Configure AAA Authentication Options
The Authentication Priority section of the AAA page specifies which authentication methods should be used for logins to the GigaVUE H series node as well as the order in which they should be used.
The valid authentication the authentication methods are:
| • | Local database |
| • | External authentication servers |
| • | TACACS+ |
| • | RADIUS |
| • | LDAP |
You can enable any of or all of the authentication methods ((TACACS+, RADIUS, LDAP, and local) at the same time. If you enable more than one method, the GigaVUE H Series node uses the methods in the same order in which they are specified, falling back as necessary:
- If remote authentication is configured first followed by local, the system only falls back to local authentication method when all the remote servers are unreachable.
- If local authentication is configured first followed by remote, the system will fallback to the remote authentication method only if the user is either non-existent in the local database or the password entered does not match the local one.
Refer to the following examples.
In this example, TACACS+ server authentication is configured as the only authentication method. Local is not included as one of the methods. Therefore, the node will be authenticated exclusively by the TACACS+ server:
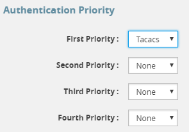
In this example, TACACS+ server authentication is configured with first priority followed by Local authentication. If TACACS+ server is reachable, the local method will not be checked. If the TACACS+ server becomes unreachable, the system will fall back to local authentication method only when all the TACACS+ servers are unreachable:
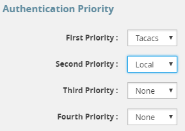
In this example, the local method will only be checked if neither the TACACS+ server or the RADIUS servers are reachable:
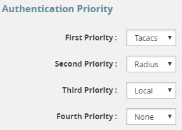
In this example, if the TACACS+ server is not reachable, the next method in order will be checked, which is local:
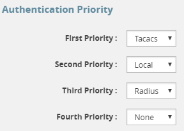
Note: To prevent lockouts, it is recommended that you include local as one of the methods. However, the local method is optional.
For example, you could use an external authentication server as your primary authentication method with local authentication as a fallback (Figure 1: Local vs. External Authentication ). The fallback is used when an authentication server is unreachable.
Note: If a server responds to a login attempt with an authentication reject, then next configured server is tried. If all the servers are unreachable, the next method is tried until either the user’s login is granted or all specified methods are exhausted.
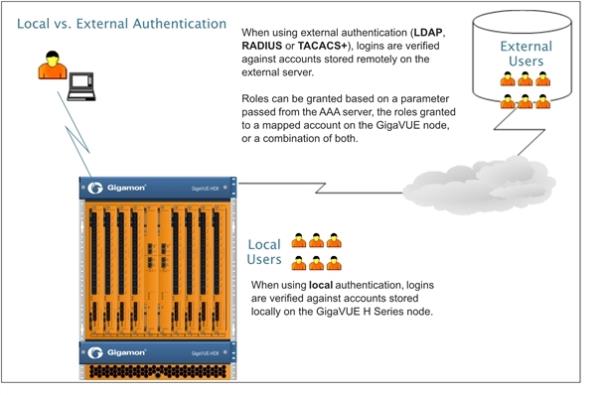
| Figure 9 | Local vs. External Authentication |
Remote Authentication Only
If you want to have the node authenticated exclusively by a remote server, do not include local as one of the methods in the Authorization Priority:

Also, configure remote-only authorization by selecting Remote Only for Map Order under User Mapping on the AAA page as shown in the following figure.

When AAA authentication is configured to a single method and authorization is configured to remote-only, there is no fallback.
When local is not in the default login order, there will be no way to access the local default users in the node’s database. If the connection to the remote server is no longer available, no further authentication will be made.
If this happens, the only option is to use a password recovery process which requires a reboot of the node. Refer to Contact Technical Support on page 345.
Authorization of User Account
If a user account exists on the remote server as well as on the local device, the remote user will be mapped to the local account, regardless of the LDAP mapping policy.
Next Steps
If you enable RADIUS, TACACS+, or LDAP, you must also:
| • | Add the RADIUS, TACACS+, or LDAP server to the GigaVUE H Series node’s list using the corresponding RADIUS, TACACS+, or LDAP pages. Refer to Add AAA Servers to the Node’s List. |
| • | Set up GigaVUE H series nodes and users within the external authentication server itself. Depending on your authorization model, you can grant privileges to externally authenticated users based on the roles assigned to a corresponding account on the local node, the roles passed from the AAA server, or a combination of both. Refer to Grant Roles with External Authentication Servers for details. |



