Precryption™
License: Requires SecureVUE Plus license.
Gigamon Precryption™ technology 1 redefines security for virtual, cloud, and containerized applications, delivering plain text visibility of encrypted communications to the full security stack without the traditional cost and complexity of decryption.s
This section explains:
| How Gigamon Precryption Technology Works |
| Why Gigamon Precryption |
| Key Features |
| Key Benefits |
| Precryption Technology on Single Node |
| Precryption Technology on Multi-Node |
| Supported Platforms |
| Prerequisites |
How Gigamon Precryption Technology Works
Precryption technology leverages native Linux functionality to tap, or copy, communications between the application and the encryption library, such as OpenSSL.
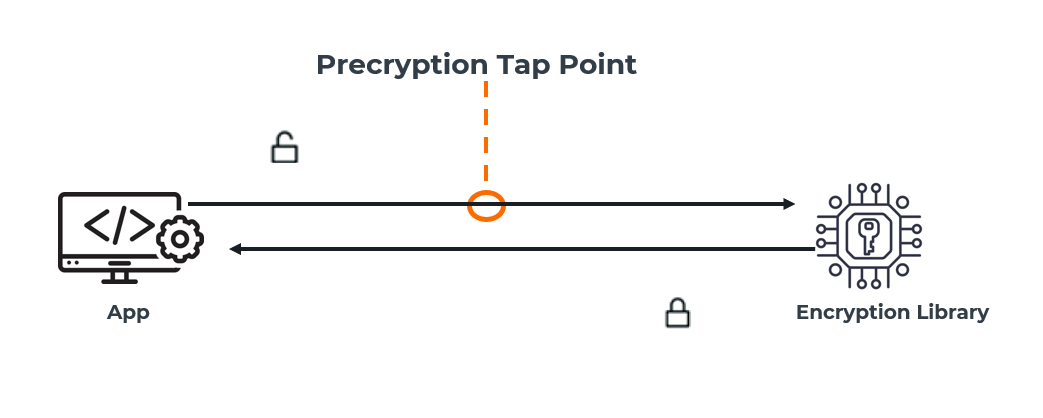
In this way, Precryption captures network traffic in plain text, either before it has been encrypted or after it has been decrypted. Precryption functionality doesn’t interfere with the message's actual encryption or transmission across the network. There’s no proxy, retransmissions, or break-and-inspect. Instead, this plaintext copy is forwarded to the Gigamon Deep Observability Pipeline for further optimization, transformation, replication, and tool delivery.
Precryption technology is built on GigaVUE® Universal Cloud Tap (UCT) and works across hybrid and multi-cloud environments, including on-prem and virtual platforms. Moreover, UCT with Precryption technology operates independently of the application and does not need to be integrated into the application development lifecycle.
Why Gigamon Precryption
GigaVUE Universal Cloud Tap with Precryption technology is a lightweight, friction-free solution that eliminates blind spots present in modern hybrid cloud infrastructure. It provides comprehensive visibility into East-West and North-South traffic across virtual, cloud, and container platforms. As long as a packet interacts with the Virtual Machine, it is mirrored, ensuring complete traffic capture. This solution delivers unobscured visibility into all encryption types, including TLS 1.3, without the need to manage and maintain decryption keys. With these capabilities, IT organizations can manage compliance, maintain the privacy of communications, establish a robust foundation for Zero Trust, and enhance security tool effectiveness by a factor of 5x or more.
