GigaSECURE Security Delivery Platform
This section is an overview of the GigaSECURE® Security Delivery Platform (SDP), which transforms the way security applications are deployed and leveraged, enabling them to be more effective at protection and remediation, less complex, and more cost-effective. This section also provides links to detailed information for the pillars of GigaSECURE and to other documents.
GigaSECURE solutions provide pervasive visibility of network traffic, user, application, and suspicious activity, which bolsters security effectiveness, eliminates blind spots, and enables protection against threats. With GigaSECURE, you look inside networks to detect where compromise has occurred.
Figure 1 displays the pillars of the Security Delivery Platform along the bottom of the figure, consisting of GigaVUE Visibility Platform nodes (H Series and TA Series, as well as standalone and embedded TAPs) with GigaVUE-VM providing access to virtual traffic, and applications for NetFlow/IPFIX Generation, SSL Decryption, and Application Session Filtering (ASF), as well as inline bypass.
On the right of Figure 1, the Application Programming Interface (API) enables a degree of automation, allowing security tools to control the traffic feeds they receive from the SDP.
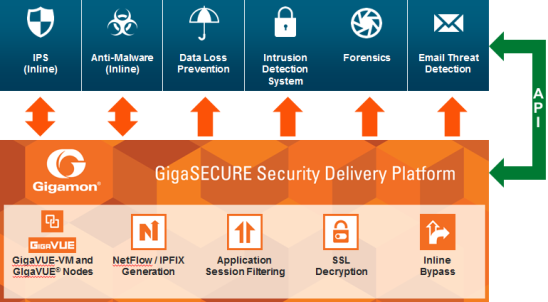
| Figure 48 | GigaSECURE Security Delivery Platform |
GigaSECURE SDP connects into the network, across physical and virtual infrastructures, and delivers traffic to the applications that require it. Security tools connect into the SDP at whatever interface speeds they are capable of connecting. Consequently, they will receive a relevant traffic stream from across the network infrastructure.
Through SDP, organizations can unify their security applications (displayed along the top of Figure 1), eliminating blind spots and partial coverage. Security devices can get a complete view of the network flows and the metadata that they require in order to detect threats or network compromise.
GigaSECURE Security Delivery Platform provides the following:
| a complete network-wide reach, physical and virtual. Refer to GigaSECURE and GigaVUE nodes, TAPs, GigaVUE-VM and GigaVUE-FM. |
| scalable metadata extraction for improved forensics. Refer to NetFlow Generation under GigaSECURE and GigaSMART Applications. |
| isolation of applications for targeting inspection. Refer to Application Session Filtering under GigaSECURE and GigaSMART Applications. |
| visibility to encrypted traffic for threat detection. Refer to SSL Decryption under GigaSECURE and GigaSMART Applications. |
| inline bypass for connected security applications. Refer to GigaSECURE and Inline Bypass. |



