Traffic Processing
GigaVUE Cloud Suite for AWS provides a comprehensive set of applications that allows you to build efficient and effective visibility solutions. These applications:
- Reduce the traffic volume by applying user-defined filtering criteria, removing duplicate copies of packets, or removing a significant portion of each packet. This helps in increasing the efficiency of analysis tools by focusing on the “right” information carried in network packets.
- Mask sensitive information to meet regulatory compliance requirements.
- Extract metadata information such as NetFlow Generation and a vast array of other types of metadata.
- Remove different layers of headers in nested packets so that analysis tools can easily access the real payload.
This section provides detailed information on the following topics:
Supported Applications
The following table provides an overview of the applications included in GigaVUE Cloud Suite for AWS:
|
Parameter |
Description |
|
Application Filtering Intelligence |
Application Filtering Intelligence allows you to filter traffic based on the application (such as YouTube, Netflix, Sophos, or Facebook) or application family (such as antivirus, web, erp, or instant-messaging). Application Filtering Intelligence enables advanced traffic filtering based on Layer 7 applications, providing the ability to fine-tune your network visibility. With this capability, you can optimize tool performance by excluding high-volume, low-risk traffic from being sent to your monitoring tools. At the same time, you can prioritize and route high-risk or critical traffic of interest to the appropriate tools for detailed analysis, ensuring efficient resource utilization and timely response to potential threats or incidents. |
|
Adaptive Packet Filtering (Part of Application Filtering Intelligence) |
Adaptive Packet Filtering (APF) delivers advanced capabilities to analyze and manage traffic flows with precision. APF enables you to inspect any part of a packet, including its payload, and take intelligent actions such as forwarding, dropping, or masking the flow. This feature supports filtering across complex encapsulation headers, such as VXLAN, ERSPAN, GRE, Nested VLANs, MPLS, VN-Tag, and more. Additionally, it allows traffic to be filtered based on inner packet contents within these encapsulated flows, offering unparalleled granularity in traffic control. APF is also session-aware, allowing you to define search patterns using regular expressions (RegEx) or strings. Once a match is detected, APF can apply actions to the entire session, such as forwarding it to specific tools or completely dropping it from the monitoring pipeline. |
|
Application Session Filtering (Part of Application Filtering Intelligence) |
Application Session Filtering (ASF) provides advanced capabilities to identify and filter network flows based on flexible user-defined criteria. By leveraging powerful regular expressions (RegEx), ASF allows you to define precise patterns to match specific flow characteristics. ASF examines one or more packets within a flow session to determine if the flow aligns with your defined criteria. Once a match is identified, all packets within that session are forwarded for analysis, ensuring that only relevant traffic reaches your tools. |
|
Application Metadata Intelligence |
Application Metadata Intelligence allows you to export metadata from applications that are detected in the network traffic. The records can be exported to a collector either in IPFIX or CEF format |
|
Application Metadata Exporter |
Application Metadata Exporter (AMX) application converts the output from the Application Metadata Intelligence (AMI) in CEF format into JSON format and sends it to the cloud tools and Kafka. |
|
Application Visualization |
Application Visualization identifies and monitors all applications contributing to the network traffic and reports on the total applications and the total bandwidth they consume over a select period. Application Visualization allows you to identify more than 3,500 applications. |
