Orchestrated Configurations
This chapter provides an overview of the configurations that can be automated from GigaVUE‑FM and describes how to use the Orchestrated Flows> Out-of-Band Flows option in the GigaVUE-FM GUI to define traffic flow through out-of-band visibility fabric.
Featured Content:
| About Intent Based Orchestrated Configurations |
| Benefits of Orchestrated Configurations |
| Supported Topologies |
| Orchestrated Configuration: Examples |
| Rules and Notes for Orchestrated Configurations |
| How to Create a Policy |
| Drop Rules |
| Import and Export Orchestrated Policies |
| Egress Filters for Additional Filtering Capabilities |
| Glossary |
About Intent Based Orchestrated Configurations
Intent Based Orchestration (IBO) is a new approach that enables you to automate the configuration tasks in GigaVUE-FM, thereby reducing the complexity and the manual labor involved in those tasks. IBO configurations (or 'Orchestrated Configurations') leverage the intelligence of GigaVUE-FM to detect the intention of the user, and accordingly translates the intentions into capabilities for configuring end-to-end flow maps.
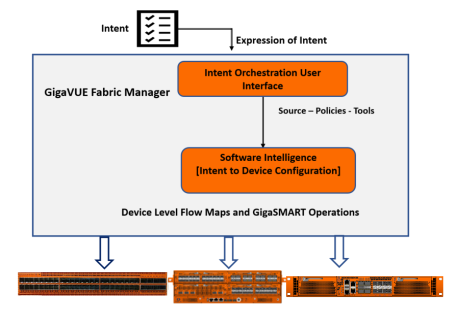
With Orchestrated Configurations, you can:
- Create policies, which are user-defined prescriptions for what to do with the traffic. The policies are translated internally into device-level maps that have the information required for the flow of traffic.
- Use filters and advanced mapping rules in policies, such as the following:
- L2-L4 filters
- Advanced filters such as GTP, ERSPAN, VXLAN, VNTAG, and MPLS
Note: Refer to the GigaVUE‑FM User's Guide and GigaVUE‑OS CLI Reference Guide for detailed information about the map rules and filters.
- Use packet transformation options along with the filters mentioned above to deliver the traffic to the desired tools. Supported packet transformation options include:
- De-duplication
- Masking
- Slicing
- Header Stripping
- Header Addition
Note: Tunneling and flow-based operations (GTP, NetFlow, Application Filtering Intelligence) will be supported in future releases.
Benefits of Orchestrated Configurations
Orchestrated configurations provides the following advantages:
The device-level flow maps created using the standard GigaVUE-FM GUI operations are priority-based maps. As a result some of the traffic may not reach the destination tools due to priority. With orchestrated configuration, you can create priority-free policies. These priority free policies are translated into internal device-level maps that direct the traffic to the configured tools. Refer to Priority-Free Policies section for detailed information.
Using the standard GigaVUE-FM operations (CLI and GigaVUE-FM), you cannot create maps with overlapping source ports. However, with orchestrated configuration you can create policies with overlapping sources and also policies with overlapping rules. Refer to Overlapping Sources in Policies for detailed information.
Without the Orchestration option, if you have to guide the tapped-and-aggregated traffic to the available traffic-monitoring and analysis tools, you must perform the following manual configurations using the standard GigaVUE-FM GUI operations:
- Create and group engine ports.
- Bind engine ports with the required application profiles to create GigaSMART Operations.
- Incorporate GigaSMART operations into flow maps.
- Use hybrid ports, if required.
Using Orchestrated Configurations you can overcome the above restrictions by simply specifying your intention for the traffic and the software intelligently creates the required device-level maps. You need not perform any of the required manual configurations mentioned above.
Orchestrated Configuration: Examples
This section provides examples for orchestrated configurations:
Priority-Free Policies
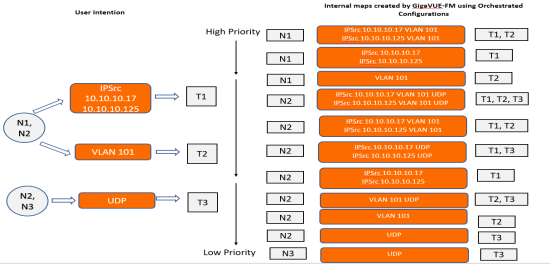
In this example traffic is tapped and sent through network port sources N1 and N2 to tools T1 and T2. The intention is to send IP traffic of specific source addresses (10.10.10.17 and 10.10.10.125) to tool T1 and VLAN traffic of a specific VLAN value to tool T2.
