GigaSMART Adaptive Packet Filtering (APF)
Adaptive Packet Filtering (APF) provides filtering on specific encapsulation protocol parameters. Additionally, it has the ability to look beyond the encapsulation protocol parameters into the original (encapsulated) data packet, to filter on source and destination IP or Layer 4 port numbers. APF offers the ability to look for content anywhere in the data packet and make intelligent filtering and forwarding decisions.
Adaptive Packet Filtering includes fragmentation awareness whereby all IP fragments associated with the filtered data packet are always forwarded allowing a complete view of the traffic stream for accurate analytics. APF also provides a powerful filtering engine that identifies content (based on patterns) across any part of the data packet, including the data packet payload.
APF Examples
The following are APF examples:
| Identify Social Security Numbers in User-Level Transactions |
| Masking Social Security Numbers |
| Filtering on Fiber Channel over Ethernet (FCOE) Traffic |
| Multi-Encapsulation Filtering |
| Filtering on Subscriber Device IP (User-Endpoint IP or UE-IP) |
| Filtering on Inner Layer 2-4 Parameters for Unrecognized Headers |
| GTP Tunnel ID-Based Filtering |
| ERSPAN Tunneling |
| Distributing Traffic Based on Inner IP Addresses and Inner TCP Port Values |
| MPLS Label Based Filtering |
| Combining APF with GigaSMART Operations |
| Conditional Header Stripping |
| Facilitating Overlapping Rules |
Identify Social Security Numbers in User-Level Transactions
The following example looks for packets containing Social Security Numbers in an incoming traffic stream using pattern matching. Once a match is detected, the packets are forwarded to a monitoring tool for additional analysis.
|
Step |
Description |
Command |
|||
|
Configure one network and two tool ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsgrp1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil apf set port-list gsgrp1 |
|||
|
Create a virtual port. |
(config) # vport alias vp1 gsgroup gsgrp1 |
|||
|
Create a first level map to forward traffic from network port 1/1/x3 to virtual port vp1. |
(config) # map alias map1 (config map alias map1) # type firstLevel byRule (config map alias map1) # from 1/1/x3 (config map alias map1) # to vp1 (config map alias map1) # rule add pass ipver 4 (config map alias map1) # exit (config) # |
|||
|
Create a second level map to forward traffic from the virtual port, vp,1 to GigaSMART with pattern matching. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x1 (config map alias map2) # gsrule add pass pmatch RegEx "\d{3}-?\d{2}-?\d{4}" 40..80 (config map alias map2) # exit (config) # |
Masking Social Security Numbers
In the following pattern matching example, IPv4 packets contain Social Security Numbers (SSNs) in the format xxx-xx-xxxx. If the SSNs are between offset 40 and 80, they will be replaced with zeros.
|
Step |
Description |
Command |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsgrp1 port-list 1/3/e1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias gsTraffic gsgroup gsgrp1 |
|||
|
Create a first level map to direct traffic from network port 1/1/x1 to virtual port gsTraffic. |
(config) # map alias map1 (config map alias map1) # type firstLevel byRule (config map alias map1) # from 1/1/x1 (config map alias map1) # to gsTraffic (config map alias map1) # rule add pass ipver 4 (config map alias map1) # exit (config) # |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsop1 apf set port-list gsgrp1 |
|||
|
Create a second level map to direct traffic from the virtual port gsTraffic to GigaSMART. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from gsTraffic (config map alias map2) # use gsop gsop1 (config map alias map2) # to 1/1/x6 (config map alias map2) # gsrule add pass pmatch mask 0x00 RegEx "\d{3}-?\d{2}-?\d{4}" 40..80 (config map alias map2) # exit (config) # |
|||
|
Display the configuration for this example. |
(config) # show gsgroup (config) # show vport (config) # show gsop (config) # show map |
Filtering on Fiber Channel over Ethernet (FCOE) Traffic
The flexibility offered by regular expression-based filters can be used as an infrastructure to classify traffic streams with protocol headers that are typically unsupported on traditional TAP/SPAN aggregation devices. In this example, regular expression-based filters are used for filtering on the source address in a Fiber Channel header.
