5G-Cloud Oracle and Nokia SCP Support
GigaVUE V Series Node supports receiving data from 5G network functions in Oracle SCP and Nokia SCP input formats. In both Oracle and Nokia SCP, 3GPP standard method is followed, which has all the standard network components implemented.
Oracle SCP
Oracle systems input format is HTTP2/HTTP2S POST over TCP with TLS enabled. In Oracle SCP, the 5G-Cloud application synthesizes the packets and egresses them to the tool port after it has received all the 4-leg transactions. Oracle SCP processing in the 5G-Cloud application supports converting the discovery and the 4-legged (consumer, SCP, and producer) transactions to packets as per 3GPP Model C and Model D.
Model C
The Consumer knows the producer and sends messages through SCP. Model C comprises of 4-legged transactions between the consumer, SCP, and the producer. The 5G-Cloud application converts the 4-legged transactions to packets and sends them to the probe.
Model D
SCP sends discovery messages to discover the producer after receiving the messages from the consumer. Model D comprises of 2-legged transactions between the consumer and the SCP, 4-legged transactions between the SCP, SCP discovery, and the NRF to find the producer, and the 2-legged transactions between the producer and the SCP. The 5G-Cloud application converts the 4-legged transactions between the consumer, SCP, and the producer to packets and sends them to the probe. The 5G-Cloud application also converts the discovery transactions between the SCP and the NRF and sends them to the probe.
5G- Cloud application will ensure that both the discovery transaction and the 4-legged transaction are transmitted in order, to the connected tool or probe.
Nokia SCP
In Nokia SCP, traffic is mirrored between control functions using the HTTP2 protocol. This traffic is mirrored from a service called SCP (Service Control Proxy), a centralized point through which all the communications between all the control plane functions pass. SCP encrypts all the messages that are going across the control plane network functions and forwards that information in JSON-encoded format to GVHTTP2.
Both Model C and Model D transactions can be received from the SCP. However, Model D cannot be identified as Model D, because a separate message id is used for the discovery messages. In the case of Model D, SCP will include the Model D discovery transactions that happened with NRF along with the network function communication. Therefore, 6 transactions will be forwarded from SCP for a single request and response pair between any two network functions. The Model C transactions will be processed in 2 modes:
| Inbound only (2 legged): The 5G-Cloud application will synthesize a direct transaction between the network functions. The 4-legged transactions received between the consumer, SCP, and the producer are synthesized to look like 2-legged transactions between the consumer and the producer. |
| Inbound and outbound (4 Legged): The 5G-Cloud application will synthesize indirect transactions, meaning all transactions between any network function will go via SCP. All the transactions received in Model C or Model D are synthesized and sent to the probes. |
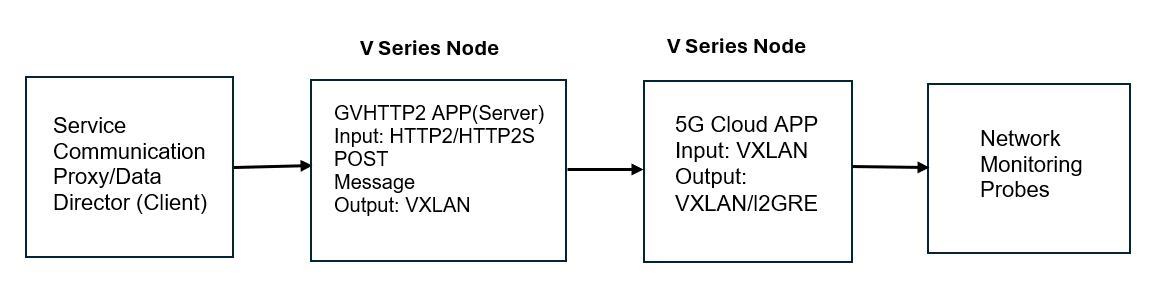
GVHTTP2 Application
The first application, GVHTTP2, acts as an HTTP2 server, receives the data over HTTP2 frame and establishes a TCP connection with multiple Oracle SCP/DD or Nokia SCP pods. It receives the HTTP2 headers and stores them in a temporary buffer. Once it receives all the headers and body of that stream, it acknowledges back to the client. The application will extract the HTTP2 header and HTTP2 body, encapsulate the data into a VXLAN header, and send it out over the VXLAN tunnel to the next application, 5G-Cloud.
