Resources for Configuring Solutions on GigaVUE V Series Nodes
To configure the Application Intelligence solution on the GigaVUE V Series nodes, you must create the virtual environment with the required connections. You must also configure the sources and the required destinations for the traffic. The following table lists the required tasks:
| S. No |
Task |
Refer to |
|---|---|---|
| 1 |
Create the Virtual Environment |
|
| 2 | Configure the Connection and deploy the V Series Node | |
| 3 |
Create the Source of traffic |
Create Source Selectors |
| 4 |
Create the Tunnel Destinations for the ingress and the egress traffic |
Create Tunnel Specifications |
| 5 |
Create Application Intelligence Session |
Application Intelligence Session |
- You can deploy multiple GigaVUE V Series Nodes in a solution.
- You can use V Series Node API Proxy Server (VPS) to scale and manage multiple V Series Nodes. Refer to the GigaVUE-FM REST API Reference in GigaVUE-FM User's Guide for detailed information.
- You can use tool templates while creating an Application Metadata Intelligence session. To create a custom tool template for GigaVUE V Series Node, signature is required from the node. Refer to the Tool Templates section for details.
- Prior to configuring the Resources, refer to the prerequisites section in the respective GigaVUE Cloud Configuration guides.
- To delete a GigaVUE V Series Node deployed in a solution, you must delete the resources in the following order:
- Delete the solution.
- Delete the GigaVUE V series Node and Connection.
- Delete the Environment.
The Environments page allows you to create the following:
- Environments: The physical or the virtual environment in which the Application Intelligence solution is to be deployed.
- Connections: Connection between GigaVUE‑FM and the cloud platform.
To configure the Environment:
- Select Inventory > Resources > Environments.
-
On the Environments page, on the Environments tab, click Create.
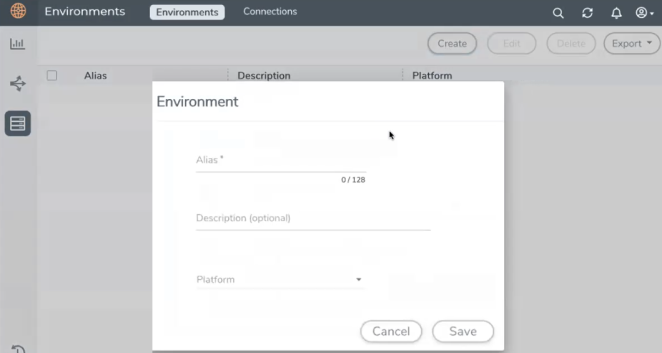
- Select or enter the following details:
- VMware ESXi
- VMware NSX-T
- AWS
- Azure
- Click Save.
|
Field |
Description |
|
Alias |
Alias name used to identify the Environment. |
|
Description |
Brief description about the Environment. |
|
Platform |
The cloud platform. Supported platforms include: |
The environment is added to the list view.
Use the following buttons to manage your environment:
|
Button |
Description |
| Delete | Use to delete an Environment. |
| Edit | Use to edit the details in an Environment. |
| Export | Export the details from the Environment page in an XLS or CSV file. |
To configure the Connection:
- Select Inventory > Resources > Environment.
- On the Environments page, on the Connections tab, click Create.
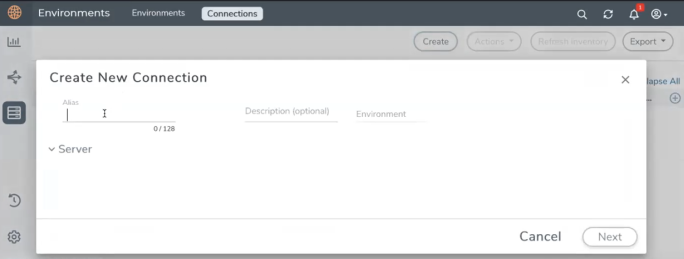
- Depending on the cloud platform selected in the Environment section, the options in the Connections page varies. Refer to the following sections for details.