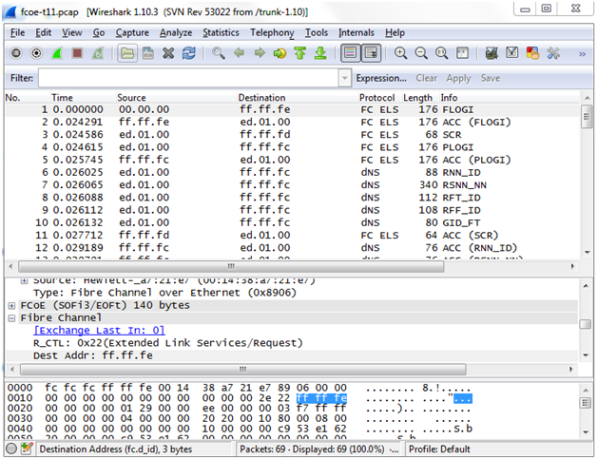
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward FCOE traffic to the virtual port. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass ethertype 8906 (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on regular expression, using a string match to the destination address in the FCOE packet. |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass pmatch string "\xff\xff\xfe" 29 (config map alias map1) # exit (config) # |
Multi-Encapsulation Filtering
In order to complement the mobility brought about by the virtualized server infrastructure, network virtualization overlays like VXLAN, VNTag, NVGRE are being designed and implemented in Data Centers and Enterprise environment. Across Service Provider environments, huge volumes of traffic are being tunneled over GTP. Until now, the GigaVUE Visibility Platform provided the option of stripping out these headers, thus providing visibility to monitoring tools that do not understand these overlays and encapsulation protocol. With APF, this capability is further enhanced where operators now have the option of making forwarding decisions based on the encapsulation and inner packet contents.
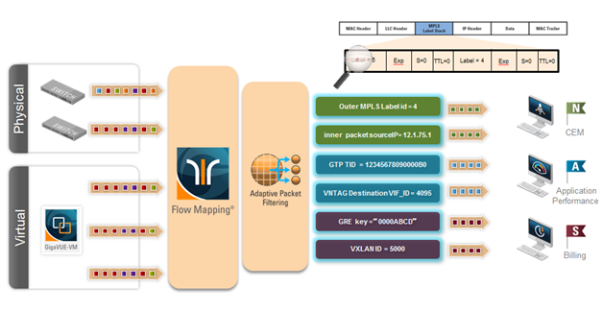
With encapsulation awareness enabled by APF, operators have multiple options to act on the packet including the flexibility to:
| Filter on encapsulation header parameters, Layer 2 – 4 parameters in the outer or inner headers (up to 5 layers of encapsulation) in any combination. For example: |
| Forward traffic specific to a subset of VXLAN ID’s to one or more monitoring tools. |
| Distribute traffic based on MPLS label values across one or more monitoring tools. |
| In combination with header stripping: |
| Implement “conditional” header-stripping, based on encapsulation header parameters or inner/outer packet contents, as follows: |
– Forward a subset of traffic “as-is” to monitoring tools that need these encapsulations for analysis.
– Alternatively, strip out the outer headers/encapsulations and distribute traffic to monitoring tools that do not require these outer headers for analysis.
| Since APF is implemented as a second level map, operators can also implement overlapping rules where: |
| A copy of the traffic can be distributed across a group of monitoring tools. |
| A refined subset from the same incoming stream is distributed across a different set of tools. |
Filtering on Subscriber Device IP (User-Endpoint IP or UE-IP)
Encapsulation awareness enabled by APF allows mobile operators to filter on Layer 2 – 4 header parameters found in an encapsulated packet.
This allows operators to filter and forward traffic specific to a mobile subscriber device or a group of subscriber devices, identified by their IP address (User-Endpoint IP) to one or more monitoring tools.
In this example, we are:
| Identifying and forwarding traffic from / to a UE-IP of 1.1.1.1 to a monitoring tool connected to 1/1/x1 |
| Identifying and forwarding traffic from / to a UE-IP of 1.1.1.2 to a different monitoring tool connected to tool port 1/1/x4 |
In many cases, the GTP control sessions are low-volume and are useful in providing some level of visibility in to the quality of experience of the subscribers. To this end, operators prefer to replicate the control sessions across all the monitoring tools, while filtering and forwarding a subset of the user-plane sessions to a subset of monitoring tools. The following example also illustrates configuration commands, leveraging the patented flow-mapping technology to replicate the GTP control sessions across all the monitoring tools involved in the traffic analysis.
