FIPS Compliance in GigaVUE-FM
GigaVUE-FM is compliant with the Federal Information Processing Standard (FIPS), a US government standard for security requirements of cryptographic modules. The FIPS module used in GigaVUE-FM is compliant with FIPS 140-3 and was validated by the National Institute of Standards and Technology (NIST). The certificate number is 4912. For more information, refer to Cryptographic Module Validation Program – Certificate 4912.
Refer to the following sections for details:
Refer to the following rules and notes for FIPS:
- After upgrading GigaVUE-FM instance from pre 5.16.00 to 5.16.00 or above, GigaVUE-FM boots in non-FIPS mode.
- FIPS is disabled by default in GigaVUE-FM. You can enable FIPS whenever needed. However, once enabled you cannot disable it.
- Only users with super admin privileges can enable FIPS.
Refer to the Frequently Asked Questions section for further details.
To configure FIPS in GigaVUE-FM:
| 1. |
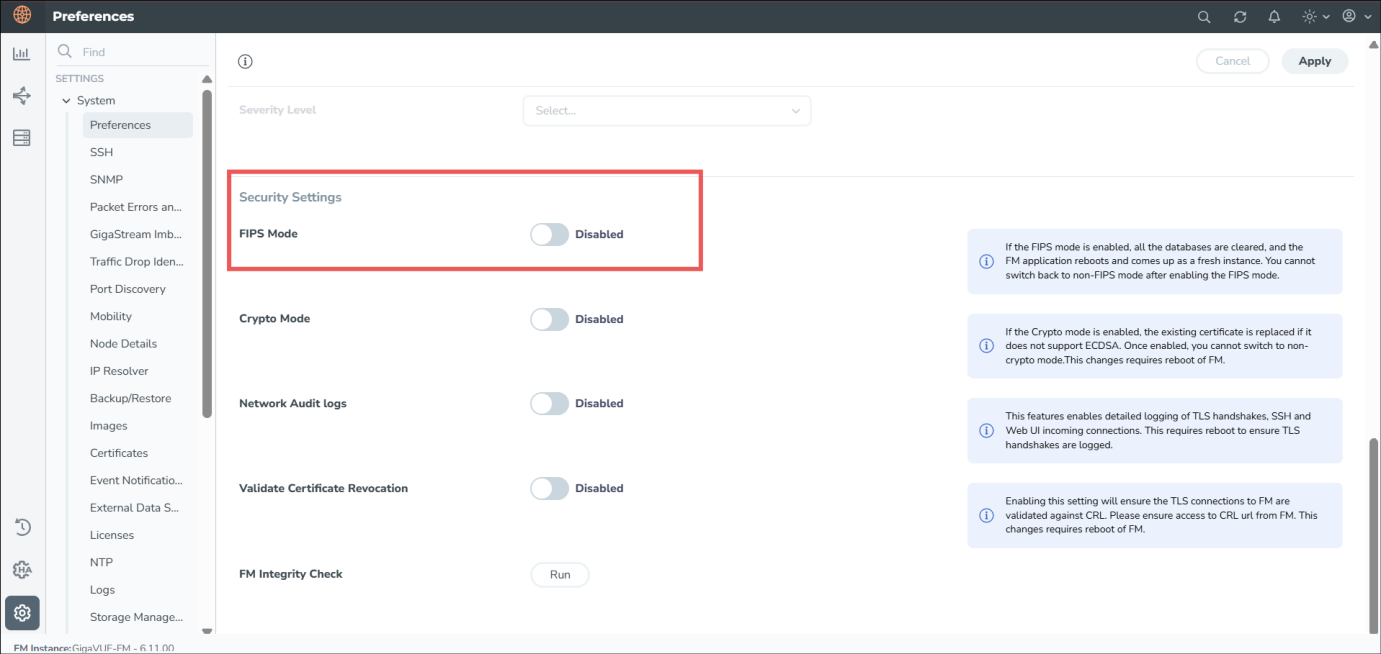
On the left navigation pane, click Settings |
| 2. | Under Security Settings, enable the FIPS Mode. |
| 3. | Click Apply to save the changes. |
| 4. | GigaVUE-FM will restart automatically after switching to FIPS Mode. Once the reboot completes, clear your browser cache and cookies to ensure the GigaVUE-FM IDP URL loads correctly. |
Note: Once enabled, the toggle button is disabled. You cannot switch back to non-FIPS mode.
To form a FIPS enabled High Availability (HA) group:
- Enable FIPS in each of the standalone GigaVUE-FM instances.
- Assemble the HA group with FIPS enabled standalone GigaVUE-FM instances.
Note: You cannot add a GigaVUE-FM instance that is not FIPS enabled to a FIPS enabled High Availability group. Similarly, you cannot add a FIPS-enabled GigaVUE-FM instance to a High Availability group that is not FIPS enabled.
Enabled TLS Cipher Suites
GigaVUE‑FM supports the commonly-supported TLS 1.2 and TLS 1.3 ciphers. The following ciphers are supported in TLS 1.2:
|
Cipher Name |
Key Exchange (Kx) | Authentication(Au) |
Encryption (Enc) |
MAC |
|---|---|---|---|---|
|
ECDHE-ECDSA-AES256-GCM-SHA384 |
ECDHE | ECDSA |
AES256-GCM |
SHA384 |
|
ECDHE-ECDSA-AES128-GCM-SHA256 |
ECDHE | ECDSA |
AES128-GCM |
SHA256 |
|
ECDHE-ECDSA-AES256-SHA384 |
ECDHE | ECDSA |
AES256 |
SHA384 |
|
ECDHE-ECDSA-AES128-SHA256 |
ECDHE | ECDSA |
AES128 |
SHA256 |
This page lists some of the most common issues and question related to FIPS.
Are all versions of GigaVUE-FM validated for FIPS compliance?
GigaVUE-FM versions 5.12.00.01 and 5.16.00 through 6.11 are compliant with FIPS 140-2. GigaVUE-FM version 6.11.01 and later are compliant with FIPS 140-3.
Can you enable FIPS using the fmctl command?
No. There is no support for enabling FIPS using the fmctl command. You can enable FIPS only using the GigaVUE-FM GUI.
Can you add a device that is not FIPS-compliant to a FIPS enabled GigaVUE-FM?
Yes. You can add a non FIPS compliant device to a FIPS enabled GigaVUE-FM.
What happens to the GigaVUE-FM database after you enable FIPS?
The GigaVUE-FM database is reset. GigaVUE-FM reboots and comes up as a new instance. You must reconfigure and setup GigaVUE-FM again.
How do I perform backup and restore operation on a FIPS enabled GigaVUE-FM?
A backup taken on a FIPS enabled GigaVUE-FM can only be restored on a GigaVUE-FM instance that is FIPS enabled. Similarly, backup taken on a non-FIPS GigaVUE-FM can be restored only on a non FIPS GigaVUE-FM.
Is the FIPS certification applicable for GigaVUE-FM instance irrespective of where it is deployed?
No. GigaVUE-FM Hardware appliance is only validated for FIPS certification.



