Configure Cisco ACS: TACACS+ Authentication
Use the following steps to configure Cisco ACS 5.x (TACACS+) to grant extra roles to externally authenticated users in GigaVUE-FM.
Enable Extra Roles for TACACS+ in GigaVUE-FM
| 1. | Configure GigaVUE-FM to accept extra roles in the response from the AAA server: |
0Click Edit Default in the Authentication > TACACS+.
aSet the Extra Roles option to Yes.
bClick Update.
Assign local-user-name to Shell Profile (ACS 5.x)
| 2. | Navigate to Policy Elements > Authorization and Permissions > Device Administration > Shell Profiles and click Create to add a new shell profile. |
3Give the profile a name and description in the General page.
4Click the Custom Attributes page.
5Set the Attribute field to local-user-name.
| 3. | Leave the Requirement and Attribute Value fields at their default value (Mandatory and Static, respectively). |
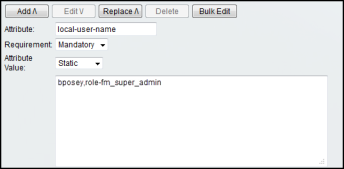
| 4. | Supply the local user mapping and optional roles using the following syntax, as shown in the figure below: |
<mapping_local_user>[:role-<mapping_local_role_1> [role-<mapping_local_role_2>[...]]]
Note: The extra role specified in the authentication server must match a role already available in GigaVUE-FM – fm_super_admin, fm_admin, or fm_user.
6Click the Add button  to add this attribute to the shell profile.
to add this attribute to the shell profile.
7Click Submit to finalize this shell profile.
8Create Service Selection Rules that will assign this shell profile to desired GigaVUE users.
Figure 209: Supplying local-user-name and Roles in ACS 5.x for TACACS+ shows the an example of a shell profile for TACACS+ in ACS 5.x with the local-user-name attribute supplied.
Figure 209: Supplying local-user-name and Roles in ACS 5.x for TACACS+