Note: When creating a connection in the connections page, the corresponding monitoring domain created for internal use in GigaVUE‑FM will not be displayed in the Monitoring Domain list page.
To establish a connection to the VMware ESXi, select or enter the following details:
|
Field |
Description |
|
Alias |
Alias name used to identify the connection. |
|
Description |
Brief description about the connection. |
|
Environment |
Select the required environment. Refer to Create Environment |
|
Server |
The IP address of the virtual server. |
| vCenterUserName | Valid user name |
| vCenterPassword | Password for the user |
After the connection is established, select or enter the following details in the fabric launch configuration page and click Save:
Note: During V Series Node upgrade, the old node gets deleted and the new V Series Node is deployed. However, when the node upgrade fails due to deployment issues, the old node gets deleted and the new node is not deployed on the Connection page. This may led to loss of traffic. To avoid this you will have to redeploy the nodes again.
|
Field |
Description |
|---|---|
| Datacenter | vCenter Data Center with the ESXi hosts to be provisioned with V Series nodes |
|
Cluster |
The Cluster on which the V Series nodes are to be deployed. From the drop-down list, select the required cluster or click All to select all the available clusters. |
| V Series Node Image |
Web Server URL of the directory where V Series node ova files are available. Note: Before VMware Configuration, the V Series OVA files must be extracted as OVF files and placed in the same directory. |
| Form Factor | Instance size of the V Series node. Refer Prerequisites for Integrating V Series Nodes with ESXi for more information. |
|
Hosts |
Select the ESXi host for V Series deployment. Click Select All or Select None to select or unselect multiple hosts. Note: You can configure multiple hosts in a single connection (GigaVUE V Series node). Select the Datastore and enter the required values. Click Apply. |
|
Field |
Description |
|---|---|
| V Series Node Name | Name of the V Series Node |
|
Datastore |
Network datastore of the selected host |
| Management Network | Management network for V Series nodes |
| IP Type | IP type, can be IPv4 or IPv6. |
|
Tunnel Network |
Tunnel Network for the V Series nodes |
| IP Type | IP type of the tunnel, can be IPv4 or IPv6. |
|
Tunnel Gateway IP |
IP address of the Tunnel Gateway |
| Tunnel CIDR | CIDR value of the Tunnel |
|
User Password: (gigamon) |
SSH Password of the V Series node |
|
Form Factor |
Instance size of the V Series node |
|
IPv6 |
Use the toggle option to configure IPv6 tunnels. Provide the IPv6 prefix length value. The value must be greater than zero. Note: Ensure to enable this option before deploying the solution with IPv6 address as tool address. |
Use the following buttons to manage your VMware ESXi connections :
|
Button |
Description |
| Create | Use to create new connection. |
| Actions |
Provides the following options:
|
| Refresh Inventory | Use to refresh the selected connection. |
| Export | Use to export the details from the Connections page into an XLS or a CSV file. |
To create Application Intelligence sessions, refer to Create an Application Intelligence Session in Virtual Environment.
Refer to the following sections for details:
- Rules and Notes
- Steps
Rules and Notes
- NSXT- manager version must be 3.0.3. Otherwise after editing the solution, the packets will not reach the V Series node.
- NSX-T manager cannot be registered for more than one GigaVUE-FM.
- For GigaVUE-FM software version 5.13.00, you cannot deploy more than one V-series node.
- For GigaVUE-FM software version 5.13.00: If you configure a GigaVUE V Series node with the Application intelligence solution, then you must not configure other basic GigaSMART applications, such as slicing, masking, and vice-e-versa. These GigaSMART applications cannot work in parallel.
- The NSX-T manager is responsible for configuring the sources. Therefore, you need not configure the Source Selectors for the NSX-T environment.