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward GTP-u traffic to the virtual port. Note: In the rule, 2152 is GTP-u traffic. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass portsrc 2152 (config map alias to_vp) # exit (config) # |
|||
|
Create a first level map to forward GTP-c traffic to the tools. Note: In the rule, 2123 is GTP-c traffic. |
(config) # map alias to_tool (config map alias to_tool) # type regular byRule (config map alias to_tool) # from 1/1/x3 (config map alias to_tool) # to 1/1/x1,1/1/x4 (config map alias to_tool) # rule add pass portsrc 2123 (config map alias to_tool) # exit (config) # |
|||
|
Create a second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # gsrule add pass ipv4 dst pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # exit (config) # |
|||
|
Create another second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x4 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # gsrule add pass ipv4 dst pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # exit (config) # |
Filtering on Inner Layer 2-4 Parameters for Unrecognized Headers
The flexibility of encapsulation awareness enables filtering on encapsulated contents even if APF does not recognize the outer encapsulation header. The following example illustrates a packet encapsulated in Fabric Path headers. Fabric Path headers (as shown in the figure) are mac-in-mac headers that are currently not recognized by APF. However operators can still filter and forward traffic flows based on Layer 2 – 4 parameters found in the encapsulated packets.
In this example, we are:
| Identifying and forwarding traffic from/to ip 1.1.1.1 in the inner / original packet to monitoring tool connected to tool port 1/1/x1 |
| Identifying and forwarding traffic from/to ip 1.1.1.2 in the inner / original packet to monitoring tool connected to tool port 1/1/x4 |
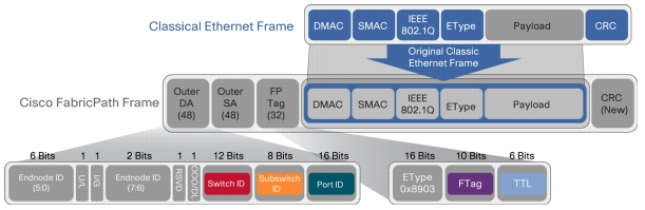
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward fabric path packets to the virtual port. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass ethertype 8903 (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass ipv4 src pos 1 value 1.1.1.1 255.255.255.255 (config map alias map1) # gsrule add pass ipv4 dst pos 1 value 1.1.1.1 255.255.255.255 (config map alias map1) # exit (config) # |
|||
|
Create another second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x4 (config map alias map1) # gsrule add pass ipv4 src pos 1 value 1.1.1.2 255.255.255.255 (config map alias map2) # gsrule add pass ipv4 dst pos 1 value 1.1.1.2 255.255.255.255 (config map alias map2) # exit (config) # |
GTP Tunnel ID-Based Filtering
The following example demonstrates filtering and forwarding traffic based on tunnel IDs included as part of the GTP user-plane messages. It also illustrates the concept of a shared collector to which traffic not matching any of the configured filters can be optionally sent. GTP control sessions are forwarded to all the monitoring tools leveraging the power of flow mapping by filtering on Layer-4 UDP port 2123.