5G-Cloud Application
The 5G-Cloud application receives and decapsulates the VXLAN packet. It extracts the HTTP2 body, parses the SCP/DD JSON mirrored message, and associates the mirrored message transaction ID to track the complete transaction. It then synthesizes TCP Flow and HTTP2 Session representing full 5G CNF / SCP / 5G CNF transaction data and sends it out over L2GRE/VXLAN tunnel to the probe.
The 5G-Cloud application runs in Oracle SCP, Nokia SCP Inbound, and Nokia SCP Inbound-Outbound modes.
-
In Nokia SCP Inbound-Outbound mode, both Inbound (between Consumer and SCP) and Outbound (between SCP and Producer) traffic is synthesized and sent to the connected Tool port. In Nokia SCP Inbound mode, only Inbound (between Consumer and SCP) traffic is processed and sent to the Tool Port.
-
In the Nokia SCP Inbound mode, the 5G-Cloud Application will drop the Outbound traffic from the SCP (if received in the input).
-
In the Nokia SCP Inbound mode, the Producer replaces the SCP in transactions between the Consumer and the SCP.
-
In the Nokia SCP Inbound mode, authority header value will be replaced (if the replace authority configuration is enabled).
Configuration of 5G-Cloud Oracle/Nokia SCP
To configure the GVHTTP2 and 5G-Cloud applications in GigaVUE-FM, refer to the following sections:
| Configuration of GVHTTP2 Application for Oracle SCP/Nokia SCP |
| Configuration of 5G-Cloud Application for Oracle SCP/Nokia SCP |
Configuration of GVHTTP2 Application for Oracle SCP/Nokia SCP
In GigaVUE-FM, you must do the following to add the GVHTTP2 application in the Monitoring Session of a Monitoring Domain:
| 1. | Create an ingress REP (Raw End Point) to receive the HTTP2/HTTP2S data over TCP. Refer to Create Raw Endpoint (VMware vCenter) for more information on creating a REP. |
| 2. | Add the GVHTTP2 application in the Monitoring Session. |
| 3. | Create a link between ingress REP and the GVHTTP2 application. |
| 4. | Create egress REP. |
| 5. | Create a link between the GVHTTP2 application and egress REP. |
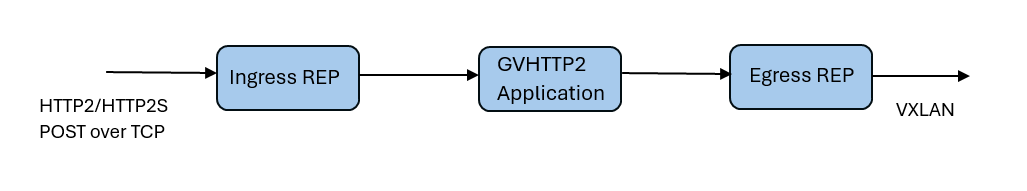
You can add a GVHTTP2 application to:
| New Monitoring Session - You can add the GVHTTP2 application after creating a new Monitoring Session and when the canvas appears. |
| Existing Monitoring Session - Click Edit on the existing Monitoring Session, and the GigaVUE-FM canvas appears. |
To add a GVHTTP2 application:
| 1. | In the canvas, drag and drop the GVHTTP2 application and select Details. The GVHTTP2 quick view appears. |
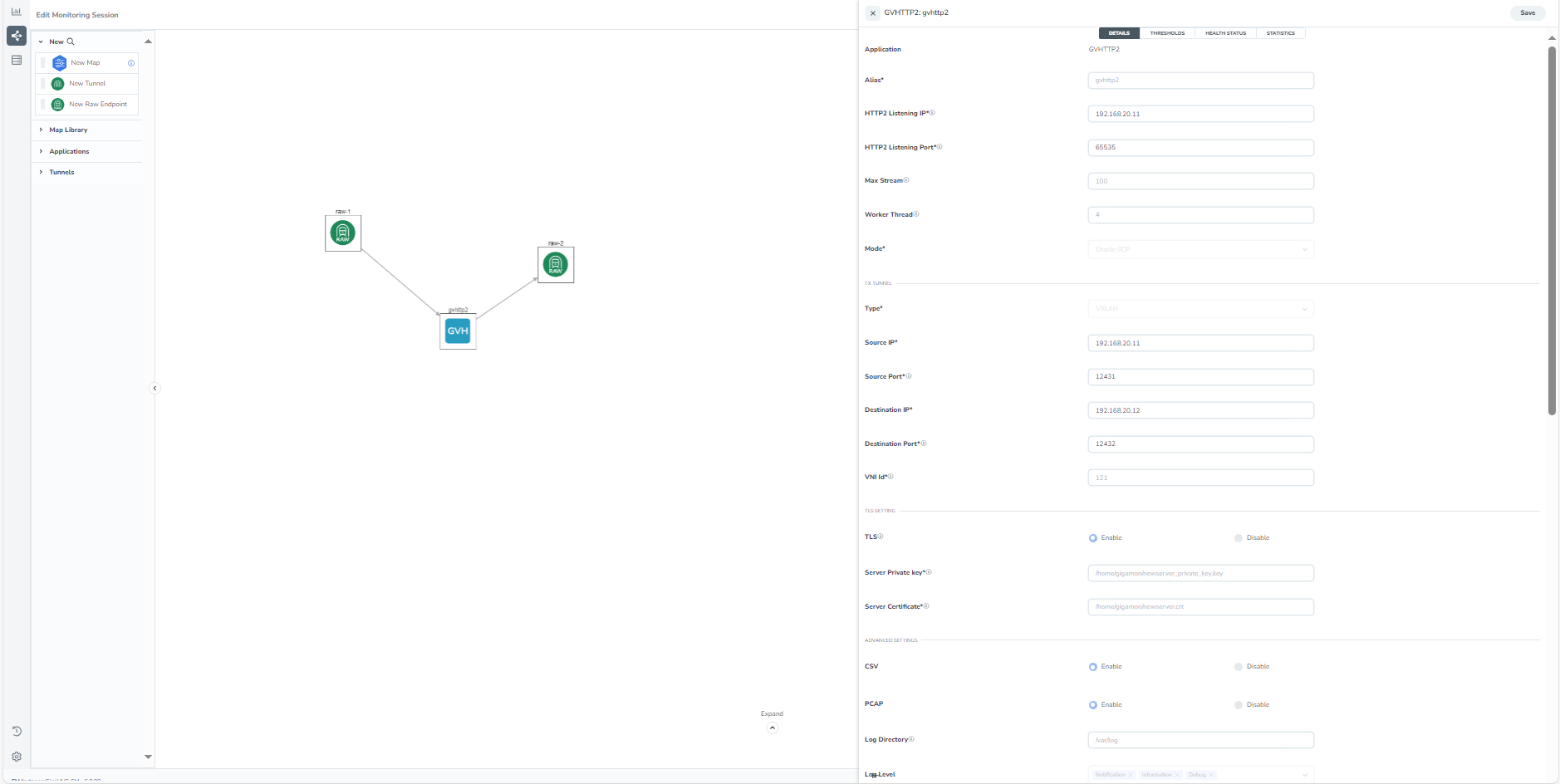
| 2. | On the application quick view, enter or select the required information as described in the following table: |
|
Field |
Description |
|||||||||
|
Application |
The name GVHTTP2 appears by default. |
|||||||||
|
Alias |
Enter the alias name as gvhttp2. |
|||||||||
|
HTTP2 Listening IP |
Specify the HTTP2 IP address. The application will listen to the traffic on the specified IP address. |
|||||||||
|
HTTP2 Listening Port |
Specify the HTTP2 Port. The application will listen to the traffic on the specified port. |
|||||||||
|
Max Stream |
Specify the maximum number of concurrent streams in one HTTP2 session. Enter a value between 1 and 100. The default value is 100. |
|||||||||
|
Worker Thread |
Specifies the number of worker threads. Enter a value between 1 and 128. The default value is four. |
|||||||||
|
Mode |
Select Oracle SCP or Nokia SCP as mode from the drop-down menu. |
|||||||||
|
TX Tunnel (Specifies the tunnel configuration from GVHTPP2 to 5G-Cloud) |
||||||||||
|
Type |
Specify the tunnel type. VXLAN is selected by default. |
|||||||||
|
Source IP |
Specify the source IP address to use when sending the packet. |
|||||||||
|
Source Port |
Specify the source port to bind for sending the packet. Enter a value between 1 and 65535. |
|||||||||
|
Destination IP |
Specify the destination IP address to which packets will be sent. |
|||||||||
|
Destination Port |
Specify the destination port where packets will be sent. Enter a value between 1 and 65535. |
|||||||||
|
VNI Id |
Specify the VNI to use for the VXLAN traffic. Enter a value between 0 and 16777215. The default value is zero. |
|||||||||
|
TLS Setting |
||||||||||
|
TLS |
Select a TLS/SSL Monitor Mode from one of the following options:
|
|||||||||
|
Server Private key* |