To connect to VMware NSX-T, select or enter the following details:
|
Field |
Description |
|
Alias |
Alias name used to identify the connection. |
|
Description |
Brief description about the connection. |
|
Environment |
Select the environment configured in the Create Environment |
|
Server |
The IP address or the DNS name of the virtual server. |
| vCenterUserName | Valid user name |
| vCenterPassword | Password for the user |
| NSX-T Manager IP Address | IP address or Hostname of your VMware NSX-T. |
| NSX-T User Name | Username of your NSX-T account. |
| NSX-T Password | Password of your NSX-T account. |
| Image URL | Web Server URL of the directory where V Series node OVA, VMDK, and OVF files are available. The Web Server URL must be in the follwoing format: http://<server-IP:port>/<path to where the OVF files are saved> and the port can be any valid number. The default port number is 80. |
| GigaVUE‑FM User Name | GigaVUE‑FM username. |
| GigaVUE‑FM Password | GigaVUE‑FM password |
Once the connection is established, enter the following details in the fabric launch configuration page, and click Save:
|
Field |
Description |
|---|---|
| Datacenter | vCenter Data Center with the NSX-T hosts to be provisioned with V Series nodes |
|
Cluster |
Cluster where you want to deploy V Series nodes |
|
Datastore |
Network datastore shared among all NSX-T hosts. |
| Management Network | Management network for V Series nodes |
| IP Type | IP type, can be IPv4 or IPv6. |
|
Tunnel Network |
Tunnel Network for the V Series nodes |
| IP Type | IP type of the tunnel, can be IPv4 or IPv6. |
|
Tunnel Gateway IP |
IP address of the Tunnel Gateway. |
| MTU | MTU value. |
| Tunnel CIDR | CIDR value of the Tunnel. |
|
User Password: (gigamon) |
SSH Password of the V Series node. |
| Confirm User Password | |
| Form Factor | Instance size of the V Series node |
|
Service Attachment |
Service segment created on NSX-T |
|
Deployment Type Deployment Count (for Clustered deployment type) |
Deployment type is clustered. Note: Host option is disabled, as there is only one V series node per V-center. Deployment count is restricted to one V Series nodes (Service Instances). |
|
IPv6 |
Use the toggle option to configure IPv6 tunnels. Provide the IPv6 prefix length value, and it should be greater than zero. Note: Ensure to enable this option before deploying the solution with IPv6 address as tool address. |
Use the following buttons to manage your VMware NSX-T connections :
|
Button |
Description |
| Create | Use to create new connection. |
| Actions |
Provides the following options:
|
| Refresh Inventory | Use to refresh the selected connection. |
| Export | Use to export the details from the Connections page into an XLS or a CSV file. |
To create Application Intelligence sessions, refer to Create an Application Intelligence Session in Virtual Environment.
Refer Deploying Application Intelligence Solution at Scale on VMware NSX-T 3.1.3 for more detailed information.
Note: For Application Intelligence solution, you must add the UDP port 2056 for GigaVUE‑FM in your AWS security group.
To connect to AWS, select or enter the following details:
|
Field |
Description |
|||||||||
|
Alias |
Alias name used to identify the connection. |
|||||||||
|
Description |
Brief description about the connection. |
|||||||||
|
Environment |
Select the environment. Refer to Create Environment |
|||||||||
|
Server |
|
|||||||||
|
Authentication Type |
Authentication type for the connection. You can select one of the following:
If Basic Credentials is selected, you must enter the Access Key and Secret Access keys. |
|||||||||
|
Access Key/Secret Access Key |
The access key and secret access key that are used to establish AWS connection. These keys are required when the authentication type is Basic Credentials. |
|||||||||
|
Region Name |
The AWS region for the connection. For example, EU (London). Note: If the region you want to choose is not available in the Region Name list, you can add a custom region. Adding a Custom RegionTo add a custom region:
|
|||||||||
|
Select Account Name/Id |
Select the AWS account name/id. | |||||||||
|
Select network name/Id |
Select the AWS network name/id | |||||||||
|
Traffic Acquisition Method |
Select a Tapping method. The available options are:
Note: For VPC Traffic Mirroring option, additional permissions are required. Refer to the Permissions and Privileges for details. |
|||||||||
