SSH
The SSH configuration page allows you to exclude less secure SSH cryptographic options, enabling you to configure only the most secure or preferred cryptographic settings. This provides greater control over the system's security. This page allows you to configure ciphers, key exchange algorithms (Kex), Message Authentication Codes (MACs), and HostKey algorithms for both the SSH client and server.
Configure SSH options
To configure SSH options:
-
On the left navigation pane, click
 and select System> SSH. The SSH page appears.
and select System> SSH. The SSH page appears. 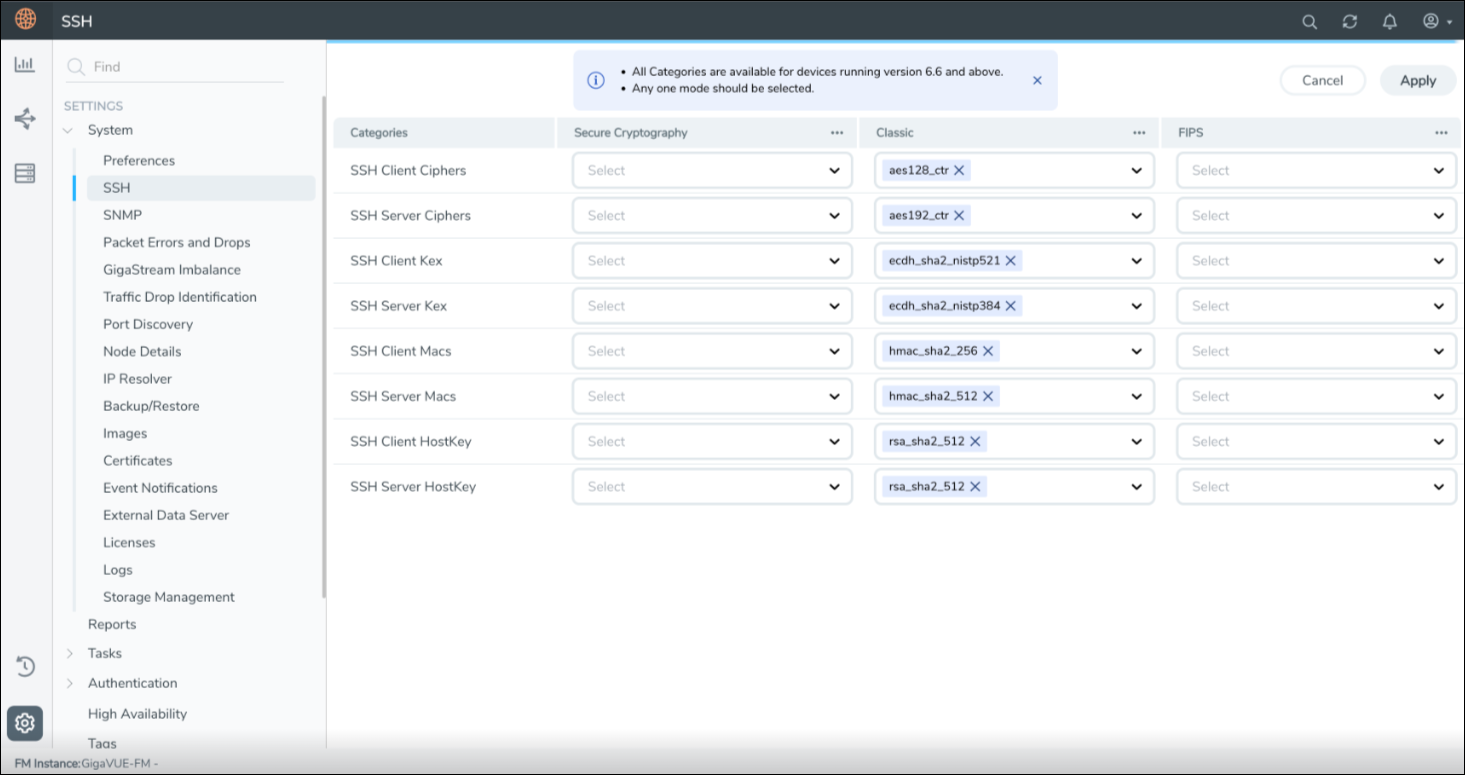
- Click the ellipses next to the secure cryptography, classic, and FIPS fields. Select Select All, De-select All, and Set as Default as required.