Specify the server private key only when TLS is enabled. |
|||||||||
|
Server Certificate* |
Specify server certificate only when TLS is enabled. |
|||||||||
|
Advanced Setting |
||||||||||
|
CSV |
Enable or disable the CSV log level. |
|||||||||
|
PCAP |
Enable or disable the PCAP log level. |
|||||||||
|
Log Directory |
Specify the path to store the log files. |
|||||||||
|
Log Level |
In the log level drop-down list, select the severity log level of the events from the following options. The default value level is Notification.
|
|||||||||
Download Logs - GVHTTP2 application
You can view the log files of a V Series Node or download them as .CSV or .txt file.
To download the log files to a local environment:
| 1. | Go to Traffic > VIRTUAL > select your cloud platform. |
| 2. | Select the required Monitoring Session and click the APPS LOGGING link. |
| 3. | The GVHTTP2 Logging page displays the logs currently available. You can download the preferred logs by selecting the required Days, Timestamps, File Name, and Type (TextLog and FlowStats) details. |
| 4. | Select the log files to download, and then click Download Files from the Actions menu. |
| 5. | The system downloads the selected files to your local environment. |
Configuration of 5G-Cloud Application for Oracle SCP/Nokia SCP
In GigaVUE-FM, you must do the following to configure the 5G-Cloud application in the Monitoring Session of a Monitoring Domain:
| 1. | Create ingress REP to extract the HTTP2 body. Refer to Create Raw Endpoint (VMware vCenter) for more information on creating a REP. |
| 2. | Add the 5G-Cloud application in the Monitoring Session. |
| 3. | Create a link between ingress REP and the 5G-Cloud application. |
| 4. | Create egress REP. |
| 5. | Create a link between the 5G-Cloud application and egress REP. |
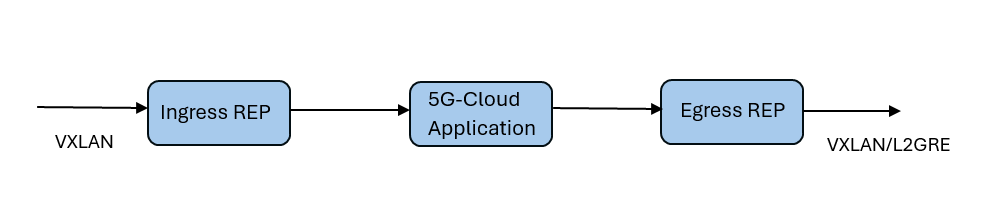
Adding 5G-Cloud Application in Oracle SCP/Nokia SCP
Prerequisites
The pre-requisite to add a 5G-Cloud Application in Oracle SCP/Nokia SCP is:
-
You must upload CSV files containing a valid FQDN, NF Instance, and User Agent ID's and a valid IPv4/IPv6 addresses. To upload the CSV file, refer to Adding CSV file for IP Mapping.
