Single Sign-on for GigaVUE‑FM High Availability
Single Sign-on for GigaVUE-FM High Availability is available from software version 5.11.00 and allows connectivity of the GigaVUE‑FM instances in a High Availability group. The following options are available:
- Internal IdP
- External IdP
With GigaVUE-FM HA SSO, if you login to the active GigaVUE-FM instance, the standby instances are also logged in automatically.
- To logout from the GigaVUE-FM High Availability group, you must first log out from the active GigaVUE-FM instance and then from the standby instances. If you attempt to logout from any of the standby instances, you will be redirected to the active GigaVUE-FM instance and the standby will not be logged out.
- If the active instance in a GigaVUE-FM HA group changes, you need not re-login to the FM HA group.
Internal IdP
GigaVUE-FM HA uses shibboleth 2.0 identity provider for authentication and authorization. The active GigaVUE‑FM instance of the High Availability group acts as the Identity provider. The two standby instances serve as the service providers.
Each of the GigaVUE‑FM instances in the HA group has the following configurations:
- GigaVUE-FM application
- Shibboleth
- Authentication layer that account for the different authentication mechanisms
If you access a standby GigaVUE-FM instance, you will be redirected to the active GigaVUE‑FM's IdP.
- If the active GigaVUE‑FM is not authenticated, the login page of the active FM instance is displayed.
- If the active GigaVUE‑FM is authenticated, it will send the authentication response to the browser, and the standby instance will verify the same and will be authenticated.
Note: The required signing certificates and SSO certificates are already uploaded in the trust store of the GigaVUE-FM instance.
External IdP
ADFS is the only external IdP that has been qualified to be operational with GigaVUE-FM. To configure ADFS as external IdP you must perform the following configuration:
- Download ADFS server's custom certificate.
- Upload that certificate in the trust store of the GigaVUE-FM master.
Note: Upload the certificate in all the members of the HA group, if required.
- Configure EntityId for all the member of the High Availability group.
Note: The EntityId must be unique for each of the members of the High Availability group.
To use the external ADFS, you must perform the following configurations in the active GigaVUE-FM instance.
- Go to Authentication > Authentication Type.
- Select Third Party as Authentication Type.
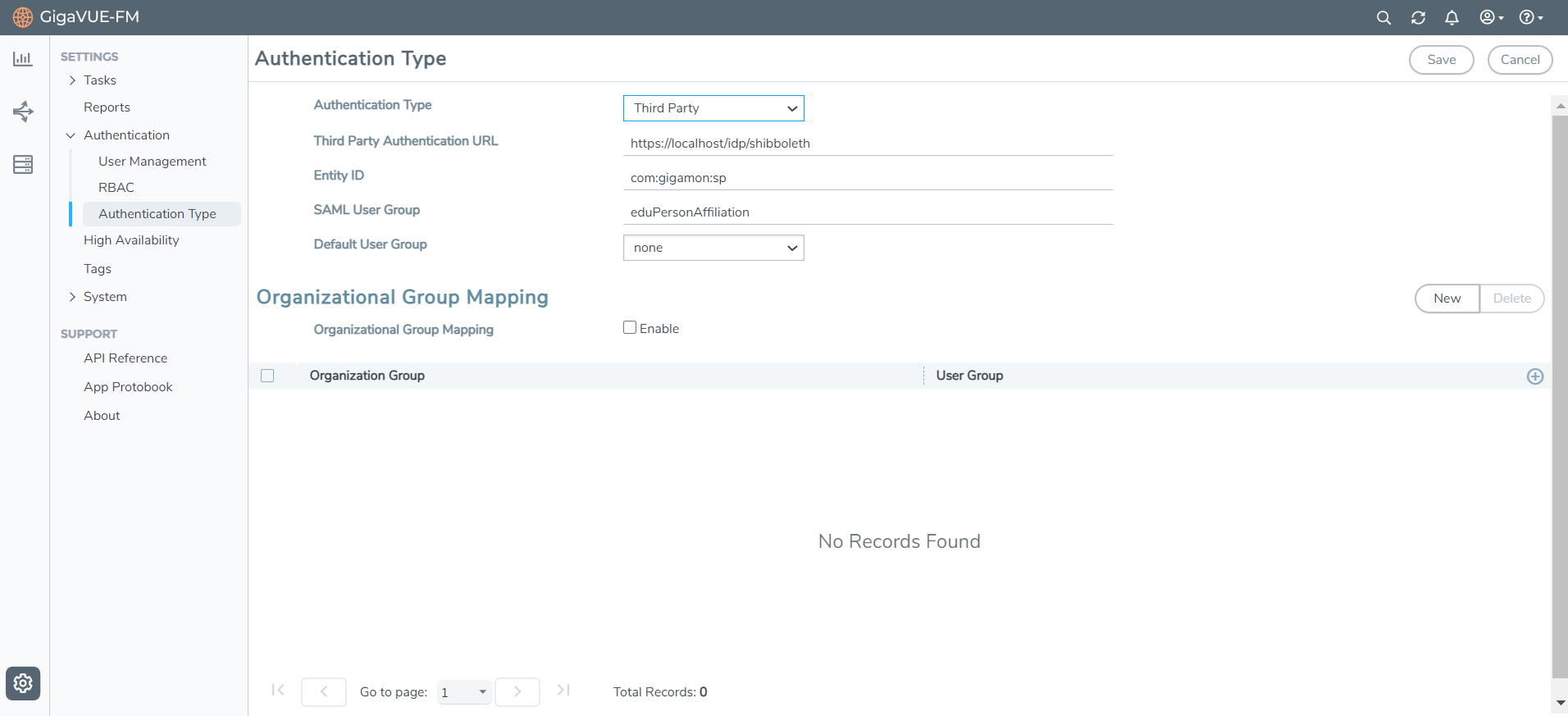
- Provide the URL of the ADFS in the Third Party Authentication URL.
Note: Do not configure EntityId as this value has been already configured through the High Availability GUI. However, if you configure the EntityId value for the active GigaVUE-FM instance it will not be overridden.
You must perform these configurations only in the active GigaVUE‑FM instance, because the values configured in the active instance will be synced across all members of the GigaVUE‑FM HA.
Use the following commands to restart the GigaVUE-FM instances of the High Availability group:
systemctl stop tomcat@cms.service
systemctl start tomcat@cms.service
After restarting GigaVUE-FM
- Access https://<fm ip address>/saml/metadata. This will generate and download GigaVUE-FM's Service Provider metadata.
- Generate this metadata for all the members of High Availability group.
- Upload the GigaVUE-FM metadata into the ADFS server.



