Configure Flexible Inline TLS/SSL Decryption Solution
Refer to the following sections that provide details about the flexible inline decryption solution and instructions on how to configure it:
| Flexible Inline TLS/SSL Decryption Solution |
| Benefits of Flexible Inline TLS/SSL Decryption Solution |
| Flexible Inline TLS/SSL Decryption Solution—Rules and Notes |
| Configure Flexible Inline TLS/SSL Decryption Solution |
Flexible Inline TLS/SSL Decryption Solution
The flexible inline TLS/SSL decryption solution combines the flexible inline arrangements feature with the inline TLS/SSL decryption solution. It includes the GigaSMART-based packet processing, which is the inline TLS/SSL decryption functionality into the flexible inline arrangements framework. In the flexible inline TLS/SSL decryption solution, the outer maps guide the inline traffic to GigaSMART for preprocessing. The inner map guides the traffic processed by GigaSMART through a user-defined sequence of inline tools and inline tool groups.
1 illustrates an example of how the inline TLS/SSL decryption functionality is incorporated in the flexible inline arrangements framework to form the flexible inline decryption solution.
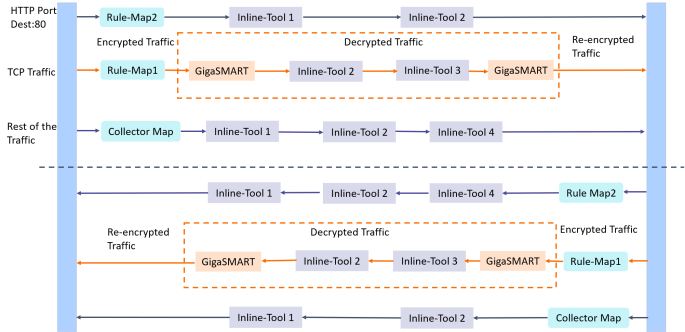
| 1 | Flexible Inline Decryption Solution |
In this example, the HTTP Port Destination:80 traffic is guided through the Flexible inline map, Rule Map2 to the sequence of inline tools, Inline Tool 1 and Inline Tool 2. The TCP traffic is encrypted and guided through Rule Map1 to GigaSMART, where it is decrypted and guided to Inline Tool 2 and Inline Tool 3. The decrypted traffic is guided back to GigaSMART, and then it is re-encrypted and routed to the network. Here, the Rule Map 1 is the outer map, which guides the traffic to GigaSMART for preprocessing. The inner map guides the traffic processed by GigaSMART through a series of inline tools or inline tool groups.
The rest of the traffic is guided through the Collector Map to a series of inline tools, and then to the network.
2 illustrates the different maps that guide the traffic in the flexible inline TLS/SSL decryption solution.
The outer maps are similar to the flexible inline maps but include virtual port alias along with inline tools and inline tool groups as the destination port. The same virtual port alias can be used in multiple outer maps.
