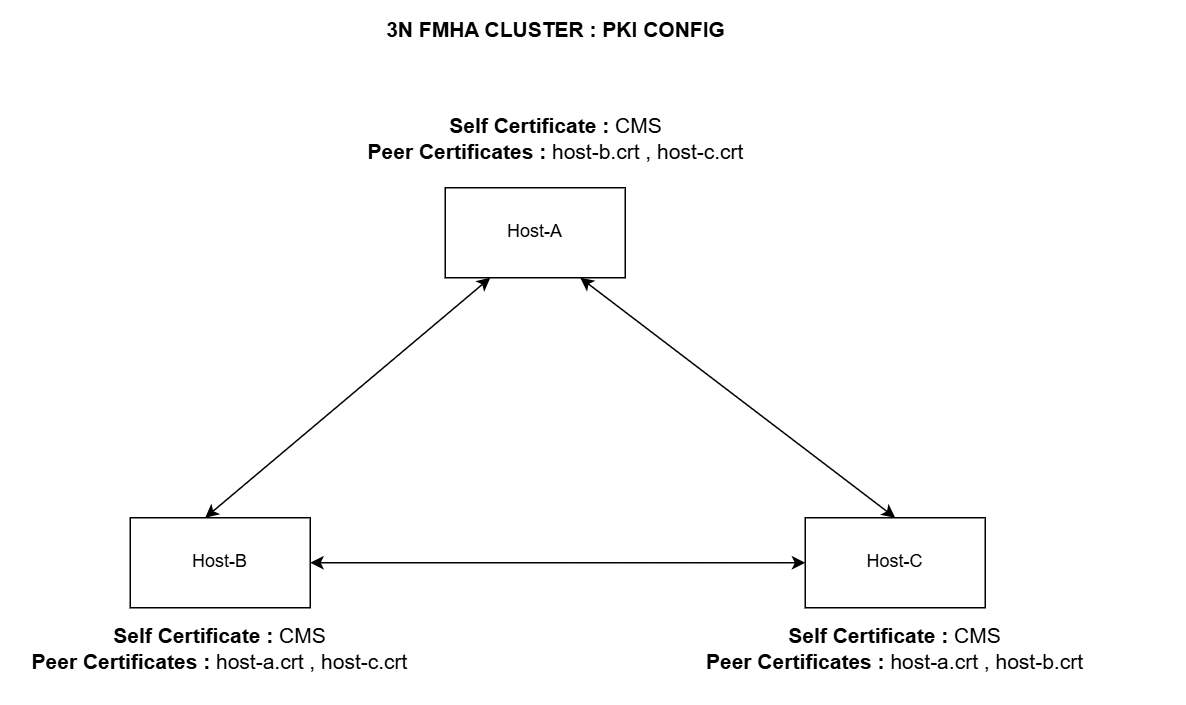
Import Peer Certificates
Add the imported certificates (Certificate Name of B and C) to the NSS db of Host-A:
certutil -A -d sql:/etc/ipsec.d -n "hostB" -t "P,P,P" -i host-b.crt
certutil -A -d sql:/etc/ipsec.d -n "hostC" -t "P,P,P" -i host-c.crt
Import the peer certificates in each node in HA cluster.
Note: Name specified with the -n flag will be used to reference this particular certificate in the fmha.yaml. The name can be GigaVUE‑FM's IPv4, IPv6, or DNS address.
Verify Imported Self Node Certificates and Peer Node Certificates on NSS DB
Verify that each node in the FMHA cluster has successfully imported its self-certificate as well as the other peer node certificates to NSS DB using the following command:
certutil -L -d /etc/ipsec.d
Create fmha.yaml
After importing all the required certificates into the NSS database (Example:) on all three nodes , you must provide GigaVUE-FM with their details.
Create a new file :
fmha.yaml at /home/admin and update the certificate related details for each FMHA node.
fmha.yaml should be available at /home/admin location on each GigaVUE‑FM node in FMHA cluster.
Example:
Configuring Node A
fmtaf@fmqaesxireg9:~/cms_log$ cat fmha.yaml
<Replace with IP address of Node A>:
cert_name: CMS (Self Certificate Name)
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
<Replace with IP address of Node B>:
cert_name: Certificate name of B
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
<Replace with IP address of Node C>:
cert_name: Certificate name of C
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
Configuring Node B
fmtaf@fmqaesxireg9:~/cms_log$ cat fmha.yaml
<Replace with IP address of Node B>:
cert_name: CMS (Self Certificate Name)
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
<Replace with IP address of Node C>:
cert_name: Certificate name of C
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
<Replace with IP address of Node A>:
cert_name: Certificate name of A
cert_san: "Replace with SAN"
cert_type: Replace with Cert type (rsasig/ecdsa)
Switch to Certificate Based From GigaVUE-FM GUI
Open the FMHA landing page on GigaVUE‑FM and select Certificate Based authentication to switch to PKI based tunnels for your existing FMHA cluster. If you are creating a new FMHA cluster, select Certificate Based(ensure that the certificates are imported in all the nodes) and then click Submit to start FMHA cluster creation with tunnel authentication mode as PKI. Refer to Create and Add GigaVUE-FM Instances to HA Group
Rules and Notes
| Currently supported certificate types : ecdsa/rsasig. |
| Ensure that the firewall rules allow IPsec traffic UDP ports 500 and 4500, and protocol 50 and 51. |
| Ensure that the certificates are correctly signed and trusted among the nodes. |
| You can delete the certificate from NSS DB on any FMHA node using the following command. Replace “MYCERT” with the certificate name which you want to remove from NSS DB: |
certutil -d sql:/etc/ipsec.d -D -n "MYCERT"



