Hardware Security Modules (HSM)
A Hardware Security Module (HSM) is a dedicated, tamper-resistant device that protects cryptographic keys and performs secure key operations. In inline deployments, HSMs are used to safeguard the private keys required for TLS/SSL decryption. By offloading key storage and sensitive cryptographic tasks to an HSM, organizations ensure that decryption happens without exposing keys inside the node.
Why HSM
Most enterprise traffic today is encrypted, making TLS/SSL decryption a critical part of inline deployments. Security tools such as intrusion prevention systems (IPS) or data loss prevention (DLP) engines need decrypted traffic to analyze threats. Without an HSM, private keys must be stored directly on a Gigamon HC Series node or server, which creates risk.
With an HSM, the private keys remain inside a hardened device. The node communicates with the HSM using secure tokens, never exposing the raw keys. This means:
| Keys never leave the HSM, even if the node is compromised. |
| The node can request private key operations such as decryption without handling the key itself. |
| Only approved applications, such as GigaSMART® SSL/TLS decryption, can use the tokenized access. |
This makes the HSM a critical part of inline solutions where compliance, regulations, or strict security rules require hardware-grade key protection.
How HSM Solution Works
In Flexible Inline Arrangements, HSMs are supported through HSM Groups. An HSM Group represents one or more hardware modules connected to a node. Supported HSM devices include:
| Entrust nShield HSMs |
| Thales Luna Network HSMs |
Each group is tied to a single vendor type; mixing vendors in the same group is not allowed. Thales Luna clustering is not supported, and IPv6 connectivity is not available. Nodes must be configured with static IPv4 addresses to communicate with HSMs.
When an HSM is in place, the node offloads TLS/SSL decryption key handling. For example, in an Inline SSL Decryption workflow, traffic passes through GigaSMART, which queries the HSM for key use. The HSM processes the request securely and returns only a tokenized response. The private key never leaves the HSM.
The following images illustrates the process flow of HSM solution.
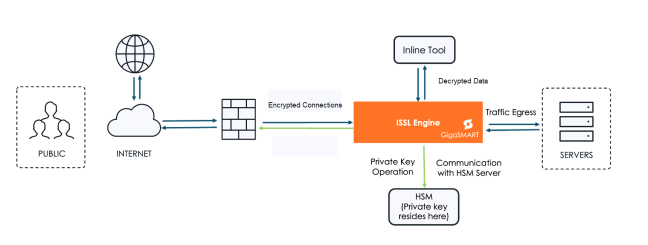
GigaSMART applications that commonly leverage HSMs include:
| SSL/TLS decryption for inline traffic inspection. |
| Passive SSL/TLS Decryption |
Note: Classic Inline Bypass does not support HSM integration. Classic deployments provide resiliency through protected inline networks, tool groups, and failover actions, but they do not include any mechanism for hardware-based key storage or integration with external HSM appliances.
HSM - Supported Platforms
HSM Group is supported in the following platforms:
| GigaVUE-HC1 Gen3 |
| GigaVUE-HC3 Gen3 |
| GigaVUE‑HC1-Plus |