You can add a 5G-Cloud application to:
| New Monitoring Session - You can add the 5G-Cloud application after creating a new Monitoring Session and when the canvas appears. |
| Existing session - Click Edit on the existing Monitoring Session, and the GigaVUE-FM canvas appears. |
To add a 5G-Cloud application:
| 1. | In the canvas, drag and drop the 5G-Cloud application and select Details. The 5G-Cloud quick view appears. |
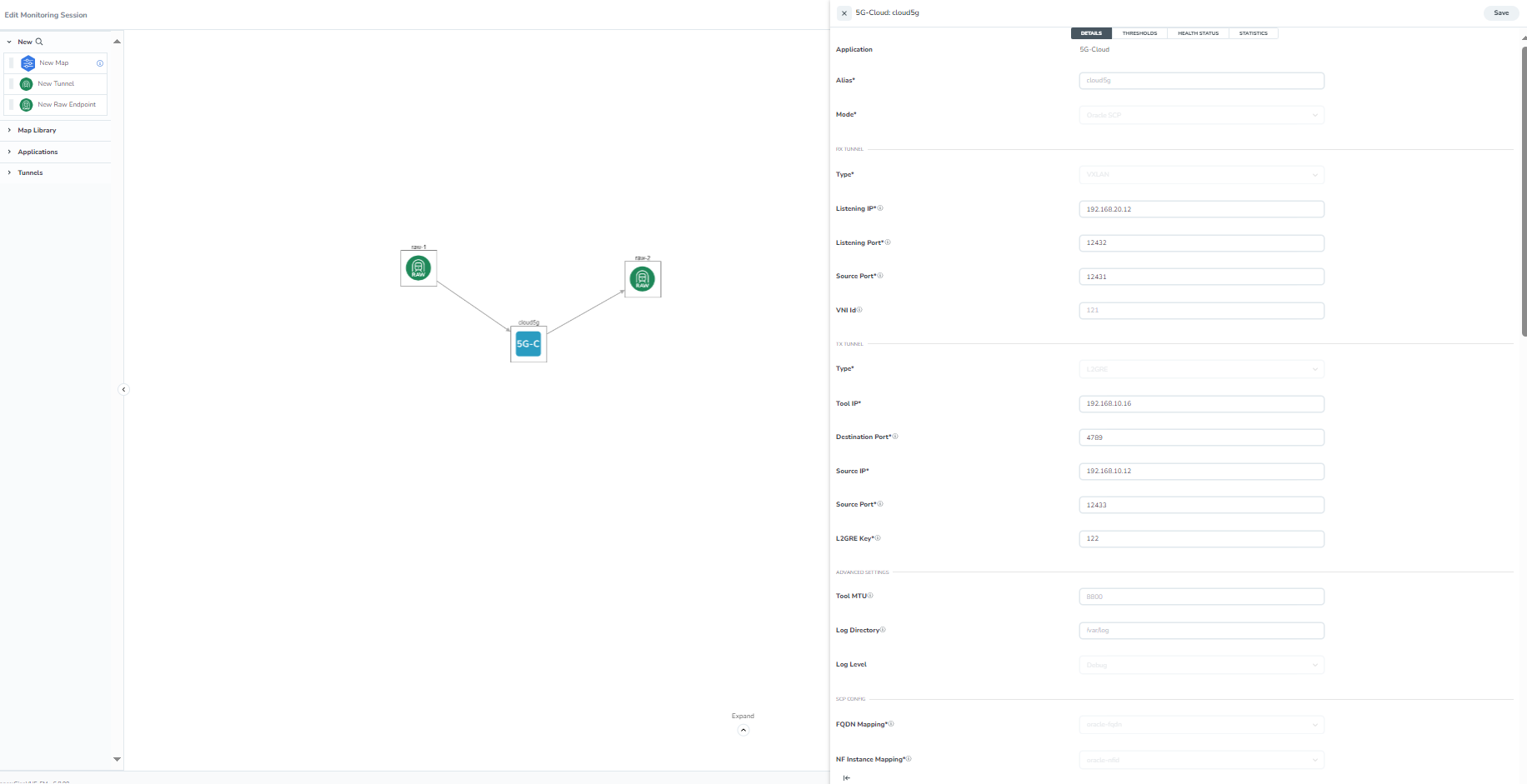
| 2. | On the application quick view, enter or select the required information as described in the following table: |
|
Field |
Description |
||||||||||||||||||
|
Application |
The name 5g-Cloud appears by default. |
||||||||||||||||||
|
Alias |
Enter the alias name as cloud5g. |
||||||||||||||||||
|
Mode |
From the drop-down list, select the required mode from the following options:
|
||||||||||||||||||
|
RX Tunnel (Specifies the tunnel configuration from GVHTPP2 to 5G-Cloud) |
|||||||||||||||||||
|
Type |
Specify the tunnel type. VXLAN is selected by default. |
||||||||||||||||||
|
Listening IP |
Specify the tunnel's local listen IP address (TX tunnel destination IP address used in GVHTTP2) to receive the packet. |
||||||||||||||||||
|
Listening Port |
Specify the tunnel's local listening port to bind to receive the packet. The application will listen to the traffic coming to the specified port. Enter a value between 1 and 65535. |
||||||||||||||||||
|
Source Port |
Specify the tunnel destination port from where the packets will be sent. Enter a value between 1 and 65535. |
||||||||||||||||||
|
VNI Id |
Specify the VNI to use for the VXLAN traffic. Enter a value between 0 and 16777215. The default value is zero. |
||||||||||||||||||
|
TX Tunnel |
|||||||||||||||||||
|
Type |
Specify the tunnel type. |
||||||||||||||||||
|
Tool IP |
Specify the remote IP address to which the packet will be sent. |
||||||||||||||||||
|
Destination Port |
Specify the tunnel destination port where the packet will be sent. Enter a value between 1 and 65535. |
||||||||||||||||||
|
Source IP |
Specify the source IP address to use when sending the packet. |
||||||||||||||||||
|
Source Port |
Specify the tunnel source port to bind for sending the packet. Enter a value between 1 and 65535. |
||||||||||||||||||