|
De-Duplication |
De-duplication application targets, identifies, and eliminates duplicate packets, blocking unnecessary duplication and sending optimized flows to your security and network monitoring tools. De-duplication lets you detect and choose the duplicate packets to count or drop in a network analysis environment. |
|
ERSPAN Tunnel Decapsulation |
ERSPAN Tunnel Decapsulation application removes the protocol header added by ERSPAN tunnel to extract the original user data packet. |
|
Map |
A map is used to filter the traffic flowing through the GigaVUE V Series Nodes. It is a collection of one or more rules (R). The traffic passing through a map can match one or more rules defined in the map. |
|
GENEVE Decapsulation |
The GENEVE Decapsulation application removes the protocol header added by the GENEVE tunnel to extract the original user data packet. |
|
Header Stripping |
Header Stripping application efficiently examines packets for specified headers, such as MPLS, VLAN, VXLAN, VN-TAG, and GRE, and removes them before sending the packets to the appropriate security and analysis tools. |
|
L2GRE Tunnel Decapsulation |
The L2GRE Tunnel Decapsulation application removes the protocol header added by the L2GRE tunnel to extract the original user data packet. |
|
L2GRE Tunnel Encapsulation |
The L2GRE Tunnel Encapsulation application wraps a user packet within an L2GRE protocol-compliant packet for transport to the next hop for processing or analysis. |
|
Load Balancing |
A Load-Balancing application allows you to distribute traffic to multiple tools for analysis. The application not only load-balances the traffic among the tools; it can also handle the distribution in a stateful manner to ensure packets of the same flow are always distributed to the same tool. |
|
Masking |
Masking application allows you to overwrite specific packet fields with a specified pattern so that sensitive information is protected during network analysis. |
|
Packet Slicing |
Packet Slicing allows you to truncate packets after a specified header and slice length, preserving the portion of the packet required for monitoring purposes. Slicing operations are typically configured to preserve specific packet header information, allowing effective network analysis without the overhead of storing full packet data. |
|
Out of Band SSL/TLS Decryption |
SSL/TLS decryption application delivers decrypted traffic to out-of-band tools that can then detect threats entering the network. |
|
UDPGRE Tunnel Decapsulation |
UDPGRE Tunnel Decapsulation application removes the protocol header added by the UDPGRE tunnel to extract the original user data packet. |
|
VXLAN Tunnel Decapsulation |
VXLAN Tunnel Decapsulation application removes the protocol header added by the VxLAN tunnel to extract the original user data packet. |
|
VXLAN Tunnel Encapsulation |
VxLAN Tunnel Encapsulation application wraps a user packet within a VXLAN protocol-compliant packet for transport to the next hop for processing or analysis. |
For more detailed information on how to configure these applications in the Monitoring Session canvas, refer to
Flexible Application Chaining
When creating a Monitoring Session, you can use more than one application to receive, process, and forward the traffic. You can define an application chain to indicate how the traffic should be received by the GigaVUE V Series Node, how the traffic should be processed, and how or where the traffic should be forwarded.
The following diagram explains application chaining with two applications, Map and Slicing between Ingress and Egress Tunnels.
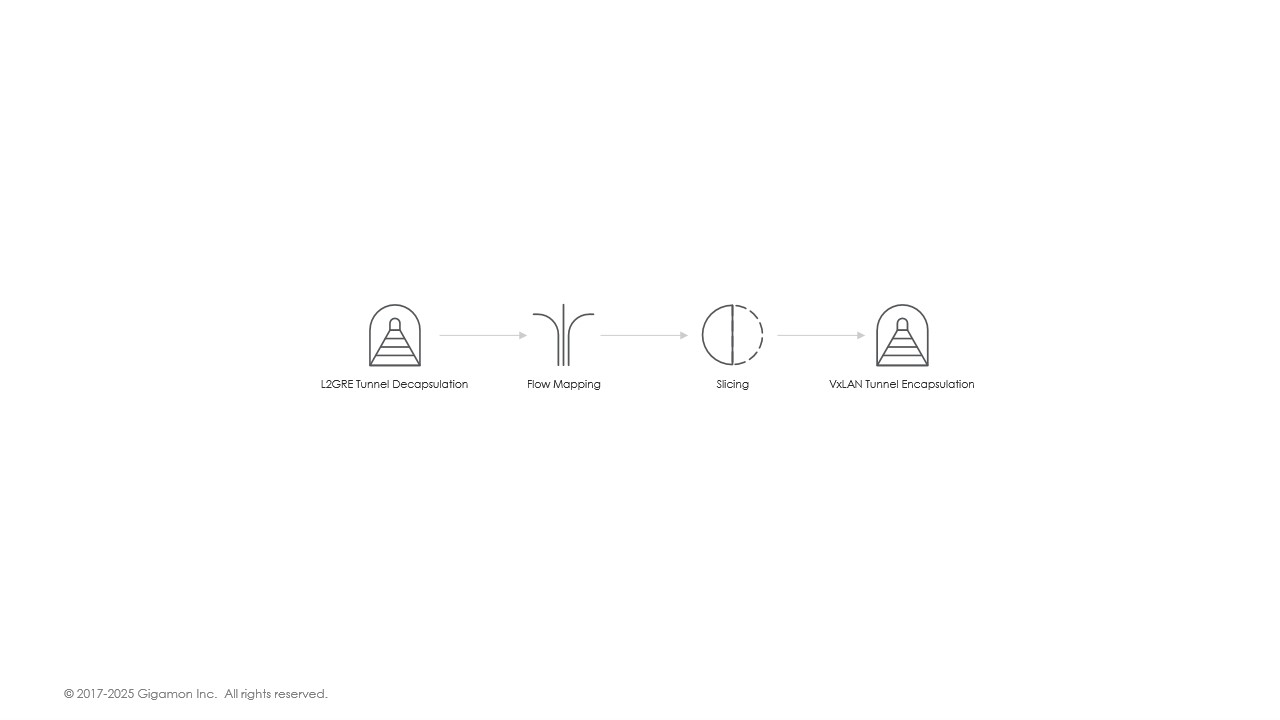
The application chain in this example specifies the following:
- Traffic Reception: Acquired traffic is received by V Series nodes through an L2GRE tunnel. The L2GRE protocol header is removed before sending packets to the FlowMap for filtering.
