map-passalls and port mirrors
How to Send All Traffic to IDS: map-passall
Intrusion Detection Systems need to see all traffic to work effectively. However, you may want to use maps to send different portions of the same traffic source to different destinations. This is the perfect place to use a map-passall. Figure 1 illustrates this:
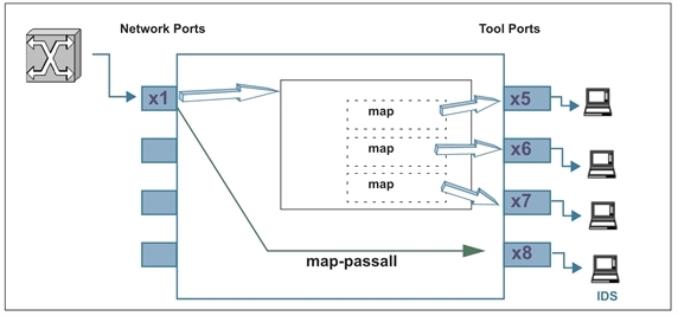
| Figure 5 | Sending All Traffic to IDS |
Temporary Troubleshooting Situations
Under certain circumstances, you may want to see all of the traffic on a particular port without disturbing any of the packet distribution commands already in place for the port. The map-passall gives you a way to do this. For example, suppose you have existing maps sending traffic from network port 1/2/x1 to tool ports 1/2/x5..x7 based on different map rule criteria (Figure 2).
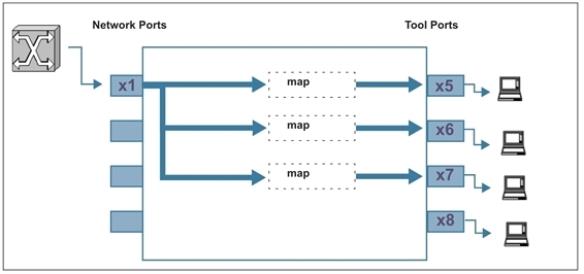
| Figure 6 | Existing Map on Network Port 1/2/x1 |
Complaints of slow response times on the network monitored by network port 1/2/x1 lead you to want to see all of the traffic rather than just the portions broken out by your maps. Because a packet goes only to the destination specified by the map with the highest priority, you cannot just create a new map with no rules to see all of the traffic on the port. However, you also do not want to take down your existing maps.
In a situation like this, you could set up a map-passall for the mapped network port and send the full set of traffic arriving at the network port to another tool port. For example:
(config) # map-passall alias temp_pass (config map temp_pass) # from 1/2/x1 (config map temp_pass) # to 1/2/x8
(config map temp_pass) # exit
Now, the full set of traffic arriving on network port 1/2/x1 is both passed to tool port 1/2/x8 and also distributed to network ports 1/2/x5..x7 based on the existing maps (Figure 3).
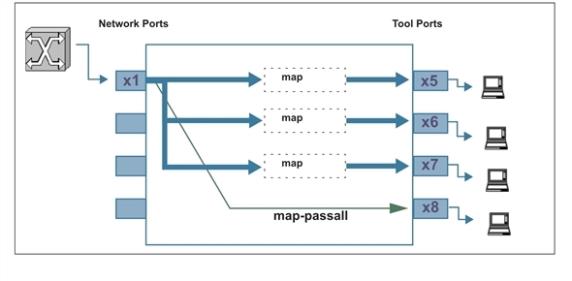
| Figure 7 | Adding a Map-passall for Temporary Troubleshooting |
Example: How to work with Multiple Rules in the Same Map
Rules created in the same map work as “AND”. This means, the Rule1 logic will use the cumulative "AND" operator to include Rule 2 and will only apply the map to the egress port when all conditions are met.
map alias mapallrules
type regular byRule
roles replace admin to owner_roles
rule add pass vlan 924
rule add pass vlan 3009
rule add pass vlan 3014
rule add pass vlan 3017
rule add pass vlan 3020
rule add drop portsrc 1556 protocol tcp
rule add drop portdst 1556 protocol tcp
to 1/1/x6
from 1/1/x2
exit
In this example, the expected output would be that if packets coming in through port x2 from vlan 924 that comes from port src ID 1556 then, drop rule does apply and packets get dropped even though the pass rule was in place for vlan 924.
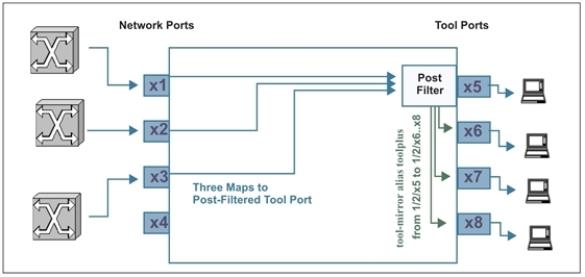
How to Send Tool-Port Filtered Traffic to Multiple Destinations: tool-mirror
You can use the tool-mirror command to see the same tool-port-filtered data on multiple tool ports.
Consider the following scenario:
| Network ports 1/3/x1..x3 have maps sending different data to tool port 1/3/x5. |
| Tool port 1/3/x5 has a port-filter set up to allow only VLAN IDs 100-500. |
Figure 4 illustrates this scenario.
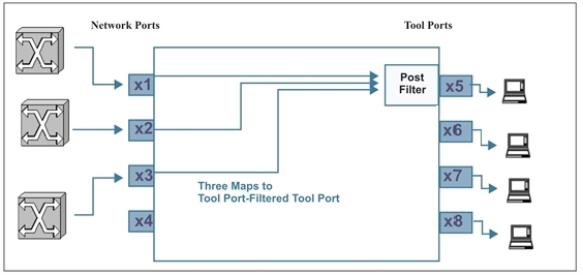
| Figure 8 | Creating a Tool-mirror |
If you wanted different tools to analyze the same tool-port-filtered data, you could set up a tool-mirror to multiple tool ports so that they could all see the same data. For example:
(config) # tool-mirror alias toolplus from 1/2/x5 to 1/2/x6..x8
With this configuration (Figure 5), tool ports 1/2/x5 to x8 all see the same tool-port-filtered data.
| Figure 9 | Adding tool-mirrors to Multiple Tool Ports |