|
VNI Id (Applicable only when the selected tunnel type is VXLAN) |
Specify the VNI to use for the VXLAN traffic. Enter a value between 0 and 16777215. |
||||||||||||||||||
|
L2GRE Key (Applicable only when the selected tunnel type is L2GRE) |
Specify the key for the L2GRE tunnel type. Enter a value between 0 and 4294967295. |
||||||||||||||||||
|
Advanced Setting |
|||||||||||||||||||
|
Tool MTU |
Specify the tool port MTU. Note: For V Series Node version 6.8.00 and above, the range should be between 1400 and 8800. The default value is 8800. For V Series Node version below 6.8.00, range should be between 1500 and 8800. The default value is 8800. |
||||||||||||||||||
|
Log Directory |
Specify the path to store the log files. |
||||||||||||||||||
|
Log Level |
In the tunnel log level drop-down list, select the severity log level of the events from the following options:
|
||||||||||||||||||
|
SCP Config |
|||||||||||||||||||
|
FQDN Mapping |
Specify the alias name created for the uploaded FQDN table CSV file. Header details:
gigamon@test-5gc-new:/var/log/cloud5g_tabledir$ cat FQDN.txt FQDN,IngressIP1,IngressIP2,IngressPort,EgrIP,NFType Examples - 5G-Cloud FQDN Entries:
|
||||||||||||||||||
|
NF Instance Mapping |
Specify the alias name created for the uploaded NFID table CSV file. Header details:
gigamon@test-5gc-new:/var/log/cloud5g_tabledir$ cat NFID.txt NFID,IngressIP1,IngressIP2,IngressPort,EgrIP,NFType Examples - 5G-Cloud NFID Entries:
|
||||||||||||||||||
|
User Agent Mapping |
Specify the alias name created for the uploaded User Agent table CSV file. Header details:
gigamon@test-5gc-new:/var/log/cloud5g_tabledir$ cat UA.txt UserAgent,IngressIP1,NFType Examples - 5G-Cloud User Agent Entries:
|
||||||||||||||||||
|
SCP Advanced Config |
|||||||||||||||||||
|
No. of TCP Flows |
Specify the total number of concurrent TCP flows. Enter a value between 128 and 2048. The default value is 1024. |
||||||||||||||||||
|
No. of Transaction Flows |
Specify the total number of Transaction Stream Flows allocated for tracking active Transaction Streams. Enter a value between 128 and 5500. The default value is 2048. |
||||||||||||||||||
|
TCP Flow Timeout |
Specify the TCP flow timeout ranging between 0 to 7200. The default value is 900. |
