Configure Internet Content Adaptation Protocol (ICAP)
Refer to the following sections that provide details about ICAP, its limitations, and instructions on how to configure the ICAP Client:
| About ICAP |
| Supported Platforms |
| Configure ICAP Client |
| ICAP - Rules, Notes, and Limitations |
About ICAP
The ICAP protocol serves as a communication interface for security tools like Data Loss Prevention (DLP) systems. Until software version 6.3, you cannot integrate inline SSL deployments with DLP-ICAP server as an inline tool. DLP tools are deployed outside of Gigamon's decryption zone as DLP tools need clear text traffic to inspect HTTP request/response.
Starting in software version 6.4, the ICAP Client app enables integration with the DLP ICAP server by functioning as an inline tool within the GigaSMART engine. Decrypted traffic from inline TLS/SSL is sent to the ICAP client and then forwarded to the ICAP server for inspection, providing enhanced security and visibility. If the ICAP application receives the decrypted traffic from a source other than Gigamon, it will function even without the iSSL deployment. ICAP app is part of TLS/SSL license SKUs.
The following figures illustrates the deployments in Inbound and Outbound with ICAP client support.
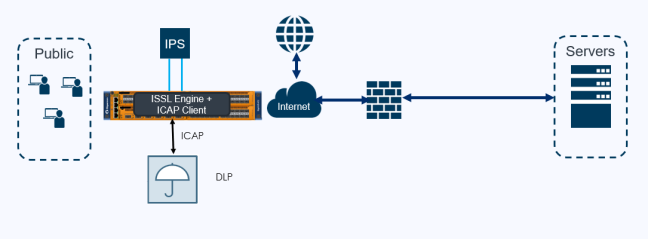
| 1 | Inline SSL Solution with ICAP Client support – Outbound Deployment |
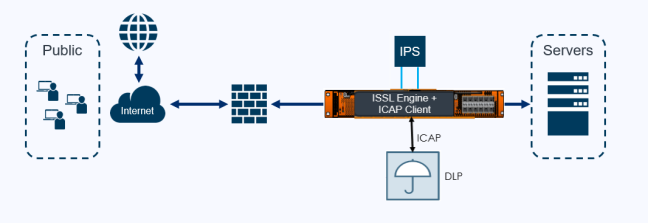
| 2 | Inline SSL Solution with ICAP Client support – Inbound Deployment |
Supported Platforms
ICAP Client app is supported in the following platforms and cards:
|
Platform |
Card |
|
GigaVUE-HC1 Gen3 |
SMT-HC1-S |
|
GigaVUE-HC1P Gen3 |
SMT-HC1-S |
|
GigaVUE-HC3 Gen3 |
SMT-HC3-C08 |
Configure ICAP Client
Following are the prerequisites that you must complete before you configure the ICAP Client:
| Configure the required inline networks. Refer to Configure Inline Network Ports and Inline Network. |
| Configure the required IP Interface. Refer to Configure IP Interface. |
Note: For ICAP, it is not necessary to add GS Groups when configuring IP interface. It will be added automatically when the port is added to ICAP Client.
To configure the ICAP Client:
| 1. | On the left navigation pane, go to Physical > Orchestrated Flows > Inline Flows, and then click Configuration Canvas to create a new Flexible Inline Canvas. |
| 2. | In the Flexible Inline Canvas that appears, select the required device for which you want to configure the ICAP Client. |
| 3. | Click the ‘+’ icon next to the ICAP Client option to create the new ICAP Client. |
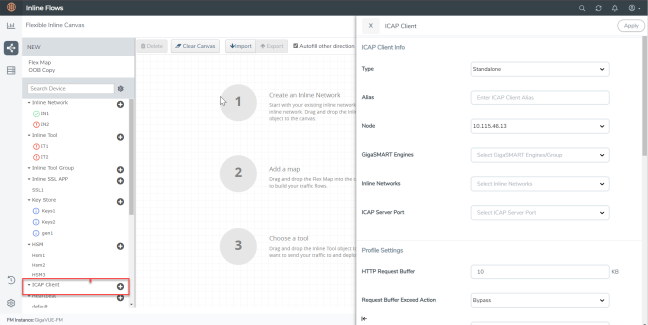
| 4. | In the ICAP Client properties pane that appears on the right, complete the required fields in the ICAP Client Info, Profile Settings, and the Server sections. Refer to ICAP Client—Field References for more details. |
| 5. | Click Apply to save the configurations. |
| 6. | Drag and drop the required inline network and inline tool into the flexible inline canvas. |
| 7. | Drag and drop the Inline SSL APP into the canvas. |
| 8. | Click Deploy. |
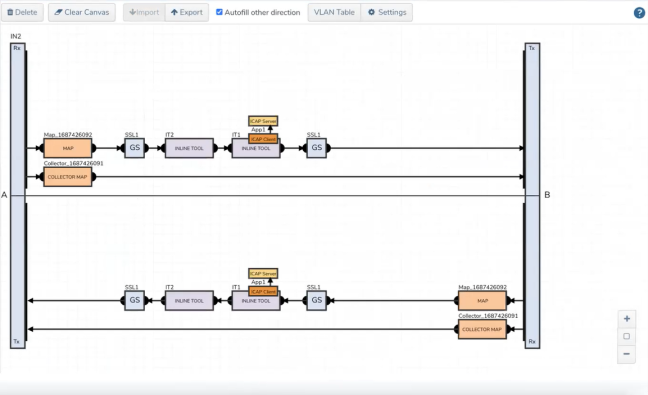
| 3 | ICAP Client APP—Deployed |
ICAP Client—Field References
The following table lists and describes the attributes that define the ICAP Client.
