Configure GigaVUE Fabric Components in GigaVUE-FM
After configuring the Monitoring Domain, you will be navigated to the Azure Fabric Launch Configuration page.
In the same Azure Fabric Launch Configuration page, you can configure all the GigaVUE fabric components.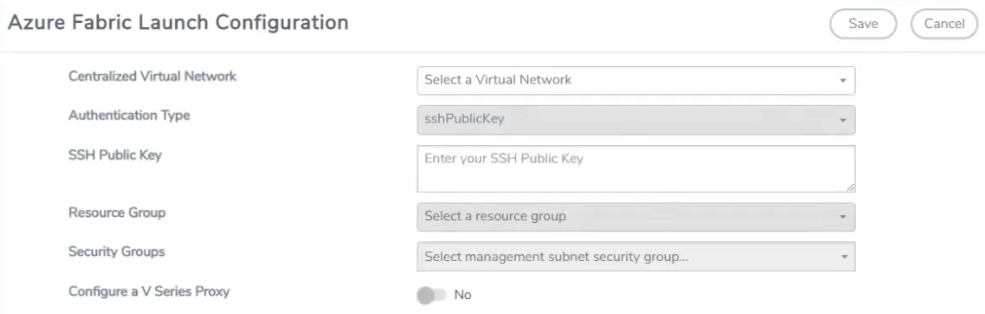
Enter or select the required information as described in the following table.
|
Fields |
Description |
|
Centralized Virtual Network |
Alias of the centralized VNet in which the G-vTAP Controllers, V Series Proxies, and the GigaVUE V Series nodes are launched. |
|
Authentication Type |
Select Password or SSH Public Key as the Authentication Type to connect with the Centralized VNet. Note: SSH Public Key is the only supported authentication type for V Series 2 solution. |
|
SSH Public Key |
The SSH public key for the GigaVUE fabric nodes. |
|
Resource Group |
The Resource Groups created in Azure for communication between the controllers, nodes, and GigaVUE-FM. This is a required field. |
|
Security Groups |
The security group created for the GigaVUE fabric nodes. |
|
Click Yes to configure V Series Proxy/Controller for the monitoring domain. Refer to Configure GigaVUE V Series Proxy/Controller |
|
Example:
az vm image list --all --publisher gigamon-inc --offer gigamon-fm-<version>
az vm image terms accept --urn gigamon-inc:gigamon-fm-<version>:vseries-node:<version>
az vm image terms accept --urn gigamon-inc:gigamon-fm-<version>:vseries-proxy:<version>
az vm image terms accept --urn gigamon-inc:gigamon-fm-<version>:gvtap-cntlr:<version>
Refer to the following topics for details:
- Configure G-vTAP Controllers
- Configure GigaVUE V Series Proxy/Controller
- Configure GigaVUE V Series Node
Configure G-vTAP Controller
A G-vTAP Controller manages multiple G-vTAP Agents and orchestrates the flow of mirrored traffic to GigaVUE V Series nodes.
Note: A single G-vTAP Controller can manage up to 1000 G-vTAP Agents. The recommended minimum instance type is Standard_B1s for G-vTAP Controller.
A G-vTAP Controller can only manage G-vTAP Agents that has the same version.
To configure the G-vTAP Controllers:
Note: You cannot configure G-vTAP Controller for Tunnel as the traffic acquisition method.
In the Azure Fabric Launch Configuration page, Enter or select the appropriate values for the G-vTAP Controller as described in the following table.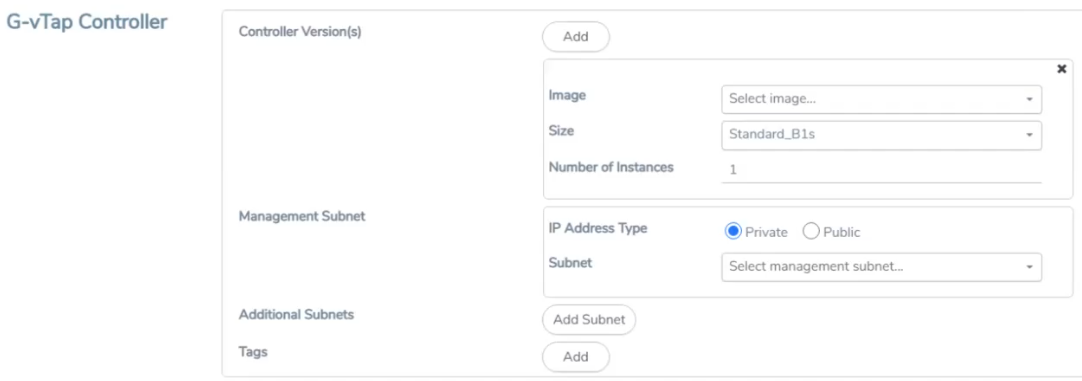
Configure GigaVUE V Series Proxy/Controller
GigaVUE V Series Proxy of the V series 2 solution and the GigaVUE V Series Controller manage multiple GigaVUE V Series nodes and orchestrates the flow of traffic from GigaVUE V Series nodes to the monitoring tools. GigaVUE-FM uses one or more GigaVUE V Series Controllers to communicate with the GigaVUE V Series nodes.
Note: A single GigaVUE V Series Controller can manage up to 100 GigaVUE V Series nodes. The recommended minimum instance type is Standard_B1s for V Series Controller.
To configure the GigaVUE V Series Controller, do the following:
- In the Azure Fabric Launch Configuration page, Select Yes to Configure a V Series Proxy and the V Series Proxy fields appears.