- Click Select All to select the supported values in the fields.
- Click De-select All to remove the selected values in the fields. If values are not assigned to the fields, default values are automatically updated in the fields.
- Click Set as Default to set the pre-defined values in the fields.
- Select the following details:
Field Description SSH Client Ciphers Select the ciphers to be used by the ssh client in the machine.
The following ciphers are allowed in the secure cryptography field:
aes128-cbc
aes128-gcm@openssh.com
aes256-cbc
aes256-gcm@openssh.com
The following ciphers are allowed in the classic field:
aes128-cbc *
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-cbc*
aes256-ctr
aes256-gcm@openssh.com
The following ciphers are allowed in the FIPS field:
aes128-cbc
aes128-gcm@openssh.com
aes256-cbc
aes256-gcm@openssh.com
SSH Server Ciphers Select the ciphers to be used by the ssh server in the machine.
The following ciphers are allowed in the secure cryptography field:
aes128-cbc
aes128-gcm@openssh.com
aes256-cbc
aes256-gcm@openssh.com
The following ciphers are allowed in the classic field:
aes128-cbc *
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-cbc*
aes256-ctr
aes256-gcm@openssh.com
The following ciphers are allowed in the FIPS field:
aes128-cbc
aes128-gcm@openssh.com
aes256-cbc
aes256-gcm@openssh.com
SSH Client Kex Select the kex to be used by the ssh client in the machine.
The following kex are allowed in the secure cryptography field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
The following kex are allowed in the classic field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
diffie-hellman-group14-sha256
The following kex are allowed in the FIPS field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
SSH Server Kex Select the kex to be used by the ssh server in the machine.
The following kex are allowed in the secure cryptography field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
The following kex are allowed in the classic field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
diffie-hellman-group14-sha256
The following kex are allowed in the FIPS field:
ecdh-sha2-nistp256
ecdh-sha2-nistp384
ecdh-sha2-nistp521
SSH Client Macs Select the macs to be used by the ssh client in the machine.
The following macs are allowed in the secure cryptography, classic, and FIPS field:
hmac-sha2-512
hmac-sha2-256
SSH Server Macs Select the macs to be used by the ssh server in the machine.
The following macs are allowed in the secure cryptography, classic, and FIPS field:
hmac-sha2-512
hmac-sha2-256
SSH Client Hostkey Select the hostkey to be used by the ssh client in the machine.
The following hostkeys are allowed in the secure cryptography field:
ecdsa-sha2-nistp256
ecdsa-sha2-nistp384
ecdsa-sha2-nistp521
The following hostkeys are allowed in the classic field:
ecdsa-sha2-nistp256
ecdsa-sha2-nistp384
ecdsa-sha2-nistp521
rsa-sha2-512
rsa-sha2-256
The following hostkeys are allowed in the FIPS field:
ecdsa-sha2-nistp256
ecdsa-sha2-nistp384
ecdsa-sha2-nistp521
SSH Server Hostkey Select the hostkey to be used by the ssh server in the machine.
The following hostkey is allowed in the secure cryptography field:
ecdsa-sha2-nistp384
The following hostkeys are allowed in the classic field:
rsa-sha2-512
rsa-sha2-256
The following hostkey is allowed in the FIPS field:
ecdsa-sha2-nistp384
- Click Apply to update the selected configurations.
