Configure SSL Decrypt
To configure SSL Decrypt Application using GigaVUE-FM follow the steps given below:
Upload SSL Keys
To upload an SSL private key, do the following:
- Go to Inventory > Resources > Security > SSL Keys.
- Click Add. The Create SSL Key page appears.
- Enter the following details:
Field
Description
Key Alias
Enter a name for the key.
Comment
Enter a description
Key Type
Select the either of the key type:
PEM
PassPhrase (optional)
SSH passphrases allows you to protect your private key from being used with out the passphrase. Enter the passphrase created with the private key.
SSL Key Store
Enter the SSL Key Store in which the Key is stored.
Private key
Enter the Private Key using any of the following options:
- Copy and Paste
- Install from URL
- Install from Local Directory
Certificate
Enter the Certificate using any of the following options:
- Copy and Paste
- Install from URL
- Install from Local Directory
PKCS12
PassPhrase
SSH passphrases allows you to protect your private key from being used with out the passphrase. Enter the passphrase created with the private key.
SSL Key Store
Enter the SSL Key Store in which the Key is stored.
- Click Save.
Note: SSL Decrypt application does not support HSM.
The following actions can also be performed from the SSL Keys Page:
|
Field |
Description |
|
Edit |
To edit a SSL Key, select the key from the list in the SSL Keys page and click the Edit button. |
|
Delete |
To delete a SSL Key, select the key from the list in the SSL Keys page and click the Delete button. |
|
Delete all |
Use this button to delete all the SSL Keys in the SSL Keys page. |
|
View certificate |
To view the certificate associated with the particular SSL Key, select the key from the list in the SSL Keys page and click the View Certificate button. |
Create SSL Service
After uploading a private key, you can add a service. A service maps to a physical server, such as an HTTP server. One server can run multiple services. A service is a combination of an IP address and a server port number.
Prerequisite
Before creating a service, upload a private key as described in Upload SSL Keys
To create a SSL service, do the following:
- Go to Inventory > Resources > Security > SSL Service. The SSL Services page appears.
- Click Add. The Create SSL Service page appears.
- On the Create SSL Service page, enter the following details:
Field
Description
Alias
Enter a name for the SSL Service.
Default Service
Enable this to use default service.
Server IP Address
Enter the IP address of the server in which the service runs.
Server Port
Enter the port number of the server.
- Click Save.
The following actions can also be performed from the SSL Service Page:
|
Field |
Description |
|
Edit |
To edit a SSL Service, select the service from the list in the SSL Service page and click the Edit button. |
|
Delete |
To delete a SSL Service, select the service from the list in the SSL Service page and click the Delete button. |
|
Delete all |
Use this button to delete all the SSL Service in the SSL Service page. |
Key Mapping
After adding the SSL Service, now you map the private key with the service using Key Mapping.
To map a key with the service, follow the steps given below,
- Go to Inventory > Resources > Security > SSL Key Mapping. The SSL Key Mapping page appears.
- Click Add.
- Enter the Key Mapping Alias.
- Select the SSL Service and Key Alias from the drop-down.
- Click Save.
The following actions can also be performed from the SSL Keys Page:
|
Field |
Description |
|
Edit |
To edit a SSL Service, select the service from the list in the SSL Service page and click the Edit button. |
|
Delete |
To delete a SSL Service, select the service from the list in the SSL Service page and click the Delete button. |
|
Delete all |
Use this button to delete all the SSL Service in the SSL Service page. |
SSL Key Store
SSL Key Store is a repository, that allows you to save all the key under a single location. You can create multiple key stores and in each key store you can store multiple keys.
- Go to Inventory > Resources > Security > SSL Key Store. The SSL Key Store page appears.
- Click Add.
- Enter the Key Store Alias and Comment.
- Click Save.
The following actions can also be performed from the SSL Key Store Page:
|
Field |
Description |
|
Edit |
To edit a SSL Key Store, select the Key Store from the list in the SSL Key Store page and click the Edit button. |
|
Delete |
To delete a SSL SSL Key Store, select the SSL Key Store from the list in the SSL Key Store page and click the Delete button. |
|
Delete all |
Use this button to delete all the SSL Key Store in the SSL Key Store page. |
Add SSL Decrypt to Monitoring Session
After mapping your keys with service, to add GigaSMART applications to GigaVUE V Series Node, follow the steps given below,
- Drag and drop SSL Decrypt from APPLICATIONS to the graphical workspace.
