Establish Connection to Azure
When you first connect GigaVUE-FM to Azure, you need the appropriate authentication for Azure to verify your identity and check if you have permission to access the resources that you are requesting. This is used for GigaVUE-FM to integrate with Azure APIs and to automate the fabric deployment and management. GigaVUE-FM supports two types of authentications with Azure.
Refer to the following topics.
Managed Identity (recommended)
Managed Identity (MSI) is a feature of Azure Active Directory. When you enable MSI on an Azure service, Azure automatically creates an identity for the service VM in the Azure AD tenant used by your Azure subscription.Enable MSI for the GigaVUE-FM VM by using the Azure CLI command:
az vm assign-identity -g <Resource group where FM is deployed> -n <GigaVUE-FM name>
The above command enables MSI for the GigaVUE-FM for the entire subscription. If more restrictions are needed, use "-scope <resource group id>" as an extension to the command to restrict the MSI permissions for GigaVUE-FM to a resource group.
Note: It may take up to 10 minutes or more for Azure to propagate the permissions. GigaVUE‑FM will fail during this time to connect to Azure.
Managed Identity (MSI) is only available for GigaVUE-FM launched inside Azure. You can run these commands in the Azure Portal in an cloud shell (icon in upper right of portal as seen here): ![]()
There are 2 steps to have MSI work:
- Enable MSI on the VM running in GigaVUE‑FM.
- Assign permissions to this VM on all the resources where you need GigaVUE‑FM to manage.
Enable MSI on the VM running GigaVUE‑FM
Note: If you are using an older CLI version, the command "az vm assign-identity" is replaced with the new command: "az vm identity assign"
- Launch the GigaVUE‑FM Virtual Machine in Azure.
- Enable MSI and Assign roles to the VM. You can use the CLI or portal to enable MSI and assign roles to VMS.
Enable MSI using the CLI
- Assign a custom role at resource group level where you will deploy the fabric:
az vm identity assign -g xxx-fm-feb15 -n xxx-fm-feb15 --role "FM Custom Role RG Level" --scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/xxxz-rg
- If you need the private images, then you have to assign permissions to the resource group of the fabrics. Therefore run this:
az vm identity assign -g xxx-fm-feb15 -n xxx-fm-feb15 --role "FM Custom Role RG Level"--scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/vseries-rg
az vm identity assign -g xxx-fm-feb15 -n xxx-fm-feb15 --role "FM Custom Role RG Level"--scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/gvtap-rg
- Assign a custom role at the subscription level to view the complete account details:
az vm identity assign -g xxx-feb8-fm -n xxx-feb8-fm --role "FM Custom Role Subscription Level" --scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111
For more information, refer to Configure managed identities for Azure resources using Azure CLI topic in the Azure Documentation.
Enable MSI Using the Portal
You can enable MSI at the time of launch or after the launch of GigaVUE‑FM through the portal.
For more information, refer to the following topics in the Azure Documentation:
| Create, list, delete, or assign a role to a user-assigned managed identity |
| Assign Azure roles |
Application ID with client secret
GigaVUE-FM supports application id with client secret authentication. When using GigaVUE-FM to connect to Azure, it uses a service principal. A service principal is an account for a non-human such as an application to connect to Azure. The key fields required for GigaVUE-FM to connect to Azure are Subscription ID, Tenant ID, Application ID, and Application Secret.
- When creating the service principal using the Azure CLI, the output of that command will display the "appId" and "password" fields. These two are the Application ID and Application Secret fields that are required for GigaVUE-FM to connect to Azure. Copy them.
- Now, using the Azure CLI again, do an ‘account show’ command and copy the Subscription ID and the Tenant ID of your subscription.
The GigaVUE‑FM to Azure connection supports application id with client secret authentication. When using GigaVUE‑FM to connect to Azure, it uses a service principal. A service principal is an account for a non-human such as an application to connect to Azure.
Following are the required endpoints for Azure GovCloud:
- authentication_endpoint = https://login.microsoftonline.us/
- azure_endpoint = https://management.usgovcloudapi.net/
To create a service principal in Azure, refer to the following topics in the Azure Documentation:
| Create an Azure service principal with the Azure CLI |
| Create an Azure service principal with Azure PowerShell |
| Create an Azure service principal with Azure Portal |
Custom Roles
The ‘built-in’ roles provided by Microsoft are open to all resources. You can create a custom role if required.
You can create a custom role in Azure as described in the following examples. The "assignableScopes" are the objects which this role is allowed to be assigned. In the example below, for the RG level role, you can assign permissions for GigaVUE‑FM to access your resource group and also two other resource groups where the GigaVUE V series proxy/controller and G-vTAP controllers are placed. Without the GigaVUE V series proxy/controller and G-vTAP controllers you would only see images in the marketplace.
For more information, refer to Azure custom roles topic in the Azure Documentation.
Using CLI:
az role definition create --role-definition FM-custom-role-azure-RG-level.json
This section provides examples of the JSON file above.The assignable scopes can be at the Resource Group level, or at the entire Subscription level. This is defined in that JSON file.
