Traffic Drop Identification
GigaVUE-FM periodically collects statistical data of the physical and logical resources from the devices. The Traffic Drop Identification feature utilizes the historical statistical data to identify any significant traffic drop in the components. For software version 6.1.00, the traffic drop at the decapsulation side of the tunnel can be identified.
To enable this feature, you must define Alert Policies based on which alarms get triggered if there is a significant throughput change in traffic volume. An alert policy binds the resources such as a tunnel and the required conditions to identify the drop in traffic volume. Refer to the How Alert Policies Work for details.
How Alert Policies Work
An alert policy consists of the following sections:
- Overview: Name and description of the alert policy.
- Monitoring Resources: Resource such as Tunnels (for software version 6.1.00).
- Threshold Conditions: Criteria for detecting the traffic drop.
- Clear Condition: Conditions based on which alarms will be cleared.
The Alert Policies work based on the threshold conditions that define the criteria for creating the alarm. It consists of the time duration to average the metrics, drop threshold percentage, and severity of the alarm.
When the computed traffic drop value exceeds the configured threshold value, an alarm is triggered with the configured severity. Alarm gets cleared based on the clear condition defined.
Alert policy supports both single threshold and multiple thresholds configuration. In multiple threshold configuration, up to three levels of drop thresholds and associated severity can be configured. Consider an alert policy that is configured with multiple threshold values such as:
- Minor - 2%
- Major - 5%
- Critical - 8%
GigaVUE-FM calculates the threshold value at periodic intervals:
| Intervals | Calculated Drop % | Alarms Severity |
|---|---|---|
| 1 |
Computed drop is 4% Exceeds the 2% configured value for severity state Minor and is lower than the 5% configured value for severity state Major |
An alarm with severity 'Minor' is triggered. |
| 2 |
Drop further increases to 7% exceeds the 5% configured value for severity state Major and is lower than 8% configured for severity state Critical |
Alarm is updated with severity as 'Major' |
| 3 | Drop goes beyond 8%. | Alarm is updated with severity as 'Critical' |
| 4 | Drop is identified as 4% | Alarm severity will not be lowered. Instead alarm will be cleared based on the clear criteria. |
Alarms get cleared based on the clear condition. The following options are provided:
- Time based: Alarms will be cleared after the configured time (10-30 minutes interval)
- Threshold based: Alarms will be cleared based on the following criteria:
- Threshold value: Denotes the threshold value to clear the alarm when the computed traffic drop value goes below this configured value
- Duration: Duration for how long the computed traffic drop should be maintained below the threshold value (10-30 minutes duration).
Therefore, the alarms do not get cleared immediately after the drop goes below the threshold value. It is ensured that the drop is consistently maintained below the threshold value for the given duration. Refer to the Configure Alert Policy section for the various fields required for creating the policy.
Tunnel Traffic Drop Identification
For tunnels, traffic drop is calculated based on the traffic sent over the tunnel versus the traffic received at the decapsulation side of the tunnel. That is, the average processed traffic is computed for configured duration for both encapsulation and decapsulation sides separately and the drop is computed used these two values.
GigaVUE-FM supports configuring various tunnel types and each tunnel type has its own source and destination components. The following table lists the components considered for computing the total traffic for the different tunnel types:
| Tunnel Type | Encapsulation side Component | Decapsulation Side Component |
|---|---|---|
| GigaSMART L2GRE | GSOP General Stats Rx Packets | GSOP General Stats Tx Packets |
| Embedded L2GRE | Encap Map Source Ports Rx Packets | Decap Map Rule Stats (Rules with L2GRE ID) |
| Embedded VxLAN | Encap Map Source Ports Rx Packets | Decap Map Rule Stats (Rules with VxLAN ID) |
| Circuit Tunnel | Encap Map Packets | Decap Map Rule Stats (Rules with Circuit ID) |
| Hybrid Tunnel (configured between V Series 2 nodes and physical nodes) | Egress TEP Tx Packets | Ingress TEP Rx Packets |
Note: The source and destination of the tunnels may reside in different clusters. As stats collection for the clusters happen at different time intervals, the encapsulation and decapsulation statistics may not always match exactly. Consider this while configuring the tunnel drop threshold in an Alert Policy for the tunnels.