- Traffic Filtering: Packets are filtered based on user-defined rules in the FlowMap. Only packets matching the criteria are forwarded to the Slicing application; non-matching packets are dropped.
- Traffic Slicing: The Slicing application removes specific parts of each packet as per user-defined parameters.
- Traffic Forwarding: Processed packets are encapsulated in a VXLAN header and sent to the specified tools based on the VXLAN Tunnel Encap configuration.
This Directed Acyclic Graph (DAG) model used in Monitoring Sessions provides you with the flexibility to customize how traffic is processed and forwarded.
Here’s another simple example of an application chain defined as part of a Monitoring Session:
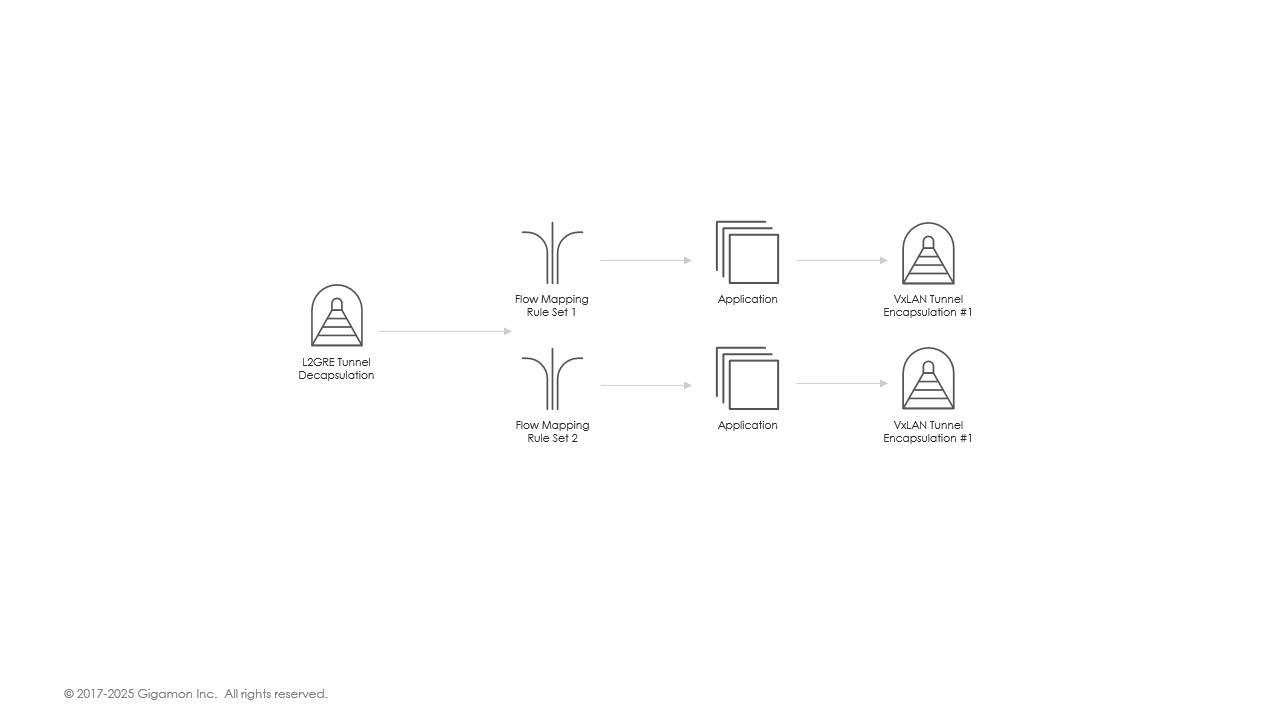
In this example, traffic is received via an L2GRE tunnel, with the L2GRE header removed before being sent to the FlowMap for filtering. The FlowMap application applies two sets of user-defined filtering rules:
- Packets matching the first set of rules are sent to App1 for further processing.
- Packets matching the second set of rules are sent to App2 for separate processing.
This flexible application chaining allows you to process different traffic streams using distinct applications and forward the resulting traffic to different tools. By enabling complex processing and forwarding logic, this approach helps you efficiently achieve your monitoring goals while optimizing costs.