Depending on the flexible inline TLS/SSL decryption solution that you create, there may be two types of inner maps:
| Inner Proxy Maps, which guides the traffic from GigaSMART to the inline tools or inline tool groups. |
| Inner Non-proxy Maps or Network-end Maps, which guide the traffic that is bypassed from GigaSMART to the inline tools or inline tool groups. |
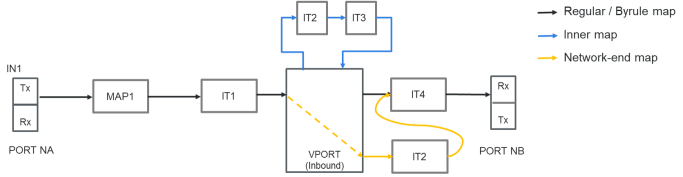
| 2 | Flexible Inline Decryption Maps |
Benefits of Flexible Inline TLS/SSL Decryption Solution
The flexible inline TLS/SSL decryption solution incorporates the inline TLS/SSL decryption with the flexible inline arrangement and offers the following benefits:
| Enables you to perform the inline decryption configuration, required map deployments, and flexible inline flow configurations, all in one canvas. |
| Shares the same inline tool or inline tool group across multiple inline network links and across multiple inline maps. Refer to 3 Flexible Inline TLS/SSL APP—Deployed. |
| Allows you to tap OOB copies of decrypted traffic from GigaSMART, either before or after the inspection of security tools. Refer to 3 Flexible Inline TLS/SSL APP—Deployed. |
| Allows you to selectively decrypt and guide traffic to the attached inline tools or inline tool groups. |
Flexible Inline TLS/SSL Decryption Solution—Rules and Notes
Keep in mind the following rules and notes when working with flexible inline decryption solution:
| When you want to migrate from the inline decryption to the flexible inline decryption solution, |
| ensure that you delete all the inline decryption virtual ports, GigaSMART, and maps configurations, and then reconfigure them using the flexible inline canvas. However, if there are OOB maps from the inline network ports, before you delete the OOB maps, ensure that the Traffic Path for the inline network is not set to ‘Bypass’. |
| It is recommended to delete the OOB map from vPort before deleting other maps. If the OOB map from the vPort is not deleted while deleting all the inline TLS/SSL maps, then GigaVUE‑FM throws an error on first time. You need to click Delete All again to delete all the maps. |
| Modifying the VLAN settings on an out-of-band map is not allowed if another out-of-band map has the same port as destination. |
| When there is a multiple tool failover across the inner and outer maps; and if any of the tool comes up, the traffic in the inline network does not flow as expected. |
| If you want to switchover from the flexible inline decryption solution to the inline decryption solution, you must delete the flexible inline SSL APP, and then reconfigure the ports, GigaSMART, and maps using the inline decryption workflow. |
| When you configure the flexible inline decryption solution using GigaVUE-FM, the keychain password will be unlocked automatically when the device participating in the solution reboots. |
| If an inline TLS/SSL profile is used across multiple map configurations with different inline network pairs, the tool set used across the maps is also the same. Consider the following example: |
Flexible Inline Map 1 with inline network pair 1 uses inline TLS/SSL Profile 1 with tools A and B.
Flexible Inline Map 2 with inline network pair 2 also uses inline TLS/SSL Profile 1. This map also has tools A and B (filled in automatically). You cannot configure this as A or C or A, C.
The following combinations are not supported:
Flexible Inline TLS/SSL Decryption
Inline Network LAG When you attempt to add an Inline SSL App to an Inline Network LAG Flexible Map you get the following error message: "An Inline SSL APP cannot be used when the traffic source is an inline network LAG" as shown in below figure.
_735x623.png)
For the Flexible Inline TLS/SSL Maps, tag of the outer map cannot be edited in the configuration canvas. To change the tag, follow these steps:
a. delete the map
b. deploy the solution
c. re-add the map with the updated tag and deploy the solution again.
Traffic is not decrypted when inline-network traffic path is in monitor mode.
Setting the Flex Traffic Path of inner chain Inline-tools as “Drop” does not drop the Inline TLS/SSL traffic and continues to reach the Inline network egress.
