GigaSMART Out-of-Band SSL Decryption
Required License: SSL Decryption for Out-of-Band
GigaVUE H Series nodes support Secure Sockets Layer (SSL) decryption. SSL is a cryptographic protocol that adds security to TCP/IP communications such as Web browsing and email. The protocol allows the transmission of secure data between a server and client who both have the keys to decode the transmission and the certificates to verify trust between them. Out-of-band SSL decryption delivers decrypted traffic to out-of-band tools that can then detect threats entering the network.
Out-of-band SSL decryption is a pillar of the GigaSECURE Security Delivery Platform. For an overview of GigaSECURE, refer to GigaSECURE Security Delivery Platform.
On GigaVUE H Series nodes, GigaSMART line cards or modules perform the decryption of SSL traffic. Using GigaSMART for decryption offloads the decryption function from tools and offers improved tool performance by removing this computationally intensive task. GigaSMART provides a centralized decryption point. Decrypted SSL traffic can be sent from GigaSMART to inspection tools for further analysis, for example, to look at encrypted communications or to detect malware.
Before SSL traffic is decrypted, the de-duplication GigaSMART operation can be performed. Decrypted traffic from the GigaSMART line card or module can be filtered, aggregated, and replicated and then sent to one or more monitoring tools for analysis.
Out-of-band SSL decryption is supported on the following GigaVUE H Series products with GigaSMART line cards or modules installed:
| • | GigaVUE-HD4/HD8 |
| • | GigaVUE-HC3 |
| • | GigaVUE-HC2 |
| • | GigaVUE-HC1 |
| • | GigaVUE-HB1 |
Use out-of-band SSL decryption on the GigaSMART line card or module with passive or offline traffic. Tap the traffic to and from a server and pass it to the GigaVUE H Series node with the GigaSMART line card or module.
Out-of-band SSL decryption operations can be assigned to GigaSMART groups consisting of multiple engine ports. Refer to Groups of GigaSMART Engine Ports for details.
For secure storage of private keys, NCipher (formerly Thales) Hardware Security Module (HSM) is integrated with out-of-band SSL decryption. Refer to NCipher HSM for SSL Decryption for Out-of-Band Tools for details.
Gigamon also offers inline SSL decryption, which inspects SSL encrypted traffic inline. Refer to the Inline SSL Decryption Guide for details.
Introducing Out-of-Band SSL Decryption
SSL encryption secures traffic between a client and a server, such as a Web server. SSL decryption uses keys to decode the traffic between the client and server.
SSL and Transport Layer Security (TLS) protocols consist of a set of messages exchanged between a client and server to set up and tear down the SSL connection between them. To set up the connection, the client and server use the Public Key Infrastructure (PKI) to exchange the bulk encryption keys needed for data transfer.
Figure 871: Basic SSL Handshake shows the basic SSL handshake between a client and server to establish a session. The messages are unencrypted up to step 6 in Figure 871: Basic SSL Handshake. The messages are encrypted after step 6, including the step 9 Finished message.
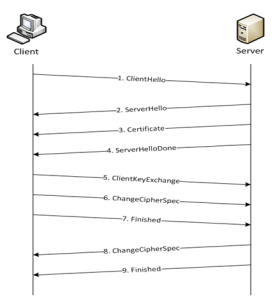
Figure 871: Basic SSL Handshake
Once a session has been established, the keys are saved so a session can be resumed efficiently later. Figure 872: Resumed SSL Handshake shows the resumed SSL handshake, with fewer steps.
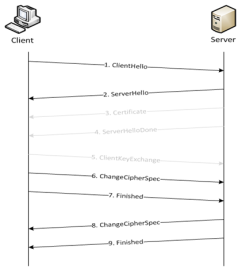
Figure 872: Resumed SSL Handshake
Out-of-band SSL decryption can be deployed close to the server, as shown in Figure 873: Inbound (Server Side).
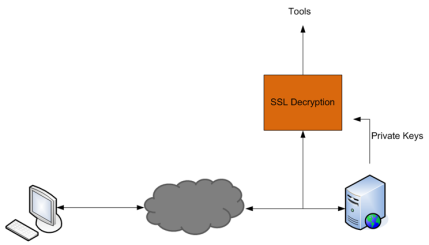
Figure 873: Inbound (Server Side)
Out-of-band SSL decryption can also be deployed close to an SSL proxy, with the server in the Enterprise domain as shown in Figure 874: Outbound (Client/Enterprise Side).