Rules, Notes, and Limitations
Refer to the following rules, notes and limitation for traffic drop identification for the tunnels:
- For software version 6.1.00, traffic drop alert policies can be created only for tunnels discovered by GigaVUE-FM. Refer to Tunnel Monitoring section for details.
- For the tunnels discovered and listed in the Tunnel Monitoring page, Alert Policies can be configured only if the Tunnel Discovery State is 'Complete'.
- For Alert Policies with multiple alarms, severity can be configured only up to three levels.
- Traffic drop computation is not performed in the following scenarios:
- when any one or both of the participating nodes are unreachable.
- when the number of statistical points at the encapsulation and decapsulation side are not equal.
- Traffic drop identification will not work for tunnels with multiple sources and single destination with decap key 0. If monitoring is required for such tunnels, it is recommended to configure a higher drop threshold value. Alarms generated for these types of tunnels can be used as a starting point for troubleshooting exact problem.
- Traffic drop identification will not work if the traffic at the decapsulation side of the tunnel is very high than at the encapsulation side (that occurs due to any misconfiguration or any other symptoms).
- For embedded tunnels: Source post statistics is considered for computing the drop threshold value. Therefore, if an alert policy is configured for these tunnels and there is a packet drop on the encapsulation map and the packet drop value is exceeding the drop threshold, an alarm will be triggered.
-
Alert Policies are updated based on the state change of the tunnels:
- Consider an Alert Policy created for a tunnel. During the next config sync cycle, if the state of tunnel changes to incomplete, then traffic drop computation is suspended for the tunnel. Traffic drop computation resumes once the state changes to complete.
- Consider an Alert Policy with only one tunnel. If the tunnel is deleted then the Alert Policy also gets deleted. Deletion of Alert Policies is captured in the Events page.
- Consider an Alert Policy with more than one tunnel. If one of the tunnels is deleted, then the deleted tunnel is also removed from the policy. Update to the Alert Policies is captured in the Events page.
- If monitoring is disabled for a tunnel (in the Tunnels Monitoring page) and if there is an Alert Policy configured for the tunnel, the traffic drop computation is suspended. Traffic drop computation resumes once monitoring is enabled for the tunnel.