Configure Flexible Inline TLS/SSL Decryption Solution
Following are the prerequisites that you must complete before you configure the flexible inline decryption solution:
| Configure the required inline networks or inline network bundle. Refer to Configure Inline Network Ports and Inline Network or Configure Inline Network Bundle. |
| Configure the required inline tools. Refer to Configure Inline Tool Ports and Inline Tools. |
| Configure the required inline tool group. Refer to Configure Inline Tool Group. |
| Ensure that there are no inline decryption configurations such as inline decryption policy, inline decryption virtual port, GigaSMART group, GigaSMART operations, or inline decryption map configured on the device. |
To configure a flexible inline decryption solution:
| 1. | On the left navigation pane, go to Physical > Orchestrated Flows > Inline Flows, and then click Configuration Canvas to create a new Flexible Inline Canvas. |
| 2. | In the Flexible Inline Canvas that appears, select the required device for which you want to configure the flexible inline decryption solution. |
| 3. | Click the ‘+’ icon next to the Inline SSL APP option to create a new flexible inline decryption solution. |
| 4. | In the Inline SSL APP page that appears, enter a name for the Inline SSL APP, and then complete the required fields. Refer Inline SSL App—Field References for details. |
| 5. | Click OK to save the configurations. |
| 6. | Drag and drop the required inline network or inline network bundle in to the flexible inline canvas. |
| 7. | Drag and drop the flexible inline map into the canvas. |
| 8. | In the Properties pane, in the Alias and Description fields, enter the name and description of the inline map. |
| 9. | Enter the Tool Side VLAN Tag for the inline network for which you are configuring the map. |
| 10. | Select the TPID for the Tool Side VLAN Tag. The default value of TPID is 0x8100. You can select the other supported values 0x9100 and 0x88a8 from the drop-down list. |
| 11. | Add the required rules for the inline map, and then click OK to save the configuration. |
| 12. | Drag and drop the Inline SSL APP into the canvas. |
| 13. | Drag and drop the required inline tools or inline tool group into the canvas. |
| 14. | Drag and drop the OOB Copy into the canvas, if required. |
| 15. | Click Deploy. |
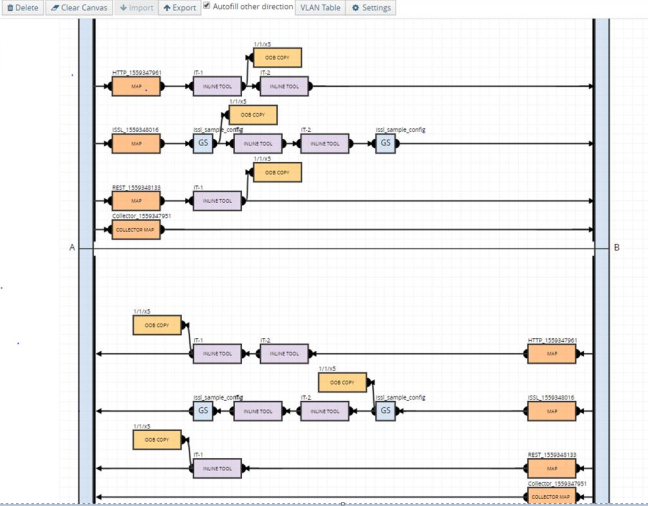
| 3 | Flexible Inline TLS/SSL APP—Deployed |
Inline SSL App—Field References
The following table lists and describes the attributes that define the flexible inline decryption solution.
|
Field |
Description |
||||||||||||||||||||||||||||||||||||
|
Alias |
Enter a unique name for the flexible inline SSL APP. |
||||||||||||||||||||||||||||||||||||
|
GS engines |
Select the required GigaSMART engines. |
||||||||||||||||||||||||||||||||||||
|
TLS/SSL Monitor Mode |
Select an TLS/SSL Monitor Mode from one of the following options:
Refer to Inline TLS/SSL Monitor Mode for details. |
||||||||||||||||||||||||||||||||||||
|
HSM Group |
Select a HSM Group alias that you have configured from the drop-down list. Select Disable from the drop-down list to disable the HSM Group. Refer to Configure Hardware Security Model (HSM) for details. Notes:
|
||||||||||||||||||||||||||||||||||||
|
Advanced Session Statistics |
Enable this option to visualize advanced Inline SSL Session dashboards, such as Session Insights and Session Table, in the Fabric Health Analytics dashboard. The basic dashboards are available by default as you configure an Inline SSL session. Refer Default Dashboards and GigaSMART Inline TLS/SSL Dashboards to know more. |
||||||||||||||||||||||||||||||||||||
|
Keychain Password |
The keychain password must be configured before installing certificates and keys. Refer to Configure Keychain Password for details. To add or reset the Keychain Password:
|
||||||||||||||||||||||||||||||||||||
|
Add new keys |
To configure a certificate-key pair:
|
||||||||||||||||||||||||||||||||||||
|
Deployment Type |
Select one of the following deployment types:
Refer to TLS/SSL Keys and Certificates and Generate and Add a Certificate to Key Store for details. |
||||||||||||||||||||||||||||||||||||
|
Configurations |
|||||||||||||||||||||||||||||||||||||
|
Default Action |
Select one of the following options :
|
||||||||||||||||||||||||||||||||||||
|
URL Cache Miss Action |
Select one of the following options:
