Check for Required IAM Permissions in Azure
GigaVUE‑FM allows you to validate whether the policy attached to the GigaVUE-FM using "Managed Identity" or "Application ID with client secret" has the required IAM permissions and notifies the users about the missing permissions. You can check permissions while creating a Monitoring Domain and deploying GigaVUE Fabric Components using GigaVUE-FM by clicking the Check Permissions button on the Create Monitoring Domain page and Azure Fabric Launch page. The GigaVUE‑FM displays the minimum required IAM permissions.
IMPORTANT: "Microsoft.Authorization/roleAssignments/read" permission is required for validating the required permissions. Ensure to include "Microsoft.Authorization/roleAssignments/read" permission in your IAM policy.
The following are the prerequisites that are required to deploy GigaVUE Cloud Suite for Azure:
- IAM permissions - Check whether the minimum required permissions are granted for the instance where the GigaVUE‑FM is deployed. Refer to Permissions and Privileges (Azure) for more detailed information on configuring the required permissions in Azure.
- Access to public cloud endpoints - Check for access to the Azure cloud endpoint APIs.
- Subscription to the GigaVUE Cloud Suite for Azure- Before deploying the solution, you must subscribe to the GigaVUE Cloud Suite components from the Azure marketplace. Refer to Enable Subscription for GigaVUE Cloud Suite for Azure for more detailed information on how to subscribe to Gigamon Products.
- Security Group - Checks whether the required ports are configured in the security group. For more information on the security groups, see Network Security Groups
After you press the Check Permissions button, GigaVUE‑FM will verify the minimum required permissions. Any missing permissions will be highlighted with the respective message against the permission in a dialog box. You can use the displayed IAM Policy JSON as a reference and update the policy that is attached to the GigaVUE‑FM.
Note: When using Managed Identity (MSI), the IAM policy modified in Azure Portal takes a long duration to reflect in GigaVUE-FM. Refer to the Limitation of using managed identities for authorization section in Azure Documentation for more detailed information.
The following table lists the different available status and their descriptions.
|
Access Status |
Description |
|
Allowed |
This status is displayed if permission is configured correctly. |
|
Denied |
This status is displayed if permission is missing. For Example: If a permission is not configured in the IAM policy or if the permission access is explicitly denied in Azure, then the status is displayed as Denied. |
|
Failed |
This status is displayed if GigaVUE-FM fails to validate a permission. The reason and the probable cause are also displayed. |
|
Not Executed |
This status is displayed if a higher level of permission is denied or not configured, then GigaVUE-FM cannot validate a permission. For Example: If a subscription level permission is in denied or failed state then the resource level permission cannot be validated. |
|
Undeterminable |
The "Microsoft.Authorization/roleAssignments/read" permission is required to validate the required permissions. If this permission is not configured, the status of several other permissions cannot be determined. |
Refer to the following section for more detailed information:
- Check Permissions while Creating a Monitoring Domain
- Check Permissions while Configuring GigaVUE Fabric Components using GigaVUE‑FM
- View Permission Status Reports
Check Permissions while Creating a Monitoring Domain
To check the permissions while creating a monitoring domain, follow the steps given below:
- Go to Inventory > VIRTUAL > Azure, and then click Monitoring Domain. The Monitoring Domain page appears.
- Click New. The Monitoring Domain Configuration page appears.
- Enter the details as mentioned in the Create Monitoring Domain section.