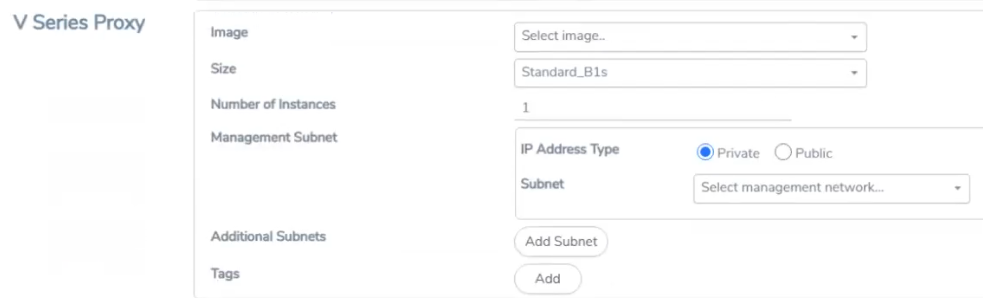
- Enter or select the appropriate values for the V Series Proxy. Refer to the G-vTAP Controller field descriptions for detailed information.
Configure GigaVUE V Series Node
GigaVUE® V Series node is a visibility node that aggregates mirrored traffic from multiple G-vTAP Agents. It applies filters, manipulates the packets using GigaSMART applications, and distributes the optimized traffic to cloud-based tools or backhaul to GigaVUE Cloud for Azure using the standard VXLAN tunnels.
To launch a GigaVUE V Series node, do the following:
In the Azure Fabric Launch Configuration page, Enter or select the appropriate values for the V Series Node. 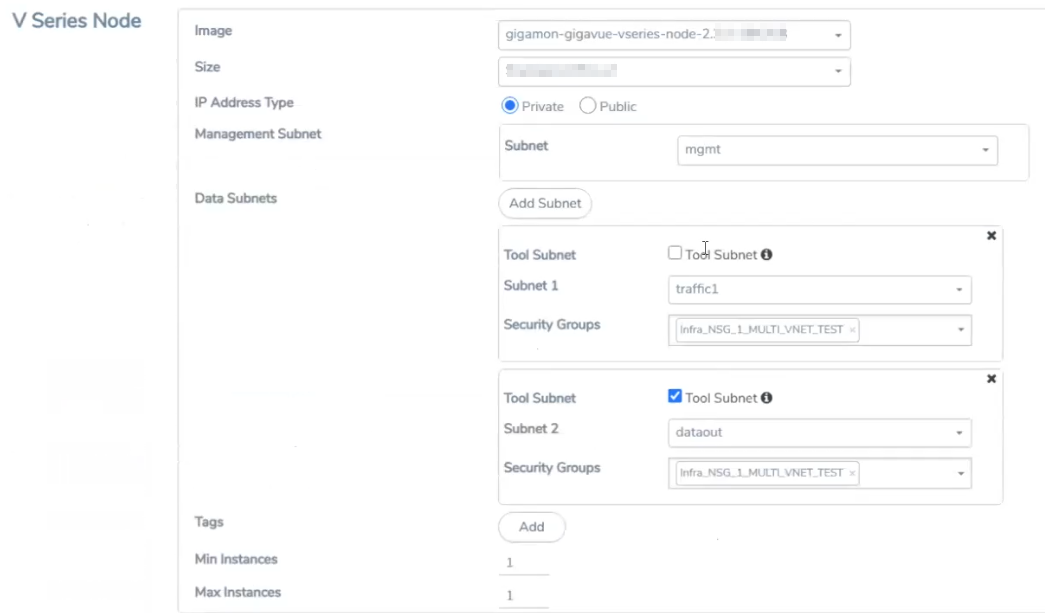
|
Fields |
Description |
|||||||||
|
Image |
From the Image drop-down list, select a V Series node image. |
|||||||||
|
Size |
From the Size down-down list, select a size for the V Series node. The default size for V Series 2 configuration is Standard_D4s_v4 and for the V Series 1 configuration is Standard_DS2_v2. |
|||||||||
|
IP Address Type |
Select one of the following IP address types:
|
|||||||||
|
Management Subnet |
Subnet: Select a management subnet for V Series node. The subnet that is used for communication between the G-vTAP Agents and the V Series nodes, as well as to communicate with GigaVUE-FM. Every fabric node (both controllers and the nodes) need a way to talk to each other and GigaVUE-FM. So they should share at least one management plane/subnet. |
|||||||||
|
Data Subnet(s) |
The subnet that receives the mirrored VXLAN tunnel traffic from the G-vTAP Agents. Select a Subnet and the respective Security Groups. Click Add to add additional data subnets. Note: Using the Tool Subnet checkbox you can indicate the subnets to be used by the V Series node to egress the aggregated/manipulated traffic to the tools. |
|||||||||
|
Tag(s) |
(Optional) The key name and value that helps to identify the V Series node instances in your Azure environment. For example, you might have V Series node deployed in many regions. To distinguish these V Series node based on the regions, you can provide a name that is easy to identify. To add a tag:
|
|||||||||
|
Min Instances |
The minimum number of GigaVUE V Series nodes to be launched in the Azure connection. The minimum number of instances that can be entered is 1. Note: Nodes will be launched when a monitoring session is deployed if GigaVUE-FM discovers some targets to monitor. The minimum amount will be launched at that time.The GigaVUE-FM will delete the nodes if they are idle for over 15 minutes. |
|||||||||
|
Max Instances |
The maximum number of GigaVUE V Series nodes that can be launched in the Azure connection. When the number of instances per V Series node exceeds the max instances specified in this field, increase the number in the Max Instances to Launch. When additional V Series nodes are launched, GigaVUE-FM rebalances the instances assigned to the nodes. This can result in a brief interruption of traffic. |
Click Save to complete the Azure Fabric Launch Configuration.
A monitoring domain is created and you can view the monitoring domain and fabric component details by clicking on a monitoring domain name in theMonitoring Domain page.



