Check for Required IAM Permissions
GigaVUE‑FM allows you to validate whether policy attached to the FM using "EC2 Instance Role" or "Access Credential" has the required IAM permissions and notifies the users about the missing permissions.
The following are the pre-requisite that are required to deploy GigaVUE Cloud Suite. You can validate them by clicking the Check Permissions button on the Create Monitoring Domain page and Create Fabric Launch page. The GigaVUE‑FM displays the minimum required IAM permissions.
-
IAM permissions - Checks whether the minimum required permissions are granted for the instance where the GigaVUE‑FM is deployed.
-
Access to public cloud end points - Checks for access to the AWS cloud end point APIs.
-
Subscription to the Gigamon Cloud Suite - Before deploying the solution, you must subscribe to the GigaVUE Cloud Suite components from the AWS marketplace. It checks whether the required components are subscribed in the marketplace.
-
Security group rules - Checks whether the required ports are configured in the security group. For more information on the security groups, see Security Group
Note: Security group rules validation does not validate prefix List and user groups. For a successful validation, the ports and CIDR range should be updated in the Security Group.
After you press the Check Permissions button, GigaVUE‑FM will verify the minimum required permissions. Any missing permissions will be highlighted in a dialog box. You can use the the displayed IAM Policy JSON as a reference and update the policy that is attached to the GigaVUE‑FM.
You can view the permission status reports from Settings--> View Permissions. The reports are purged once in every 30 days.
You can check permissions while configuring the following :
- Monitoring Domain
- GigaVUE Fabric components in GigaVUE‑FM
- VPC Mirroring
Check Permissions while configuring a Monitoring Domain
To check the permissions while creating a monitoring domain, do the following:
-
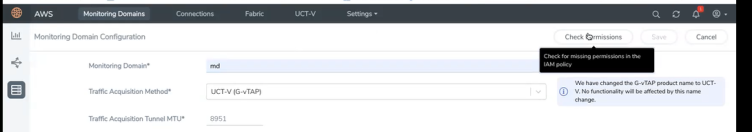
On the Create Monitoring Domain page, click Check Permissions
-
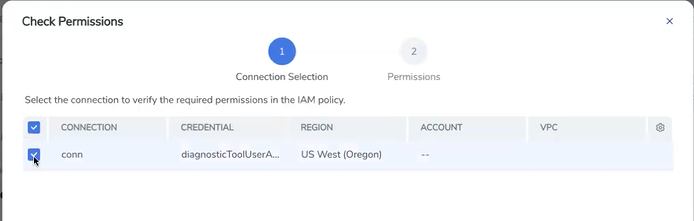
Select the connection and then click Next.
-
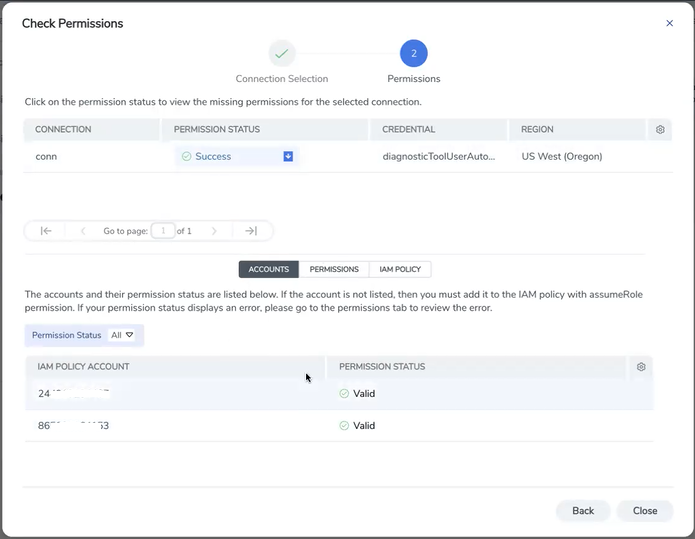
The accounts and the permissions status are listed under Accounts tab. Review the accounts that has an error in the permission status.
-
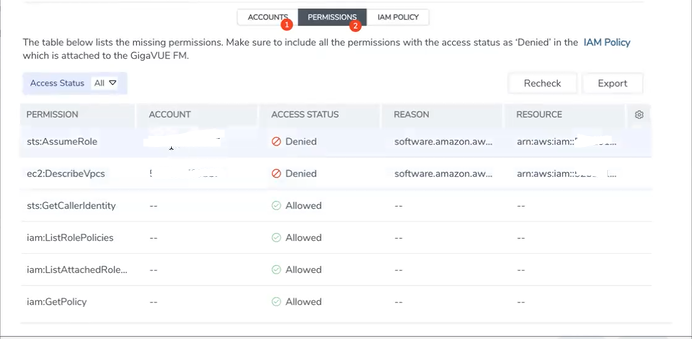
The permissions tab lists the permissions required to run GigaVUE Cloud Suite. Make sure to include all these permissions in the IAM policy with Access Status as 'Denied'.