||||||||||||||||||
|
SCP Transaction Timeout |
Specify the SCP transaction timeout value ranging between 1 and 300. The default value is 10. Note: The recommended timeout value is between 10 and 20 seconds. An increase in the transaction timeout value will impact the total number of transactions that can be processed in parallel. |
||||||||||||||||||
|
Minimum TCP Client Port |
Specify the minimum value to be used for TCP client port ranging between 1023 and 65535. The default value is 32768. |
||||||||||||||||||
|
Maximum TCP Client Port |
Specify the maximum value to be used for client port ranging between 1023 and 65535. The default value is 36863. |
||||||||||||||||||
|
Header Index |
Enable or disable the header indexing flag from the available options. The default value is disable. |
||||||||||||||||||
|
Header Compression Code Note: HTTP/2 requests and responses typically contain a large number of redundant headers. HTTP/2 uses header compression to compress headers significantly. |
Enable or disable the header compression code from the available options. The default value is disable. |
||||||||||||||||||
|
Gigamon Header Note: Helps in the debugging process to identify all transactions. |
Enable or disable the Gigamon Header from the available options. The default value is Enable. |
||||||||||||||||||
|
Nokia Use 3gpp Target API Root
|
Specify the value which upon detecting producer IP/FQDN, treats the 3gpp Target API Root to be predictive of the Producer IP if value is non-zero as either enable or disable. The default value is disable. |
||||||||||||||||||
|
Nokia Replace Authority
(Applicable only when the selected mode is Nokia SCP Inbound) |
Specify the value which upon detecting producer IP/FQDN, treats the 3gpp Target API Root to be predictive of the Producer IP if the value is non-zero as either enable or disable. The default value is disable. |
||||||||||||||||||
|
Packet Capture Level |
Select the packet capture level from the drop-down list:
|
||||||||||||||||||
|
5G-Cloud Log Level |
Select the required 5G-Cloud CSV log level from the drop down list. The default value is None.
|
||||||||||||||||||
Download Logs - 5G-Cloud application
You can view the log files of a V Series Node or download them as .CSV or .txt file.
