Passive SSL Decryption
GigaVUE V Series 2 nodes support Secure Sockets Layer (SSL) decryption. SSL is a cryptographic protocol that adds security to TCP/IP communications such as Web browsing and email. The protocol allows the transmission of secure data between a server and client who both have the keys to decode the transmission and the certificates to verify trust between them. Passive SSL decryption delivers decrypted traffic to out-of-band tools that can then detect threats entering the network.
Note: Passive SSL Decryption is called as SSL Decrypt on GigaVUE V Series 2.
Licensing
GigaSMART Passive SSL Decryption on V Series 2 follows Volume Based License. (VBL).
Volume Based License (VBL)
All the V Series 2 nodes connected to GigaVUE-FM periodically reports the stats. GigaVUE-FM adds the required licensing tags into the Elasticsearch. All licensed applications, when running on the node, generate usage statistics. In the Volume-Based Licensing scheme, a license entitles specific applications on your devices to use a specified amount of total data volume over the term of the license. The distribution of the license to individual nodes or devices becomes irrelevant for Gigamon’s accounting purpose. GigaVUE-FM tracks the total amount of data processed by the various licensed applications and provides visibility into the actual amount of data, each licensed application is using on each node, and track the overuse if any. You will have grace period for each license that are conveyed in the license file.
For purchasing licenses with the VBL option, contact our Gigamon Sales. Refer to Contact Sale.
Configure Passive SSL Decryption on V Series 2
To configure passive SSL Decryption on V Series 2, follow the steps given below:
Prerequisite: Register the nodes on the Monitoring Domain. Refer Configure GigaVUE V Series Nodes using VMware ESXi for more detailed information.
Upload SSL Keys
To upload an SSL private key, do the following:
- On the left navigation pane, select Inventory >Resources > Security to open the Security page. Select SSL Keys on the top navigation bar.
- Click Add. The Create SSL Key page appears.
- In the Create SSL Key page, enter the following details:
- For Alias, enter an alias for the SSL key.
- For Description, enter any additional information for the SSL key.
- For Key Upload Type, select PEM or PKCS12.
- (optional) For Passphrase, enter a passphrase for the key.
- Select a Private Key by pasting the copied key in PEM format or installing from URL or installing from local directory.
- Select a Certificate by pasting the copied key in PEM format or installing from URL or installing from local directory.
Note: Install from URL option only supports scp protocol.
- Click Save.
Note: Passive SSL Decryption on V Series 2 does not support HSM.
Delete SSL Keys
To delete a particular SSL key select the key on the SSL Keys page, and then select Delete. To delete all SSL Keys, select the Delete All button.
Create SSL Service
After you have uploaded a private key, you can add a service. A service maps to a physical server, such as an HTTP server. One server can run multiple services. A service is a combination of an IP address and a server port number. Also, the key and the service must be tied together.
Prerequisites
Before creating a service, you must do the following:
| Upload a private key as described in Upload SSL Keys |
To create a service, do the following:
| 1. | On the left navigation pane, select Inventory >Resources > Security to open the Security page. Select SSL Service on the top navigation bar.The SSL Services page appears. |
| 2. | Click Add. |
| 3. | On the SSL Service configuration page, do the following: |
| Enter an alias. |
| Enter the information for the service: Server IP Address, Server Port. |
| 4. | Click Save. |
Delete SSL Service
To delete a particular SSL service select the service on the SSL Services page, and then select Delete. To delete all SSL services, select the Delete All button.
Notes about Private Keys and Passwords
Consider the following notes about private keys and passwords:
| Encrypted private keys are stored on the node. When a private key is uploaded, it is encrypted with a password before it is stored, therefore keys are password-protected. Keychain passwords are not stored on the node. |
| Because only encrypted private keys are stored on the node and because the keychain password is not stored on the node, after any node reboot you will be prompted to enter the password. Until the password is entered, Passive SSL decryption is not working. |
| Key content cannot be displayed. |
| Keys that are synchronized across a cluster are encrypted. |
Key Mapping
After adding the SSL Service, now you map the private key with the service using Key Mapping.
To map a key with the service, follow the steps given below,
- On the left navigation pane, select Inventory >Resources > Security to open the Security page. Select SSL Key Mapping on the top navigation bar.