- Click the SSL Decrypt application and select Details.
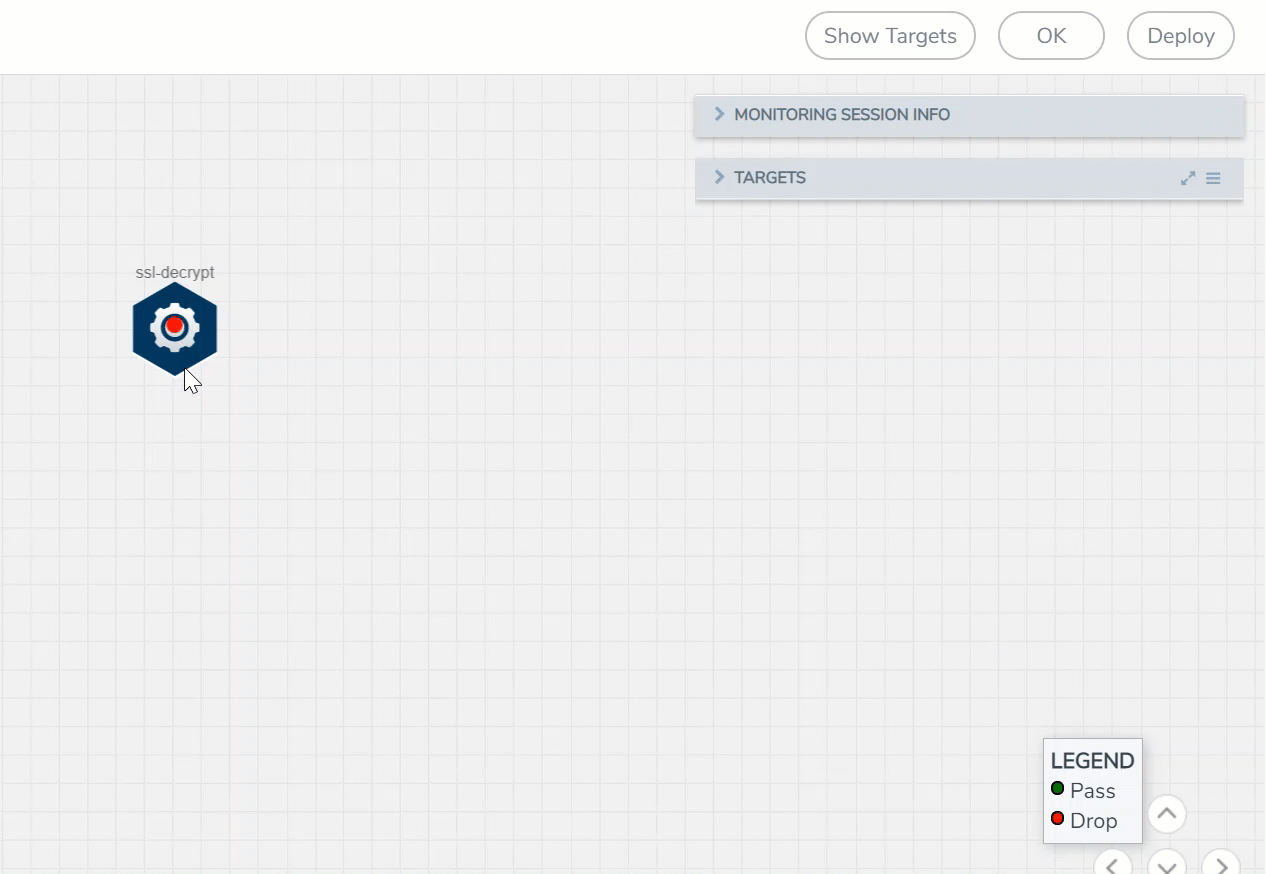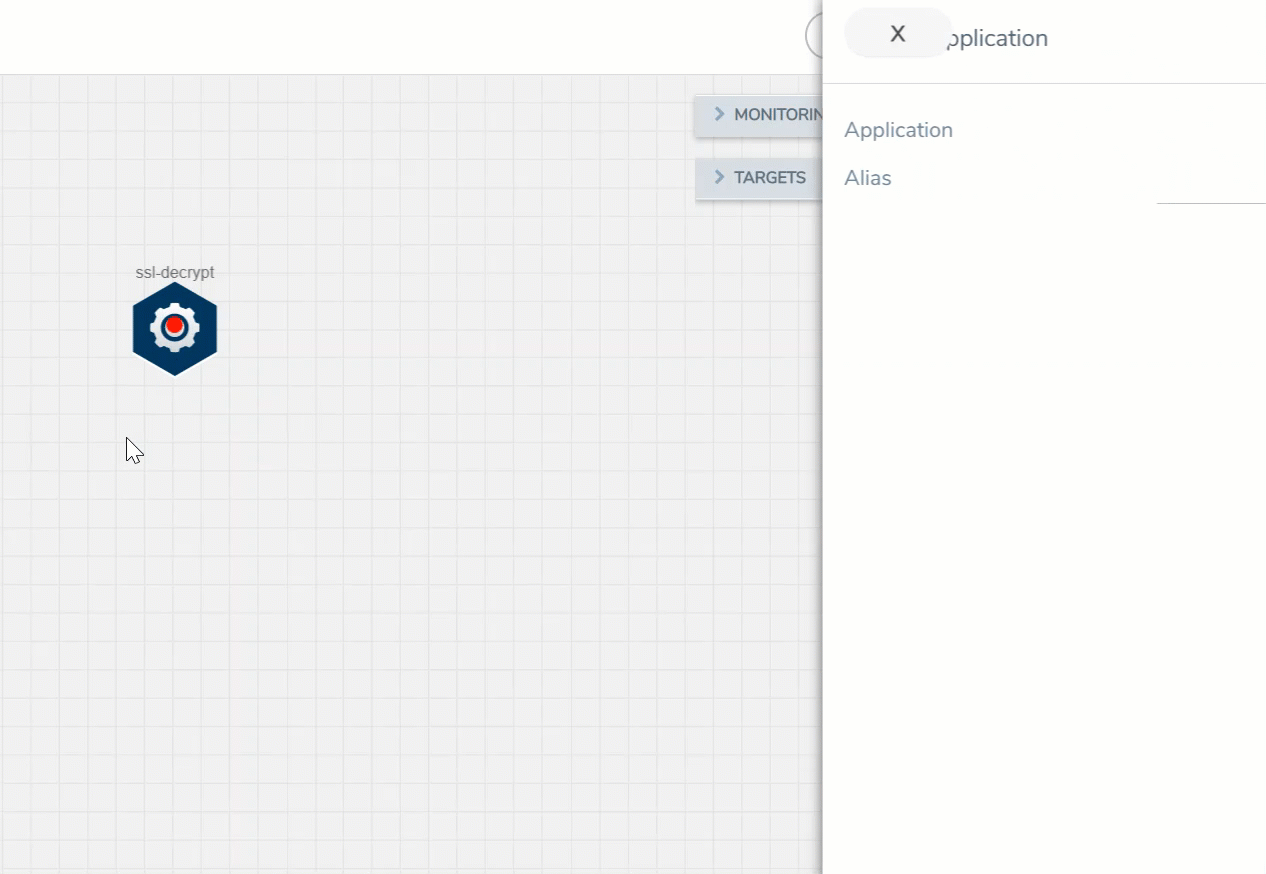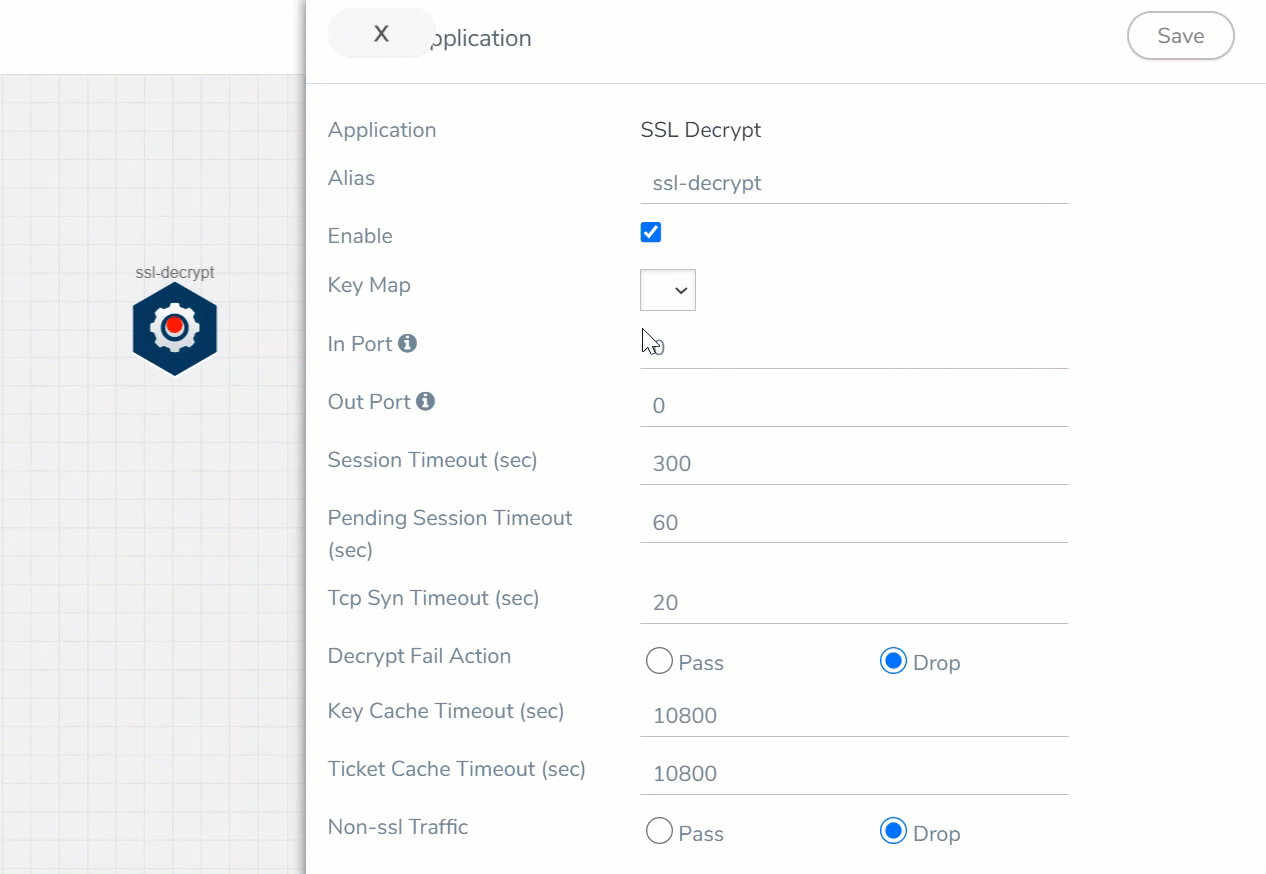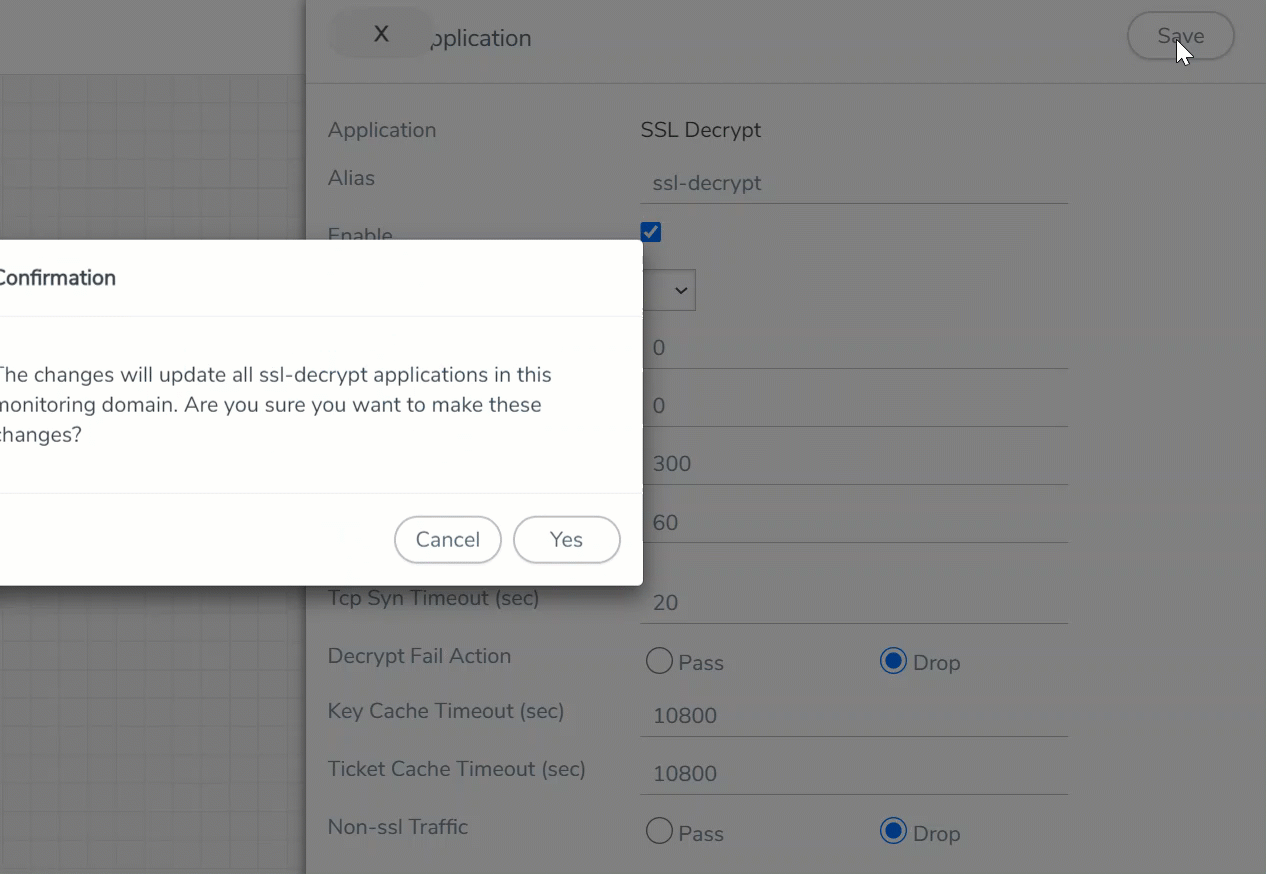
- Enter the following details in the Application quick view:
Fields
Description
Alias
Enter the alias name for the application.
Enable
Enable the box to enable SSL Decryption.
Key Map
Select the Key Map from the list of available Key Maps. Refer to Key Mapping for more details on how to map the key to SSL Service.
In Port
Enter the source port number from which the traffic should be fetched.
Out Port
Enter the destination port number to which the decrypted traffic should be delivered.
Session Timeout
Enter the value in seconds after which the session should be timeout. The default value is 300 seconds.