| MTU | The Maximum Transmission Unit (MTU) is the maximum size of each packet that the tunnel endpoint can carry | |||||||||
| Use Proxy Server |
Select Yes to add a proxy server. Proxy server enables communication from GigaVUE-FM to the Internet, if GigaVUE-FM is deployed in a private network. On selecting a Proxy Server, enter the following information:
|
|||||||||
| Secure Mirror Traffic |
Check box to establish secure tunnel between G-vTAP Agents and GigaVUE V Series nodes for traffic across VPCs. |
In the AWS Virtual Node Deployment page, select or enter the following details and click Save:
|
Fields |
Description |
|||||||||
|
Centralized VPC |
Alias of the centralized VPC in which the G-vTAP Controllers, V Series Proxies and the GigaVUE V Series nodes are launched. |
|||||||||
|
EBS Volume Type |
The Elastic Block Store (EBS) volume that you can attach to the fabric components. The available options are:
|
|||||||||
|
SSH Key Pair |
The SSH key pair for the GigaVUE fabric nodes. |
|||||||||
|
Management Subnet |
The subnet that is used for communication between the controllers and the nodes, as well as to communicate with GigaVUE-FM. This is a required field. |
|||||||||
|
Security Groups |
The security group created for the GigaVUE fabric nodes. |
In the G-vTAP Configuration section, select or enter the following details:
|
Fields |
Description |
||||||||||||
|
Controller Version |
The G-vTAP Controller version. If there are multiple versions of G-vTAP Agents deployed in the EC2 instances, then you must configure multiple versions of G-vTAP Controllers that matches the version numbers of the G-vTAP Agents. Note: If there is a version mismatch between G-vTAP controllers and G-vTAP Agents, GigaVUE-FM cannot detect the agents in the instances. Click Add to add multiple versions of G-vTAP Controllers: An older version of G-vTAP Controller can be deleted once all the G-vTAP Agents are upgraded to the latest version. |
||||||||||||
|
Instance Type |
The instance type for the G-vTAP controller. The recommended minimum instance type is nitro-based starting from t3a.xlarge. Note: V Series 2 solution does not support non-nitro-based instance types. |
||||||||||||
|
Number of Instances |
The number of G-vTAP Controllers to deploy in the monitoring domain. |
||||||||||||
|
Agent Tunnel Type |
The type of tunnel used for sending the traffic from G-vTAP Agents to GigaVUE V Series nodes. The options are GRE or VXLAN tunnels. If any Windows agents co-exist with Linux agents, VXLAN must be selected. |
||||||||||||
|
G-vTAP Agent MTU (Maximum Transmission Unit) |
The Maximum Transmission Unit (MTU) is the maximum size of each packet that the tunnel endpoint can carry from the G-vTAP Agent to the GigaVUE V Series node.
Note: If Secure Mirror Traffic option is enabled, then to account for IPSec tunnel overhead and to minimize the occurrence of fragmentation, the following values are recommended to be configured for G-vTAP Agent Tunnel MTU: AWS Platform MTU is 9001
|
||||||||||||
|
IP Address Type |
The IP address type. Select one of the following:
Note: The elastic IP address does not change when you stop or start the instance. |
||||||||||||
|
Additional Subnet(s) |
(Optional) If there are G-vTAP Agents on subnets that are not IP routable from the management subnet, additional subnets must be specified so that the G-vTAP Controller can communicate with all the G-vTAP Agents. Click Add to specify additional subnets, if needed. Also, make sure that you specify a list of security groups for each additional subnet. |
||||||||||||
|
Tag(s) |
(Optional) The key name and value that helps to identify the G-vTAP Controller instances in your AWS environment. For example, you might have G-vTAP Controllers deployed in a VPC. To identify the G-vTAP Controllers you can provide a name that is easy to identify such as us-west-2-gvtap-controllers. To add a tag,
|
In the V Series Node configuration section, select or enter the following:
|
Fields |
Description |
|||||||||
|
Version |
GigaVUE V Series Proxy/Controller version. |
|||||||||
|
Instance Type |
Instance type for the GigaVUE V Series Proxy/Controller. The recommended minimum instance type is nitro-based starting from t3a.xlarge. Note: V Series 2 solution does not support non-nitro-based instance types. |
|||||||||
|
Number of Instances |
Number of GigaVUE V Series controllers to deploy in the monitoring domain. |
|||||||||
|
Set Management Subnet |
Use the toggle button to select a management subnet.
