Introduction to Inline TLS/SSL Map Workflows
In GigaVUE‑FM, workflows guide you through configuration steps. For the Inline TLS/SSL Map configuration, there are seven flows, Flow A to Flow G based on which you can perform different configurations.
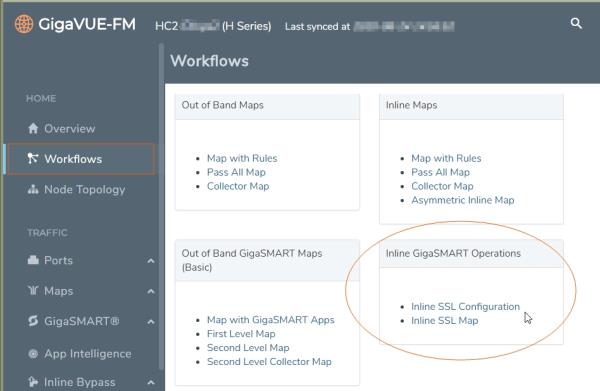
Go to Workflows and select Inline SSL Map from the Inline GigaSMART Operations section as shown in 1 Select Inline TLS/SSL Map Configuration.
|
1
|
Select Inline TLS/SSL Map Configuration |
Flow A to Flow G are displayed as shown in 2 Flow A to Flow G.

The following sections describe each flow:
Flow A
Flow A is for the following use case:
|
■
|
filter HTTP traffic and direct it to the tool(s) |
|
■
|
filter remaining TCP traffic and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
direct all other traffic to the tool(s) |
Refer to 3 FLOW A Views for a larger view of Flow A on the left and a pictorial view on the right.
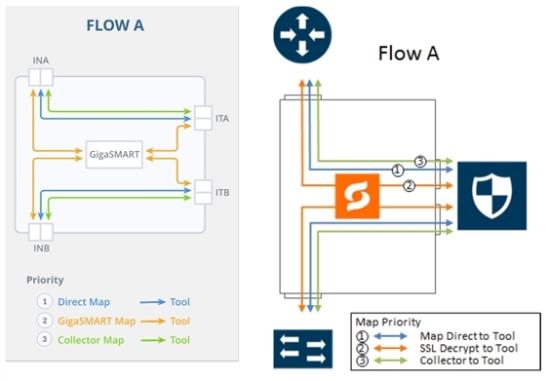
The map priorities of Flow A are as follows:
|
1.
|
limit traffic going to decryption |
|
2.
|
selectively forward traffic for decryption |
|
3.
|
direct unselected traffic to a collector, which sends traffic to tool |
Flow B
Flow B is for the following use case:
|
■
|
filter HTTP traffic and direct it to the tool(s) |
|
■
|
filter remaining TCP traffic and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
bypass all other traffic |
Refer to 4 FLOW B Views for a larger view of Flow B on the left and a pictorial view on the right.
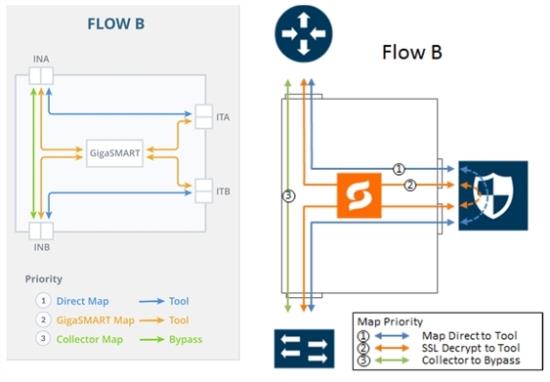
The map priorities of Flow B are as follows:
|
1.
|
limit traffic going to decryption |
|
2.
|
selectively forward traffic for decryption |
|
3.
|
direct unselected traffic to a collector, which sends traffic to bypass |
Flow C
Flow C is for the following use case:
|
■
|
filter traffic from or to certain VLANs (for example, a guest WiFi VLAN) and direct it to bypass |
|
■
|
filter remaining TCP traffic and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
direct all other traffic to the tool(s) |
Refer to 5 FLOW C Views for a larger view of Flow C on the left and a pictorial view on the right.
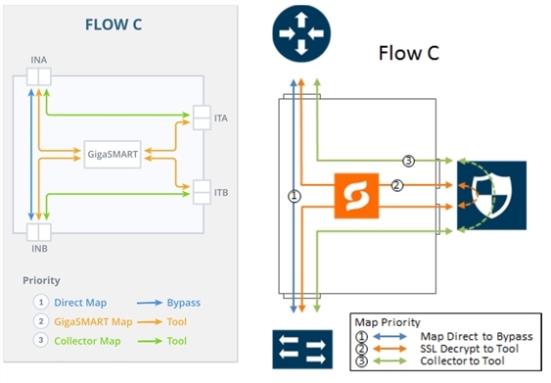
The map priorities of Flow C are as follows:
|
1.
|
send trusted traffic to bypass |
|
2.
|
selectively forward traffic for decryption |
|
3.
|
direct unselected traffic to a collector, which sends traffic to tool |
Flow D
Flow D is for the following use case:
|
■
|
filter traffic from certain VLANs (for example, an employee WiFi VLAN) and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
filter traffic from or to selected internal servers and direct it to bypass |
|
■
|
direct all other traffic to tool(s) |
Refer to 6 FLOW D Views for a larger view of Flow D on the left and a pictorial view on the right.