-
The IAM policy tab lists the sample policy containing the required permissions for deploying the GigaVUE Cloud Suite. You must update the AWS IAM policy with the missing permissions that are highlighted in the JSON. To recheck the IAM policy, go to the Permissions tab and click the Recheck button.
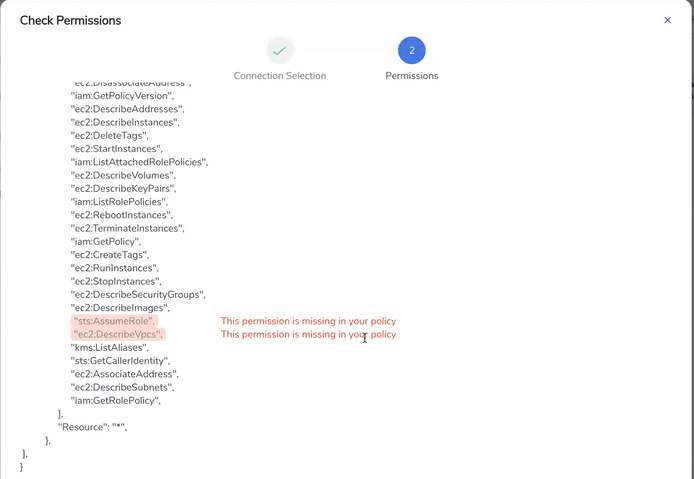
When you click Copy or Download, the entire JSON will be copied or downloaded.
Note: After updating the IAM Policy, it takes around 5 minutes for the changes to reflect on the Check Permissions screen.
Check Permissions while configuring GigaVUE Fabric components in GigaVUE‑FM
To check for permissions from the AWS Fabric Launch page, do the following:
- In the AWS Fabric Launch page, click Check Permissions
- The permission status for Inventory, Security Group and Fabric Launch is displayed.
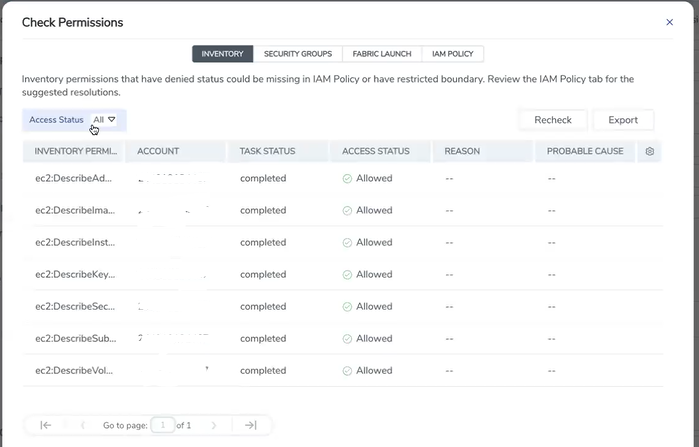
Note: Populating permissions status for Fabric launch takes a longer duration.
Check Permissions to acquire traffic using VPC mirroring
To check permissions to acquire traffic using VPC mirroring, navigate to the Monitoring Domain page, select the Monitoring Domain, click Actions, and then click Check Permissions.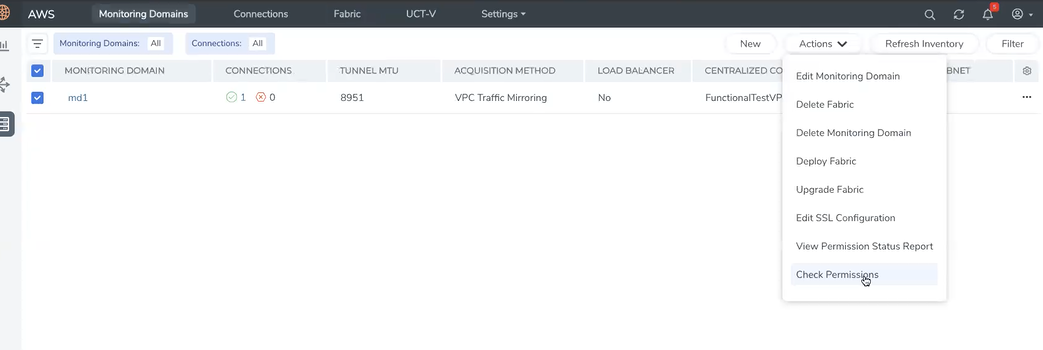
View permission status reports
Permission status reports consists previously ran Check permissions reports. They are auto purged once in 30 days. You can change the purge interval from the advanced settings page.
To view the reports, click Actions and then click View Permission Status Report.
Alternatively, you can navigate to Settings and then click View Permission Status Report