|
|||||||||
|
Set Security Groups |
Toggle option to Yes to set the security group that is created for the GigaVUE V Series node. |
|||||||||
|
IP Address Type |
Select one of the following IP address types:
The elastic IP address does not change when you stop or start the instance. |
|||||||||
|
Additional Subnets |
(Optional) If there are GigaVUE V Series nodes on subnets that are not IP routable from the management subnet, additional subnets must be specified so that the GigaVUE V Series Proxy/Controller can communicate with all the GigaVUE V Series nodes. Click Add to specify additional subnets, if needed. Also, make sure that you specify a list of security groups for each additional subnet. |
|||||||||
|
Tags |
(Optional) The key name and value that helps to identify the GigaVUE V Series Proxy/Controller instances in your AWS environment. |
Use the following buttons to manage your AWS connections :
|
Button |
Description |
| Create | Use to create new connection. |
| Actions |
Provides the following options:
|
| Refresh Inventory | Use to refresh the selected connection. |
| Export | Use to export the details from the Connections page into an XLS or a CSV file. |
To create Application Intelligence sessions, refer to Create an Application Intelligence Session in Virtual Environment.
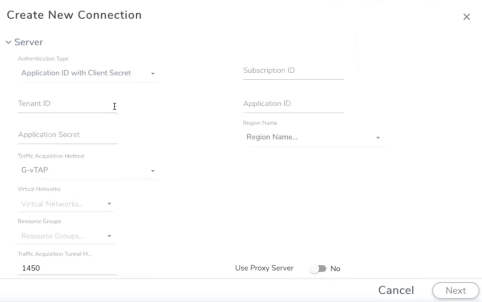
To connect to Azure, select or enter the following details:
|
Field |
Description |
||||||||||||||||||
|
Alias |
Alias name used to identify the connection. |
||||||||||||||||||
|
Description |
Brief description about the connection. |
||||||||||||||||||
|
Environment |
Select the environment. Refer to Create Environment |
||||||||||||||||||
|
Server |
|||||||||||||||||||
|
Authentication Type |
Select an authentication type for the connection.
|
||||||||||||||||||
|
Region Name |
The Azure region for the connection. For example, East Asia. |
||||||||||||||||||
|
Traffic Acquisition Method |
Select a Tapping method. The available options are:
|
||||||||||||||||||
| Virtual Networks |
Alias of the Virtual Networks (VNet) specified in the connection configuration that contains the VNet of the fabric nodes and the VNets of the target VMs. You can select multiple VNets for a connection. |
||||||||||||||||||
| Resource Groups |
The Resource Groups created in Azure for communication between the controllers, nodes, and GigaVUE-FM. A Resource Group must contain the VMs that needs to be monitored. |
||||||||||||||||||
| Traffic Acquisition Tunnel MTU | The Maximum Transmission Unit (MTU) is the maximum size of each packet that the tunnel endpoint can carry. | ||||||||||||||||||
| Use Proxy Server |
Select Yes to enable a proxy server. The Proxy Server enables communication between GigaVUE-FM and the Azure Public Endpoints over the internet. |
||||||||||||||||||
In the Azure Virtual Node Deployment page, select or enter the following details and click Save:
|
Field |
Description |
|
Centralized Virtual Network |
Alias of the centralized VNet in which the G-vTAP Controllers, V Series Proxies, and the GigaVUE V Series nodes are launched. |
|
Authentication Type |
SSH Public Key is the only supported authentication type for V Series 2 solution. |
|
SSH Public Key |
The SSH public key for the GigaVUE fabric nodes. |
|
Resource Group |
The Resource Groups created in Azure for communication between the controllers, nodes, and GigaVUE-FM. |
|
Security Groups |
The security group created for the GigaVUE fabric nodes. |
|
Configure a V Series Proxy |
Select Yes to configure a V Series Proxy for the connection. |
In the G-vTAP Controller section, select or enter the following details:
|
Field |
Description |
||||||||||||
|
Controller Version(s) |