For GTP-u:
| Filter and forward teid ranges 0x001e8480..0x001e8489 to a monitoring tool |
| Filter and forward teid ranges 0x001e8490..0x001e8499 to another monitoring tool |
| Forward the rest of the traffic to a shared collector |
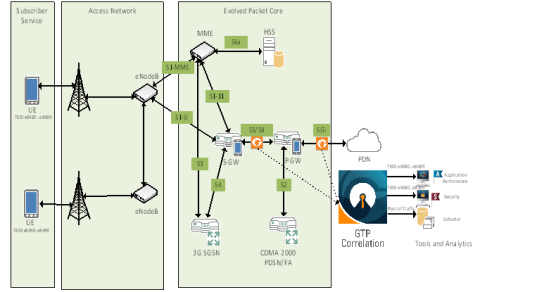
|
Step |
Description |
Command |
|||
|
Configure one network and three tool type of ports. |
(config) # port 1/3/x9 type network (config) # port 1/3/x15 type tool (config) # port 1/3/x13 type tool (config) # port 1/3/x14 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation and assign it to the GigaSMART group. Packets processed by this operation are evaluated using Adaptive Packet Filtering (APF) rules. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map that directs GTP-u traffic from physical network port/s to the virtual port created in the previous step. Note: In the rule, 2152 is GTP-u traffic. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # to vp1 (config map alias to_vp) # from 1/3/x9 (config map alias to_vp) # rule add pass portsrc 2152 (config map alias to_vp) # exit (config) # |
|||
|
Create a first level map that directs GTP-u traffic from physical network port/s to the tool ports. Note: In the rule, 2123 is GTP-c traffic. |
(config) # map alias ctrl_to_tool (config map alias ctrl_to_tool) # type regular byRule (config map alias ctrl_to_tool) # to 1/3/x13,1/3/x15 (config map alias ctrl_to_tool) # from 1/3/x9 (config map alias ctrl_to_tool) # rule add pass portsrc 2123 (config map alias ctrl_to_tool) # exit (config) # |
|||
|
Create a second level map that takes traffic from the virtual port, applies the GigaSMART operation, and matches tunnel IDs specified by the gsrule. |
(config) # map alias m1 (config map alias m1) # type secondLevel byRule (config map alias m1) # use gsop gsfil (config map alias m1) # to 1/3/x15 (config map alias m1) # from vp1 (config map alias m1) # gsrule add pass gtp gtpu-teid range 0x001e8480..0x001e8489 subset none (config map alias m1) # exit (config) # |
|||
|
Create a second level map that takes traffic from the virtual port, applies the GigaSMART operation, and matches tunnel IDs specified by the gsrule. |
(config) # map alias m2 (config map alias m2) # type secondLevel byRule (config map alias m2) # use gsop gsfil (config map alias m2) # to 1/3/x15 (config map alias m2) # from vp1 (config map alias m2) # gsrule add pass gtp gtpu-teid range 0x001e8490..0x001e8499 subset none (config map alias m2) # exit (config) # |
|||
|
Add a shared collector for any unmatched data and send it to the third tool port. |
(config) # map-scollector alias scoll (config map-scollector alias scoll) # from vp1 (config map-scollector alias scoll) # collector 1/3/x14 (config map-scollector alias scoll) # exit (config) # |
ERSPAN Tunneling
In this example, APF is used to filter packets based on ERSPAN ID. The ERSPAN header is not removed from the packet.
A second level map is configured in the example. A virtual port feeds traffic to the second level map. APF filters the packets and forwards those that match the filter criteria in the map.
|
Step |
Description |
Command |
|||
|
Configure a tool type of port. |
(config) # port 1/1/g1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsgp2 port-list 1/3/e2 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp gsgroup gsgp2 |
|||
|
Configure the GigaSMART operation and assign it to the GigaSMART group. |
(config) # gsop alias er2 apf set port-list gsgp2 |
|||
|
Create a first level map. |
(config) # map alias test1a (config map alias test1a) # type firstLevel byRule (config map alias test1a) # to vp (config map alias test1a) # from 1/1/g3 (config map alias test1a) # rule add pass macsrc 0000.0000.0000 0000.0000.0000 (config map alias test1a) # exit (config) # |
|||
|
Create a second level map. |
(config) # map alias test1b (config map alias test1b) # type secondLevel byRule (config map alias test1b) # use gsop er2 (config map alias test1b) # to 1/1/g1 (config map alias test1b) # from vp (config map alias test1b) # gsrule add pass erspan id value 0 (config map alias test1b) # exit (config) # |