- Click Add.
- Enter the Key Mapping Alias.
- Select the SSL Service and Key Alias from the drop-down.
- Click Save.
Delete SSL Key Mappings
To delete a particular SSL key map select the key mapping on the SSL Key Mapping page, and then select Delete. To delete all SSL Key Mapping, select the Delete All button.
Add SSL Decrypt to Monitoring Session
After mapping your keys with service, to add GigaSMART applications to V series 2, follow the steps given below,
- Create a new monitoring session. Refer to Create a Monitoring Session for more detailed instructions.
- Drag and drop SSL Decrypt from APPLICATIONS to the graphical workspace.
- Click the SSL Decrypt application and select Details.
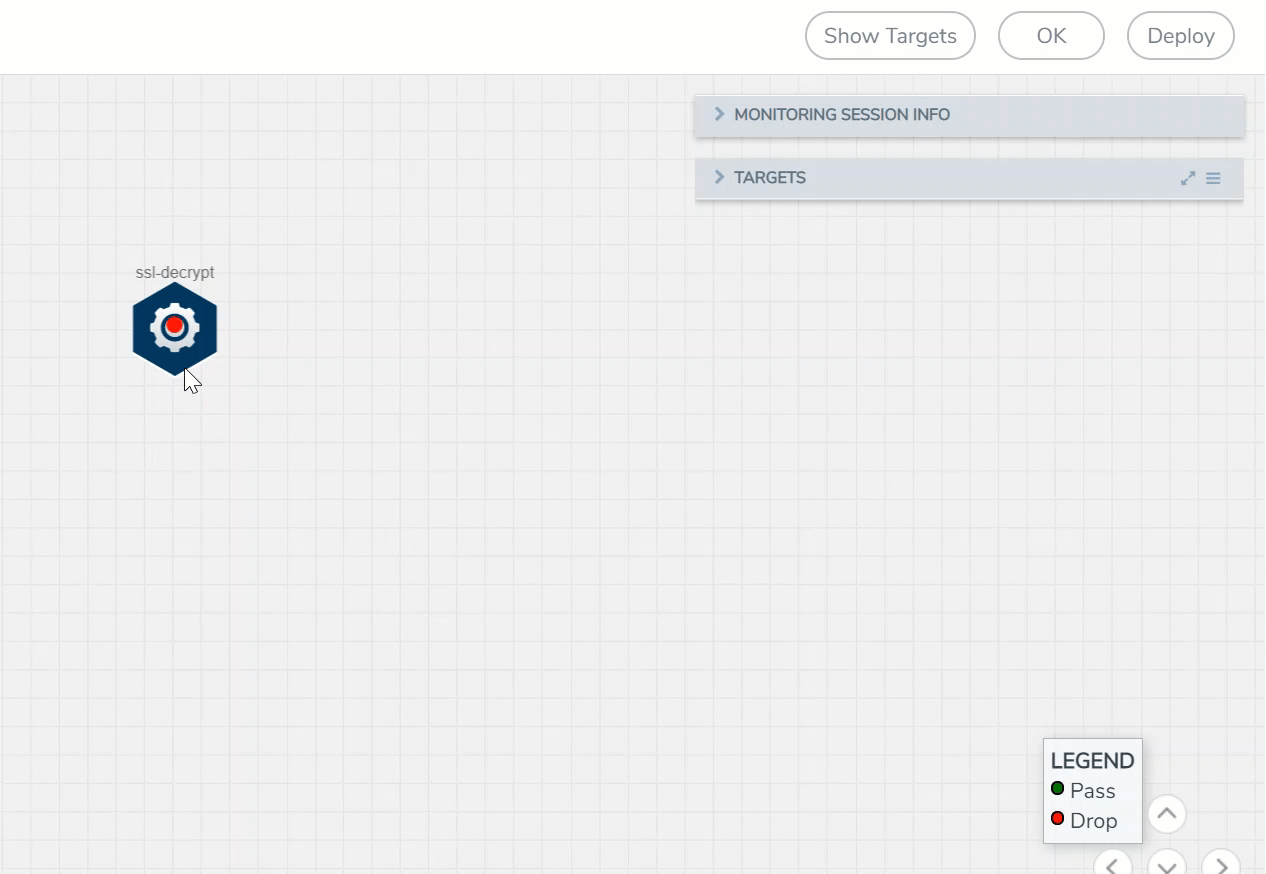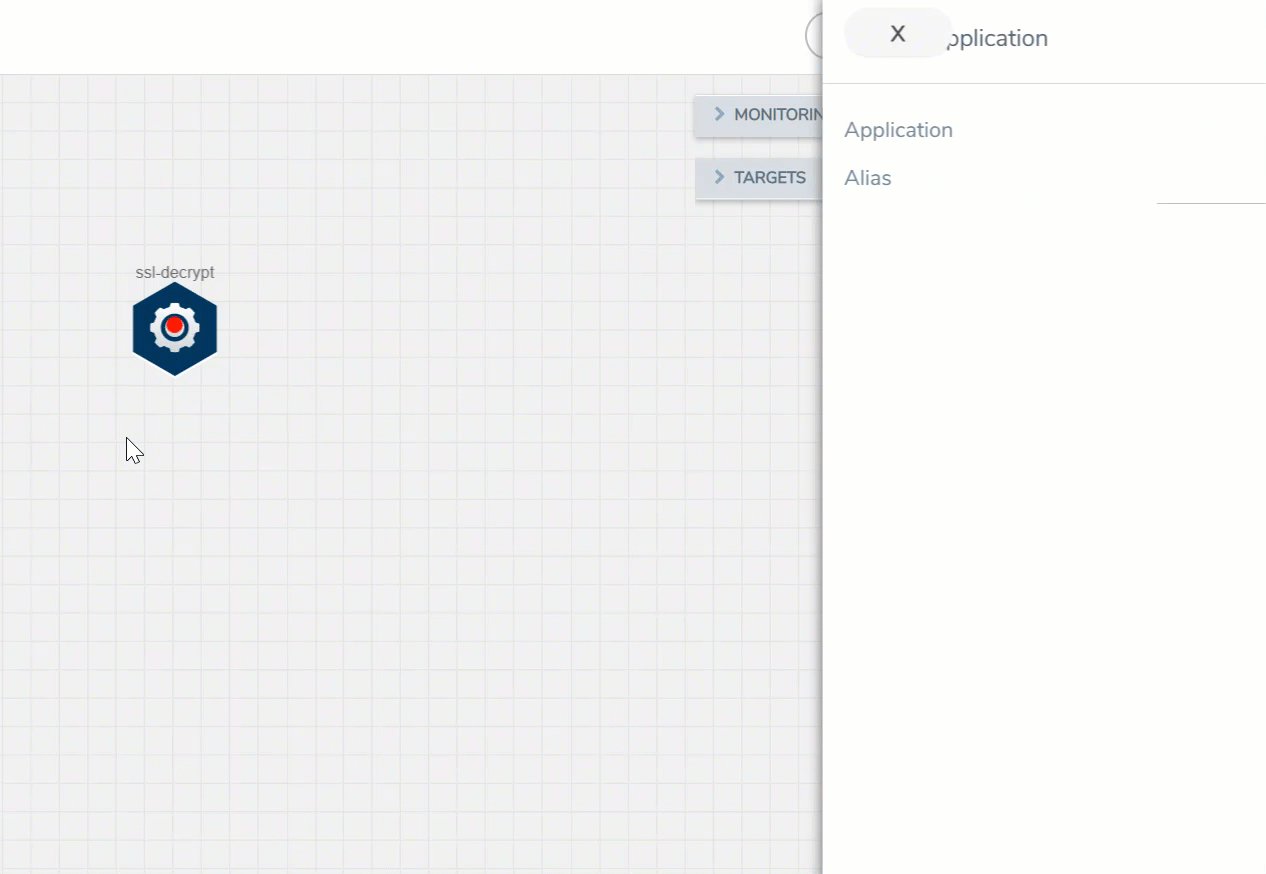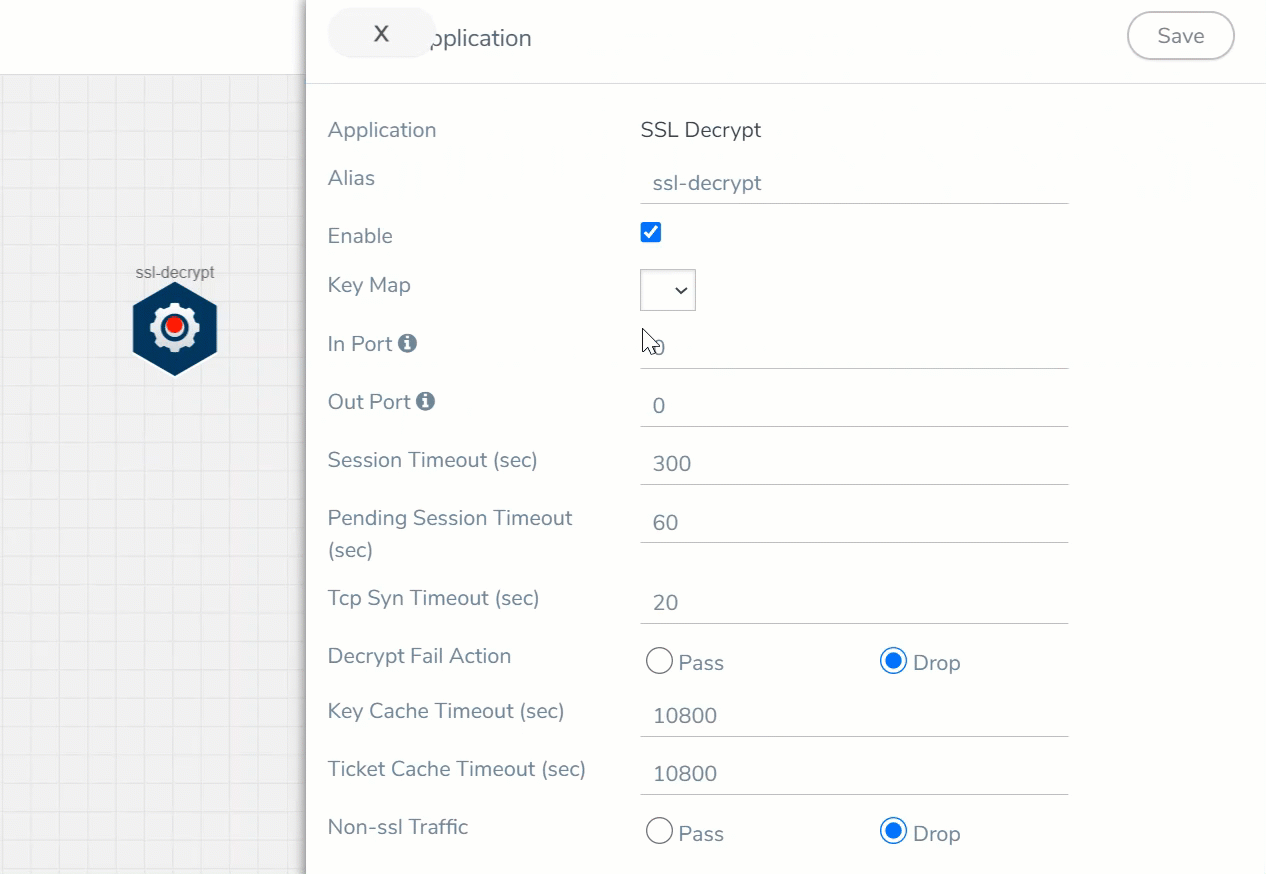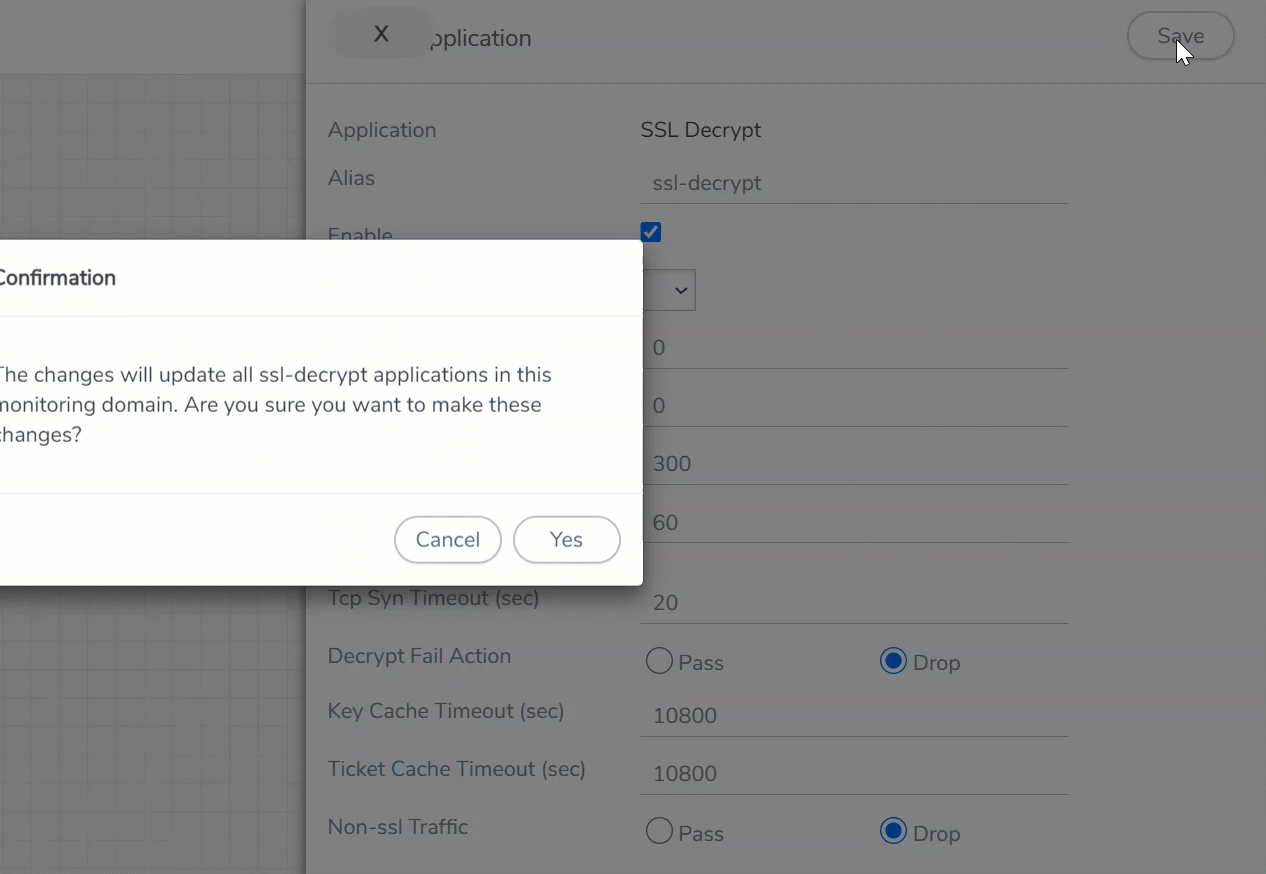
- Select the Enable checkbox to enable the application.
- Select the Key Map (created in the previous step) from the drop-down.
- Click Save.
- Click Deploy. The Select nodes to deploy the monitoring session page appears.
- Select the nodes you want to deploy and select an interface for each node. Then, click Deploy.
View Application Statistics
After adding SSL Decrypt to the monitoring session, to view the application statistics, open the Monitoring Session Statistics page. Refer to View Monitoring Session Statistics for more detailed information.
- Click View Monitoring Session Diagram. The monitoring session diagram appears, click the SSL Decrypt application.
- The ssl-decrypt application statistics page appears.
- You can view the following in the SSL application statistics page:
- Application: The application statistics are displayed here.
- Sessions: To view the session summary and session details of the SSL Decryption application, select the V Series Node IP and enter the Server Name and Client/ Server IP address. Then click Apply.
- Server Certificates: To view the server certificate statistics, select the V Series Node IP from the drop-down and enter the Key Alias. Then, click Apply.
- Services: All the service related statistics are displayed here. To view the statistics, select the V Series Node IP and the Service Alias from the drop-down and click Apply.
- Error Codes: The error messages are displayed here.
Server Certificates, Services and Error Codes pages has Refresh and Reset button, which helps you to refresh and reset the statistics.