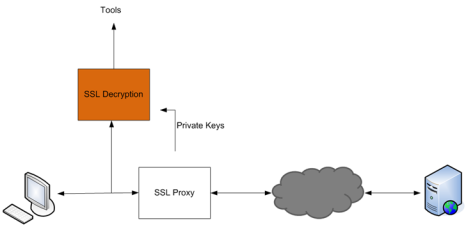
Figure 874: Outbound (Client/Enterprise Side)
In Figure 873: Inbound (Server Side), tap traffic to the server and then send it for decryption. In Figure 874: Outbound (Client/Enterprise Side), tap traffic to the proxy and then send it for decryption. You can have a deployment with either a server or a proxy, but not both.
The following sections describe out-of-band SSL decryption on GigaSMART:
| • | Supported Protocols, Algorithms, and Ciphers |
| • | Limitations |
| • | Creating and Resetting Passwords |
| • | Working with Keys and Services |
| • |
Supported Protocols, Algorithms, and Ciphers
The supported protocols are as follows:
| • | SSL 3.0 |
| • | TLS 1.0 |
| • | TLS 1.1 |
| • | TLS 1.2 |
The supported authentication (Au) is as follows:
| • | RSA |
The supported key exchange (Kx) is as follows:
| • | RSA |
The supported encryption algorithms (Enc) are as follows:
| • | NULL |
| • | RC4 |
| • | DES |
| • | 3DES |
| • | AES (including GCM mode) |
| • | CAMELLIA |
| • | SEED |
| • | IDEA |
The supported compression algorithm is as follows:
| • | NULL |
The supported digest algorithms are as follows:
| • | MD5 |
| • | SHA1 |
| • | SHA2 |
The supported key sizes are 128, 256, 512, 1024, 2048, and 4096.
The supported TLS extensions are as follows:
| • | Extended Master Secret, RFC 7627 |
| • | Encrypt-then-MAC, RFC 7366 |
The supported ciphers are listed in Table 1: Supported Ciphers for Out-Of-Band SSL decryption.
|
Cipher Name |
Kx |
Au |
Enc |
Bits |
Mac |
|
TLS_RSA_WITH_NULL_MD5 |
RSA |
RSA |
NULL |
0 |
MD5 |
|
TLS_RSA_WITH_NULL_SHA |
RSA |
RSA |
NULL |
0 |
SHA |
|
TLS_RSA_EXPORT_WITH_RC4_40_MD5 |
RSA_EXPORT |
RSA_EXPORT |
RC4_40 |
40 |
MD5 |
|
TLS_RSA_WITH_RC4_128_MD5 |
RSA |
RSA |
RC4_128 |
128 |
MD5 |
|
TLS_RSA_WITH_RC4_128_SHA |
RSA |
RSA |
RC4_128 |
128 |
SHA |
|
TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 |
RSA_EXPORT |
RSA_EXPORT |
RC2_CBC_40 |
40 |
MD5 |
|
TLS_RSA_WITH_IDEA_CBC_SHA |
RSA |
RSA |
IDEA_CBC |
128 |
SHA |
|
TLS_RSA_EXPORT_WITH_DES40_CBC_SHA |
RSA_EXPORT |
RSA_EXPORT |
DES40_CBC |
40 |
SHA |
|
TLS_RSA_WITH_DES_CBC_SHA |
RSA |
RSA |
DES_CBC |
56 |
SHA |
|
TLS_RSA_WITH_3DES_EDE_CBC_SHA |
RSA |
RSA |
3DES_EDE_CBC |
168 |
SHA |
|
TLS_RSA_WITH_AES_128_CBC_SHA |
RSA |
RSA |
AES_128_CBC |
128 |
SHA |
|
TLS_RSA_WITH_AES_256_CBC_SHA |
RSA |
RSA |
AES_256_CBC |
256 |
SHA |
|
TLS_RSA_WITH_CAMELLIA_128_CBC_SHA |
RSA |
RSA |
CAMELLIA_128_CBC |
128 |
SHA |
|
TLS_RSA_WITH_CAMELLIA_256_CBC_SHA |
RSA |
RSA |
CAMELLIA_256_CBC |
256 |
SHA |
|
TLS_RSA_WITH_SEED_CBC_SHA |
RSA |
RSA |
SEED_CBC |
128 |
SHA |
|
TLS_RSA_WITH_NULL_SHA256 |
RSA |
RSA |
NULL |
0 |
SHA256 |
|
TLS_RSA_WITH_AES_128_CBC_SHA256 |
RSA |
RSA |
AES_128_CBC |
128 |
SHA256 |
|
TLS_RSA_WITH_AES_256_CBC_SHA256 |
RSA |
RSA |
AES_256_CBC |
256 |
SHA256 |
|
TLS_RSA_WITH_AES_128_GCM_SHA256 |
RSA |
RSA |
AES_128_GCM |
128 |
SHA256 |
|
TLS_RSA_WITH_AES_256_GCM_SHA384 |
RSA |
RSA |
AES_256_GCM |
256 |
SHA384 |
All algorithms used for out-of-band SSL decryption are FIPS 140-2 compliant.