If you use the standard approach from the GigaVUE-FM GUI to create maps, then you have to configure the following device-level maps:
| Map from source ports N1, N2 with a rule to send traffic with IP source 10.10.10.17 and 10.10.10.125 to tool T1. |
| Map from source ports N1, N2 with a rule to send VLAN 101 traffic to tool T2. |
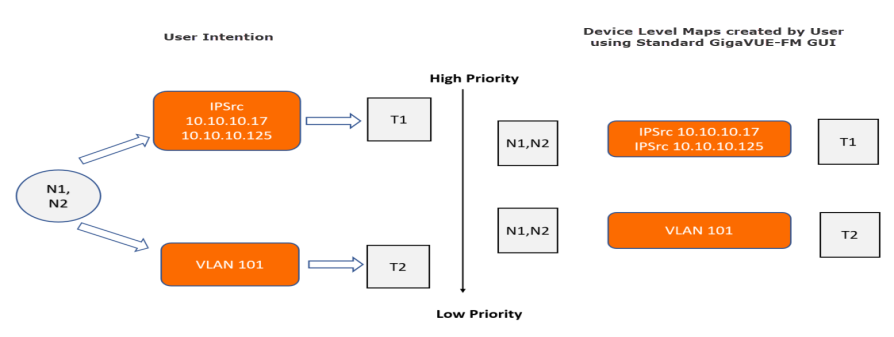
By default, the first map configured always has the highest priority. If a traffic has both IP and VLAN sources, IP traffic is sent to tool T1 but VLAN traffic is not delivered to tool T2.
With Orchestrated configuration, you only have to specify your intention for the traffic in GigaVUE‑FM GUI and create a policy. The software intelligently creates the following internal maps:
| Map from Sources N1, N2 to send both IP and VLAN traffic to tools T1 and T2. |
| Map from Sources N1, N2 to send IP traffic to tool T1. |
| Map from Sources N1, N2 to send VLAN traffic to tool T2. |
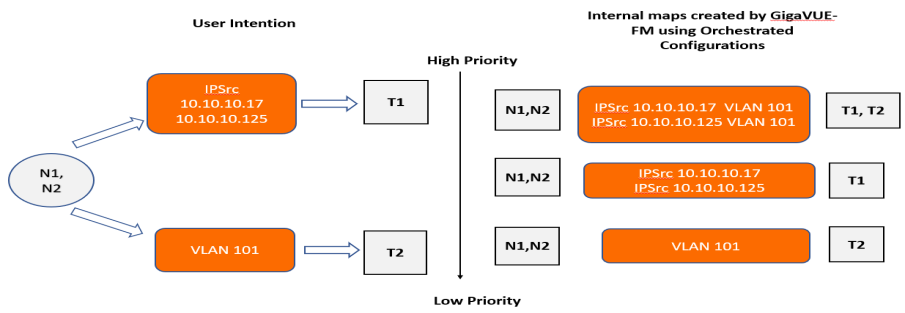
Note: You can create priority-based policies by enabling the Prioritize Rules checkbox in the Orchestrated Configuration GUI. Refer to How to Create a Policy for details.
Overlapping Rules in Policies
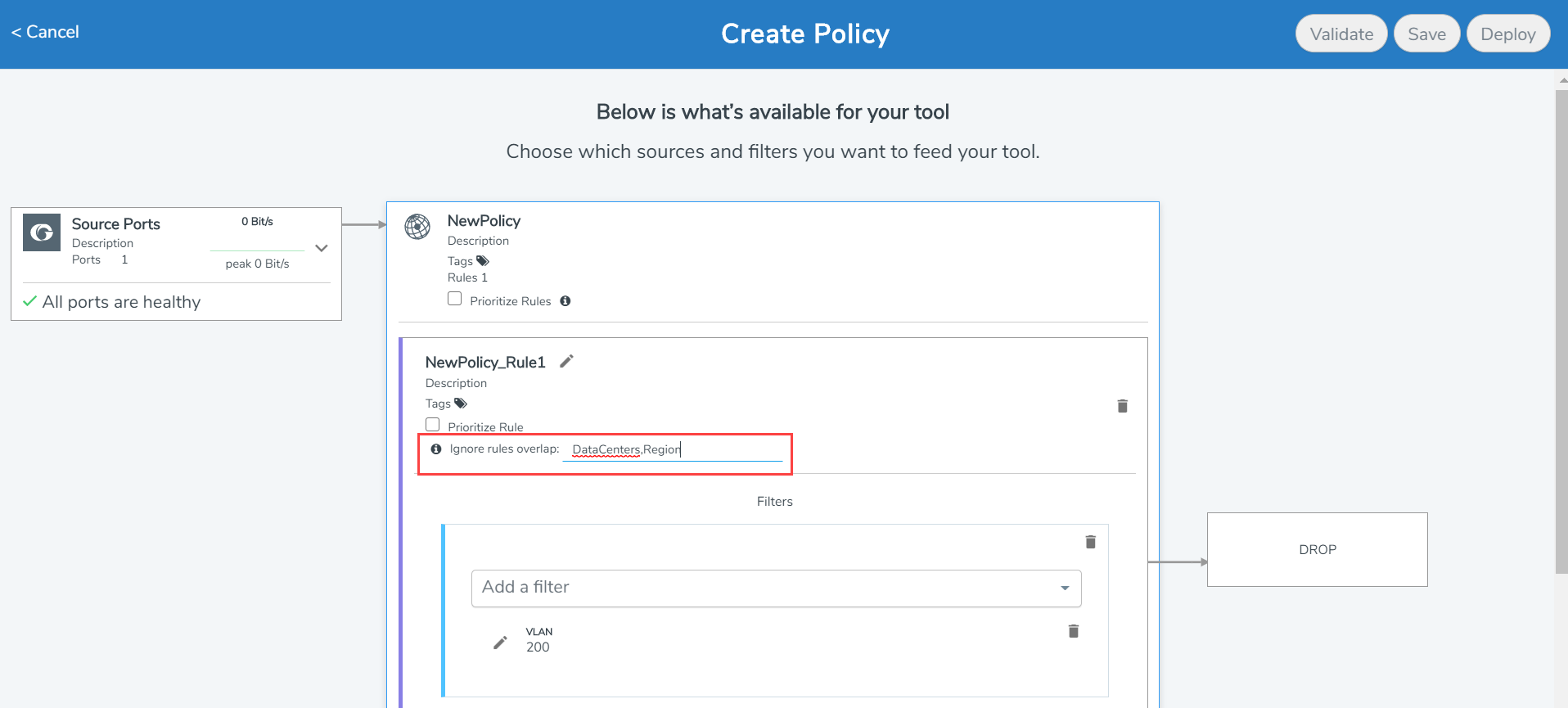
With priority free policies, internal maps with overlapping rules will be created. You can use the Ignore rules overlap option to restrict creating overlapping rules across policies, thereby saving filter resources. However, to ensure that the designated traffic reaches the destination tools in case the traffic matches multiple rules, use a comma separated list of tags to the ignore matching rules.