|||
|
Display the configuration for this example. |
(config) # show gsgroup (config) # show gsop (config) # show map |
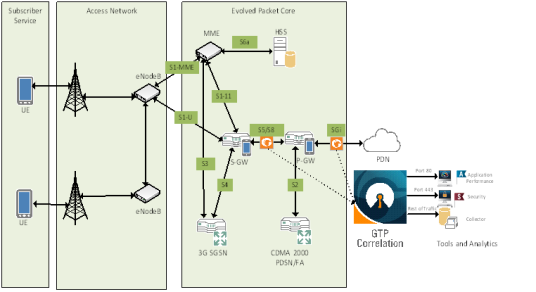
Distributing Traffic Based on Inner IP Addresses and Inner TCP Port Values
In the following example, traffic is distributed based on inner IP addresses and inner TCP port values as follows:
| Packets from VLAN 20 with GTP inner IP 65.128.7.21 and 98.43.132.70, inner TCP port 80 is forwarded to one tool port |
| Packets from VLAN 20 with GTP inner IP 65.128.7.21 and 98.43.132.70, inner TCP port 443 is forwarded to a second tool port |
| All packets not matching these rules is forwarded to a third tool port |
|
Step |
Description |
Command |
|||
|
Configure one network and three tool type of ports. |
(config) # port 1/1/x1 type network (config) # port 1/1/x10 type tool (config) # port 1/1/x11 type tool (config) # port 1/1/x12 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsgrp1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation and assign it to the GigaSMART group. Packets processed by this operation are evaluated using Adaptive Packet Filtering (APF) rules. |
(config) # gsop alias g1 apf set port-list gsgrp1 |
|||
|
Configure a virtual port and associate it with the GigaSMART group. |
(config) # vport alias gsTraffic gsgroup gsgrp1 |
|||
|
Create a first level map that directs traffic from the physical network port/s to the virtual port created in the previous step. |
(config) # map alias map1 (config map alias map1) # type firstLevel byRule (config map alias map1) # to gsTraffic (config map alias map1) # from 1/1/x1 (config map alias map1) # rule add pass vlan 20 protocol udp portdst 2152 (config map alias map1) # exit (config) # |
|||
|
Create a second level map that takes traffic from the virtual port, applies the GigaSMART operation, matches the rules, and sends the traffic to one tool port. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # use gsop g1 (config map alias map2) # to 1/1/x10 (config map alias map2) # from gsTraffic (config map alias map2) # gsrule add pass ipv4 dst pos 2 value 65.128.7.21 /32 ipv4 protocol pos 2 value tcp l4port dst pos 2 value 80 (config map alias map2) # gsrule add pass ipv4 dst pos 2 value 98.43.132.70 /32 ipv4 protocol pos 2 value tcp l4port dst pos 2 value 80 (config map alias map2) # exit (config) # |
|||
|
Create a second level map that takes traffic from the virtual port, applies the GigaSMART operation, matches the rules, and sends the traffic to another tool port. |
(config) # map alias map3 (config map alias map3) # type secondLevel byRule (config map alias map3) # use gsop g1 (config map alias map3) # to 1/1/x11 (config map alias map3) # from gsTraffic (config map alias map3) # gsrule add pass ipv4 dst pos 2 value 65.128.7.21 /32 ipv4 protocol pos 2 value tcp l4port dst pos 2 value 443 (config map alias map3) # gsrule add pass ipv4 dst pos 2 value 98.43.132.70 /32 ipv4 protocol pos 2 value tcp l4port dst pos 2 value 443 (config map alias map3) # exit (config) # |
|||
|
Add a shared collector for any unmatched data and send it to the third tool port. |
(config) # map-scollector alias mapcl (config map-scollector alias mapcl) # from gsTraffic (config map-scollector alias mapcl) # collector 1/1/x12 (config map-scollector alias mapcl) # exit (config) # |
MPLS Label Based Filtering
Multiprotocol Label Switching (MPLS) is a mechanism in high-performance telecommunications networks that directs data from one network node to the next based on short path labels rather than long network addresses, avoiding complex lookups in a routing table. The labels identify virtual links (paths) between distant nodes rather than endpoints.
MPLS is a scalable, protocol-independent transport. In an MPLS network, data packets are assigned labels. Packet-forwarding decisions are made solely on the contents of this label, without the need to examine the packet itself. This allows one to create end-to-end circuits across any type of transport medium, using any protocol.
