About Flexible Inline Arrangements
Flexible inline arrangements is an approach to guide multiple inline traffic flows through a user-defined sequence of inline tools and inline tool groups. It uses the same software constructs as the existing Inline Bypass solution, such as inline network, inline tool, and inline tool group. Flexible inline arrangements support physical protection based on the specialized hardware on BPS modules. It also supports both protected and unprotected inline network links.
Flexible inline arrangements offers an alternative to classic Inline Bypass. Classic Inline Bypass functionality remains intact for backwards compatibility. For information on configuring Inline Bypass solutions (classic), refer to Inline Bypass Solutions.
Using flexible inline maps, traffic from the same inline network can traverse different sequences of inline tools and share tools across traffic flows or with other inline networks.
You can identify specific flows of traffic using Layer 2 to Layer 4 rules, then designate the tools that will inspect the traffic, and specify the order of the tools. For example, you can send Web traffic (defined by L4 port, 80 and/or 443) through a Web Application Firewall (WAF) and an Intrusion Prevention System (IPS), have backup traffic that might bypass inspection, and send all other traffic through the same IPS.
1 Flexible Inline Arrangements Scenario illustrates a complex inspection scenario that is enabled by flexible inline arrangements.
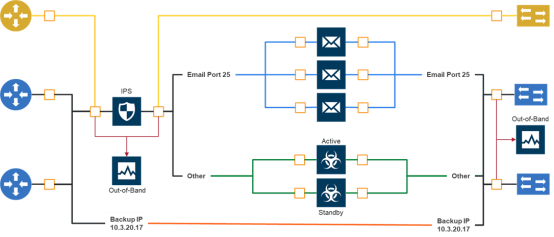
| 1 | Flexible Inline Arrangements Scenario |
In this example, on the left, there are three network links, all of which share the IPS. The details are as follows:
| At the top of the figure, the yellow line represents a flow of network traffic that only needs IPS inspection. |
| In the middle of the figure, the Email and Other traffic represents network traffic flows that go through IPS inspection first, then the Email traffic goes to dedicated inspection tools, here shown as three tools in an inline tool group, and the Other traffic goes to a threat protection active/standby pair. |
| At the bottom of the figure, daily Backups of already-inspected traffic goes to bypass. |
Although not shown graphically in 1, the traffic in the reverse direction can have a different order of tools than the west-east traffic.
Refer to the Deploying GigaSECURE Inline SSL Solution using Flexible Inline Gigamon Validated Design for more information.