All key URLs must point to an RSA private key stored in the PEM or PKCS12 format, as follows:
| • | http://keyserver.domain.com/path/keyfile.pem |
| • | https://keyserver.domain.com/path/keyfile.pem |
| • | ftp://keyserver.domain.com/path/keyfile.pem |
| • | tftp://keyserver.domain.com/path/keyfile.pem |
| • | scp://username[:password]@keyserver.domain.com/path/keyfile.pem |
The supported applications are as follows:
| • | HTTPS |
| • | FTPS |
| • | SMTP, IMAP, and POP3 with StartTLS |
Limitations
The following are limitations of out-of-band SSL decryption:
| • | Only IPv4. |
| • | Only regular maps; no virtual ports (vports). |
| • | Only combined with the de-duplication GigaSMART operation. |
| • | Only one private key per PKCS12 file. |
| • | Only server-side authentication. |
| • | Only the protocols and ciphers listed in Supported Protocols, Algorithms, and Ciphers. If an SSL session cannot be decrypted due to having a non-supported protocol or cipher, the packets will be forwarded to the tool without decryption if the GS Parameter SSL Decryption has Decrypt Fail Action is set to Pass to Tool Port. Non-supported ciphers and protocols include SSL 2.0, TLS 1.3, Diffie-Hellman (DHE keys), Ephemeral keys, Elliptic Curves Extension, compression, and 8K key size. |
Licensing
The GigaSMART license for out-of-band SSL decryption is installed as any other license.
There are no limits to the number of out-of-band SSL decryption sessions or the number of users.
Creating and Resetting Passwords
To perform the configuration in the following section, you must have an admin level access role.
Before uploading keys or configuring SSL, you must create an SSL keychain password. The password is used to encrypt the private keys that you upload to the node.
Keychain passwords are not saved on the node. Refer to Notes about Private Keys and Passwords.
Note: When uploading SSL keys, make sure that you are not creating a duplicate key. Adding a duplicate key can cause errors.
To create an SSL keychain password, use the following steps:
| 1. | From the device view, select GigaSMART > Passive SSL > Key Store. |
| 2. | Click Keychain Password. |
The set-up page shown in figure Figure 875: SSL Keychain Password Setup Page displays.
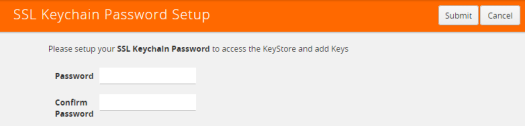
Figure 875: SSL Keychain Password Setup Page
| 3. | Enter a password in the Password and Confirm Password fields. |
You can only configure a strong password. A strong password has at least ten (10) characters and at least three (3) of the following:
| • | uppercase letters |
| • | lowercase letters |
| • | numbers |
| • | special characters |
| 4. | Click Submit. |
After keys are installed on the node, you will be prompted to enter the password after any login as well as after a node reboot, for example:
If you are a user who does not have an admin level access role, when you enter the configure terminal mode, the following message is displayed:
Password required. Please contact administrator.
If you are a user with an admin level access role, but you enter an incorrect password, the following message is displayed:
Password does not match. Please reenter the password
If an SSL keychain password is lost, it can be reset, but all existing private keys will be revoked. When there are keys installed on the node, a warning is displayed before you are prompted for the new password.