Overlapping Sources in Policies
In this example, traffic is tapped and sent through network port sources N1, N2, and N3 to tools T1, T2 and T3. The intention is to send:
| IP traffic from source ports N1, N2 to tool T1 |
| VLAN Traffic from source ports N1, N2 to tool T2 |
| UDP traffic from source ports N2, N3 to tool T3 |
You cannot create a map with overlapping sources using the standard GigaVUE-FM operations (CLI and GUI). However, with orchestrated configurations, you can create priority-free policies with overlapping sources as shown in the following figure.
Supported Topologies
Orchestrated configurations is supported:
- Within a Standalone device or within a cluster.
- In Muticluster topologies in which multiple physical clusters are connected using circuit ids and circuit tunnels.
Multicluster Topology
Orchestrated Configurations support creating policies in which the source ports, the destination ports and the engine ports are configured across clusters.
In the following example, traffic is tapped and sent through network source port group PG1 consisting of network ports from Clusters A, B and C. The intention is to send VLAN traffic to tool port group TG1 consisting of tool ports from Clusters A, B and C.
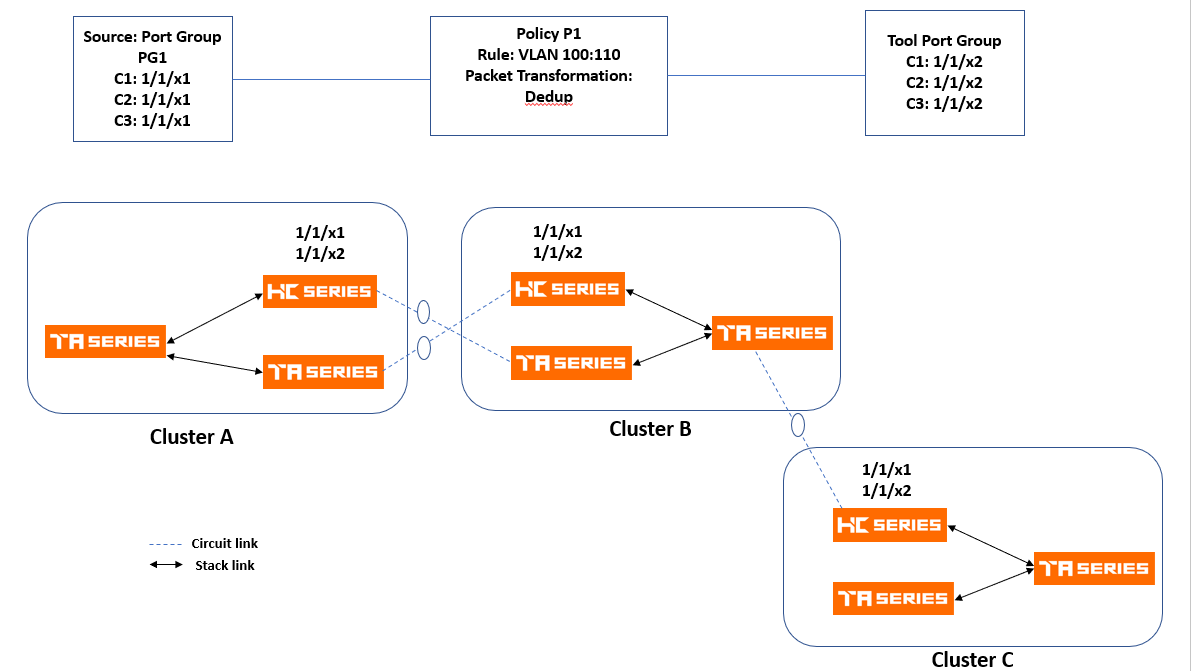
Note: You must manually select the engine ports, as automatic allocation of engine ports is not supported in multi-cluster arrangements.
