Create AWS Credentials
You can monitor workloads across multiple AWS accounts within one monitoring domain.
- After launching GigaVUE‑FM in AWS, if the IAM is attached to the running instance of FM, then the EC2 Instance Role authentication credential is automatically added to the AWS Credential page as the default credential. You must attach the IAM prior to creating a Monitoring Domain.
- If you use the Basic Credentials authentication credentials then you must add these to the GigaVUE‑FM in the AWS Settings page, or in the Monitoring Domain creation page.
To create AWS credentials:
- Go to Inventory > VIRTUAL > AWS, and then click Settings > Credentials
- On the AWS Credential page, click the Add button. The Configure Credential page appears.
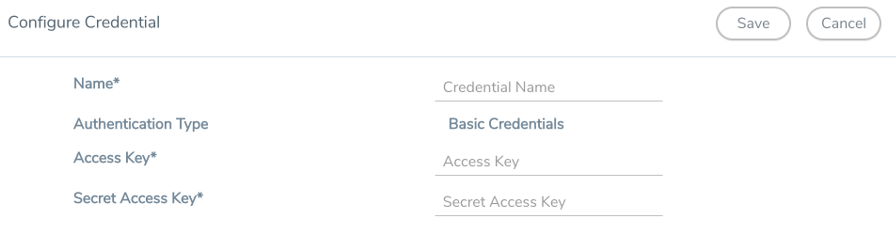
- Enter or select the appropriate information as shown in the following table.
Field
Action Name
An alias used to identify the AWS credential.
Authentication Type
Basic Credentials
For more information, refer to AWS Security Credentials.Access Key
Enter your AWS access key. It is the credential of an IAM user or the AWS account root user.
Secret Access Key
Enter your secret access key. It is the AWS security password or key.
- Click Save. You can view the list of available credentials in the AWS Credential page.
Required Policies and Permissions
To add multiple AWS accounts in a monitoring domain, you must add the access and role name of all the additional accounts to your STS policy. Following is a sample STS policy where the account2 and account3 are the accesses added to the existing account1 policy.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "sts:*",
"Resource": [
"arn:aws:iam::account2:role/ROLE-NAME"
"arn:aws:iam::account3:role/ROLE-NAME"
]
}
}For detailed information on the policies attached to GigaVUE‑FM, refer to Permissions and Privileges (AWS).
Following is the required IAM policy to exist in your remote networks:
{
"Version": "2012-10-17",
"Statement": [ {
"Action": [
"ec2:CreateTags",
"ec2:DeleteTags",
"ec2:Describe*",
"ec2:*TrafficMirror*",
"ram:GetResourceShareInvitations"
],
"Resource": "*"
"Effect": "Allow",
}
]
}Following is the required trust policy to set in your remote account:
{
"Version": "2012-10-17",
"Statement": [ {
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com",
"AWS": "arn:aws:iam::account:role/ROLE-NAME"
},
"Action": "sts:AssumeRole"
}
]
}


