SSL Keys and Certificates
The SSL protocol allows the transmission of secure data between a server and client who both have the keys to decode the transmission and the certificates to verify trust between them.
An SSL certificate is a digital document containing a public key, host information, and a digital signature from the certificate issuer, known as a Certificate Authorities (CAs). The certificate allows trust to be established between two communicating endpoints.
The inline SSL decryption solution has a trust store, which is a collection of certificates of CAs. Gigamon only trusts server certificates that have a trust anchor in the configured trust store, in other words, if the certificate chain can be built with one of the root CAs in the trust store. Gigamon ships with a default trust store, which you can replace.
The inline SSL decryption solution acts as a Man-in-the-Middle (MitM). In the outbound deployment case, the MitM generates server certificates on-the-fly signed by the installed Signing CA. In the inbound deployment case, server certificate generation is not needed but the server's private key and certificate chain need to be made available to the MitM.
The inline SSL decryption solution also has a key store, which is a collection of SSL private keys (for inbound deployments) and SSL certificates and corresponding private keys that are used to digitally sign the emulated server certificates (for outbound deployments).
1 shows a sample certificate and its relevant parts.
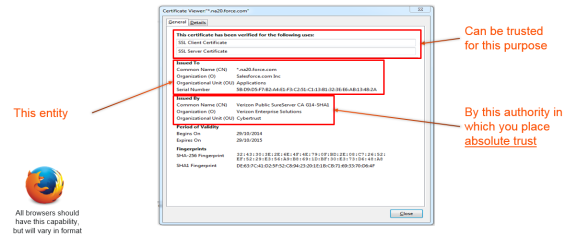
| 1 | Sample Certificate |
The key store contains keys and certificate-key pairs. The key store can contain a maximum of 1000 key pairs.
A particular key in the key store can be selected only for decryption (inbound deployment) or for re-signing and decryption (outbound deployment).
Starting in software version 5.2, encrypted or password protected PEM is supported for fetching or downloading a private key.
Starting in software version 5.6.00, ECDSA keys are supported for both inbound and outbound deployments.
A Key Store certificate can be setup to be auto- enabled, auto-deleted and auto-retained to an inline-SSL profile. The configuration can be done as follows:
-
On the left navigation pane, click
 , and then select Physical > Nodes
, and then select Physical > Nodes -
In the Physical Nodes page, select the node for which you want to configure Key Store settings.
-
Go to GigaSMART>Inline SSL >Key Store .
-
Click Settings.Configure the following settings:
| Auto Enable New Certificates – Associates new certificates to an inline-SSL profile, if the new certificate shares a common name with an existing certificate(s) of the inline-SSL profile. The setting will be triggered as and when a new certificate is uploaded or pushed by a third-party tool. |
| Auto Delete Expired Certificates – Deletes expired certificates automatically. This setting will be triggered once a day at 12:00:00 UTC. Specify the number of days to retain an expired certificate in the Number of days to retain expired certificates field. The default value would be 30 days. |
| Auto Delete Certificates with same entity – Deletes expired certificates with similar name associated to an inline-SSL profile. Once the setting is updated; the oldest certificate will be deleted as and when the maximum number of allowed certificates are crossed. Specify the maximum number of days to retain an expired certificate with same entity in the Max number of Certificates to retain for the same Entity field. |
To generate and add an inline-SSL signing certificate to key store for outbound deployment, perform the following steps:
| 1. | Create an internal root CA (for example, using Microsoft AD, or OpenSSL, or any other CA implementation). |
| 2. | Push this CA root certificate to all devices. |
| 3. | Issue a sub-CA certificate for Gigamon. |
| 4. | Upload the sub-CA certificate to Gigamon with the private key of only the sub-CA. |
The key store certificates added would be displayed in Key Store page.
To access the Key Store page:
-
On the left navigation pane, click
 , and then select Physical > Nodes
, and then select Physical > Nodes -
Select the node for which you want to view the key store certificate information.
-
From the left navigation pane, go to System > GigaSMART > Inline SSL > Key Store. The details about the key store certificates added for the selected node is displayed.
The following table describes the fields:
|
Component |
Description |
||||||
|---|---|---|---|---|---|---|---|
|
Key Alias |
The alias name of the Key certificate. | ||||||
|
Type |
Defines whether the Key Store is a Certificate or a Private Key . |
||||||
|
Common name |
A common name given to group the key based on domain. |
||||||
|
Health Status |
The health indicator of a certificate used in traffic flow. The three major indicators with their respective color legend are as follows: Green Blue Red |
||||||
|
Organization |
Organization name that provided the key . | ||||||
|
.Organization Unit |
Organization unit name that provided the key. | ||||||
|
Expiry Date |
Date on which the key certificate would get expired. |
||||||
|
Installed On |
Date on which the key certificate was installed. | ||||||
|
Description |
Description or additional information about the key certificate |
||||||
|
Status |
Status of the key certificate. The valid values are:
|
You can control the key store certificates display by utilizing the filters provided.
The trust store contains a trusted certificate authority (CA) for server validation. A default trust store from Mozilla is included with this GigaVUE‑OS software version. The trust store is updated periodically. You can also fetch a trust store file containing certificates in PEM format if you want to replace the default trust store.
Starting in software version 5.2, CA certificates can be appended to the trust store or specific certificates can be deleted from the trust store. Also, the trust store can be queried for a specific certificate by its fingerprint. The query includes the hex representation of the first four octets of the certificate’s SHA1 fingerprint.
Gigamon needs to validate the server certificate so that an incoming untrusted certificate is not made legal by Gigamon re-signing the certificate.