Once you have a new password, you will have to upload the keys again.
Working with Keys and Services
This section describes working with private keys as well as services. Keys must be uploaded to the GigaVUE H Series node using a unique alias. Services must be defined for each server destination that needs decryption.
To perform the configuration in the following section, you must have an admin level access role.
Encrypted private keys are saved on the node. Refer to Notes about Private Keys and Passwords.
Note: When uploading SSL keys, make sure that you are not creating a duplicate key. Adding a duplicate key can cause errors.
Upload SSL Private Keys
To upload an SSL private key, do the following:
| 1. | From the device view, select GigaSMART >Passive SSL > Key Store to open the Key Store page shown in Figure 876: SSL Key Store Page. |
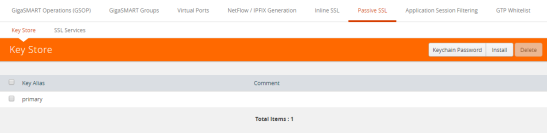
Figure 876: SSL Key Store Page
| 2. | Click Install. |
The SSL Key page shown in Figure 877: SSL Key Page displays.
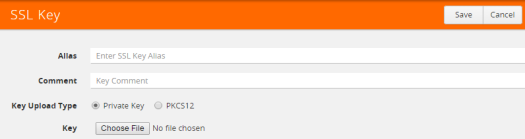
| 3. | Enter an alias for the SSL key in the Alias field. |
| 4. | Select the upload type. |
| 5. | Choose the file. |
The URL can be downloaded using HTTP, HTTPS, FTP, TFTP, SCP, and SFTP. Using a secure protocol, such as HTTPS is recommended. Only PEM encoded keys are supported.
| 6. | Click Save. |
If you choose to use Venafi, Inc. as your Electronic Key Management System (EKMS), ensure that you have the GigaVUE-FM host address and credentials to push the generated key into the selected nodes. For details on pushing keys from Venafi, contact either Venafi or Gigamon customer support.
Deleting an SSL Key
To delete a particular SSL private key, select the key on the SSL Keys page, and then select Delete. To delete all SSL private keys, select multiple keys.
Creating an SSL Service
After you have uploaded a private key, you can add a service. A service maps to a physical server, such as an HTTP server. One server can run multiple services. A service is a combination of an IP address and a server port number. Also, the key and the service must be tied together.
Prerequisites
Before creating a service, you must do the following:
| • | Upload a private key as described in Uploading SSL Private Keys |
| • | Create GigaSMART Group with SSL Decryption enabled. |
To create a service, do the following:
| 1. | From the device view, select GigaSMART > Passive SSL > SSL Services. The SSL Services page displays as shown in Figure 878: SSL Services Page. |
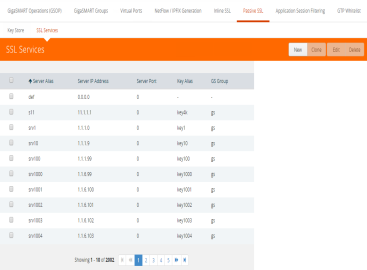
| 2. | Click New. |
| 3. | On the SSL Service configuration page, do the following: |
| • | Enter an alias. |
| • | Enter the information for the service: IP Address, Server Port. |
| • | Select the alias of SSL Key previously uploaded. For the steps, refer to Uploading SSL Private Keys. |
| • | Select the GigaSMART Group with SSL decryption enabled to associate with this SSL service. |
Figure 879: SSL Service Settings shows an example of an SSL Service.
| 4. | Click OK. |
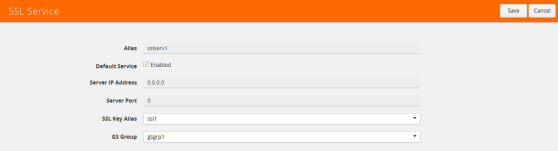
Figure 879: SSL Service Settings
Deleting a Service
To delete a particular SSL service select the service on the SSL Services page, and then select Delete. To delete all SSL services, select multiple keys.