Pending Session Timeout
Enter the value in seconds after which the session must timeout if the session is in pending state
Tcp Syn Timeout
Enter the value in seconds after which the session must timeout when the session does not synchronize TCP.
Decrypt Fail Action
Select Pass to allow the traffic to pass through the application when the decryption fails and select Drop to drop the traffic before passing through the application when the decryption fails.
Key Cache Timeout (sec)
Enter the value in seconds until which the key cache information can be reused for resumption.
Ticket Cache Timeout (sec)
Enter the value in seconds until which the ticket cache information can be reused for resumption.
Non-ssl Traffic
Select Pass to allow the non-SSL traffic to pass through the application and select Drop to drop the non- SSL traffic before passing through the application.
- Click Save.
- Click Deploy. The Select nodes to deploy the monitoring session page appears.
- Select the GigaVUE V Series Nodes you want to deploy and select an interface for each GigaVUE V Series Node. Then, click Deploy.
What's Next
You can configure the traffic health monitoring for this application in the THRESHOLDS tab. You can select an existing template from the Threshold Templates drop-down menu or provide the threshold values. For more details on Traffic health monitoring and how to create threshold template, refer to
You can view the configuration health status and the traffic health status of the application in the HEALTH STATUS tab. For more details on configuration health and traffic health, refer to
You can view the statistics of the application in the STATISTICS tab.
You can view the session summary and session details of the SSL Decryption application in the SESSIONS tab. Select the V Series Node IP and enter the Server Name, Client/ Server IP address, and Subnet Mask. Then, click Apply to view the session summary and session details.
You can view the server certificate statistics in the SERVER CERTIFICATES tab. Select the V Series Node IP from the drop-down and enter the Key Alias. Then, click Apply.
All the service related details are displayed in the SERVICES tab. Select the V Series Node IP and Service Alias from the drop-down. Then, enter the IP Address and Port. Click Apply.
All the error codes and respective description are displayed in the ERROR CODES tab. To view the error code, select the V Series Node IP and Service Alias from the drop-down. Then, enter the IP Address and Port. Click Apply.



