Entrust nShield HSM for TLS/SSL Decryption for iSSL
The purpose of this feature is to provide the capability for inline-TLS/SSL feature to work with HSM hardware. Some enterprises where security is paramount use nCipher HSM to keep the sensitive information such as private keys safe. For the deployments that involves HSM, changes need to be made for how the keys are used during session establishment for inline-TLS/SSL feature. Current inline TLS/SSL is enhanced to include Thales-Luna HSM support in addition to the current already supported nTrust-nCipher HSM solution.
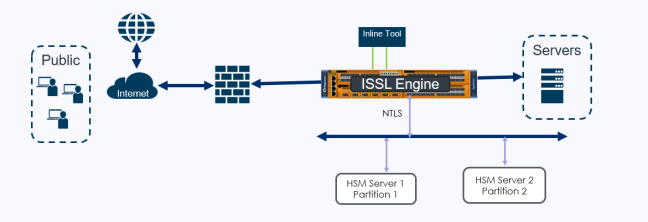
| 1 | ISSL with Thales Luna - Inbound support |
Supported Platforms
| GigaVUE-HC1 Gen3 |
| GigaVUE-HC3 Gen3 |
| GigaVUE‑HC1-Plus |
Limitations
Keep in mind the following limitations when configuring HSM:
| Gen3 nTrust-nCipher HSM iSSL and Gen3 Thales-Luna HSM iSSL cannot be configured together on the same H series device. (Also, you cannot configure each HSM on separate GigaSMART Gen3 card.) |
| Gen3 non-HSM iSSL and Gen3 HSM iSSL cannot be configured together on the same H series device. (Also, cannot be configured on separate GigaSMART Gen3 card.) |
| Gen2 non-HSM iSSL and Gen3 HSM iSSL cannot be configured together on the same H series device. (Also, cannot be configured on separate GigaSMART Gen2 and Gen3 cards.) |
PKCS#11 Library
The PKCS#11 (Public Key Cryptography Standards) is a standard programming interface to communicate with HSMs. This standard specifies an application programming interface (API), called “Cryptoki” to devices which hold cryptographic information and perform cryptographic functions.
Proprietary interfaces using Secure Object Library are provided to interact with the HSM for:
| Generating key pair within the HSM. |
| Installing existing key in the HSM. |
| Manufacturing Protection key operations. |
Refer to Configure Hardware Security Modules (HSM) and Configure Flexible Inline TLS/SSL Decryption Solution sections for more details on how to configure HSM Group and use HSM Group for TLS/SSL decryption for iSSL.



