Masking
Masking lets you overwrite specific packet fields with a specified pattern so that sensitive information is protected during network analysis. Masking operations consist of an offset, length, and pattern.
To add a Masking application:
- Drag and drop Masking from APPLICATIONS to the graphical workspace.
- Click the Masking application and select Details. The Application quick view appears.
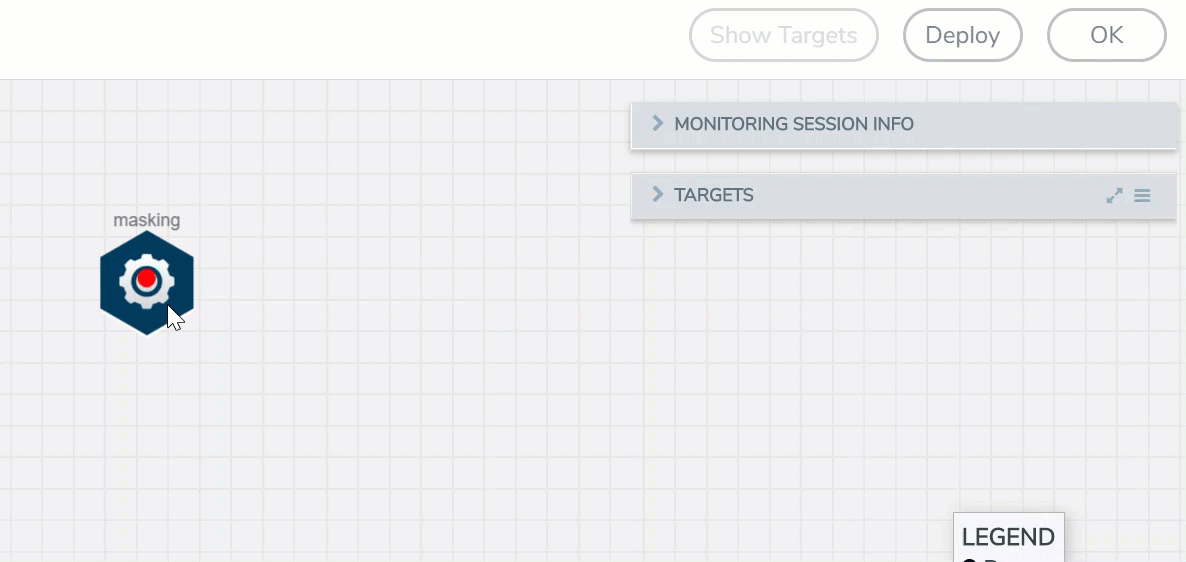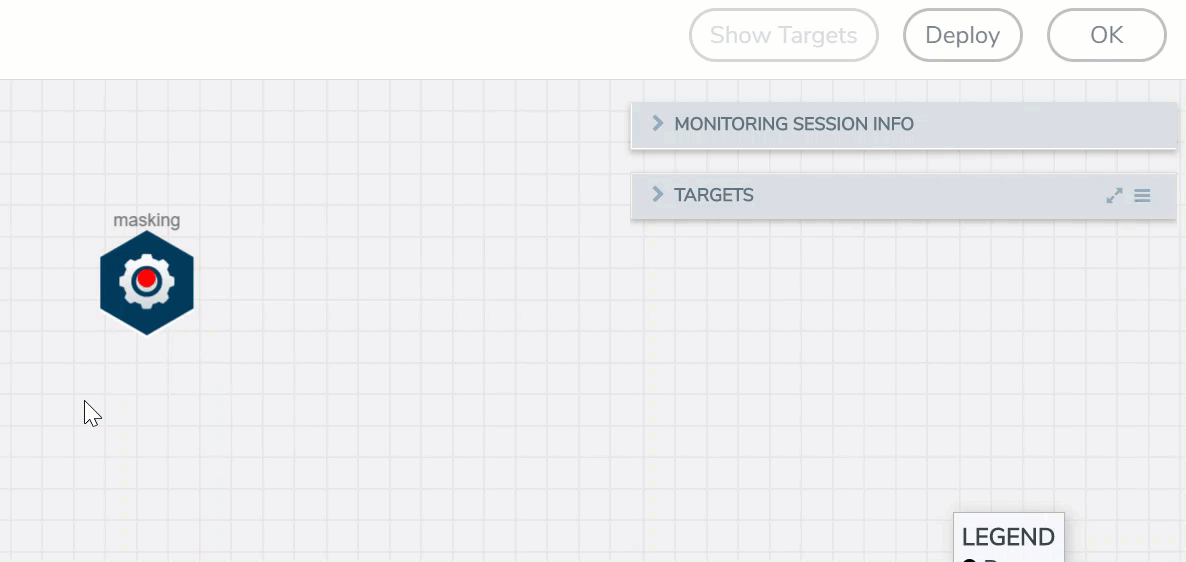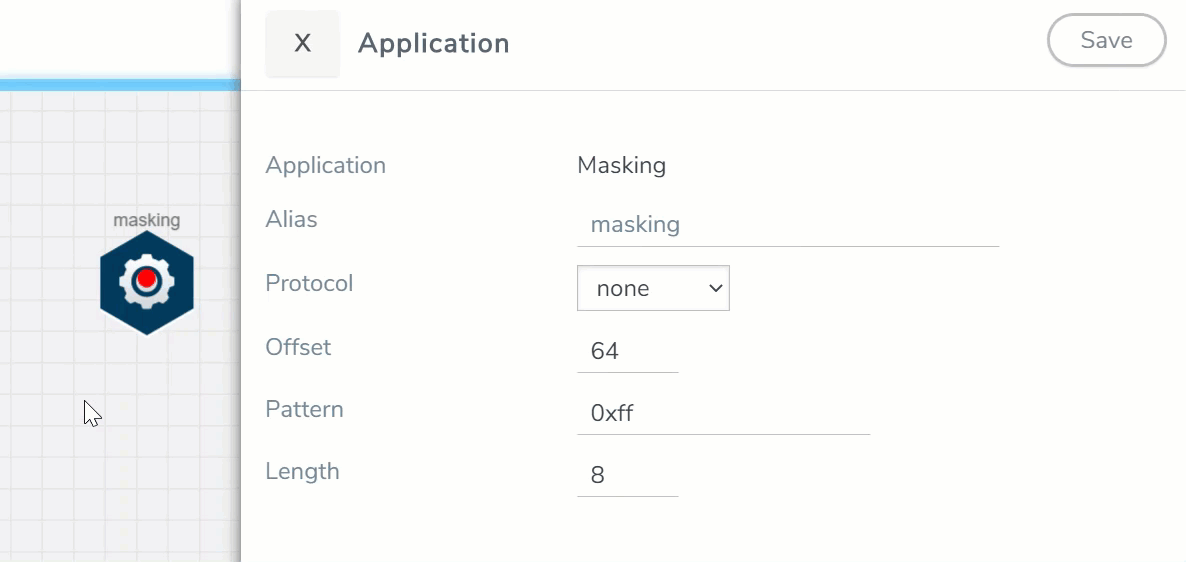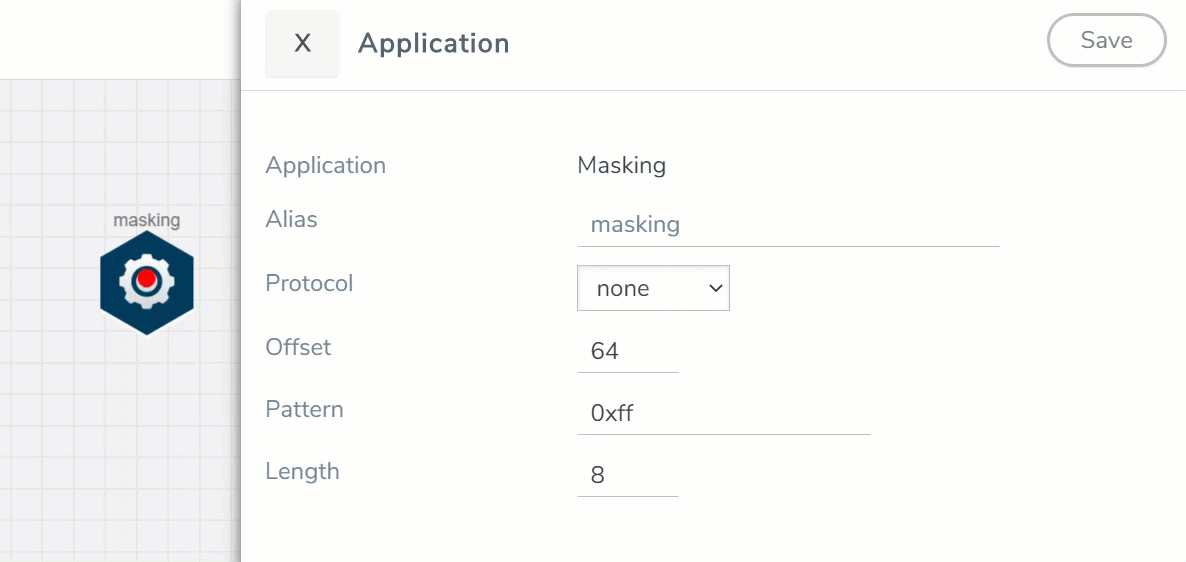
- In the Application quick view, enter the information as follows:
Component
Description
Alias
Enter a name for the application.
Protocol
The following are the protocols that you can select from the protocol drop-down list:
o None – Mask starting a specified number of bytes from the start of the packet. o IPV4 – Mask starting a specified number of bytes after the IPv4 header. o IPV6 – Mask starting a specified number of bytes after the IPv6 header. o UDP – Mask starting a specified number of bytes after the UDP header. o TCP – Mask starting a specified number of bytes after the TCP header. o ftp-data– Identify using TCP port 20. Mask payloads using offset from the TCP header. o HTTPS – Identify using TCP port 443. Mask payloads using offset from the TCP header. o SSH – Identify using TCP port 22. Mask payloads using offset from the TCP header. o GTP – Mask starting a specified number of bytes after the outer GTP header. o GTP-IPV4 – Mask starting a specified number of bytes after the IPv4 header inside the encapsulating GTP packet. o GTP-UDP – Mask starting a specified number of bytes after the UDP header inside the encapsulating GTP packet. o GTP-TCP – Mask starting a specified number of bytes after the TCP header inside the encapsulating GTP packet. Offset
Specifies where the application should start masking data with the supplied pattern. You can specify this in terms of either a static offset from the start of the packet or a relative offset from a particular protocol layer. This lets you automatically compensate for variable length headers, specifying a mask target in terms of a particular packet header.
Length
Specifies how much of the packet should be masked. The specified one-byte pattern can be repeated to mask from 1-9600 bytes.
Pattern
Specifies what pattern the application should use to mask the specified portion of the packet. You can specify a one-byte hex pattern (for example, 0xFF).
- Click Save.
Masking application is successfully configured.
What's Next
You can configure the traffic health monitoring for this application in the THRESHOLDS tab. You can select an existing template from the Threshold Templates drop-down menu or provide the threshold values. For more details on Traffic health monitoring and how to create threshold template, refer to
You can view the configuration health status and the traffic health status of the application in the HEALTH STATUS tab. For more details on configuration health and traffic health, refer to
You can view the statistics of the application in the STATISTICS tab.



