FIPS Compliance in GigaVUE-OS
GigaVUE‑OS is compliant with the Federal Information Processing Standard (FIPS), a US government standard for security requirements of cryptographic modules. The Gigamon Linux-based cryptographic module (the FIPS module) provides cryptographic functions for GigaVUE nodes and offers a high level of security for the Ethernet management interface. The FIPS module is compliant with FIPS 140-3 and was validated by the National Institute of Standards and Technology (NIST). The certificate number is 4781. For more information, refer to Cryptographic Module Validation Program – Certificate 4781.
To enable FIPS:
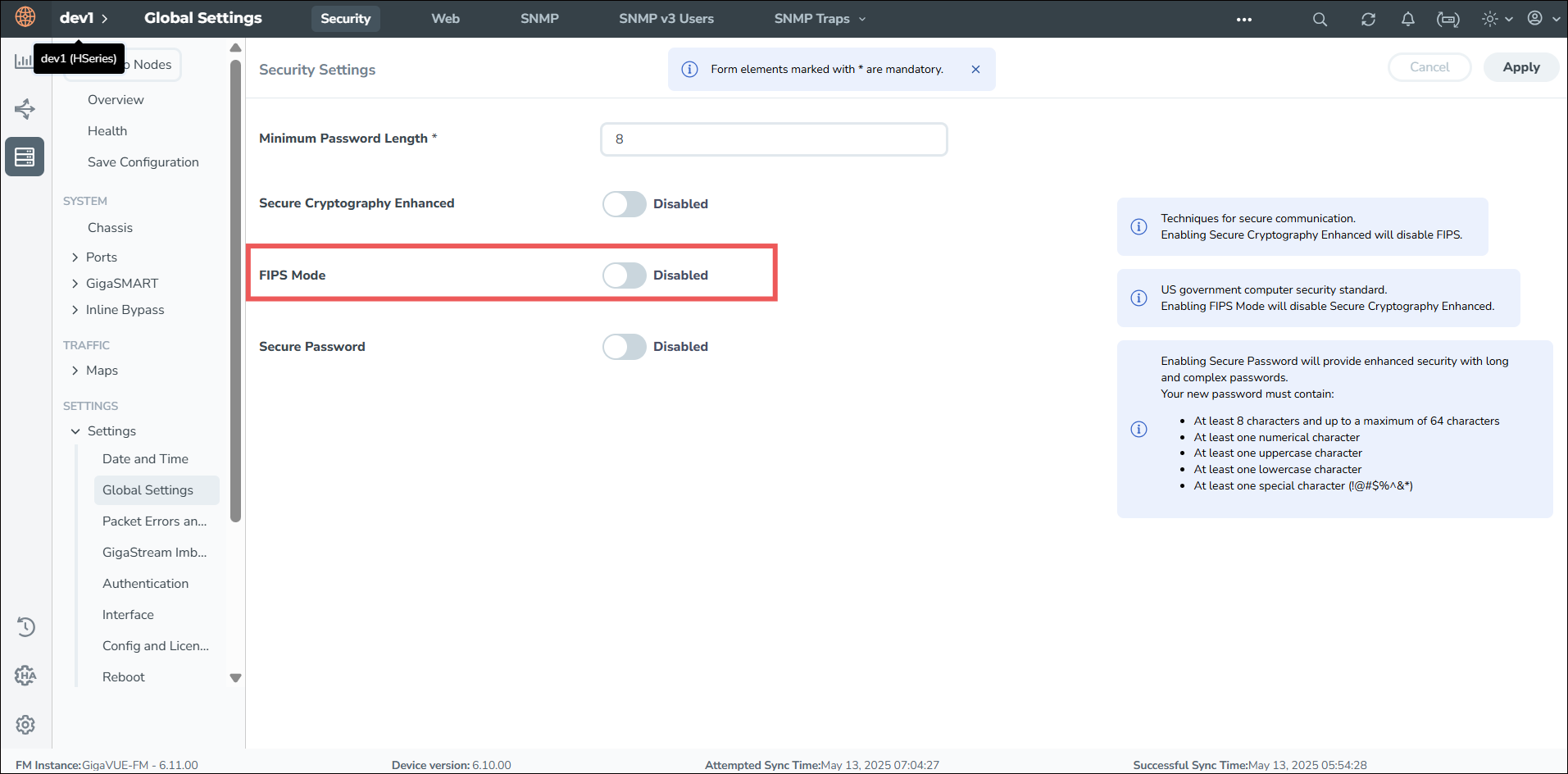
- On the left navigation pane, go to
 >Settings > Global Settings > Security.