|
||||||||||||||||||||||||||||||||||||
|
Tool Fail Action |
The failover action taken in response to a failure of an inline tool. Select one of the following options:
|
||||||||||||||||||||||||||||||||||||
|
Tool Bypass |
Select the required options:
|
||||||||||||||||||||||||||||||||||||
|
High Availability |
Select the check box to detect the link switchover by upstream device that is in active or standby mode. Note: Do not select this check box if the inline network links are in active state. Refer to High Availability Active Standby for details. |
||||||||||||||||||||||||||||||||||||
|
Network Group Multiple Entry |
Select this check box to allow the traffic from different inline network to reenter GigaSMART. Refer to Inline Network Group Multiple Entry for details. |
||||||||||||||||||||||||||||||||||||
|
Tool Early Engage |
Select this check box to allow the inline tools to change the MAC address or VLAN IDs. When a connection request is received from the client, GigaSMART establishes the connection with the inline tool first, before connecting with the server. This helps the inline tools to modify the MAC address or VLAN IDs when sending the traffic back to the server. Refer to Tool Early Engage and One-Arm Mode for additional information and limitations. |
||||||||||||||||||||||||||||||||||||
|
Tool Early Inspect |
Select this check box to allow the inline tool to inspect the decrypted data first before connecting to the server. This will allow the inline tool to validate the data and ensure that only valid connections are sent to the server. Notes:
Refer to Tool Early Inspect for details. |
||||||||||||||||||||||||||||||||||||
|
StartTLS Port |
Enter the required SSL/TLS ports. Refer to StartTLS and HTTP CONNECT for details. |
||||||||||||||||||||||||||||||||||||
|
Session Logging |
|||||||||||||||||||||||||||||||||||||
|
Session Logging |
Select the Enable checkbox to log the Inline-TLS/SSL session related information to a remote server. |
||||||||||||||||||||||||||||||||||||
|
IP Version |
Select IPV4 or IPV6 as the IP Version for the Session Logging server. You can select one session logging configuration per GigaSMART group. |
||||||||||||||||||||||||||||||||||||
|
Remote Syslog Server IP |
Enter the IP address of the remote syslog server. |
||||||||||||||||||||||||||||||||||||
|
Associated IP Interface |
In the Associated IP interface drop-down list, select the IP interface that you assigned to the GigaSMART group. You can create the IP interface by clicking the Create IP Interface button and the IP Interface window will open. Complete the fields to create the IP Interface:
|
||||||||||||||||||||||||||||||||||||
|
Remote Syslog Port Number |
Enter the port number of the remote syslog server. |
||||||||||||||||||||||||||||||||||||
|
Log Level |
In the Log Level drop-down list, select the severity log level of the events that you want to send to the inline TLS/SSL session logging server. |
||||||||||||||||||||||||||||||||||||
|
Traffic Path |
|||||||||||||||||||||||||||||||||||||
|
Single VLAN Tag |
Enable the check box to deploy flexible inline TLS/SSL solution with a single VLAN tag. If an inline tool is involved in an inline TLS/SSL map, the inline tool can be supported across multiple maps with different single VLAN tags. Note: Deploying a flexible iSSL solution with SVT is optional, and you can choose to enable or disable the Single VLAN Tag option. If you choose to enable the Single VLAN Tag option in the iSSL solution, you should also enable the Single VLAN Tag configuration in the flex map deployed in that solution. Note: If you enable the Single VLAN tag option in the Flexible iSSL solution, you should also enable the Single VLAN Tag configuration in the inline-ssl app profile deployed in the solution Refer to Single VLAN Tagging (SVT) in iSSL for more details. |
||||||||||||||||||||||||||||||||||||
|
Tool Side VLAN Tag |
Enter the required tool side VLAN tag for the inline network. |
||||||||||||||||||||||||||||||||||||
|
TPID |
Select the TPID for the Tool Side VLAN Tag. The default value of TPID is 0x8100. You can select the other supported values 0x9100 and 0x88a8 from the drop-down list. |
||||||||||||||||||||||||||||||||||||
|
Traffic Path |
Select one of the following options:
Note: You can select the Monitoring option only if you have set the SSL Monitor Mode to either Enable or Inline.
