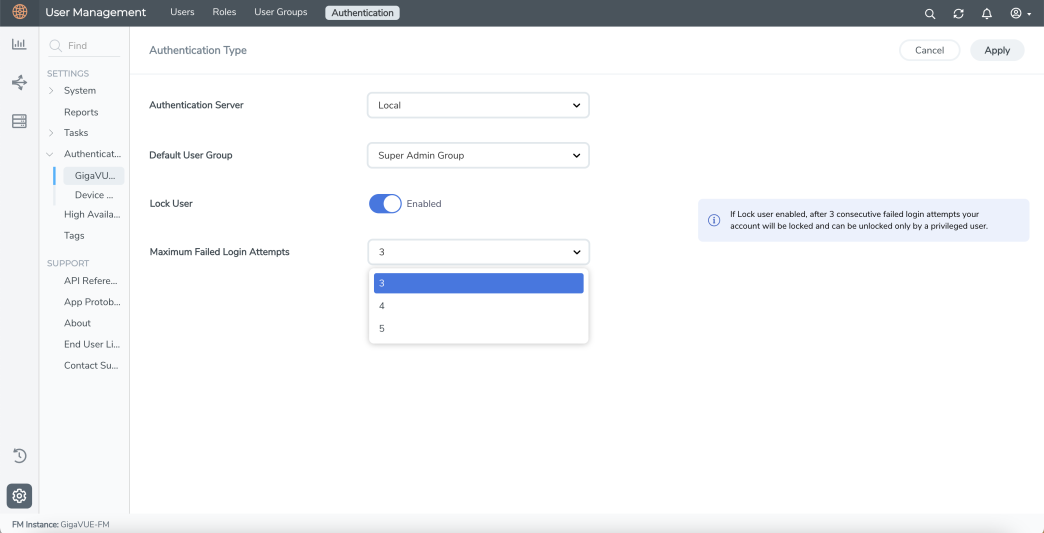
Authentication Type
Use the Authentication Type page to configure the following:
- Configure Authentication Type
- Configure Default User Group
- Configure Lock/Unlock Authentication Setting for Local User Accounts
- Configure Authentication
Configure Authentication Type
GigaVUE‑FM supports and authenticates users against the following authentication methods:
- Local: Local database configured through the GigaVUE-FM User Management page.
- External authentication servers: Includes LDAP, RADIUS, or TACACS+
- Third Party: External identity provider.
Note: GigaVUE-FM automatically gets logged off when you change the Authentication Type.
You can select only one of the authentication methods depending on your requirement. That is, you can select any one of the remote authentication methods or use the local authentication method or the external identity provider. This allows for enhanced security by maintaining the user names and passwords in a single location.
In case of remote authentication methods, you can configure fall back within the same scheme of AAA authentication. For example, for RADIUS authentication, you can add multiple RADIUS servers, so that, if the first server is not reachable, the second server is tried for accessibility and so on.
Note: If you cannot access GigaVUE‑FM due to failure in authentication, you can use the special access provided (https://<fm ip address/dns name>/admin). This access is applicable only for local users with super admin privileges. You can also access GigaVUE-FM through the Command Line Interface and locate the following log file to determine the reason for the failure in authentication: /var/log/shibboleth/idp-process.log
If authentication is done in the local server, then authorization is also performed locally. If authentication is done in the remote server, then authorization is also done at remote. Therefore, it is not required to configure extra roles for mapping purposes.
Configure Default User Group
For security reasons, the Default User Group option is not configured by default in GigaVUE‑FM. If required, you can configure the Default User Group option to specify how the local and externally authenticated users can be granted privileges in GigaVUE‑FM. If there are no valid GigaVUE‑FM specific groups configured in the remote server but if a default user group is configured in GigaVUE‑FM, then that group will be assigned. Otherwise, the user cannot login in to GigaVUE‑FM without groups being configured.
Note: You are responsible for configuring the groups at the remote server in the specified format for TACACS+ and RADIUS servers. For LDAP, you must configure the list of groups for Group Base DN in GigaVUE‑FM.
Groups Configured in GigaVUE‑FM Based on AuthMethod
The following table consists of examples with groups resolved in GigaVUE‑FM based on the AuthMethod field:
|
AuthMethod |
Logged in User |
MapDefaultUserGroup |
Remote Roles/Group Base DN (if configured) |
Expected Group |
Assigned Group |
Notes |
|
Local |
test |
- |
- |
fm_user |
fm_user |
The authMethod is 'LOCAL'. Therefore, the logged-in user group will be assigned.
|
|
TACACS+ |
tacacsuser1 |
- |
fm_admin |
fm_admin |
fm_admin |
The role which has been assigned remotely will be assigned.
|
|
TACACS+ |
tacacsuser3 |
- |
fm_non_exist_group [specified group Does not match any roles in GigaVUE‑FM] |
- |
- |
If non-exist group is being assigned remotely, then that user cannot login into GigaVUE‑FM. GigaVUE‑FM will reject that user.
|
|
TACACS+ |
tacacsuser3 |
User Group |
fm_non_exist_group [specified group Does not match any roles in GigaVUE‑FM] |
User Group |
User Group |
If non-exist group is being assigned remotely, then GigaVUE‑FM will check if Default User Group has been configured. If Default User Group is configured, then it will assign the same and allow the user to log in to GigaVUE‑FM.