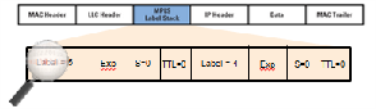
However in the context of Visibility Platform nodes, traffic flows encapsulated in MPLS labels cannot be filtered and forwarded. With the wide-scale adoption of MPLS as a technology across enterprise and service provider environments, the ability to classify traffic flows based on MPLS labels would be a huge value add to granularly control the flow of traffic to the monitoring tools. APF can be leveraged to filter and forward traffic flows based on MPLS label values. MPLS can stack multiple labels to form tunnels within tunnels. The flexibility of APF facilitates traffic classifications across up to 5 levels of MPLS label stacks in addition to the capability to filter and forward based on Layer 2-4 parameters found in the encapsulated packet. The following example illustrates filtering and forwarding traffic based on MPLS labels, as follows:
| Filter and forward traffic flows specific to mpls label = 4 at the second level in the MPLS label stack to tool 1 |
| Filter and forward traffic flows specific to mpls label = 3 at the first level in the MPLS label stack to tool 2 |
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward traffic to the virtual port. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass ipver 4 (config map alias to_vp) # rule add pass macsrc 00:00:00:00:00:00 bidir (config map alias to_vp) # exit (config) # |
|||
|
Create another second level map to filter on MPLS label. |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass mpls label pos 1 value 4 (config map alias map1) # exit (config) # |
|||
|
Create another second level map to filter on MPLS label. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x4 (config map alias map1) # gsrule add pass mpls label pos 1 value 3 (config map alias map2) # exit (config) # |
Combining APF with GigaSMART Operations
APF can also be combined with other GigaSMART functions including Header Stripping, Packet Slicing or Masking, De-duplication and FlowVUE. This provides network administrators and operators to perform a second layer of filtering in combination with the GigaSMART tool optimization and packet manipulation operations.
In the following example, operators can distribute traffic to monitoring tools based on de-capsulated contents, more specifically, after Header stripping VXLAN:
| Identifying and forwarding traffic from/to ip 1.1.1.1 from the decapsulated packets to monitoring tool connected to tool port 1/1/x1 |
| Identifying and forwarding traffic from/to ip 1.1.1.2 in the decapsulated packets to monitoring tool connected to tool port 1/1/x4 |
Note: This can be applied to any protocol that is supported through header-stripping, for example:
| GTP, VXLAN, ISL, MPLS, MPLS+VLAN, VLAN, VN-Tag, fabric-path. |
| This is also supported for Gigamon tunnel decapsulation. |
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operation. |
(config) # gsop alias gsfil_vxlanhs apf set strip-header vxlan 0 port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward VXLAN traffic to the virtual port. VXLAN accepts destination UDP ports 8472 and 4789. Starting in software version 4.5.01, VXLAN also accepts destination UDP port 48879. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass portsrc 8472 (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil_vxlanhs (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # gsrule add pass ipv4 dst pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # exit (config) # |
|||
|
Create another second level map to filter on source and destination IP (bi-directional). |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil_vxlanhs (config map alias map2) # to 1/1/x4 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # gsrule add pass ipv4 dst pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # exit (config) # |
Conditional Header Stripping
Another use-case that can be addressed leveraging the flexibility of APF would be the capability to header strip packets based on specific contents found across the packet including the inner packet contents. Since the APF rules are enforced before any other GigaSMART operation, operators can filter based on encapsulation protocol values and /or encapsulated (original) packet contents and apply conditional header stripping operations.
The following example shows how an end-user can filter and strip out outer VXLAN headers for a subset of the traffic based on inner IP addresses, while sending the rest of the traffic “as-is” to monitoring tools that need the VXLAN headers for traffic analysis, as follows.
| Identifying and forwarding traffic from/to ip 1.1.1.1 in the inner / encapsulated packets to monitoring tool connected to tool port 1/1/x1 after header stripping VXLAN. |
| Identifying and forwarding traffic from/to ip 1.1.1.2 in the inner / encapsulated packets to monitoring tool connected to tool port 1/1/x4 without stripping the VXLAN header. |
Note: This can be applied to any GigaSMART operation. While this example shows filtering based on inner packet contents, conditional SMART operations can be applied by filtering on encapsulation headers as well.
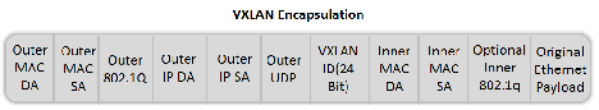
Note: This can be applied to any protocol that is supported through header stripping. GTP, VXLAN, ISL, MPLS, MPLS+VLAN, VLAN, VN-Tag, and fabric-path are all supported, as is Gigamon tunnel decapsulation.