Rules and Notes for Orchestrated Configurations
Refer to the following rules and notes for Orchestrated Configurations.
| The orchestrated configurations co-exist with the configurations created and maintained using the standard GigaVUE-FM interface options. However, you cannot edit the orchestrated configurations using the standard GigaVUE‑FM operations and vice-e-versa. |
| You can view the orchestrated policies and maps by enabling the Show Auto Generated maps option. GigaVUE-FM does not allow you to edit the auto generated maps (maps with prefix FMAuto/_FMAuto). |
| When creating a policy, ensure to not include the following special characters: . @ \ " % *: ; / , ? in the policy name. |
| The priority-free policies are translated into multiple device-level map configurations, which in turn can result in exhaustion of memory resources. However, the software does not allow you to deploy a policy that may result in exhaustion of memory resources. Appropriate warning messages that describe the reason for the policy not getting deployed, will be displayed. |
| Intent Based Orchestration feature is integrated with the GigaVUE-FM Tagging and RBAC infrastructure. Refer to the Tagging and RBAC Support section for detailed information. |
| GigaVUE-FM triggers alarms to track the changes in the health status of the policies. Refer to the "Alarms" section in the GigaVUE Administration Guide for more details. |
| In orchestrated configurations, you can drop the traffic instead of sending the traffic to a specified tool port. Refer to Drop Rules section for details related to drop rules. |
| You can use hybrid ports in a policy as both source ports and destination ports. You must configure the hybrid ports prior to using them in a policy. Refer to Work with Hybrid Ports section for details about configuring the hybrid ports. You can use hybrid ports for policy destination as follows: |
- Tool object
- Hybrid port
- GigaStream comprising of hybrid ports
Hybrid port that are part of the destination in a policy can also be used as source in another policy.
| Ports used in a policy will not be released until you delete the policy. |
| When you upgrade to software version 5.11.00, the policies created previously will not be retained in the system and will not be listed. You must create the policies again. |
| Orchestration is not supported in GigaVUE-HB1 device (both as a stand-alone device and also when it exists within a cluster). |
Create Orchestrated Policies
On the left navigation pane, click on  and under Physical > Orchestrated Flows> Out-of-Band Flows option in the GigaVUE-FM GUI to create and view policies, go to Traffic >. The following tabs are available:
and under Physical > Orchestrated Flows> Out-of-Band Flows option in the GigaVUE-FM GUI to create and view policies, go to Traffic >. The following tabs are available:
- Policies: Displays the list of configured policies. Click on a policy to view the following details:
- Health Status
- Deployment Status
You can deploy, undeploy, edit, delete, and create policies from this page.
- Tools: Displays the configured tools. You can associate new tools using the Create New Tool option. You can also group the tools to create a tool GigaStream. You can apply egress filters in tool ports. Refer to the Egress Filters section for more details.
- Sources: Displays the configured ports. You can edit the ports and create port groups from sources. Do not use fan out port as source port in policy.
- Filters: Displays the available filters. You can create a new template from the Filters option. Starting in software version 5.9, you can use advanced filters for creating the filter rules.
- Packet Transformations: Displays the supported packet transformation options. You can also create a template with the required Packet Transformation option.
- Visualize: You can select multiple policies and click Visualize to compare the policies.
Note: You can create policies by navigating to Actions > Create Policy from all of the tabs listed above. You can view the health status of the ports, tools and policies when creating the policy.