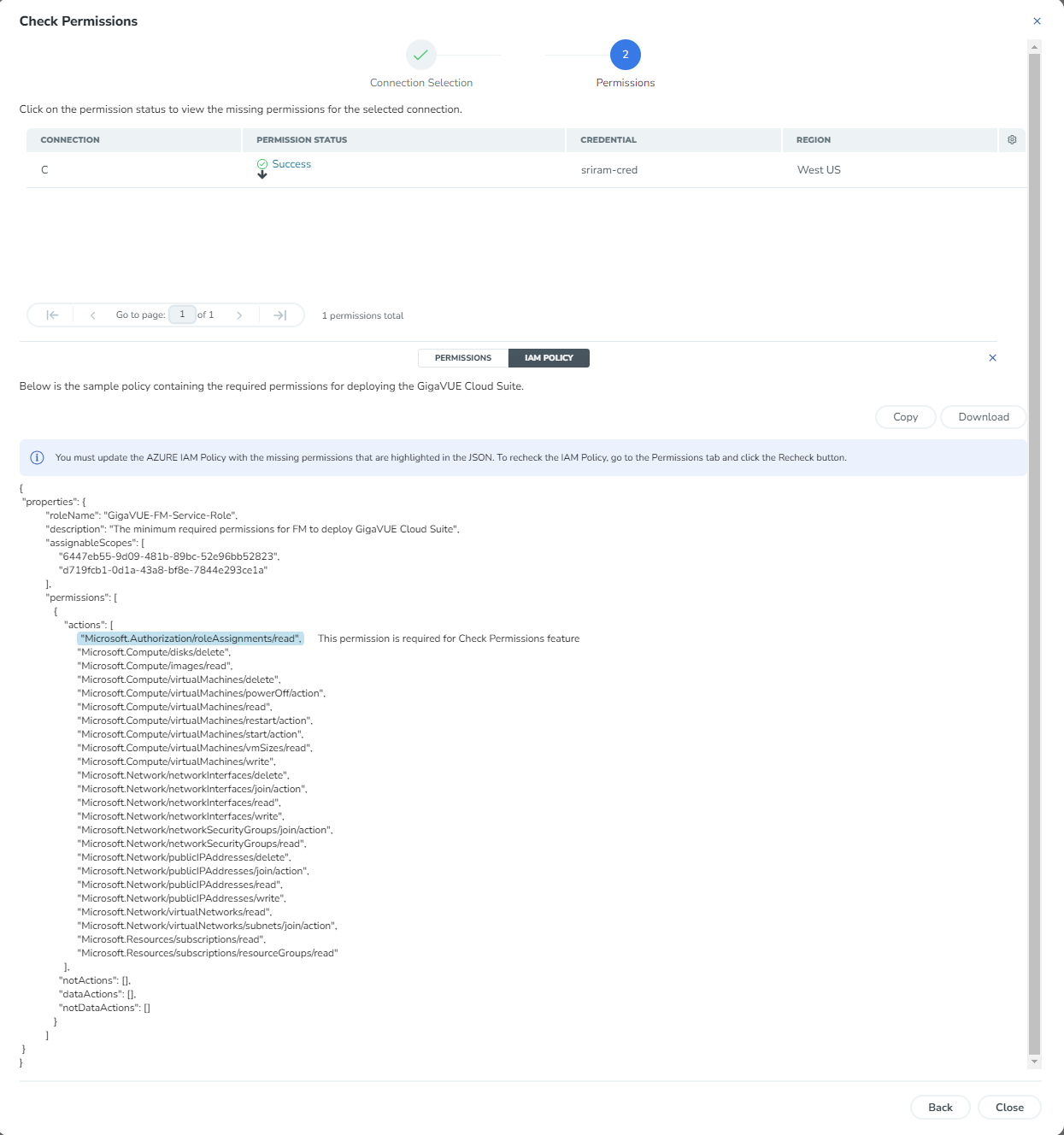
- Click the Check Permission button. The Check Permissions widget opens.
- Select the connection for which you wish to check the required permissions and then click Next.
- Click the Permission Status tab to view the missing permissions.
- The PERMISSIONS tab lists the permissions required to run GigaVUE Cloud Suite for Azure. Make sure to include all the permissions with Access Status as 'Denied' in the IAM policy.
- The IAM POLICY tab lists the sample policy containing the required permissions for deploying the GigaVUE Cloud Suite for Azure. You must update the Azure IAM policy with the missing permissions that are highlighted in the JSON. To recheck the IAM policy, go to the PERMISSIONS tab and click the Recheck button.
You can use the Copy button to copy the permissions to the clipboard. Also, you can use the Download button to download the permission in JSON format.
Note: After updating the IAM Policy, it takes around 5 minutes for the changes to reflect on the Check Permissions screen.