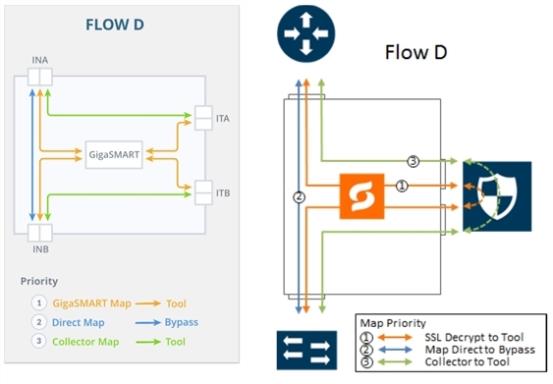
The map priorities of Flow D are as follows:
|
1.
|
selectively forward traffic for decryption |
|
2.
|
send trusted traffic to bypass |
|
3.
|
direct unselected traffic to a collector, which sends traffic to tool |
Flow E
Flow E is for the following use case:
|
■
|
filter traffic from certain VLANs (for example, an employee WiFi VLAN) and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
filter traffic from or to selected internal servers and direct it to the tool(s) |
|
■
|
bypass all other traffic |
Refer to 7 FLOW E Views for a larger view of Flow E on the left and a pictorial view on the right.
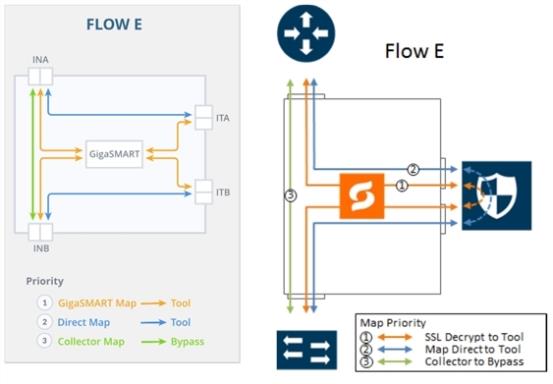
The map priorities of Flow E are as follows:
|
1.
|
selectively forward traffic for decryption |
|
2.
|
send remaining IP traffic to tool(s) |
|
3.
|
direct non-IP traffic to a collector, which sends traffic to bypass |
Flow F
Flow F is for the following use case:
|
■
|
filter TCP traffic and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
direct all other traffic to the tool(s) |
Refer to 8 FLOW F Views for a larger view of Flow F on the left and a pictorial view on the right.
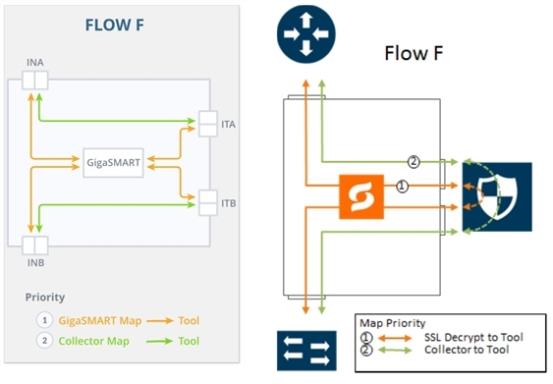
The map priorities of Flow F are as follows:
|
1.
|
selectively forward traffic for decryption |
|
2.
|
direct unselected traffic to a collector, which sends traffic to tool |
Flow G
Flow G is for the following use case:
|
■
|
filter TCP traffic and direct it to the GigaSMART engine for inspection before forwarding it to the tool(s) |
|
■
|
bypass all other traffic |
Refer to 9 FLOW G Views for a larger view of Flow G on the left and a pictorial view on the right.
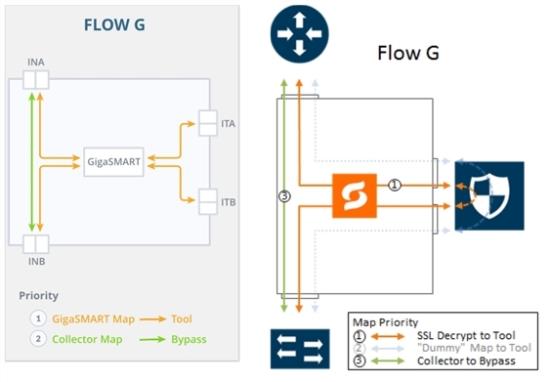
The map priorities of Flow G are as follows:
|
1.
|
selectively forward traffic for decryption |
|
2.
|
direct unselected traffic to a collector, which sends traffic to bypass |