|
||||||||||||||||||||||||||||||||||||
|
Inline Failover Action |
Select one of the following options:
|
||||||||||||||||||||||||||||||||||||
|
Security Exceptions |
You can choose to either decrypt or drop the traffic for the following certificates:
You can also choose to configure the security exceptions for certificate revocation validation based on OCSP or CRL on inline decryption profile. Select one of the following options:
Refer to Certificate Revocation List (CRL), Online Certificate Status Protocol (OCSP), CRL and OCSP, and Checking Certificate Revocation Status for details. |
||||||||||||||||||||||||||||||||||||
|
No-decrypt list/Decrypt list |
Select the following check boxes:
Select from the below operations that can be performed on an uploaded list:
If you select Append/Replace, you can enter the list using any of the following options: • Copy and Paste • Install from URL • Install from Local Directory Refer to No-decrypt Listing Policy and Decrypt Listing Policy for details. |
||||||||||||||||||||||||||||||||||||
|
Policy Rules |
Add the required policy rules for the inline decryption profile. Click Add a Rule. In the Condition field, Select one of the following options from the drop-down list:
Select one of the following options:
|
||||||||||||||||||||||||||||||||||||
|
Network Access |
Network access configuration is used to get URL categorization updates. Refer to URL Categorization for details. To configure the network access for the GigaSMART engine ports:
Notes:
|
||||||||||||||||||||||||||||||||||||
|
Decryption Port Mapping |
The TCP destination port for decrypted traffic sent to inline tools can be configured as part of the inline decryption profile. Configure the required Priority 1 map, which is user configurable and Priority 2 map, which is the default out port. Refer to Inline TLS/SSL Decryption Port Map for details. |
||||||||||||||||||||||||||||||||||||
|
Trust Store |
The trust store contains a trusted certificate authority (CA) for server validation. You can choose to either append or replace the trust store. Refer to Trust Store for details. |
||||||||||||||||||||||||||||||||||||
|
TCP Settings |
Configure the required TCP settings as follows:
|
||||||||||||||||||||||||||||||||||||
|
Split-Proxy Settings |
|||||||||||||||||||||||||||||||||||||
|
Split-Proxy |
Select the check box to enable the split proxy settings for the inline decryption solution. The TLS connection between the server and client is divided into two independent connections, and the security parameters are kept separate. |
||||||||||||||||||||||||||||||||||||
|
Non-PFS Ciphers (Server) |
Select the check box to enable the non-PFS ciphers settings for the inline decryption solution that has the split proxy settings enabled. This setting is to indirectly force the server to use protocols that are lower than TLS1.3 with non-PFS ciphers. This means that the ciphers with DHE/ECDHE key-exchange will not be used on the server side. |
||||||||||||||||||||||||||||||||||||
|
Miscellaneous (Global Settings) |
|||||||||||||||||||||||||||||||||||||
|
SSL/TLS Version |
Select the minimum and maximum SSL/TLS version. |
||||||||||||||||||||||||||||||||||||
|
Connection Reset Action |
Select one of the following options for the minimum SSL/TLS version:
Select one of the following options for the maximum SSL/TLS version:
|
||||||||||||||||||||||||||||||||||||
|
Caching persistence |
Select this check box to allow the information to be saved on the GigaVUE node in the control card’s persistent storage so that it can be retrieved in case of reboots. Refer to Cache Persistence for details. |
||||||||||||||||||||||||||||||||||||
Support for unattended restart of TLS/SSL decryption in managed nodes
The keychain is an encrypted database of certificates and private keys. On individual nodes, the keychain is stored in flash memory until reboot. The user needs to enter a keychain password to access the keychain. The keychain password is cached in the RAM of the control plane processor to allow decryption of the keychain file, but the keychain password is not cached across reboots. The SSL processing is not possible without the keychain password.
