Application Metadata Intelligence Capabilities
NetFlow/IPFIX Generation
AMI supports generating only unsampled (i.e., 1:1) NetFlow/IPFIX records. Records can be generated in the following formats: NetFlow v5/v9, IPFIX, or CEF. Only standard information elements can be exported (i.e., no application metadata).
Users can select the NetFlow v5 tool template for exporting NetFlow v5 records or configure the collect fields for exporting NetFlow v9 and IPFIX records.
Flow Behavior
The flow behavior determines the number of records generated for each direction of the (monitored) traffic flows. Exporters can be configured with either Unidirectional or Bidirectional Flow Behavior. Unidirectional Flow Behavior exports one record for each direction, whereas Bidirectional Flow Behavior exports one record for both directions. The Flow Behavior is user configurable under Application metadata Settings. The following table lists the export formats supported for each flow behavior.
More than one exporter (max 5) can be configured to export records to multiple tools. When more than one exporter exists, all the exporters must support the same Flow Behavior.
|
Export Formats* |
Unidirectional Flow Behavior |
Bidirectional Flow Behavior |
|---|---|---|
|
NetFlow v5/v9 |
Supported |
Not Supported |
|
IPFIX |
Supported |
Supported |
|
CEF |
Supported |
Supported |
*Application metadata can be exported in IPFIX or CEF format and it supports only bidirectional flow behavior.
Record Types
AMI can generate separate records (Segregated) for network and application metadata. Tools that rely on flow correlation will prefer to receive network and application metadata in a single record. In which case, AMI can be configured to generate consolidated (Cohesive) records for each flow.
Records Export
AMI keeps track of all sessions using the 5-tuple information, including flows exchanged over reliable transport protocols like TCP and connectionless transport protocols like UDP. Records are exported based on the Active Timeout and Inactive Timeout, with the following exceptions:
-
For connection-oriented applications (ex., TCP-based applications), records are exported as soon as the corresponding connections are closed.
-
For connectionless applications (ex., UDP-based applications), the corresponding flows are determined to be completed after the expiration of the inactive timeout. The default value for the inactive timeout is 15 seconds (user configurable). Records for the corresponding flows are exported thereafter.
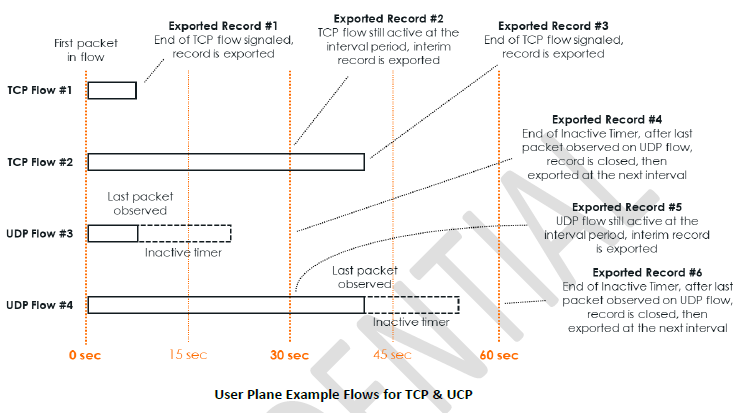
In the diagram above, there are 4 flows, but 6 records are generated. Two flows (#2 & #4) lasted longer than the configured Active Timeout (30 seconds). Therefore, interim records were generated at every 30 seconds. If the flows had lasted longer than 60 seconds, additional interim records would have been generated at 90 seconds, 120 seconds, and so on.
Tool Templates
Tool template in Application Metadata Intelligence predefines a list of applications and its attributes, which you can choose as per your requirements while configuring Application Metadata Intelligence solution.
A template once created can be used by multiple exporters to export the attributes in the specified format to the destination tools.
You can use the tool templates while creating an Application Metadata Intelligence session. By default, you can find the following tool templates:
| BroMetadata Template |
| Netflow V5 Template |
| SplunkMetadata Template |
Starting from software version 6.2.00, the following tool templates are supported:
| SecurityPosture |
| RogueActivity |
| SuspiciousActivities |
| AnomalousTraffic |
| Troubleshooting |
| M2131Logging |
| UnmanagedAssets |
The following table provides the purpose of each of the tool templates when used in Application Metadata Intelligence :
| Tool Template | Purpose |
|---|---|
| BroMetadata Template |
For selecting applications and attributes that can be detected by Bro sensor |
| Netflow V5 Template |
For emulating NetFlow V5 behavior |
| SplunkMetadata Template |
For providing a quick insight into the network traffic generated by various applications and protocols |
| SecurityPosture |
For detecting flaws in securing the applications in the network |
| RogueActivity |
For detecting unsanctioned applications that can pose challenges to network security |
| SuspiciousActivities |
For detecting issues related to unmanaged devices, suspicious connections, and traffic outside normal limits in the network |
| AnomalousTraffic |
For detecting challenges with HTTP, HTTPS, and DNS traffic in the network |
| Troubleshooting |
For detecting latency, connectivity, and protocol errors in the network |
| M2131Logging |
For U.S. Office of Management and Budget M-21-31 logging requirements |
| UnmanagedAssets |
For providing visibility into unmanaged hosts and devices in the network |
Note: You cannot edit the above templates. Hover over the Description column to view the description of the default tool templates.
You can create new tool templates according to your requirements. You can also edit and clone the templates. Refer to Application Metadata Intelligence Capabilities for more information.
DPI Packet limit
DPI Packet Limit is used to restrict the number of packets in a particular session to be sent to the DPI engine instead of sending all the packets to improve the AMI performance.
Aggregate Round-trip Time
Aggregate Round-trip Time allows to export the minimum, maximum, and mean of RTT values , and also the aggregate of TCP Lost byte values collected per export time interval.
RTT Attribute in AMI
The RTT attribute supported in AMI export is in the struct timeval format. The size of the attribute is 16 bytes. The first 8 bytes represent the value in seconds and the next 8 bytes represent the value in microseconds.
The values are exported in the network byte order.
In the following example:
| The PEN id 3365 has a RTT value of 0 seconds and 0xb827 microseconds |
| The PEN id 3384 has a RTT value of 0 seconds and 0xbfb8 microseconds |