Prerequisites
You must have the following licenses:
| GigaSMART Masking |
| GigaSMART Packet Slicing |
| GigaSMART De-duplication |
| GigaSMART Header Addition |
| GigaSMART Header Stripping |
How to Create a Policy
Refer to the Rules and Notes for Orchestrated Configurations section before creating the policy.
To create orchestrated policies:
- On the left navigation pane, click on
 and under Physical > Orchestrated Flows> Out-of-Band Flows.
and under Physical > Orchestrated Flows> Out-of-Band Flows. - Click Create Policy. The Create Policy wizard is displayed. You can specify a name for the policy.
- Select Sources to select the available source ports or port groups.
- Click Select Tools to select the required tool ports (port type: tool port or hybrid). You cannot select a port that is already used. You can also associate a new tool using the Create New Tool option.
- Create the policy with the required rules. You can define the required filters and criterion in the rule.
- If you have configured multiple filters in a rule, then the traffic will be filtered only if all the filter rules are true.
- If you have configured multiple criterion in a rule, then the traffic will be filtered even if one of the criteria is true.
- Select the required packet transformation option. You can combine multiple packet transformation options with in a single rule. The GigaSMART packet transformation operations are performed in parallel.
- Click on the edit option next to the Processing Engine option to select the required GigaSMART engine ports for your rule. If you do not select the engine ports, then they will be automatically selected.
- For policies created based on multicluster topology, you must manually select the engine ports, as automatic allocation is not supported.
- For policies created based on single cluster topology, automatic allocation of engine ports is supported. However, only engine ports that have not been already used will be allocated.
- Enable the Prioritize Rules check box to create priority-based policy.
- Click the Tags option to associate the policy to tags. Refer to Tagging and RBAC Support section for more details.
- Click Validate to validate the policy. You can either:
- Click Save to save the policy. You can deploy the saved policies later.
- Click Deploy to deploy the policy.
Note: You can configure the sources, tools and policies in any sequence you want.
Note: If a port (port type: network or hybrid) is already used as a source port in any of the following standard GigaVUE‑FM configurations, then those ports will not be listed in the drop-down:
| Maps |
| Fabric Maps |
| Application Intelligence |
| 5G CUPS solution |
However, you can view all the ports in the Ports page.
Note: You can select Drop to drop the packets without selecting the tools. Refer to the Drop Rules section for details related to drop rules.
Note: You can create a policy with multiple rules. With in each rule, you can configure multiple criteria and multiple filters and use them together with the packet transformation options.
Note: Engine ports that have not been used in standard GigaSMART operations will only be available for selection. You cannot edit or delete an engine once a policy is deployed. However, you can remove the packet transformation and add the packet transformation option with a different engine.
Note: Use the Everything Else option to configure the shared collector. Refer to the GigaVUE Fabric Management Guide for details on Shared Collector.
The policy thus created is listed together with the list of policies. You can edit, delete, deploy and undeploy a policy, as required.
Tagging and RBAC Support
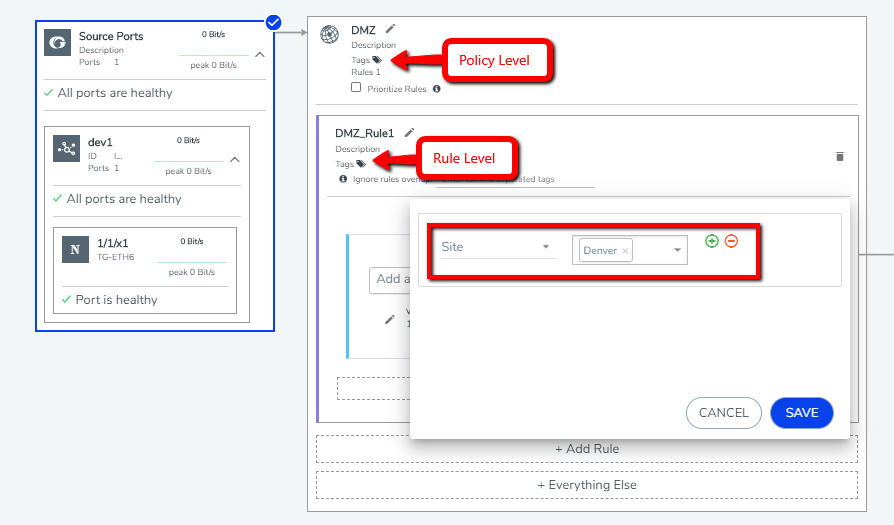
Role Based Access Control (RBAC) in GigaVUE-FM controls the access privileges of users and restricts users from either modifying or viewing unauthorized data. In Orchestrated Configurations, RBAC controls the accessibility of the users to the policies based on the tags. Tags can be either RBAC tags or aggregation tags. Multiple tags can be assigned to policies and rules.