Key Features
The following are the key features of this technology:
| Plain text visibility into communications with modern encryption (TLS 1.3, mTLS, and TLS 1.2 with Perfect Forward Secrecy). |
| Plain text visibility into communications with legacy encryption (TLS 1.2 and earlier). |
| Non-intrusive traffic access without agents running inside container workloads. |
| Elimination of expensive resource consumption associated with traditional traffic decryption. |
| Elimination of key management required by traditional traffic decryption. |
| Zero performance impact based on cipher type, strength, or version. |
| Support across hybrid and multi-cloud environments, including on-prem, virtual, and container platforms. |
| Keep private communications private across the network with plaintext threat activity delivered to security tools. |
| Integration with Gigamon Deep Observability Pipeline for the full suite of optimization, transformation, and brokering capabilities. |
Key Benefits
The following are the key benefits of this technology:
| Eliminate blind spots for encrypted East-West (lateral) and North-South communications, including traffic that may not cross firewalls. |
| Monitor application communications with an independent approach that enhances development team velocity. |
| Extend security tools’ visibility to all communications, regardless of encryption type. |
| Achieve maximum traffic tapping efficiency across virtual environments. |
| Leverage a 5–7x performance boost for security tools by consuming unencrypted data. |
| Support a Zero Trust architecture founded on deep observability. |
| Maintain privacy and compliance adherence associated with decrypted traffic management. |
How Gigamon Precryption Technology Works
This section explains how Precryption technology works on single nodes and multiple nodes in the following sections:
| Precryption Technology on Single Node |
| Precryption Technology on Multi-Node |
Precryption Technology on Single Node
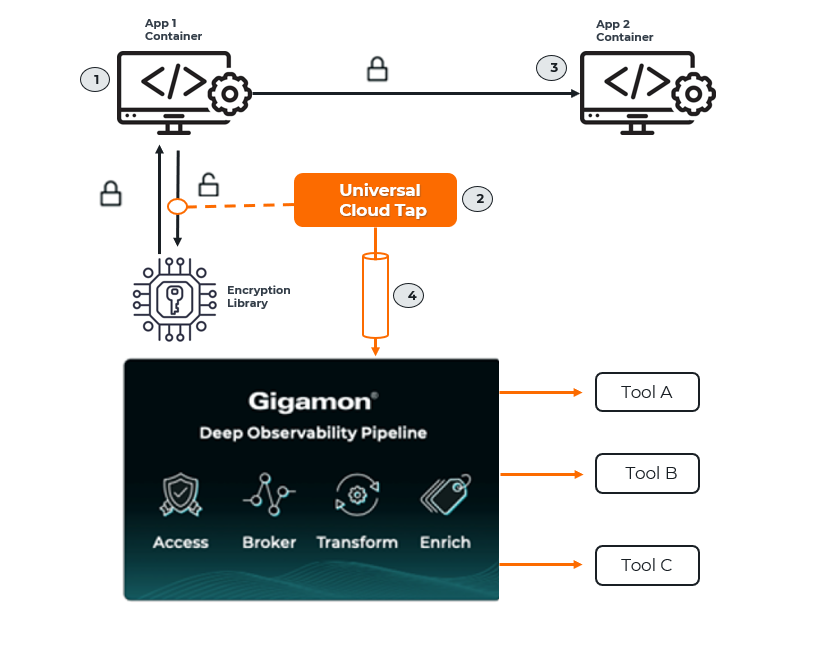
| 1. | When any application needs to encrypt a message, it uses an encryption library, such as OpenSSL, to perform the actual encryption. |
| 2. | GigaVUE Universal Cloud Tap (UCT), enabled with Precryption technology, gets a copy of this message before it’s encrypted on the network. |
| 3. | The encrypted message is sent to the receiving application with unmodified encryption—no proxy, no re-encryption, no retransmissions. |
| 4. | GigaVUE UCT creates packet headers as needed, encapsulates them in a tunnel, and forwards them to GigaVUE V Series in the deep observability pipeline. Gigamon optimizes, transforms, and delivers data to tools without further decryption. |
Precryption Technology on Multi-Node
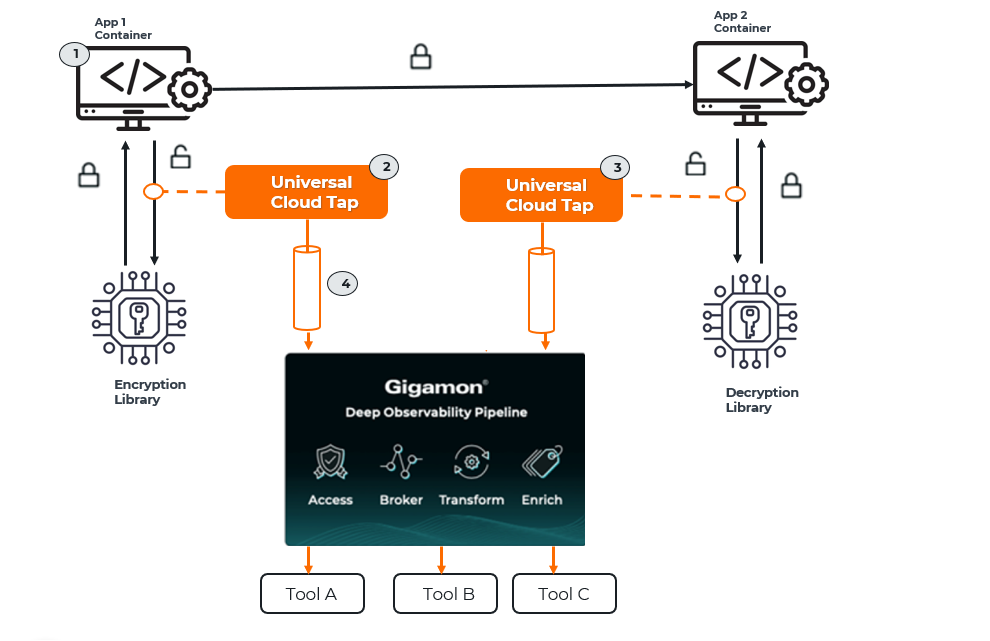
| 1. | When any application needs to encrypt a message, it uses an encryption library, such as OpenSSL, to perform the actual encryption. |