>Settings > Global Settings > Security. - Under Security Settings, enable the FIPS Mode.
- Click Apply to save the changes.
Note: FIPS mode does not support the MD5 authentication protocol for SNMP v3 hosts or users. Use SHA or SHA-2 authentication algorithms instead to comply with FIPS requirements.
Note: When you enable or disable FIPS mode from GigaVUE-FM GUI or switch to other security modes, the updated security configuration changes will not be immediately reflected in the GUI. The lapse is due to the time taken for the device to reboot and implement the security configuration changes. The changes will be reflected in the GigaVUE-FM GUI after the next config sync cycle.
For communications with the GigaVUE node, SSL or SSH clients are requested to use high strength ciphers during the session set up negotiation. A high strength cipher is one that uses a key that is equal to or greater than 128 bits.
Weak ciphers will be rejected by the GigaVUE node. For example, if a client attempts to connect to the GigaVUE Ethernet management port using blowfish, the following error message will be displayed: No matching cipher found.
FIPS Compliance in Gen 3 GigaSMART modules
The Gen 3 GigaSMART module supports FIPS 140-3 for inline SSL applications. This ensures that all cryptographic operations adhere to the Federal Information Processing Standards (FIPS) defined by NIST.
FIPS Standards
-
FIPS 140-3 only supports TLS_1.2 and TLS_1.3 versions.
-
FIPS accepts RSA key size minimum of 2048 bits.
-
The system drops traffic that uses unsupported versions and ciphers, resulting in expected connection failures. Only FIPS 140-3 compliant versions and ciphers are allowed for decryption. For supported ciphers list, refer allowed algorithms in the "Supported Cipher Suites" section in the GigaVUE Fabric Management Guide.
-
FIPS 140-3 validated modules do not support non-NIST curves, such as Brainpool, Ed448, x25519, x448, and secp256k1. Using these curves may result in handshake failures. Only NIST-recommended prime EC curves (P-256, P-384, P-521) are allowed.
Limitations
-
Use only PKCS#12 files that include encryption and hashing algorithms compatible with OpenSSL 3.x to ensure compliance, as FIPS 140-3 supports only versions of OpenSSL 3.x and later.
-
Passive SSL is not supported in FIPS mode.
-
FIPS mode disables HSM support for Gen 3 GigaSMART modules. For the list of devices that support Gen 2 GigaSMART modules and Gen 3 GigaSMART modules, refer to the below table.
Device
Gen 2
Gen 3
GigaVUE-HC1 ü
ü
GigaVUE-HC3
ü
ü
GigaVUE-HC1-Plus
û
ü
GigaVUE-HCT û
ü
-
FIPS 140-3 is not supported in Inline SSL (iSSL) on Gen 2 GigaSMART modules.
-
FIPS mode currently disables secure tunnel feature-specific profile configurations. However, support for FIPS mode in secure tunnels is planned for future releases.
-
Post-Quantum Cryptography (PQC) is not supported and remains disabled in FIPS mode.
Upgrade Requirements for FIPS-Enabled Devices
Before you upgrade to version 6.11 on a FIPS-enabled device, complete the following steps to ensure a successful upgrade:
-
Delete all Inline SSL (iSSL) configurations and the keystore before the upgrade. After the upgrade, reconfigure the Gen 3 GigaSMART module.
-
Remove all HSM and HSM Groups, including nCipher and Luna, from the device.
-
Delete all Inline SSL (iSSL) configurations for Gen 2 GigaSMART modules, since they do not support FIPS 140-3. If you require Inline SSL on GigaVUE-HC1 or GigaVUE-HC3 devices, add a Gen 3 GigaSMART card.
-
Remove SNMPv3 configurations that use the MD5 authentication protocol because FIPS 140-3 does not support MD5 algorithms.
-
If you don't complete all required steps before upgrading, the upgrade will fail. The system will automatically revert to the previous version.