The G-vTAP Controller version you configure must always be the same as the G-vTAP Agents’ version number deployed in the VM machines. If there are multiple versions of G-vTAP Agents deployed in the VM machines, then you must configure multiple versions of G-vTAP Controllers that matches the version numbers of the G-vTAP Agents. Note: If there is a version mismatch between G-vTAP controllers and G-vTAP Agents, GigaVUE-FM cannot detect the agents in the instances. To add G-vTAP Controllers:
|
||||||||||||
|
Management Subnet |
IP Address Type: Select one of the following IP address types:
Subnet: Select a management subnet for G-vTAP Controller. The subnet that is used for communication between the G-vTAP Controllers and the G-vTAP Agents, as well as to communicate with GigaVUE-FM. Every fabric node (both controllers and the nodes) need a way to talk to each other and GigaVUE-FM. So, they should share at least one management subnet. Note: Some instance types are supported in Azure platform. Refer to Microsoft Azure documentation to learn on supported instance types. |
||||||||||||
|
Additional Subnets |
(Optional) If there are G-vTAP Agents on subnets that are not IP routable from the management subnet, additional subnets must be specified so that the G-vTAP Controller can communicate with all the G-vTAP Agents. Click Add to specify additional data subnets, if needed. Also, make sure that you specify a list of security groups for each additional subnet. |
||||||||||||
|
Tags |
(Optional) The key name and value that helps to identify the G-vTAP Controller instances in your Azure environment. For example, you might have G-vTAP Controllers deployed in many regions. To distinguish these G-vTAP Controllers based on the regions, you can provide a name that is easy to identify such as us-west-2-gvtap-controllers. To add a tag:
|
Note: In a connection, you can configure multiple versions of a G-vTAP Controller and you can only configure one version of a V Series Proxy.
In the V Series Proxy section, select or enter the values for the fields as described in the previous G-vTAP Controller configuration table. The fields of the V Series Proxy configuration are similar to G-vTAP Controller configuration.
In the V Series Node section, select or enter the following details:
|
Fields |
Description |
|||||||||
|
Image |
From the Image drop-down list, select a V Series node image. |
|||||||||
|
Size |
From the Size down-down list, select a size for the V Series node. The default size for V Series configuration is Standard_D4s_v4. |
|||||||||
|
IP Address Type |
Select one of the following IP address types:
|
|||||||||
|
Management Subnet |
Subnet: Select a management subnet for V Series node. The subnet that is used for communication between the G-vTAP Agents and the V Series nodes, as well as to communicate with GigaVUE-FM. Every fabric node (both controllers and the nodes) needs a way to talk to each other and GigaVUE-FM. So, they should share at least one management subnet. |
|||||||||
|
Data Subnets |
The subnet that receives the mirrored VXLAN tunnel traffic from the G-vTAP Agents. Select a Subnet and the respective Security Groups. Click Add to add additional data subnets. Note: Using the Tool Subnet checkbox you can indicate the subnets to be used by the V Series node to egress the aggregated/manipulated traffic to the tools. |
|||||||||
|
Tag(s) |
(Optional) The key name and value that helps to identify the V Series node instances in your Azure environment. For example, you might have V Series node deployed in many regions. To distinguish these V Series node based on the regions, you can provide a name that is easy to identify. To add a tag:
|
Use the following buttons to manage your Azure connections :
|
Button |
Description |
| Create | Use to create new connection. |
| Actions |
Provides the following options:
|
| Refresh Inventory | Use to refresh the selected connection. |
| Export | Use to export the details from the Connections page into an XLS or a CSV file. |
To create Application Intelligence sessions, refer to Create an Application Intelligence Session in Virtual Environment.
