Configure External IdP in GigaVUE‑FM
To configure external IdP (Active Directory Federation Services (ADFS)/Okta/Microsoft Azure) in GigaVUE‑FM:
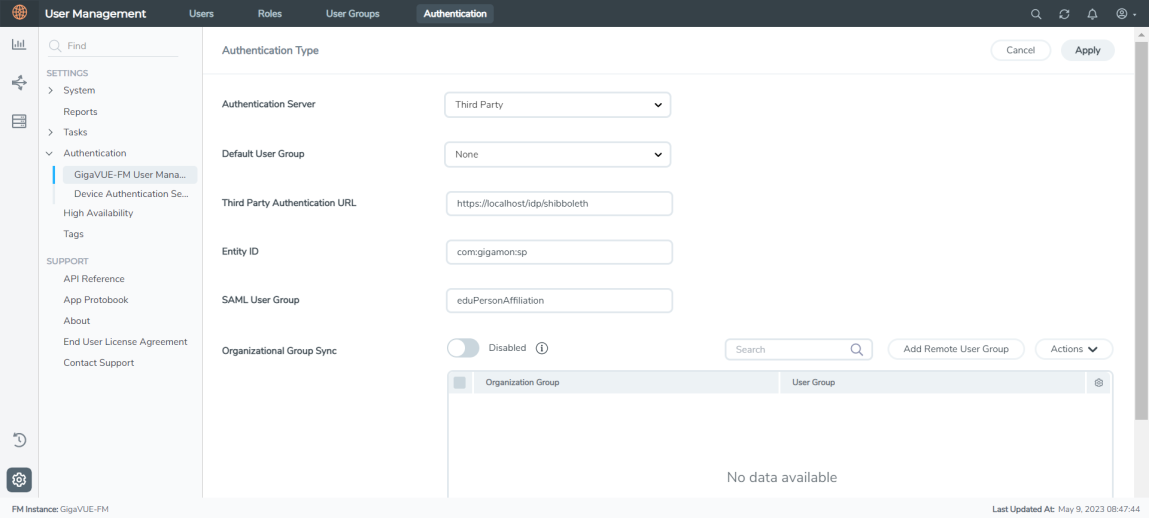
- Select Authentication > Authentication Types.
- Select Authentication Server as Third Party.
- Enter the following details and click Apply.
|
Field |
Description |
|---|---|
|
Third Party Authentication URL |
Third party authentication URL. When you launch the URL in a browser, it must be a proper xml file. Example: For ADFS: https://<<ADFS_HOSTNAME>>/FederationMetadata/2007-06/FederationMetadata.xml |
|
Entity ID |
Service provider's entity ID (GigaVUE‑FM). Fetch the Service Provider metadata (which is GigaVUE‑FM’s metadata) from https://<FM IP Address>/saml/metadata. |
|
SAML User Group |
SAML User Group. This is used for authorization. The SAML User Group name entered here must match the SAML User Group configured in external IdP. |
|
Default User Group |
Default User Group |
|
Organizational Group Sync |
Map the GigaVUE‑FM group to the corresponding organizational groups in ADFS/OKTA/Microsoft Azure. |
You must add the IdP signing certificate into the GigaVUE‑FM Trust Store (Administration > System > Trust Store).
Note: It is not required to enable Trust Store Node Certificate based authentication access.
You must restart GigaVUE‑FM for the above configuration to be implemented.