Configure Alert Policy
To configure Alert Policies:
-
On the left navigation pane, click
 and select System> Traffic Drop Identification. The Traffic Drop Identification page appears.
and select System> Traffic Drop Identification. The Traffic Drop Identification page appears. - Click New Policy.
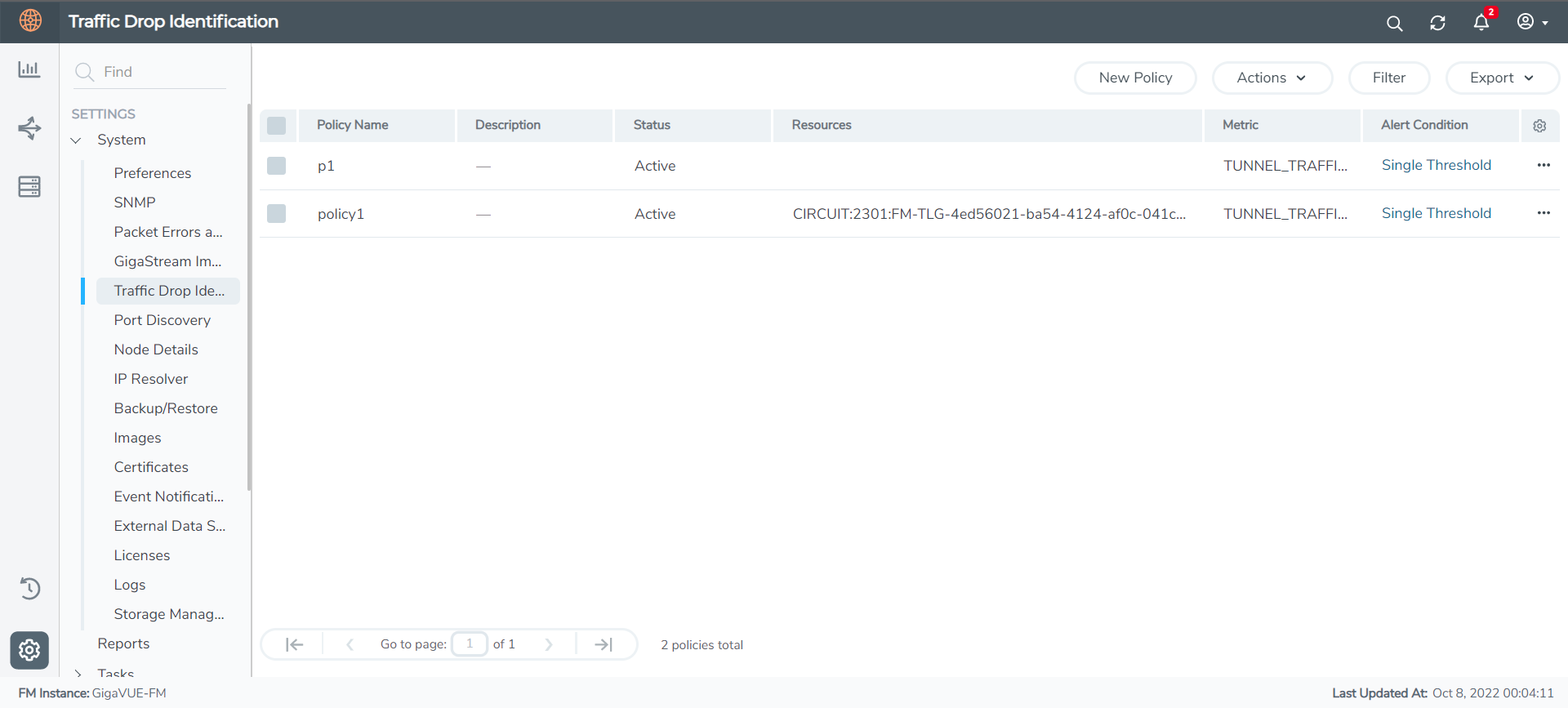
- Select or enter the following details:
Field Description Policy Name Name of the policy Description Detailed description about the policy Monitoring Resources - Metric Metric for the various resource types. For software version 6.1.00, Tunnel Traffic Monitoring is the only metric supported. - Resources List of tunnels identified in the Tunnel Monitoring page. Conditions - Alert Condition Alert condition. You can configure this as Single Threshold or Multiple Thresholds. - Average Duration Period during which the metric is to be monitored. - Threshold Threshold value in %. If you select Alert Condition as Multiple, you can configure up to three threshold values with varying severity levels. Clear Alarm Condition Clear Type You can clear the alerts based on:
- Time
- Threshold
Clear Alarm After If Clear Type is selected as Time, configure the Duration after which the alarm should be cleared. Clear alarm when traffic drop is maintained below If Clear Type is selected as Threshold, configure the threshold percentage for the required minutes. - Click Apply to apply the Alert Policy.
- The policy is added to the list view. The Alarm column lists the alarm count for each policy. Click on the alarms and you will be redirected to the Alarms page.
Once the Alert Policy is created with the required details, the policy is scheduled and runs periodically every 5 minutes to compute the traffic drop based on the conditions. If the traffic drop exceeds the configured threshold values for the specified duration, alarms are triggered.
Use the following buttons to manage the Alert Policies:
| Button | Description |
|---|---|
| New Policy |
Use to create a new Alert Policy |
| Actions |
Use the Actions drop-down button to perform the following tasks. You can select either a single policy or multiple policy, as required.
|
| Filter |
Use to filter the Alert Policies based on the policy name or the status of the Policy. |
| Export | Use to export the Alert Policies (either all or the selected Alert Policies) in CSV or XLSX format. |