Check Permissions while Configuring GigaVUE Fabric Components using GigaVUE‑FM
To check for permissions from the Azure Fabric Launch page, follow the steps given below:
- In the Azure Fabric Launch page, enter the details as mentioned in Configure GigaVUE Fabric Components in GigaVUE-FM.
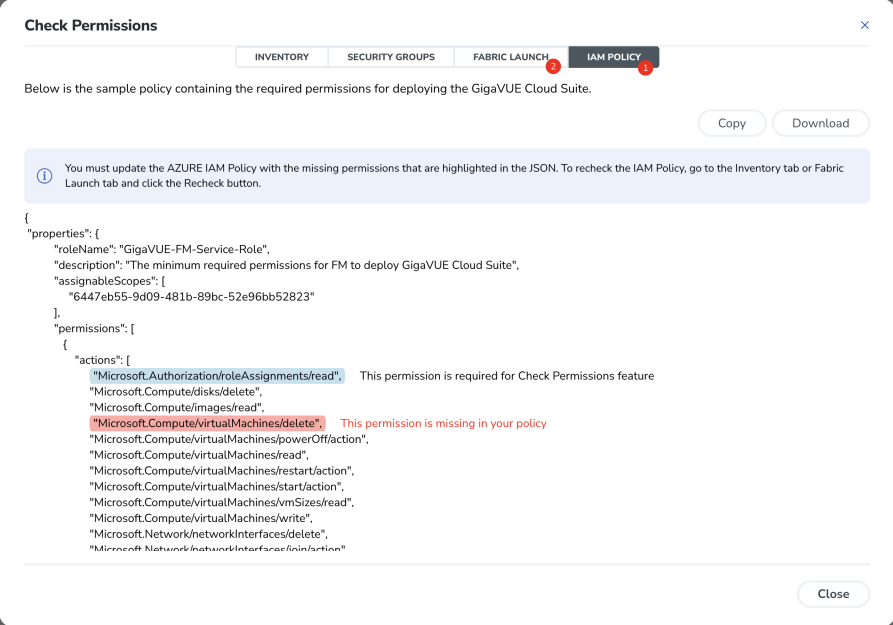
- Click the Check Permissions button. The Check Permissions widget opens.
- The permission status for Inventory, Security Group, and Fabric Launch are displayed in this widget.
- Click the INVENTORY tab and click Check Inventory Permissions, to view the required inventory permissions. Inventory permissions with the access status "Denied" could be missing in the IAM Policy or have restricted boundary
- Click the SECURITY GROUPS tab and click Check Security Group Permissions, to view the required ports that need to be opened for the security groups. The ports in the Denied State are not open in the security group. The ports with the status Explicit denied are blocked or restricted by the user. The ports with status Partially configured have incorrect IP address.
- Click the FABRIC LAUNCH tab and click Check Fabric Launch Permissions, to view the permissions required for deploying the GigaVUE fabric components. The Virtual Machine permissions with the access status "Denied" could be missing in the IAM Policy.
Note: The permissions "Microsoft.Compute/virtualMachines/write" and "Microsoft.Network/networkInterfaces/join/action" are dependent and cannot be validated separately. So, if either of the permissions is denied or not configured, then both permissions will be displayed as "Denied".
- The IAM POLICY tab lists the sample policy containing the required permissions for deploying the GigaVUE Cloud Suite for Azure. You must update the Azure IAM policy with the missing permissions that are highlighted in the JSON.
Note: Populating the permissions status for Fabric launch takes a longer duration.
View Permission Status Reports
The permission status reports consist of previously run Check permissions reports. They are auto purged once every 30 days. You can change the purge interval from the Advanced Settings page. Refer to Configure Azure Settings for more detailed information.
You can view the Permission Status Report in the following two ways:
- In the Monitoring Domain page, click Actions > View Permission Status Report.
- In the Monitoring Domain page, you can navigate to Settings and then click Permission Status Report
On the Permission Status Report page, you can use the Filter button to filter the reports based on File Name, Type, and Date.
To view or delete individual reports, select the report and click Actions button.