|
Field |
Description |
|
ICAP Client Info |
|
|
Type |
Select the required type from the following:
|
|
Alias |
Enter a unique name for the ICAP Client. |
|
Node |
Select the required node for which you want to configure the ICAP Client. |
|
GigaSMART engines |
Select the required GigaSMART engine. |
|
Inline Networks |
Select the required inline networks, which are the source for the ICAP app. |
|
Source Ports |
Select the required tool port of iSSL, which is connected to the inline network. (This option will not appear if you select standalone as type.) |
|
ICAP Server Port |
Select the required IP interface physical port. |
|
Profile Settings |
|
|
HTTP Request Buffer |
Enter the HTTP request buffer size. |
|
Request Buffer Exceed Action |
Select the buffer action on exceeding the size:
|
|
Preview Size |
Enter the required preview size. |
|
REQMOD |
Enable or disable the Request Modification Mode. |
|
RESPMOD |
Enable or disable the Response Modification Mode. |
|
Response Timeout |
Enter the response timeout in seconds. |
|
Response Timeout Action |
Select the response timeout action on exceeding the timeout:
|
|
Inactivity Timeout |
Enter the session inactivity timeout value in seconds. |
|
Port Range |
Enter the ICAP client source port range for connecting to ICAP server. |
|
Server |
|
|
Server Alias |
Enter a unique name for the ICAP Server. |
|
Description |
Enter a description for the ICAP Server. |
|
Port |
Enter the L4 port number on which the ICAP server is listed. |
|
Address |
Enter the L3 IPV4/IPV6 address of the ICAP server. |
|
Request Modification URL |
Enter the Request Modification service URL. |
|
Response Modification URL |
Enter the Response Modification service URL. |
|
Options URL |
Enter the ICAP options URL (if necessary). |
ICAP - Rules, Notes, and Limitations
Keep in mind the following rules, notes, and limitations when configuring the ICAP Client app:
| ICAP app gsop is not supported in the cluster environment. |
| It is not possible to chain ICAP app gsop with other gsops. |
| For a gsgroup, only one instance of ICAP gsop is allowed. |
| HTTP2 traffic ICAP inspection will not be supported in the current implementation for software version 6.4. As an alternative, you can enable HTTP2 downgrade in iSSL to enforce traffic in HTTP 1.1 version. |
| If HTTP messages are within preview length and if any Trailer is present, they will not be sent to the ICAP server. This is a limitation as part of the RFC 3507 design itself. |
| Any Trailer present in HTTP messages will be sent to the ICAP server as it is. No modifications will be made. There is no specific definition in ICAP RFC for HTTP trailers. |
| HTTP 1.1 pipeline will not be supported. That is multiple HTTP requests that are sent one after another. Only one outstanding HTTP request/response is supported in our ICAP Client. |
| The chunk extensions (a note that is added along with the data chunk during data transfer in http/1.1) in the http communication between client and server will not be sent to the ICAP server for inspection. |
| ICAP app cannot be deployed as inline tool with One-Arm iSSL, L3 NAT iSSL, and RIA iSSL. |
| In HC1P, the inline-network ports must be in the same slot. |
| ICAP server traffic will be disrupted randomly on the HC1P device when an inline pair map is deployed with multiple GigaSMART engine ports. TCP SYN packet from inline network IN1 side A reaches the engine port1 whereas SYN/ACK packet from inline network IN2 side B reaches the other engine port2. Issues in traffic will be observed due to this asymmetric pattern of traffic. |
| ICAP is not supported in GigaVUE-HCT chassis. |
| Refer to the table below for information on the number of GS engine ports required for each deployment module: |
|
Type |
Number of GS Engine |
Comments |
|---|---|---|
|
Standalone |
1 |
1 Gen3 for ICAP |
|
Inline SSL: Same Node |
2 |
1 Gen3 for ICAP and 1 Gen3 or Gen2 for iSSL Note: Inline SSL does not support HTTP2 Downgrade on Gen2. If HTTP2 Downgrade is required for iSSL, use 1 Gen3 for ICAP and 1 Gen3 for iSSL. |
|
Inline SSL: Different Node |
2 |
1 Gen3 for ICAP in the same node and 1 Gen3/Gen2 for ISSL in the other node |