The keychain password is stored in GigaVUE‑FM to automatically unlock the keychain during reboots and processing the TLS/SSL decryption without any intervention. The keychain password is stored in an encrypted database for key protection and risk management. Enable the Auto Login option when you set up or reset the keychain password to automatically unlock the keychain during reboots.
You can configure to deploy flexible iSSL solution with a single VLAN tag. With shared mode enabled, through this support, the inline tool that is shared with a single VLAN tag in a packet will be supported in the flexible inline TLS/SSL arrangements across multiple maps with different single VLAN tags. You can configure the VLAN tags when you create the flexible inline maps.
Note: If you enable the Single VLAN tag option in Flexible iSSL solution, you should also enable the Single VLAN Tag configuration in the inline-ssl app profile deployed in the solution
Note: The PCP and CFI fields in the VLAN header cannot be retained when SVT is enabled in Flexible Inline maps and it will always be zero when sent out of the inline network ports.
You can configure a Flexible Inline SSL and RIA iSSL solution with Single VLAN Tagging (SVT).
The following table explains the compatibility matrix between single VLAN tag enabled and disabled maps. Symbol (√) denotes the engine ports that are supported, and symbol (X) denotes the engine ports that are not supported.
|
Maps |
SVT enabled iSSL map
|
|
|---|---|---|
|
same gs_engine |
different gs_engine in different maps |
|
|
Flex |
√ |
√ |
|
Flex + SVT |
√ |
√ |
|
Flex + iSSL |
√ |
√ |
Rules and Notes
Keep in mind the following rules and notes when deploying a flexible iSSL solution with single VLAN tag:
| 1. | An untagged iSSL session map can also use a SVT enabled GigaSMART application. |
| 2. | An untagged or non-SVT solution should be of the least priority. |
| 3. | With SVT enabled in the TLS/SSL app, VLAN based policy rule is not applicable hence, the option will not be shown once SVT is enabled in TLS/SSL app. |
Supported Platforms
The following devices support single VLAN tag feature in flexible inline TLS/SSL solution in both Gen2 and Gen3:
| GigaVUE‑HC1-Plus |
| GigaVUE‑HC1 |
| GigaVUE-HC3V1 |
| GigaVUE-HC3V2 |
Limitations
| In all H-series devices, the same GSApp profile can be part of both SVT enabled and non-SVT iSSL solution, but if SVT is disabled in the gs_app profile then it will not be part of the SVT enabled solution. |
| OOB-copy from vport with tag as original will not be supported for both proxy and non-proxy map because even if multiple VLAN tags are configured, only one proxy map will be created. |
| For inline-tools that are part of a proxy(inner) map, oob-copy from inline-tool with tag as original will not supported. |
| Flexible Inline single vlan tag configuration in GigaVUE‑HC1-Plus fails to send traffic with a proper VLAN tag with monitoring mode configured in either the inline-network, inline-tool, or vport. |
| In GEN2 GigaSMART card, a maximum of 28 VLANs will be supported for a single inline-network per GS Group. In the case of multiple inline-network ports (number of inline-network ports x number of VLANs), the number should not exceed 28 per GS Group. |
| In GEN3 GigaSMART card, a maximum of 32 VLANs will be supported for a single inline-network per GS Group. In the case of multiple inline-network ports (number of inline-network ports x number of VLANs), the number should not exceed 32 per GS Group. |
| With SVT enabled in the TLS/SSL app, VLAN based policy rule is not applicable hence, the option will not be shown once SVT is enabled in TLS/SSL app. |
Note: If you edit the Single VLAN Tag in the inline SSL app present in a solution, you should explicitly edit the Single Tag Mode on flex maps manually in the same or other solutions that use the same SSL app.