Refer the following Gigamon Validated Design for more detailed information on how to achieve deep observability in Azure
When setting up a traffic flow, it is important to define the selection criteria for the source of traffic. Use the Source Selectors page for configuring the source of traffic to the GigaVUE V Series nodes.
Note: You need not configure the Source Selectors if the environment is selected as NSX-T. The NSX-T manager is responsible for configuring the sources.
To configure the Source Selectors:
- Select Inventory > Resources > Source Selectors.
-
On the Source Selectors page, on the VM tab, click Create.
The Create Source Selector wizard appears.
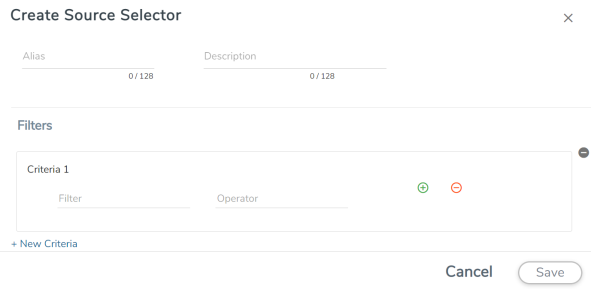
- Enter or select the required information:
Field Description Alias Name of the source Description Description of the source Filters You can create a filter template from the Filters option Criteria 1 Criteria to filter the traffic source.
Note: You can create multiple criteria.
Filter The criteria based on which the traffic is filtered. Select from the list of available filters.
Operator Select the required operator based on the filter selected. Options are:
- Starts with
- Ends with
- excludes
- equals
- between
Values The values for the filter. - Click Save to save the filter.
- If you have configured multiple filters in a criterion, then the traffic will be filtered only if all the filter rules are true.
- If you have configured multiple criteria, then the traffic will be filtered even if one of the criteria is true.
A tunnel endpoint can be created using a standard L2GRE, VXLAN, or ERSPAN tunnel. The tunnel can be an ingress tunnel or an egress tunnel.
Note: VXLAN is the only supported tunnel type for Azure.
To configure the tunnels:
- Select Inventory > Resources > Tunnel Specifications.
-
On the Tunnel Specifications page, navigate to VM tab and click Create. The Create Tunnel Specification wizard appears.
- Enter or select the following information:
- Choose In (Decapsulation) for creating an Ingress tunnel, Tunnel Spec for the Source should always have the Traffic Direction as IN, signifying an ingress tunnel. Enter values for the Key.
- Choose Out (Encapsulation) for creating an Egress tunnel from the V Series node to the destination endpoint. Select or enter values for MTU, Time to Live, DSCP, PREC, Flow Label, and Key.
- ERSPAN, L2GRE, and VXLAN are the supported Ingress tunnel types. You can configure Tunnel Endpoint as your first level entity in Monitoring Session.
- L2GRE and VXLAN are the supported Egress tunnel types.
- For Azure connection, VXLAN is the supported Ingress and Egress tunnel type.
- Click Save to save the configuration.
|
Field |
Description |
|
Alias |
The name of the tunnel endpoint. Note: Do not enter spaces in the alias name. |
|
Description |
The description of the tunnel endpoint. |
|
Tunnel Type |
The type of the tunnel. Select ERSPAN, or L2GRE, or VXLAN to create a tunnel. Do not select UDPGRE tunnel type. Note: VXLAN is the only supported tunnel type for Azure. |
|
Traffic Direction |
The direction of the traffic flowing through the V Series node. |
|
IP Version |
The version of the Internet Protocol. Select IPv4 or IPv6. |
|
Remote Tunnel IP |
For Ingress tunnel, Remote Tunnel IP is the IP address of the tunnel source. For Egress tunnel, Remote Tunnel IP is the IP address of the tunnel destination endpoint. |