Note: RBAC tags are supported only at the policy level. The orchestration wizard allows RBAC tags to be applied at the rule level as well, though it is not supported in this release.
To associate policies to tags:
- Click the Tags option at the policy level. You can associate tags either at the time of creating a policy or edit an existing policy.
- Select the required tag keys and tag values.
- Click Save.
Note: The tag key and the associated tag values must be created in advance in GigaVUE- FM. Refer to the "Tags" and "Role Based Access Control" sections in the GigaVUE Administration Guide for more details
Once you associate the policy to a tag, only users with fm_super_admin role or users with read/write access to the Traffic Control Management category can access the policies.
Drop Rules
You can use the Drop option in the 'Create Policy' wizard as the destination to drop a packet. For a drop rule to pass a packet, it must be used together with a pass rule or with the 'Everything Else' rule, such that the packets that do not match the drop criteria will be forwarded to the tools.
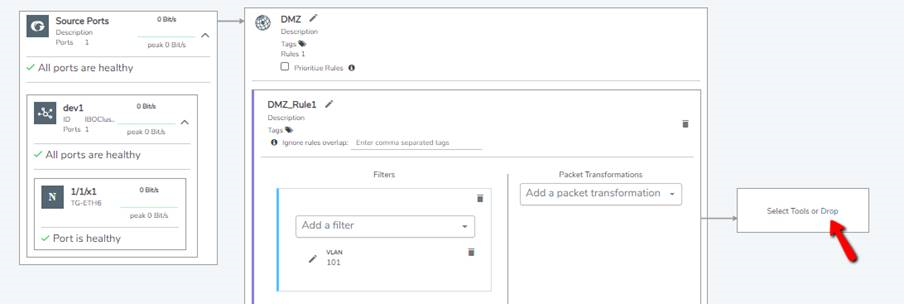
In orchestrated configurations, there are no rule priorities for pass rules. However, the following is the order of priority for prioritized and unprioritized drop rules together with the pass rules:
- Prioritized drop rules
- Pass rules
- Unprioritized drop rules
- Default collector
A drop rule, by default, has lower priority than the pass rule and higher priority than 'Everything else'. Therefore, a drop rule will drop the traffic before the traffic gets passed to the destination of the 'Everything Else' rule. However, a prioritized drop rule has the highest priority amongst all the rules in a policy and will drop matching traffic before any other policy rule can process that traffic.
Consider a scenario in which the intent is to drop packets with VLAN 101 and pass packets with IP version 4. Based on the default settings, if there is only IPv4 traffic on the source side, packets with VLAN Id 101 will not be dropped because pass rule has higher priority than the drop rule. To choose 'Drop' as high priority within the policy, you must prioritize the drop rule by checking the 'Prioritize Rule' option.
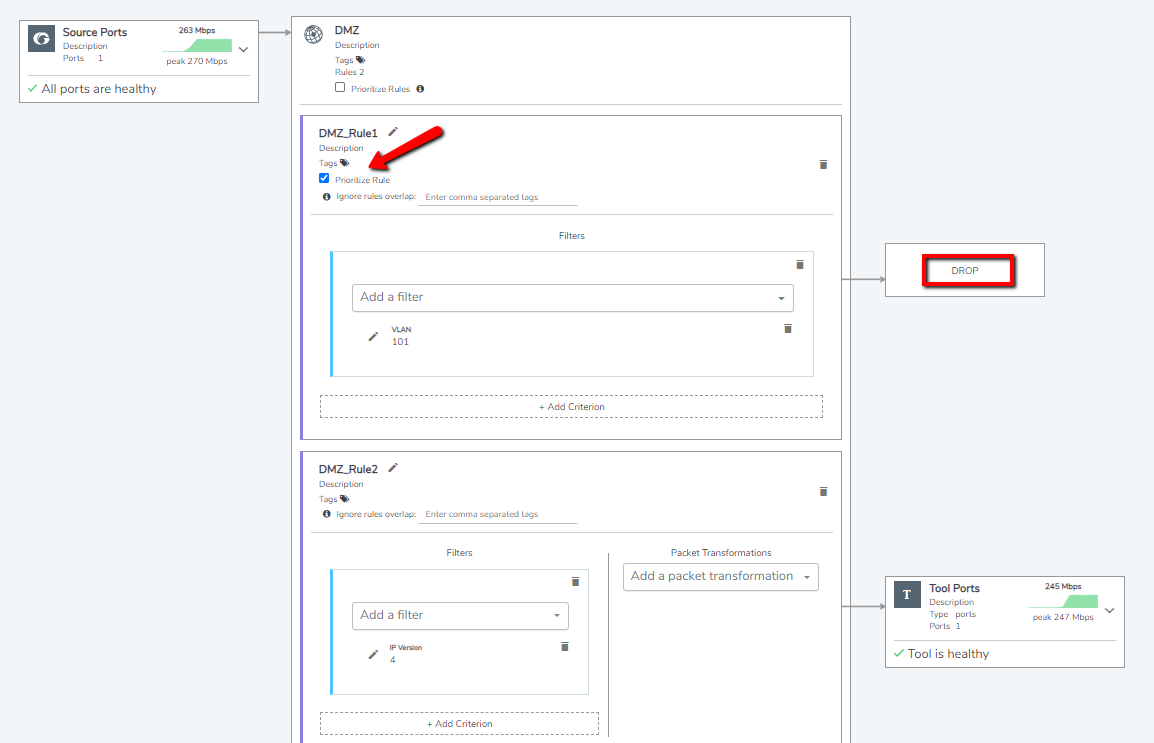
Note: To prioritize the drop rules in deployed policies, you must first undeploy the policy.