View SSH options
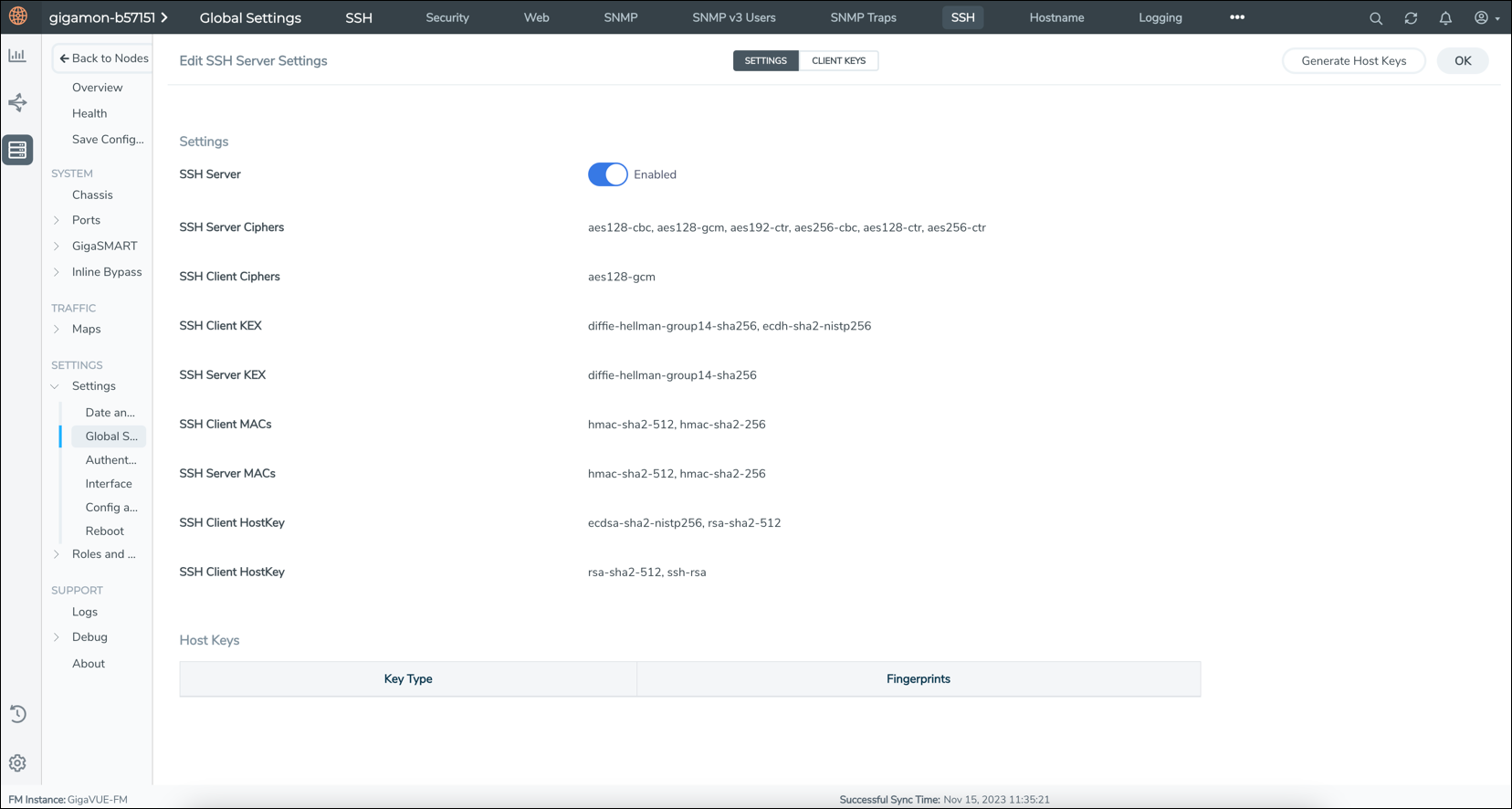
Once the SSH management configurations are updated, you can view the applied configurations on the global settings page.
- On the left navigation pane, click on
 select Nodes.
select Nodes. - In the Physical Nodes page, select the node for which you want to view the SSH configurations.
- Go to Settings > Global Settings > SSH.
- The selected ciphers, kex, macs, and hostkey algorithms for SSH client and server are listed on the settings page.
Note: For any settings or configurations outside the purview of GigaVUE‑FM, please reach out to Gigamon Support at support@gigamon.com. You can also refer to https://www.gigamon.com/support-and-services/contact-support for Technical Support hours and contact information.



