Packet Flows
Normally, a client and server talk directly to each other, such as when you are using a browser to go to a bank website, a health care provider, or a search engine.
As shown in 2, the GigaVUE node is placed in the middle between the client and the server. All traffic from the Internet goes through the GigaVUE node.
Incoming traffic arrives on an ingress inline network port on the inline bypass module.
SSL traffic, which is TCP traffic, is directed to the GigaSMART module. Until the traffic is processed by the GigaSMART module, it is not known if it is SSL traffic or not.
The GigaSMART module decides what traffic is bypassed, what traffic is sent to tools without decryption, and what traffic is decrypted and then sent to tools. So, there are three types of decisions as follows:
| to bypass or not |
| to decrypt or not |
| to send to tools or not |
1 shows the flow for a configuration consisting of a single inline network, a single inline tool, and a single out-of-band tool.
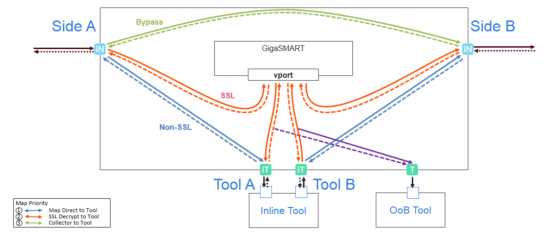
| 1 | Packet Flow for Inline SSL Decryption |
Traffic enters the inline SSL decryption solution at the side A inline network port on the inline bypass module.
Some traffic can be bypassed. That traffic goes from the side A inline network port to the side B inline network port on the inline bypass module as shown in the solid green line in 1. Bidirectional traffic is shown by dotted lines.
Traffic that is not encrypted (non-SSL) can be sent to tools for inspection. That traffic goes from the side A inline network port to the inline tool A port, to the inline tool, and from the inline tool to the inline tool B port and the side B inline network port on the inline bypass module without going through the GigaSMART module as shown in the solid blue lines in 1.
Traffic that is encrypted (SSL) goes from the side A inline network port on the inline bypass module to the GigaSMART module. That traffic goes to a virtual port (vport) that directs traffic to an inline SSL GigaSMART operation as shown by the red line on the left in 1. The traffic is decrypted in the GigaSMART module based on policy configuration, sent to the inline tool A port to the inline tool and from the inline tool to the inline tool B port, then back to the GigaSMART module for re-encryption as shown in the solid red lines in the center of 1. Finally, the re-encrypted traffic is sent from the GigaSMART module to the side B inline network port on the inline bypass module as shown by the red line on the right in 1.
The out-of-band tool can also receive the traffic as shown by the purple line on the right in 1.
Starting in software version 5.2, an out-of-band map from a virtual port to a single tool port is supported. Starting in software version 5.3.01, an out-of-band map from a virtual port to multiple tool ports is supported. The ports can be tool, hybrid, or GigaStream. Out-of-band maps from a vport to port groups are also supported when the ports in the group are tool or hybrid.
Modules Matrix
For traffic that is encrypted, there is a question as to whether or not it needs to be decrypted. For example, is there a policy for or against decrypting that traffic? There might be a policy, such as do not decrypt financial or health care traffic, or there might be a decrypt list that states that traffic from a particular site should always be decrypted, or there might be a no-decrypt list that states that traffic from a particular site should always be bypassed. So encrypted packets need to be filtered because some packets will not be decrypted, while others will be decrypted.
Table 2: GigaVUE Modules Used for Type of Traffic is a matrix of the GigaVUE module used for different types of traffic.
|
Type of Traffic |
GigaSMART |
Inline Bypass |
GigaSMART |
|
Bypassing GigaSMART |
No |
Yes - to network |
No |
|
Not encrypted (non-SSL) |
Yes |
Yes - to tools then to network |
Yes, depending on the configuration |
|
Encrypted (SSL), and to be decrypted |
Yes |
Yes - to tools |
Yes - to be re-encrypted, then to network |
The GigaSMART module does the decryption as well as handling policies, no-decrypt lists, and decrypt lists. The decision to decrypt or not is made in the GigaSMART module.