Import and Export Orchestrated Policies
Starting in software version 5.11.00, you can import and export an orchestrated policy in YAML format. This allows you to bulk deploy the policies.
The following are the advantages of importing and exporting policies:
- Retrieve a policy that was deleted unintentionally.
- Deploy the policy in another device.
- Re-deploy a policy in the device after GigaVUE-FM is upgraded to a new version (in case of issues in the existing solution).
The YAML file contains the following information:
- Policy
- Sources
- Rules
- Packet Transformation
- Destination
The below is the Import and Export Policy sample template of a YAML file. You can use the following sample template as a reference while building a policy in YAML format.
name: <PolicyExample>
priority: false
deployed: false
source:
- <IP address of the device>:<Port Number>
- <Network Name>
rules:
- ruleName: <Rule Name>
tags: chicago
type: pass
highPriorityDrop: false
noExpansionTags:
criteria:
- criteria1:
filters:
- type: ipSrc
addresses:
- <IP address of the device>
- <IP address of the device>
- type: portSrc
addresses: 5
- type: ipVer
addresses: 4
- criteriaWithBinding
packetTransformation:
- type: dedup
parameters:
action: drop
timer: 50000
ipTclass: include
vlan: ignore
tcpSeq: include
ipTos: include
- Slicing-gsApp
tools:
- Tool1
# it is practical to have all the tool bindings separate from the policy body in order to leave the policy body as an abstract policy template
toolBindings:
- toolName: Tool1
# in the future we may have also metadata receivers
receiverType: packets
groupingType: replicate
outputs:
- type: port
ports:
- Generic2:22/3/x1
# possibly more tool bindings...
sourceBindings:
- sourceName: ChicagoServers
tags:
inputs:
# in the future we will have various types including types that reflect tunnelling arrangements
- type: port
clusterName: <ClusterName>
ports:
- cluster1:22/2/x12
- cluster2:22/2/x11
criteriaBindings:
- criteriaName: CriteriaWithBinding
filters:
- type: ipDest
addresses:
- <IP address of the device>
- <IP address of the device>
- type: port
addresses:
- 5
Rules and Notes
Refer to the following rules and notes:
- You can export policies that either deployed or undeployed. However, when you import a policy, it will be in undeployed status. You must manually deploy the imported policy.
- You cannot import or export the egress port filters in a policy. You must manually apply them.
- When you export a policy that has GigaStream , port groups and other such groups, you must ensure that those groupings exist when you import the same policy. This also applies to tools that were created through the tool wizard.
- Port types involved in a policy that is exported must not be changed when trying to import the same policy.
- If templates were used to create a policy that was exported, then those templates must remain when importing a policy.
- You can import and export several policies in one operation.
Import and Export Orchestrated Configuration
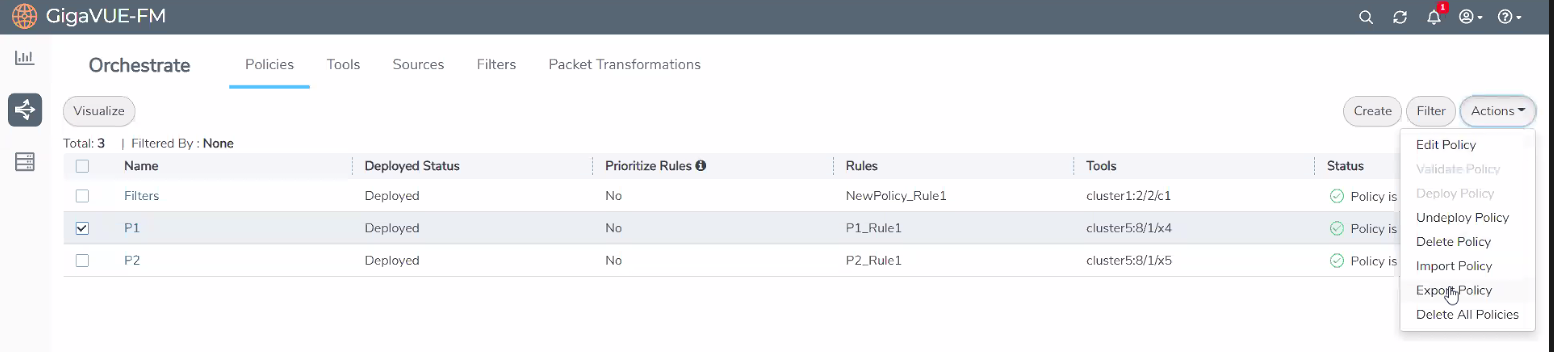
To export a policy:
- In the Policies page, select the policy that must be exported.
