Slicing
Packet Slicing allows you to truncate packets after a specified header and slice length, preserving the portion of the packet required for monitoring purposes. Slicing operations are typically configured to preserve specific packet header information, allowing effective network analysis without the overhead of storing full packet data.
Packets can have multiple variable-length headers, depending on where they are captured, the different devices that have attached their own headers along the way, and the protocols in use (for example, IPv4 versus IPv6). Because of this, slicing operations with a hard-coded offset will not typically provide consistent results.
To address this, the Slicing application lets you configure Packet Slicing using protocols that allow you to start slicing from a particular number of bytes after a specific packet header (IPv4, IPv6, UDP, and so on). The Slicing application parses through Layer 4 (TCP/UDP) to identify the headers in use, slicing based on the variable offset identified for a particular header instead of a hard-coded number of bytes.
To add a Slicing application:
- Drag and drop Slicing from APPLICATIONS to the graphical workspace.
- Click the Slicing application and select Details. The Application quick view appears.
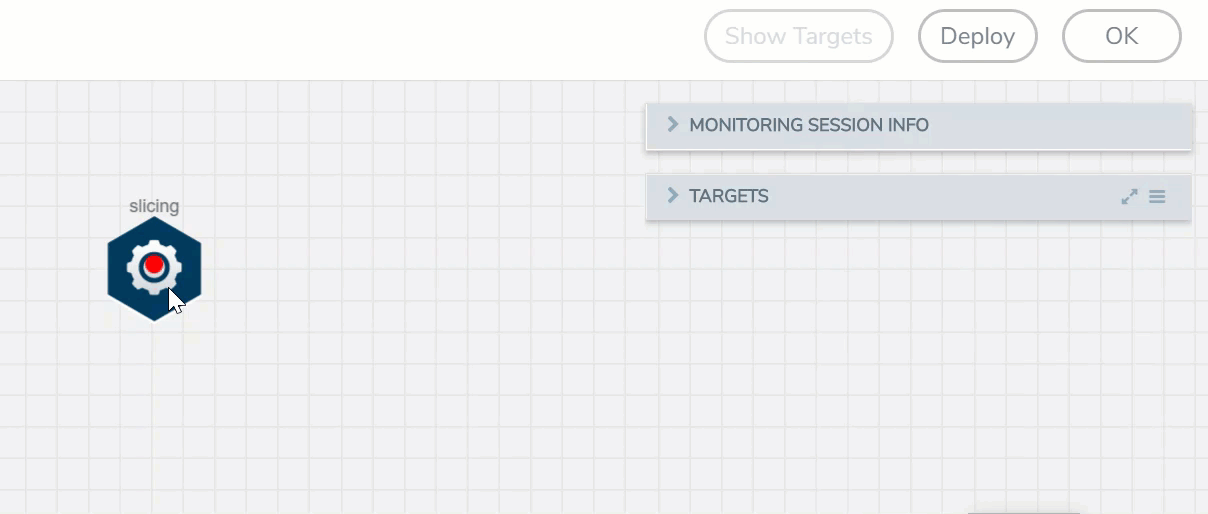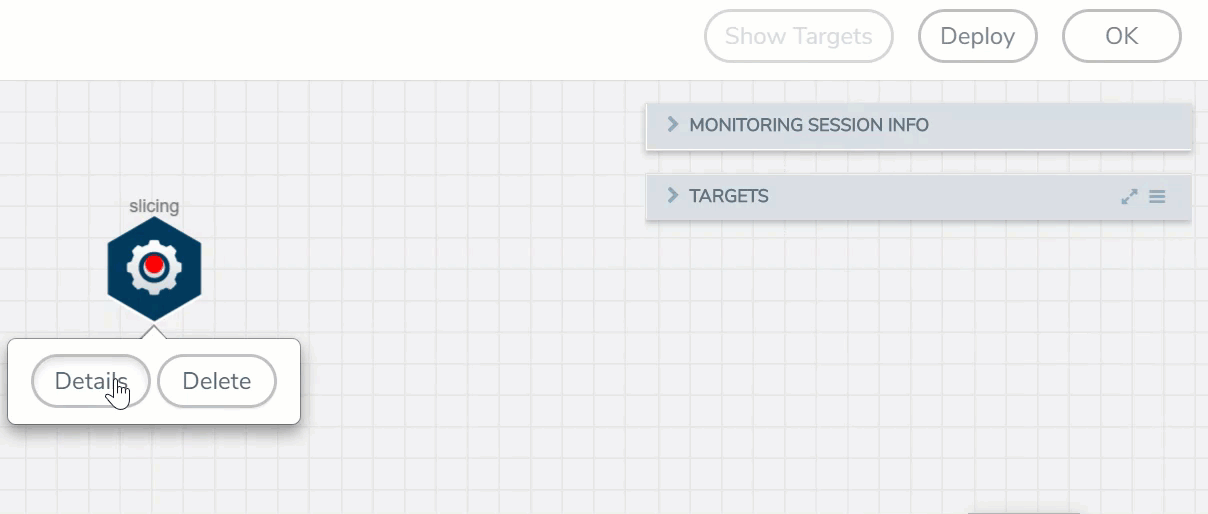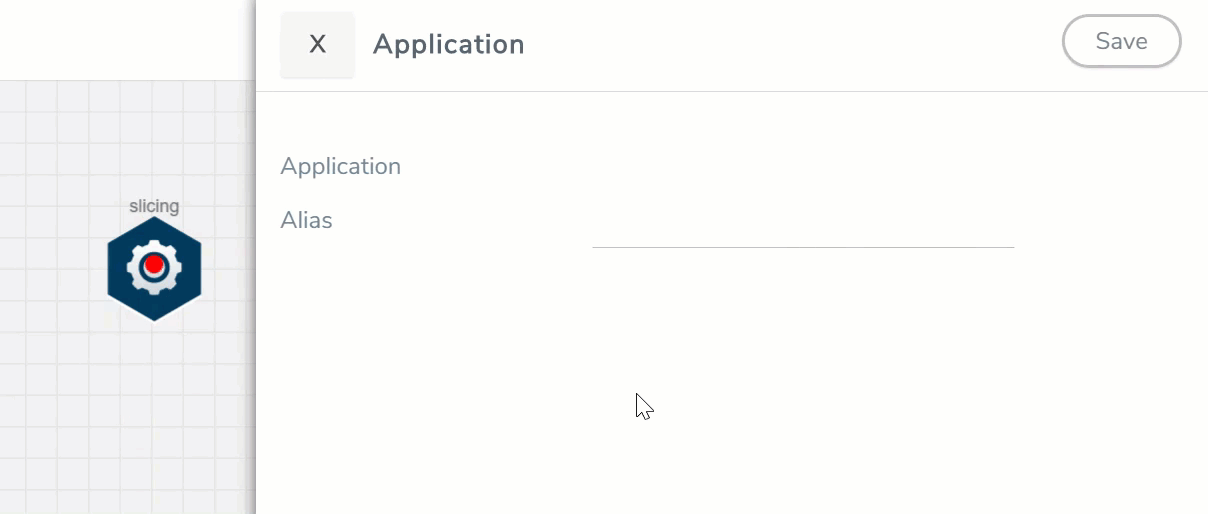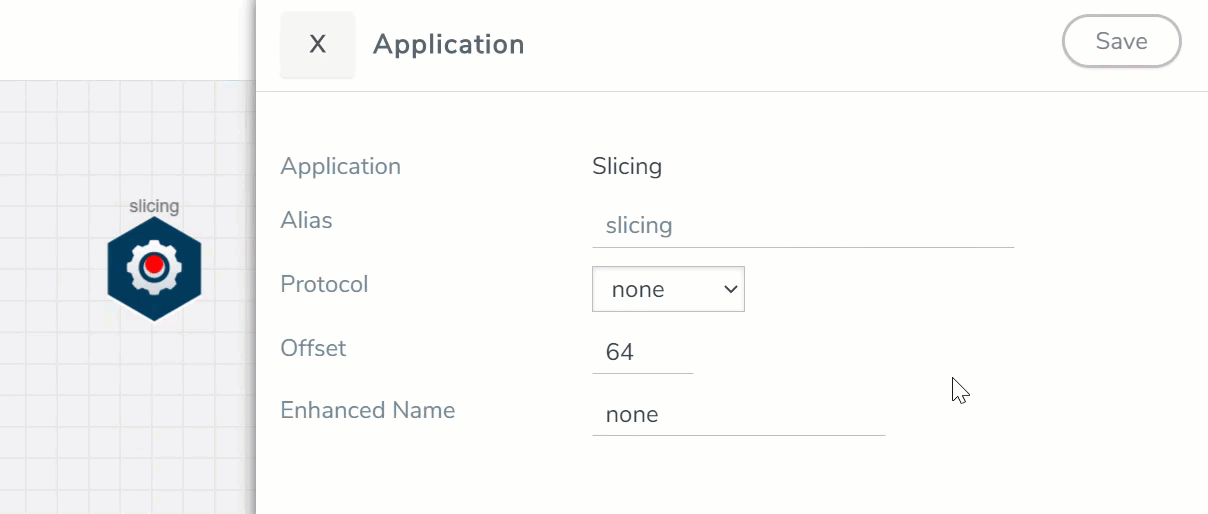
- In the Application quick view, enter the information as follows:
Component
Description
Alias
Enter a name for the application.
Protocol
The following are the protocols that you can select for from the protocol drop-down list:
o None –Slice starting a specific number of bytes from the start of the packet. o IPV4 – Slice starting a specified number of bytes after the IPv4 header. o IPV6 – Slice starting a specified number of bytes after the IPv6 header. o UDP – Slice starting a specified number of bytes after the UDP header. o TCP – Slice starting a specified number of bytes after the TCP header. o FTP – Identify using TCP port 20 and slice payloads using offset from the TCP header. o HTTPS – Identify using TCP port 443. Slice encrypted payloads using offset from the TCP header. o SSH – Identify using TCP port 22. Slice encrypted payloads using offset from the TCP header. The Slicing application can provide slicing for GTP tunnels, provided the user payloads are unencrypted. Both GTPv1 and GTPv2 are supported – GTP' (GTP prime) is not supported. Keep in mind that only GTP-u (user plane packets) are sliced. Control plane packets (GTP-c) are left unmodified because of their importance for analysis.
o GTP – Slice starting a specified number of bytes after the outer GTP header. o GTP-IPV4 – Slice starting a specified number of bytes after the IPv4 header inside the encapsulating GTP packet. o GTP-UDP – Slice starting a specified number of bytes after the UDP header inside the encapsulating GTP packet. o GTP-TCP – Slice starting a specified number of bytes after the TCP header inside the encapsulating GTP packet. Offset
Specify the length of the packet that must be sliced.
- Click Save.
Slicing application is successfully configured.
What's Next
You can configure the traffic health monitoring for this application in the THRESHOLDS tab. You can select an existing template from the Threshold Templates drop-down menu or provide the threshold values. For more details on Traffic health monitoring and how to create threshold template, refer to
You can view the configuration health status and the traffic health status of the application in the HEALTH STATUS tab. For more details on configuration health and traffic health, refer to
You can view the statistics of the application in the STATISTICS tab.