To download the log files to a local environment:
| 1. | Go to Traffic > VIRTUAL > select your cloud platform. |
| 2. | Select the required Monitoring Session and click the APPS LOGGING link. |
| 3. | The CLOUD5G Logging page displays the logs currently available. You can download the preferred logs by selecting the required Days, Timestamps, File Name, and Type (TextLog and FlowStats) details. |
| 4. | Select the log files to download, and then click Download Files from the Actions menu. |
| 5. | The system downloads the selected files to your local environment. |
Adding CSV file for IP Mapping
To add the CSV file for IP mapping:
| 1. | Go to Inventory > VIRTUAL > select your cloud platform, and then click Settings > 5G-Apps. The 5G-Apps Configuration page appears. |
| 2. | Click New. Enter the name for the CSV file in the Alias field |
| 3. | Select any of the following from the Type as per the requirement: |
| 5G-Cloud FQDN - Adding the CSV file containing a valid FQDN ID and a valid IPv4/IPv6 address for IP mapping. Adding FQDN is mandatory. |
| 5G-Cloud NF Instance - Adding the CSV file containing a valid NF instance ID and a valid IPv4/IPv6 address for IP mapping. |
| 5G-Cloud UA - Adding the CSV file containing a valid user agent ID and a valid IPv4/IPv6 address for IP mapping. |
| 4. | Click Choose File in FileName field to upload the CSV file into GigaVUE-FM. |
| 5. | Click Validate to validate the CSV file. |
| 6. | Click Save to add the CSV file. |
Note: For Oracle SCP, configuration of FQDN Mapping, NF Instance Mapping, and User Agent Mapping are mandatory. For Nokia SCP Inbound and Nokia SCP Inbound/Outbound, configuration of FQDN Mapping is mandatory.
Limitations
| The following configuration parameters for the GVHTTP2 application are non-editable and can be configured only during the initial configuration: |
| • | Mode |
| • | TX Tunnel – txType |
| • | Worker thread |
| • | RX VNI Id |
| • | Max Streams |
| • | TLS configuration |
| • | Log Level |
| • | Log Directory |
| The following configuration parameters for the 5G-Cloud application are non-editable and can be configured only during the initial configuration: |
| • | Mode |
| • | TX Tunnel – txType |
| • | RX Tunnel - rxType |
| • | RX VNI Id |
| • | Tool MTU |
| • | Log Directory |
| • | Log Level |
| • | Header Index |
| • | Header Compression Code |
| • | Packet capture log level |
| • | SCP log level |
| • | Gigamon Header |
| • | FQDN Mapping |
| • | NF Instance Mapping |
| • | User Agent Mapping |
Rules and Notes
| The 5G-Cloud and GVHTTP2 applications require the "VBL-250T-ADD-5GC" license. |
| It is recommended to use SRIOV enabled drivers for better performance and higher throughput. Refer to |
| On a V Series Node, only one application (GVHTTP2 or 5G-Cloud or AMX) can be deployed across Monitoring Sessions. |
| GVHTTP2, 5G-Cloud, and AMX applications should not be combined with general GigaSMART applications in a Monitoring Session or across Monitoring Sessions. |
| For GVHTTP2, 5G-Cloud, and AMX applications, the source and destination links should be Raw Endpoints. |
| Support GVHTTP2, 5G-Cloud, and AMX applications is limited to 'none' tapping type. |
| Configuration of GVHTTP2 and 5G-Cloud in V Series Node will fail in versions less than v6.7.00. |
| To deploy a Monitoring Session, ensure that the 'HTTP2 Listening IP address' and 'TX Tunnel Source IP address' in GVHTTP2 correspond to the IP addresses of one of the V Series Node interfaces. |
| To deploy a Monitoring Session, ensure that the 'RX Tunnel Listening IP address' and 'TX Tunnel Source IP address' in 5G-Cloud correspond to the IP addresses of one of the V Series Node interfaces. |
| To deploy a Monitoring Session, ensure that the TX Tunnel Destination IP address used in GVHTTP2, and the RX Tunnel Listening IP address used in 5G-Cloud are the same. |
| When you have already deployed the 5G-Cloud application with all the table files uploaded, you should undeploy and redeploy the Monitoring Session again with the updated files to update the table. |
| In the GVHTTP2 application, when the TLS/SSL configuration is enabled, the private key and certificate path must be configured. |
| To upload the table configuration file in CSV format, go to Inventory -> Virtual ->Settings -> 5G-Apps, enter the alias, type the CSV file name, and upload it. |
| To download the files, go to Inventory -> Virtual ->Settings -> 5G-Apps and select the alias name to be downloaded. |
FHA Dashboards for 5G-Cloud Applications
After configuring the GVHTTP2 and 5G-Cloud applications, you can monitor the statistics for Oracle SCP and Nokia SCP by the reports displayed in the Dashboard.
To access the details, refer to