The certificate validation process includes several steps as follows:
| 1. | Certificate expiration date and validity period: The GigaVUE node compares the current date to the validity period listed in the certificate. If the expiration date has not passed and the current date is within the period, the certificate is good. |
| 2. | Certificate issued by trusted CA: The GigaVUE node maintains a list of trusted root CAs. This list determines the certificates that the client will accept. The trust store acts as a trust anchor during certificate validation. The GigaVUE node validates that each incoming certificate chain is trusted by one of the certificates in the trust store. |
| 3. | Server name: The GigaVUE node validates that the server certificate is valid for the hostname mentioned in the SNI. This validation is not performed if the client does not send SNI. |
| 4. | Certificate revocation check: The GigaVUE node validates the server certificate status using OCSP and CRL lists downloaded from the concerned CAs. Internet connectivity is required for this functionality. The certificate revocation check determines the revocation status of the server certificate. |
Certificates that pass the validation are accepted. The primary MitM CA signs the forged certificate. Certificates that fail validation can be accepted if security exceptions are configured and the secondary MitM CA signs the corresponding forged certificate. For self-signed certificates, the forged certificate will also be self-signed.
Client applications will typically add the primary MitM CA to their trust store and not to the secondary. This will act as a mechanism to bubble up certificate validation errors on the client applications and provide the end users an opportunity to reject the connection.
If there are certificate validation errors, the SSL connection is dropped unless explicitly permitted by the security exceptions in the policy profile. The certificate validation errors are grouped into the following four categories:
| Expired: The validity period of the certificate is in the past. |
| Self-signed: The certificate is self-signed, meaning that the subject and the issuer are the same. The validity period is current and the certificate signature is valid. |
| Unknown CA: The CA is not valid. The issuer certificate cannot be obtained from the certificate chain or is not in the trust store. You can download the root certificates for these sites and import them into the trust store if the certificate is valid and trusted. |
| Invalid: The certificate is not valid for the given SNI (for the Client Hello containing the SNI). There might have been a failure to decrypt or decode the certificate signature or the fields, not and before/not, were not read. |
For security exceptions for expired, unknown CA, and invalid certificates, the resulting certificate is signed (re-signed) by the secondary MitM CA, so the user can accept or reject the connection.
A server can challenge the client by requesting for a client certificate after the server responds with its Server Hello message. The client then respond with its certificate and the server validates the client certificate.
Gigamon does not support client authentication for outbound and inbound connections. If client authentication is detected during server handshake, then the connection is bypassed.
As a MitM, Gigamon re-signs certificates. The following fields are copied from the original certificate:
| subject name |
| certificate validity |
| subject alternative name |
The following fields are set in the removed list:
| authority Information Access |
| certificate Policies |
| CRL distribution points |
| SCT List |
The following fields are set in the re-signed certificate:
| certificate type—v3 |
| issuer |
| version |
| public key |
| serial number—randomly generated |
| signature algorithm / hash |
| thumbprint |
| v3 extensions: |
| basicConstraints CA—True |
Note: As this is a CA certificate, basicConstraints is set to True. For leaf certificates, basicConstraints is set to False.
| keyUsage—digitalSignature and keyEncipherment |
| extendedkeyUsage—serverAuth |
| subjectKeyIdentifier—hash |
| authorityKeyIdentifier—keyid,issuer:always |
All server certificates for decrypted outbound connections are issued by the GigaVUE node. The issuing CA is imported into the client’s browsers as a trusted CA. Thus, the clients will trust all certificates signed by the GigaVUE node. This interferes with the ability of the clients to check for the revocation status of the certificates. Thus the burden is upon the node to perform the revocation checks on the original server certificates before regenerating the certificates to the clients.
If revocation check is enabled with soft fail, decryption will continue even if the revocation status is not already known, whereas with hard fail, traffic will not be decrypted unless the revocation status is determined for certain.
If revocation check is enabled, once the GigaVUE node determines that the server certificate is revoked, further SSL connections to the server are dropped.
By default, revocation check is disabled.
There are two methods to check the revocation status of the certificates as follows:
| using a Certificate Revocation List (CRL) from the issuing Certificate Authorities (CAs). Refer to Certificate Revocation List (CRL). |
| using the Online Certificate Status Protocol (OCSP). Refer to Online Certificate Status Protocol (OCSP). |
A Certificate Revocation List (CRL) is an online database of certificates that have been revoked.
Each issuing CA in the PKI infrastructure maintains a list of revoked certificates that they had issued earlier. The list contains the serial number of the revoked certificates and the reasons for the revocation. Any revoked certificate should not be trusted even if the signatures are valid. CAs publish the revocation list periodically.
Each server certificate will contain the CRL location in the “CRL distribution points” X.509 extension.
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 certificate.
Certificate status can be verified near real-time by querying the OCSP link in the certificate. The link will be present in the “Authority Information Access” X.509 extension.
If both CRL and OCSP are enabled, OCSP is performed first, followed by CRL.
Both CRL and OCSP require Internet connectivity. Refer to Set up the Stack Port Interface for more information.
 - The key certificate is attached to an inline-SSL profile and the profile is part of the inline-SSL GSOP which is used in a traffic map. This will also indicate a certificate which is being used as a signing CA in outbound deployment .
- The key certificate is attached to an inline-SSL profile and the profile is part of the inline-SSL GSOP which is used in a traffic map. This will also indicate a certificate which is being used as a signing CA in outbound deployment . - The key certificate is not actively participating in any traffic flow.
- The key certificate is not actively participating in any traffic flow. - The key certificate has been expired .
- The key certificate has been expired .