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operations. |
(config) # gsop alias gsfil_vxlanhs apf set strip-header vxlan 0 port-list gsg1 (config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward VXLAN traffic to the virtual port. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1 (config map alias to_vp) # rule add pass portsrc 8472 (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on source and destination IP (bi-directional), using first GigaSMART operation. |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil_vxlanhs (config map alias map1) # to 1/1/x1 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # gsrule add pass ipv4 dst pos 2 value 1.1.1.1 255.255.255.255 (config map alias map1) # exit (config) # |
|||
|
Create another second level map to filter on source and destination IP (bi-directional), using second GigaSMART operation. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x4 (config map alias map1) # gsrule add pass ipv4 src pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # gsrule add pass ipv4 dst pos 2 value 1.1.1.2 255.255.255.255 (config map alias map2) # exit (config) # |
Facilitating Overlapping Rules
Because APF is implemented as a second level map operation, APF can also be leveraged for implementing basic overlapping rules. For the same incoming input stream, a copy of the traffic can be sent out to a group of monitoring tools while a refined subset of the traffic stream can be sent to a different set of monitoring tools. Typically overlapping rules would be implemented by combining APF with the patented FlowMapping technology.
Note that Role-Based Access control in the case of APF is applied at the gsgroup / e port.
In the following example, for the same input stream:
| HTTP traffic is identified and distributed to a monitoring tool connected to tool port 1/1/x1. |
| At the same time, the same stream of HTTP packets are being sent out after slicing unwanted packet contents to a different monitoring tool connected to tool port 1/1/x4. |
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operations. |
(config) # gsop alias gsfil apf set port-list gsg1 (config) # gsop alias gsfil_slice apf set slicing protocol none offset 150 port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward traffic to the virtual port. Port 1/1/x1 and virtual port vp1 are sent destination port 80 traffic, which is HTTP. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1,1/1/x1 (config map alias to_vp) # rule add pass portdst 80 bidir (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on HTTP traffic and slice it. |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil_slice (config map alias map1) # to 1/1/x4 (config map alias map1) # gsrule add pass ipver pos 1 value 4 (config map alias map1) # exit (config) # |
|||
|
Create another second level map for the rest of the traffic. |
(config) # map alias map2 (config map alias map2) # type secondLevel byRule (config map alias map2) # from vp1 (config map alias map2) # use gsop gsfil (config map alias map2) # to 1/1/x1 (config map alias map1) # gsrule add pass ipver pos 1 value 4 (config map alias map2) # exit (config) # |
In the following example, for the same traffic stream, TCP traffic is sent to one monitoring tool while forwarding a subset of TCP flows specific to HTTP to another monitoring tool connected to tool port 1/1/x4.
|
Step |
Description |
Command |
|||
|
Configure ports. |
(config) # port 1/1/x3 type network (config) # port 1/1/x4 type tool (config) # port 1/1/x1 type tool |
|||
|
Configure a GigaSMART group and associate it with a GigaSMART engine port. |
(config) # gsgroup alias gsg1 port-list 1/1/e1 |
|||
|
Configure the GigaSMART operations. |
(config) # gsop alias gsfil apf set port-list gsg1 |
|||
|
Create a virtual port and associate it with the GigaSMART group. |
(config) # vport alias vp1 gsgroup gsg1 |
|||
|
Create a first level map to forward TCP traffic to the virtual port. |
(config) # map alias to_vp (config map alias to_vp) # type firstLevel byRule (config map alias to_vp) # from 1/1/x3 (config map alias to_vp) # to vp1,1/1/x1 (config map alias to_vp) # rule add pass protocol tcp (config map alias to_vp) # exit (config) # |
|||
|
Create a second level map to filter on HTTP traffic. |
(config) # map alias map1 (config map alias map1) # type secondLevel byRule (config map alias map1) # from vp1 (config map alias map1) # use gsop gsfil (config map alias map1) # to 1/1/x4 (config map alias map1) # gsrule add pass l4port dst pos 2 value 80 (config map alias map1) # gsrule add pass l4port src pos 2 value 80 (config map alias map1) # exit (config) # |
|||
|
Display APF statistics |
(config) # show gsop stats alias forapf
|