| 2. | GigaVUE Universal Cloud Tap (UCT), enabled with Precryption, gets a copy of this message before it’s encrypted on the network. |
| 3. | Optionally, GigaVUE UCT enabled with Precryption can also acquire a copy of the message from the server end after the decryption. |
| 4. | GigaVUE UCT creates packet headers as needed, encapsulates them in a tunnel, and forwards them to V Series in the deep observability pipeline. There, they are further enriched, transformed, and delivered to tools without further decryption. |
Supported Platforms
VM environments: Precryption™ is supported on the following VM platforms where UCT-V is supported:
Platform Type | Platform | ||||||||||||
| Public Cloud |
| ||||||||||||
| Private Cloud |
|
Container environments: Precryption™ is supported on the following container platforms where UCT-C is supported:
Platform Type | Platform | ||||||
| Public Cloud |
| ||||||
| Private Cloud |
|
Prerequisites
Deployment Prerequisites
| OpenSSL version 1.0.2, version 1.1.0, version 1.1.1, and version 3.x. |
| For UCT-C, worker pods should always have libssl installed to ensure that UCT-C Tap can tap the precrypted packets from the worker pods whenever libssl calls are made from the worker pods. |
| For GigaVUE‑FM, you must add port 5671 in the security group to capture the statistics. |
| Port 9900 should be enabled in security group settings on the UCT-V Controller to receive the statistics information from UCT-V. |
| For UCT-C, you must add port 42042 and port 5671 to the security group. |
License Prerequisite
| Precryption™ requires a SecureVUE Plus license. |
Supported Kernel Version
Precryption is supported on kernel versions 4.18 and above, including 5.4+ kernels, across all Linux and Ubuntu operating systems. For the Kernel versions below 5.4, refer to the following table:
Kernel-Version | Operating System |
4.18.0-193.el8.x86_64 | RHEL release 8.2 (Ootpa) |
4.18.0-240.el8.x86_64 | RHEL release 8.3 (Ootpa) |
4.18.0-305.76.1.el8_4.x86_64 | RHEL release 8.4 (Ootpa) |
4.18.0-348.12.2.el8_5.x86_64 | RHEL release 8.5 (Ootpa) |
4.18.0-372.9.1.el8.x86_64 | RHEL release 8.6 (Ootpa) |
4.18.0-423.el8.x86_64 | RHEL release 8.7 Beta (Ootpa) |
4.18.0-477.15.1.el8_8.x86_64 | RHEL release 8.8 (Ootpa) |
5.3.0-1024-kvm | ubuntu19.10 |
4.18.0-305.3.1 | Rocky Linux 8.4 |
4.18.0-348 | Rocky Linux 8.5 |
4.18.0-372.9.1 | Rocky Linux 8.6 |
4.18.0-425.10.1 | Rocky Linux 8.7 |
4.18.0-477.10.1 | Rocky Linux 8.8 |
4.18.0-80.el8.x86_64 | centos 8.2 |
4.18.0-240.1.1.el8_3.x86_64 | centos 8.3 |
4.18.0-305.3.1.el8_4.x86_64 | centos 8.4 |
4.18.0-408.el8.x86_64 | centos 8.5 |
For details on how to enable Precryption™ in VM environments, see the Configure Precryption in UCT-V.
For details on how to enable Precryption™ in container environments, see the Configure Precryption in UCT-C
For details to enable secure delivery of precrypted data, see the Secure Tunnels feature.