Example: Custom Role at Resource Group Level
The following is an example of what you need at RG level:
{
"Name": "FM Custom Role RG Level",
"IsCustom": true,
"Description": "Minimum permissions for FM to operate",
"Actions": [
"Microsoft.Compute/virtualMachines/read",
"Microsoft.Compute/virtualMachines/write",
"Microsoft.Compute/virtualMachines/delete",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/powerOff/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Compute/virtualMachines/instanceView/read",
"Microsoft.Compute/locations/vmSizes/read",
"Microsoft.Compute/images/read",
"Microsoft.Compute/disks/read",
"Microsoft.Compute/disks/write",
"Microsoft.Compute/disks/delete",
"Microsoft.Network/networkInterfaces/read",
"Microsoft.Network/networkInterfaces/write",
"Microsoft.Network/virtualNetworks/subnets/join/action",
"Microsoft.Network/virtualNetworks/subnets/read",
"Microsoft.Network/networkInterfaces/join/action",
"Microsoft.Network/networkInterfaces/delete",
"Microsoft.Network/publicIPAddresses/read",
"Microsoft.Network/publicIPAddresses/write",
"Microsoft.Network/publicIPAddresses/delete",
"Microsoft.Network/publicIPAddresses/join/action",
"Microsoft.Network/virtualNetworks/read",
"Microsoft.Network/virtualNetworks/virtualMachines/read",
"Microsoft.Network/networkSecurityGroups/read",
"Microsoft.Network/networkSecurityGroups/join/action",
"Microsoft.Network/publicIPAddresses/read ",
"Microsoft.Network/publicIPAddresses/write",
"Microsoft.Network/publicIPAddresses/delete",
"Microsoft.Network/publicIPAddresses/join/action",
"Microsoft.Resources/subscriptions/locations/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Resources/subscriptions/resourcegroups/resources/read"
],
"NotActions": [
],
"AssignableScopes": [
"/subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/xxxz-rg",
"/subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/vseries-rg",
"/subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/gvtap-rg"
]
}
Example: Custom Role for Subscription Level
The following is an example of what you need at the Subscription level:
"Name": "FM Custom Role Subscription Level",
"IsCustom": true,
"Description": "Minimum permissions for FM to operate at a subscription level",
"Actions": [
"Microsoft.Compute/virtualMachines/read",
"Microsoft.Compute/virtualMachines/write",
"Microsoft.Compute/virtualMachines/delete",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/powerOff/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Compute/virtualMachines/instanceView/read",
"Microsoft.Compute/locations/vmSizes/read",
"Microsoft.Compute/images/read",
"Microsoft.Compute/disks/read",
"Microsoft.Compute/disks/write",
"Microsoft.Compute/disks/delete",
"Microsoft.Network/networkInterfaces/read",
"Microsoft.Network/networkInterfaces/write",
"Microsoft.Network/virtualNetworks/subnets/join/action",
"Microsoft.Network/virtualNetworks/subnets/read",
"Microsoft.Network/networkInterfaces/join/action",
"Microsoft.Network/networkInterfaces/delete",
"Microsoft.Network/publicIPAddresses/read",
"Microsoft.Network/publicIPAddresses/write",
"Microsoft.Network/publicIPAddresses/delete",
"Microsoft.Network/publicIPAddresses/join/action",
"Microsoft.Network/virtualNetworks/read",
"Microsoft.Network/virtualNetworks/virtualMachines/read",
"Microsoft.Network/networkSecurityGroups/read",
"Microsoft.Network/networkSecurityGroups/join/action",
"Microsoft.Network/publicIPAddresses/read ",
"Microsoft.Network/publicIPAddresses/write",
"Microsoft.Network/publicIPAddresses/delete",
"Microsoft.Network/publicIPAddresses/join/action",
"Microsoft.Resources/subscriptions/locations/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Resources/subscriptions/resourceGroups/write",
"Microsoft.Resources/subscriptions/resourcegroups/resources/read"
],
"NotActions": [
],
"AssignableScopes": [
"/subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111"
]
}
Add Custom Role to Subscription or Resource Group
After creating the custom role, you can add the role to either the Resource Group, or at the Subscription level in the Azure console. In this example, the role is added to my Resource Group. As the GigaVUE‑FM connection gets connected to the VNET in the resource Group "xxxz-rg", the following permissions/roles are added to the Resource Group. If you want to have GigaVUE‑FM create a resource group to launch fabric into, you must add these permissions to the subscription level instead.
For more information, refer to Create or update Azure custom roles in the Azure Documentation.
Note: You are adding permissions for the GigaVUE‑FM running in Azure (Virtual Machine).
