To enable secure and confidential communication between GigaVUE-FM, GigaVUE-OS devices and other network entities, it is important to deploy, manage and update the required certificates. By default, GigaVUE-FM and the GigaVUE-OS devices come up with self-signed certificates. However, you can also deploy custom certificates signed by the Certificate Authorities (CA). This requires you to manually install the certificates and map the certificates to the web.
Starting in software version 5.13.01, GigaVUE-FM and the devices support Automated Certificate Management Environment (ACME) protocol that allows automatic certificate signing and deployment between Certificate Authorities (CAs) and GigaVUE-FM, GigaVUE-OS devices web servers. If your devices and GigaVUE-FM instances are running software version 5.13.00 or lower, ensure to add all the devices to GigaVUE-FM, upgrade the devices and GigaVUE-FM to software version 5.13.01 for the ACME protocol to be functional.
How ACME Works
The ACME protocol is based on the principle of client-server communication:
- ACME Server: Runs at a Certificate Authority, for example, Step-ca . The ACME server responds to the client requests and executes the requested actions (issue, renew, revoke) once the client is authorized.
- ACME Client: Runs on the user’s server or device that needs to be protected by the PKI certificate. The ACME client uses the ACME protocol to request the ACME server running in CA to perform the certificate management tasks such as issue, renew, revoke of certificates.
An ACME server and a client must be appropriately configured. The client sends requests to the server and the server receives the requests and issues certificates for the client. The ACME server and the client communicate over a secure HTTPS connection using JSON messages.
Note: For more details about the Automatic Certificate Management Environment protocol, refer to RFC 8555.
ACME Configuration in GigaVUE-FM and the Devices
ACME client is configured in both GigaVUE-FM and the GigaVUE-OS devices, and takes care of the following operations by contacting the ACME server that runs in a Certificate Authority:
- Issue of Certificates
- Renewal of Certificates
- Certificate Revocation
The following diagram shows how ACME works in GigaVUE-FM and the devices:
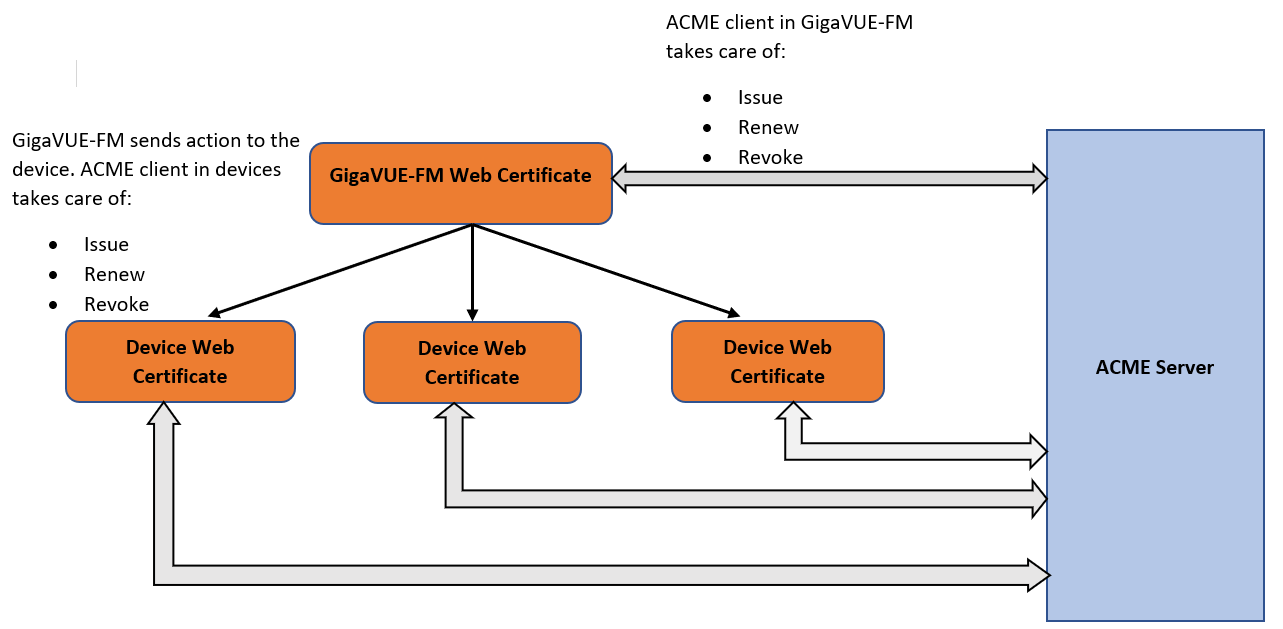
Refer to the following table for a summary of the ACME process in devices and GigaVUE-FM:
| Task | In Device | In GigaVUE-FM |
|---|---|---|
| Certificate Issuance and Renewal |
The ACME Client is installed in the devices and takes care of automatic issue/renew/revoke of the HTTPS certification of the devices. Issuance: After the certificate is downloaded, the device will automatically update the ACME issued certificate for web operation. Renewal:
Note: If the user provided auto renew days is > (expiry date – today date), then default renewal days will be calculated (1/3rd days before expiry). |
The ACME client is installed in GigaVUE-FM and takes care of automatic issue/renew/revoke of the HTTPS certification of GigaVUE-FM (standalone GigaVUE-FM instances and also instances in a HA group). Issuance: After the certificate is downloaded, GigaVUE-FM will automatically update the ACME issued certificate for web operation. Renewal:
|
| Certificate Revocation |
Upon receiving revoke command (from GigaVUE‑FM), the device:
Note: The certificate revocation process renews the certificate first followed by the revocation. This is to avoid the down time of the web server . |
Revoke operation in GigaVUE-FM:
Once the re-issue and revoke operation is successful, the newly issued ACME certificate will be activated as the Web certificate. If revoke fails, GigaVUE-FM will fall back to default certification mode. |
| Clear Certificate | Clear operation clears the ACME issued certificate from the devices and maps the web certificate to the default certificate. This command also cancels the auto-renewal timers that are started by the ACME client in the device | Deleting the ACME issued certificate results in GigaVUE-FM falling back to the default certification mechanism. |