- Select Actions and click Export Policy. The policy is downloaded as an YAML file.
- Save the file to the required location.
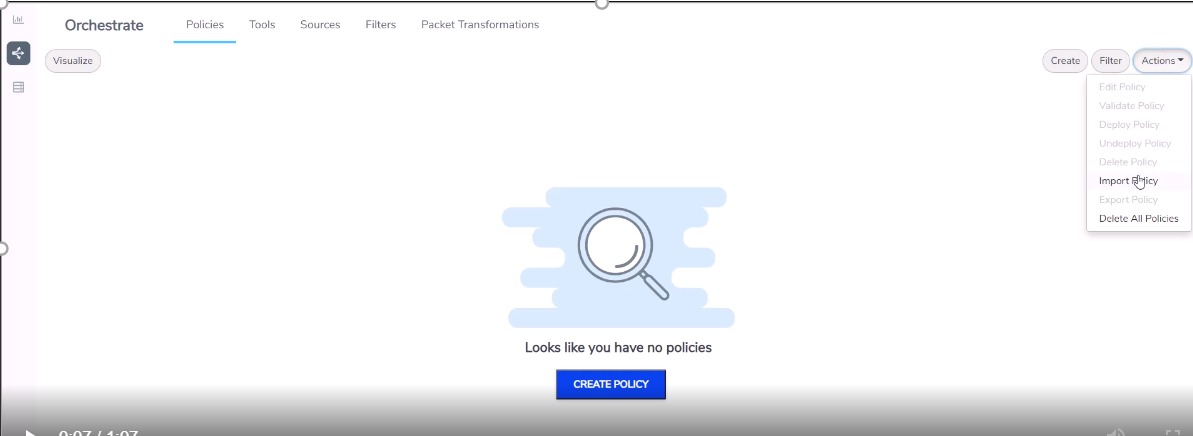
To import a policy:
- In the Policies page, select Actions and click Import Policy.
- Browse to the folder that has the required policy file in YAML format.
- Select the file and click Open. The Import button gets activated.
- Click Import and refresh the page.
Egress Filters for Additional Filtering Capabilities
Egress filters provide additional filtering capabilities when applied on tool or hybrid ports in a policy. Egress filters are used to pass or drop the traffic and can be combined logically using 'AND' and 'OR' operators.
Note: The number of egress filters vary depending on the platform. Refer to the Port Filters section for the number of filters allowed for each platform.
To apply egress filter for a tool port in a policy:
- Select the tool port or the hybrid port for which you need to add filters.
- Click the Egress filter icon and click Edit.
- Click Add a Rule.
- Select the required conditions.
- To create an egress filter with logical AND: In a single rule, create multiple conditions. That is, create Rule 1 with conditions for filtering IPv4 traffic and source port as '443'. Traffic will get filtered to the tool only if both of these conditions are true.
- To create an egress filter with logical OR: Create multiple rules with required conditions. That is create Rule 1 to filter IPv4 traffic and Rule 2 to filter traffic from source port ''443'. Traffic will get filtered to the tool even if one of the condition is true.
- Define a name to each of the rules created and click Save.
- You can click Pass or Drop against each of the rules to either pass the traffic to the destination or to drop the traffic. Refer to the following notes for pass and drop rules:
- Drop rules are applied first.
- If there are only drop rules, then all the traffic except that specified in the drop rule(s) will be passed.
- If there are only pass rules, only the traffic specified in the pass rule(s) will be passed and all other traffic will be dropped.
- If there are both drop and pass rules, only the traffic specified in the pass rule(s) that does not also match the drop rule(s) will be passed.
Note: Use the edit icon to edit the egress filter directly from the canvas. If you edit the egress filter in edit mode, the Deploy button is disabled.
- Policy: A user defined instruction for what to do with the traffic
- Packet transformation: GigaSMART Operations
- Everything else: Shared Collector
- Filters and Criteria: Map rule criteria to filter the traffic