In this example, GigaVUE‑FM is running in another resource group "xxxz-fm-feb7". Select the VM and give the required permissions to access the other resource group "xxxz-rg":
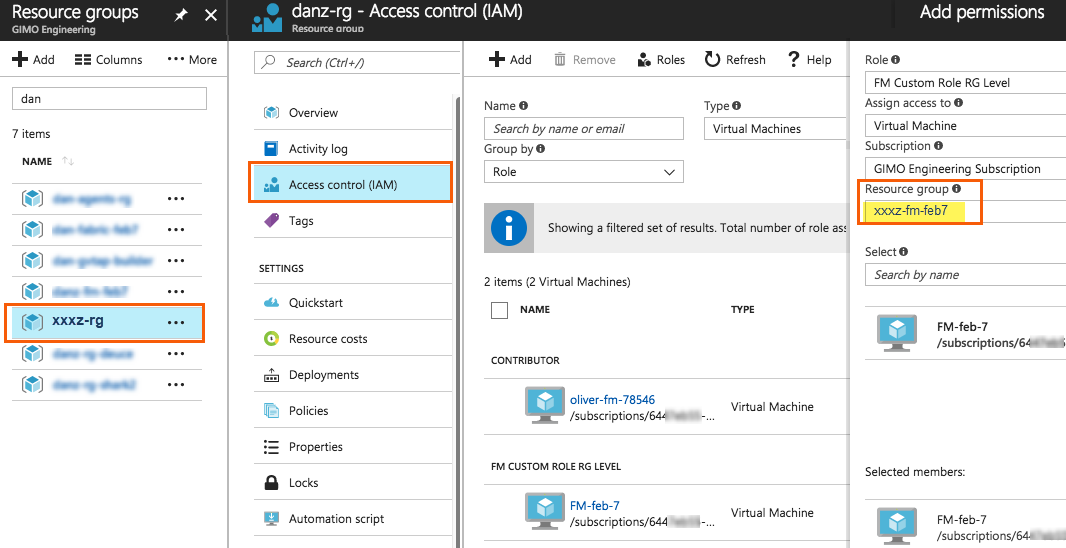
You can also use the CLI to perform the same process. This adds the GigaVUE‑FM instance in RG "xxx-feb8-fm" to have access to another RG called "xxxz-rg":
CLI to add role to Resource Group
az vm assign-identity -g xxx-feb8-fm -n xxx-feb8-fm --role "FM Custom Role RG Level" --scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111/resourceGroups/xxxz-rg
CLI for Subscription Level
az vm assign-identity -g xxx-feb8-fm -n xxx-feb8-fm --role "FM Custom Role Subscriptions Level" --scope /subscriptions/6447xxx11-1x11-111x-11xx-11x11xx11111
If you want to update the Role, you can edit the JSON file, and then update the Role in Azure using the following CLI command:
update role
az role definition update --role-definition FM-custom-role-azure-RG-level.json
Pre-defined Roles
Resource groups pre-created (which the GigaVUE‑FM monitors):
- Assign Reader
- Virtual Machine Contributor
- Network Contributor
- Storage Account Contributor
Resource groups created by GigaVUE‑FM: Contributor on subscription level
Accept EULA and Enable Programmatic Deployment in Azure
For GigaVUE‑FM to be able to launch the fabric images, you must accept the terms of the end user license agreements (EULAs) and enable programmatic access. This can be done in the Azure portal or through PowerShell.
- Accept the Gigamon EULAs for each SKU. These examples show accepting the EULAs from a PowerShell terminal in the Azure Portal:
- HOURLY FM:
Azure:/
PS Azure:\> Get-AzureRmMarketplaceTerms -Publisher "gigamon-inc" -Product "gigamon-fm-5_XX_XX_hourly" -Name "GigaVUE Cloud Suite 5.XX.XX Hourly (100 pack)" | Set-AzureRmMarketplaceTerms -Accept
- BYOL FM:
Azure:/
PS Azure:\> Get-AzureRmMarketplaceTerms -Publisher "gigamon-inc" -Product "gigamon-fm-5_XX_XX" -Name "GigaVUE Cloud Suite 5.XX.XX" | Set-AzureRmMarketplaceTerms -Accept
- Fabric Images (need to accept on all 3):
Azure:/
PS Azure:\> Get-AzureRmMarketplaceTerms -Publisher "gigamon-inc" -Product "gigamon-fm-5_XX_XX" -Name "gvtap-cntlr" | Set-AzureRmMarketplaceTerms -Accept
Azure:/
PS Azure:\> Get-AzureRmMarketplaceTerms -Publisher "gigamon-inc" -Product "gigamon-fm-5_XX_XX" -Name "vseries-cntlr" | Set-AzureRmMarketplaceTerms -Accept
Azure:/
PS Azure:\> Get-AzureRmMarketplaceTerms -Publisher "gigamon-inc" -Product "gigamon-fm-5_XX_XX" -Name "vseries-node" | Set-AzureRmMarketplaceTerms -Accept
- HOURLY FM:
- Configure programmatic deployment through the Azure portal so that GigaVUE‑FM can launch these images:
- Find the images in the Azure Marketplace.
- Click the "Want to deploy programmatically? Get started" link.
- Review the terms of service and the subscription name and then click Enable.
Disclaimer: These are general guidelines for enabling a deployment in Azure. Since the Azure interface is subject to change and is outside Gigamon’s purview, please see Azure documentation for instructions on using Azure.