|
|
TACACS+ |
tacacsuser2 |
- |
- |
- |
- |
If there are no groups configured remotely and Default User Group is also not configured in GigaVUE‑FM, then that user cannot log in to GigaVUE‑FM. GigaVUE‑FM will reject that user.
|
|
RADIUS |
radiususer1 |
- |
fm_admin |
fm_admin |
fm_admin |
The role which has been assigned remotely will be assigned.
|
|
RADIUS |
radiususer3 |
- |
fm_non_exist_group [specified group Does not match any roles in GigaVUE‑FM] |
- |
- |
If non-exist group is being assigned remotely, then that user cannot log in to GigaVUE‑FM. GigaVUE‑FM will reject that user.
|
|
RADIUS |
radiususer3 |
User Group |
fm_non_exist_group [specified group Does not match any roles in GigaVUE‑FM] |
User Group |
User Group |
If non-exist group is being assigned remotely, then GigaVUE‑FM will check whether Default User Group has been configured; If Default User Group is configured, then it will assign the same and allow the user to log in to GigaVUE‑FM.
|
|
RADIUS |
radiususer2 |
- |
- |
- |
- |
If there are no groups configured remotely and Default User Group is also not configured in GigaVUE‑FM, then that user cannot log in to GigaVUE‑FM. GigaVUE‑FM will reject that user.
|
|
LDAP |
ldapuser1 |
- |
CN=FMQA-SSO,DC=hqdevtest,DC=com |
fm_admin |
fm_admin |
The mapped group for the provided Group Base DN will be assigned to the logged in user.
|
|
LDAP |
ldapuser2 |
- |
CN=FMQA-SSO,DC=hqdev,DC=com |
- |
- |
If there are no group mapped to the provided/associated GROUP BASE DN, then GigaVUE‑FM will reject the user and will not allow the user to log in as well.
|
|
LDAP |
ldapuser2 |
User Group |
CN=FMQA-SSO,DC=hqdev,DC=com |
User Group |
User Group |
If there are no group mapped to the provided/associated GROUP BASE DN, then GigaVUE‑FM will check whether Default User Group has been configured; If so, it will assign the same and allow the user to login to GigaVUE‑FM.
|
|
LDAP |
ldapuser3 |
- |
- |
- |
- |
If the LDAP user is not associated to any GROUP in LDAP and it does not return any group, then GigaVUE‑FM will reject the user and will not allow the user to login as well.
|
|
LDAP |
ldapuser3 |
User Group |
- |
User Group |
User Group |
If the LDAP user is not associated to any GROUP in LDAP and it does not return any group, then GigaVUE‑FM will check whether Default User Group has been configured; If so, it will assign the same and allow the user to log in to GigaVUE‑FM. |
Configure Lock/Unlock Authentication Setting for Local User Accounts
Until software version 6.2.00, when locally authenticated users log in to GigaVUE-FM, user credentials are validated and upon successful validation of the credentials, the user is logged into GigaVUE-FM. If validation of user credentials fails, incorrect user name and password message prompts up. GigaVUE-FM does not impose any restriction on unsuccessful login attempts.
Starting from software version 6.3.00, when locally authenticated users try to login to GigaVUE-FM, and if the login fails after a defined number of failed password attempts, the user account is locked. Only an admin user can unlock the user account. The lock-unlock authentication prevents unauthorized user access and also limits the number of login attempts, thereby controlling the number of brute-force password attacks.
Rules and Notes
Refer to the following rules and notes:
- The lock-unlock authentication option is enabled by default.
- To disable the lock-unlock authentication option from the Authentication Type page, you must be a user with fm_super_admin role or a user with read/write access to the GigaVUE‑FM Security Management category.
- Once your user account is unlocked, you can login with the default password. Ensure to change the default password to a new password for security reasons.
- You can view the status of locked and unlocked users from the GigaVUE-FM User Management page. However, the status in this page does not depict the Near-real Time status. You must manually refresh the screen to know the status. Refer to the Users section for more details.
- Whenever a user account is locked or unlocked, events are triggered and can be viewed in the GigaVUE-FM Events page.
- You can also configure Event Notification settings for the events triggered for the lock-unlock authentication. Refer to the Event Notifications section for more details.
- The Events captures in the Events page are not near-real time events.
- Unsuccessful Login attempts and locked/unlocked user information is captured in the Audit Logs page.
Note: The default fm_super_admin (preconfigured in GigaVUE-FM with username: admin) user can be unlocked only from the GigaVUE-FM Command-line Interface using the fmctl command. Refer to the GigaVUE-FM CLI Commands.
Configure Authentication
Use the Authentication > Authentication Type to configure how user logins are authenticated in GigaVUE-FM.
To access the Authentication Type page:
-
On the left navigation pane, click Settings
 , select Authentication > Authentication Type. In the authentication type page that appears:
, select Authentication > Authentication Type. In the authentication type page that appears: - Select the required Authentication Type. Refer to Configure Authentication Type section for more details.
- Set the Default User Group to one of the options: Refer to Configure Default User Group section for more details.
- Super Admin Group
- Admin Group
- User Group
- None
- Use the Toggle option to enable and disable the lock-unlock authentication setting.
- Configure the Maximum Failed Login Attempts. Allowable range is from 3 to 5. Default is 5. Refer to Configure Lock/Unlock Authentication Setting for Local User Accounts section for more details.
-
Click Save.