Notes about Private Keys and Passwords
Consider the following notes about private keys and passwords:
| • | Encrypted private keys are stored on the node. When a private key is uploaded, it is encrypted with a password before it is stored, therefore keys are password-protected. Keychain passwords are not stored on the node. |
| • | Because only encrypted private keys are stored on the node and because the keychain password is not stored on the node, after any node reboot you will be prompted to enter the password. Until the password is entered, out-of-band SSL decryption is not working. |
| • | Key content cannot be displayed. |
| • | Keys that are synchronized across a cluster are encrypted. |
ECODES for Troubleshooting Out-of-Band SSL Decryption
Use the following table of ECODE messages to assist with troubleshooting out-of-band SSL decryption:
|
ECODE |
Description |
|
81 |
TCP flow errors detected. Make sure you see the complete TCP flow. Use the de-duplication GigaSMART operation with out-of-band SSL decryption. |
|
103 |
Session limit reached. The session table has been exhausted. If the session timeout (session-timeout) value is large, lower it. |
|
104 |
Key/ticket cache limit reached. The allocated cache entries have been used up. If the timeout (key-cache-timeout or ticket-cache-timeout) value is large, lower it. |
|
206 |
No server info. A flow has been received for which service-key mapping is not defined. |
|
213 |
Packets for missed TCP handshake. Packets were received for TCP flows that do not exist. If the device was just started, this should trend down quickly. |
|
218 |
Unknown SSL version. An SSL handshake processing error occurred. Use the de-duplication GigaSMART operation with out-of-band SSL decryption. |
|
221 |
Unknown SSL version. An unsupported SSLv2 handshake was seen. |
|
222 |
Protocol error. An unsupported protocol version was seen. |
|
225 |
Unsupported cipher. The cipher suite cannot be decrypted. |
|
226 |
Pre-master secret error. Check that the private key is correct and that the session is complete. |
|
228 |
Generic decryption error. Usually indicates errors in the handshake. Check that you are getting the full session from both sides. |
|
231 |
Invalid MAC. Likely indicates that invalid or truncated packets have been received. |
|
232 |
Session not in cache. Indicates that you are trying to decrypt a restarted session where the original negotiation was not seen. These should trend down in time, but if they do not, increase the key-cache-timeout value. |
|
237 |
Cannot decrypt ephemeral key based encryption. One of the Ephemeral/PFS ciphersuites, usually Diffie-Hellman Ephemeral, has been seen. These are not supported. |
|
245 |
Ticket not in cache. This is usually not an error. Indicates that you are trying to decrypt a restarted session where the original negotiation was not seen. These should trend down in time, but if they do not, increase the ticket-cache-timeout value. |
Displaying Out-of-Band SSL Decryption Flow Ops Report
To display the Flow Ops report for out-of-band SSL decryption:
| 1. | From the device view, select GigaSMART > GigaSMART Groups > Report. The Report page displays as shown in Figure 880: Report Page. |
| 2. | Select report type SSL Decryption and select a GigaSMART group from the drop-down menu. |
| 3. | Click Generate. The SSL Decryption Report Summary displays as shown in Figure 881: SSL Decryption Report Summary. |
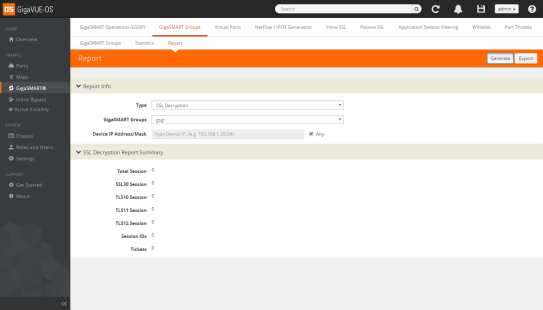
Figure 881: SSL Decryption Report Summary
The fields in the SSL Decryption Report Summary are as follows:
| • | Total Session—The total number of out-of-band SSL decryption sessions. |
| • | SSL30 Session—The cumulative total number of SSL 3.0 sessions. |
| • | TLS10 Session—The cumulative total number of TLS 1.0 sessions. |
| • | TLS11 Session—The cumulative total number of TLS 1.1 sessions. |
| • | TLS12 Session—The cumulative total number of TLS 1.2 sessions. |
| • | Session IDs—The number of concurrent session IDs. |
| • | Tickets—The number of current TLS tickets. |



